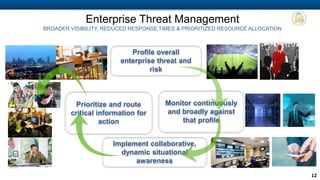
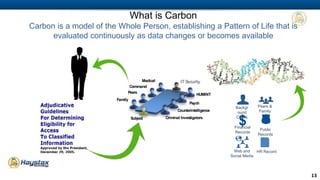
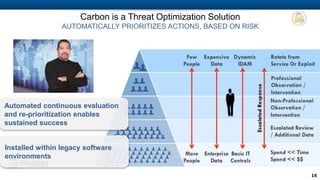
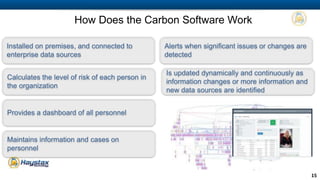
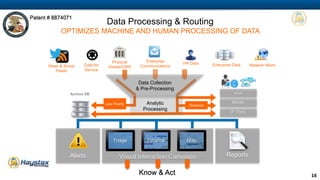
Haystax provides advanced cybersecurity and threat management solutions focused on insider threats and optimizing personnel risk assessment through its 'carbon' model. The platform integrates various data sources to continuously evaluate individual risk levels and streamline threat detection and response. Their analytical approach aims to reduce noise in threat signals, offering real-time actionable intelligence for better decision-making in enterprise environments.