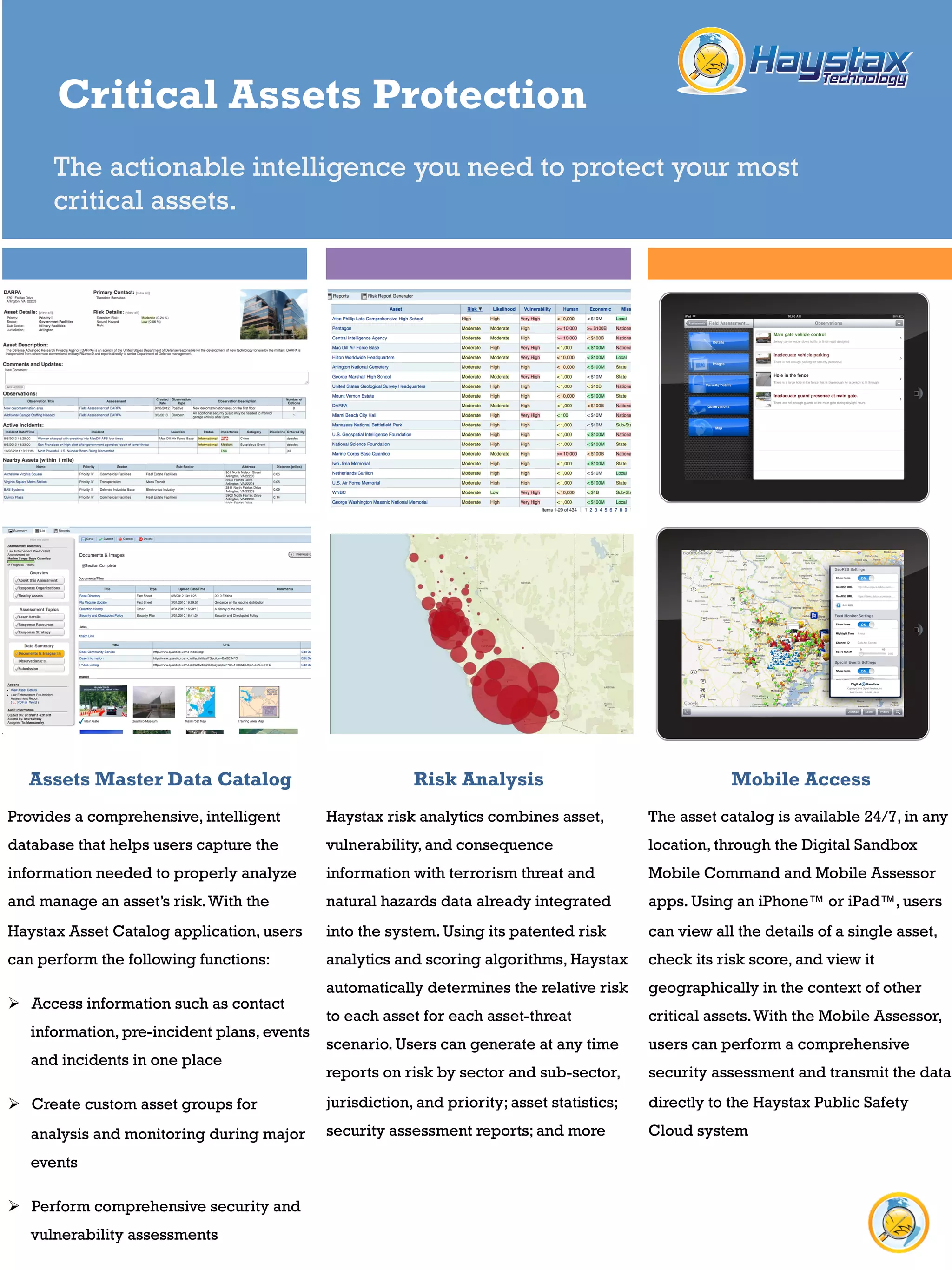
The Haystax Asset Catalog application provides a comprehensive database to help users manage asset risk. It allows users to access asset information, create custom groups, and perform security assessments in one place. Haystax risk analytics combines asset, vulnerability, and consequence data to automatically determine relative risk to each asset. The asset catalog is available through mobile apps for viewing asset details and security assessments from any location. Haystax has been used by Boston and Houston to manage critical infrastructure, share information across agencies and private partners, and leverage mobile apps for data collection and incident response.