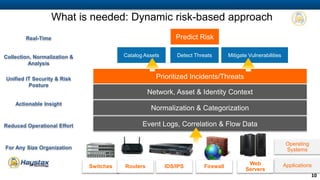
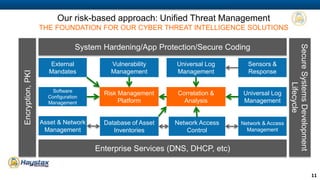
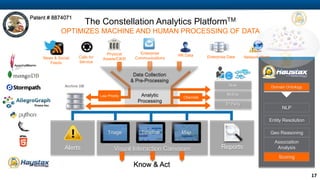
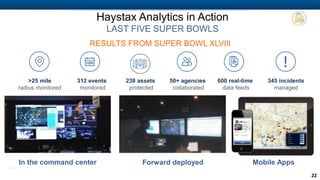
Haystax is a cybersecurity and enterprise threat intelligence company that provides real-time actionable intelligence solutions through advanced analytics. It has over 350 employees with extensive government and commercial experience. Haystax protects critical infrastructure, detects threats, and provides contextual situational awareness through mobile apps and visualization tools to enable rapid decision making. Key customers include the defense sector, intelligence community, and large cities.