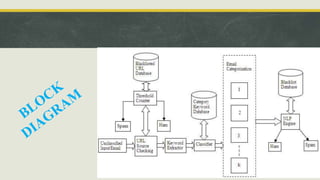
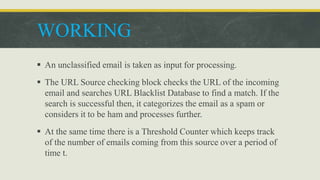
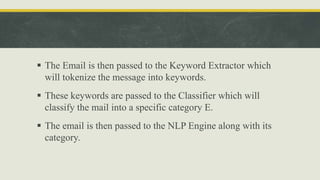
This document discusses natural language processing (NLP) and its application in spam detection through methods such as n-gram modeling, word stemming, and Bayesian classification. It outlines a proposed model that includes a threshold counter to enhance spam filtering efficiency while managing web server congestion. The model involves multiple processing steps, including URL checks and keyword extraction, to classify incoming emails as spam or legitimate.