This document provides information about various hacking techniques such as:
1. Using virtual operating systems and VMware Workstation software to discover system vulnerabilities.
2. Methods for accessing restricted folders using CACLS commands and changing access control lists.
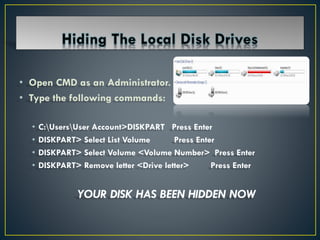
3. Techniques for hiding files like hiding text in images using the COPY command and hiding disk volumes using DISKPART commands.
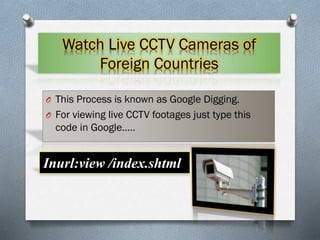
4. Details on phishing, keyloggers, SQL injection attacks, creating fake emails, and viewing live CCTV footage through Google searches.