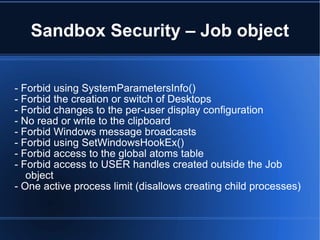
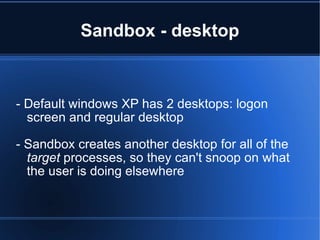
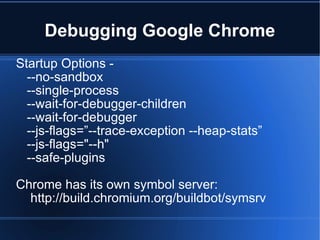
Google Chrome uses a user-mode sandboxing technique to isolate and restrict the renderer process. The sandbox consists of a privileged broker process and one or more sandboxed target processes. The broker process specifies policies, spawns targets, and acts on their behalf by intercepting and evaluating Windows API calls. The sandbox aims to isolate targets and restrict their access to resources using techniques like restricted tokens, job objects, and separate desktops. However, the sandbox has some limitations in its ability to restrict network and USB access under Windows.









![Sandbox Security - restricted token - windows job object - windows desktop object - integrity levels (Vista only [ and Windows 7?])](https://image.slidesharecdn.com/googlechromesandbox-100511051436-phpapp02/85/Google-chrome-sandbox-10-320.jpg)