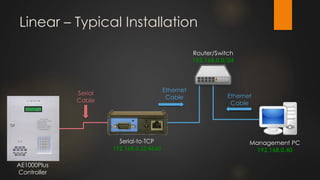
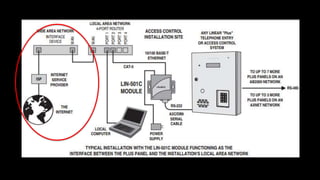
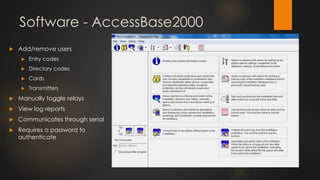
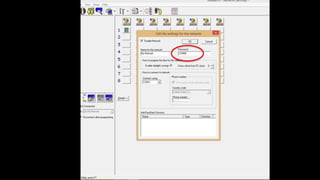
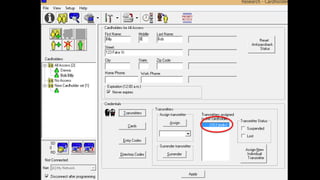
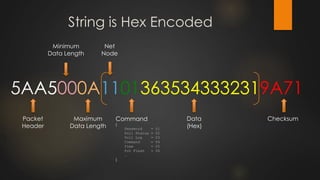
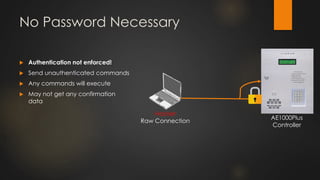
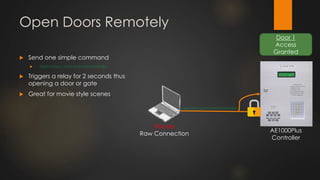
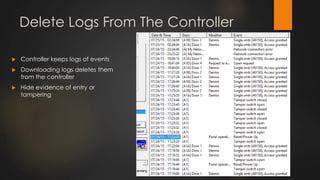
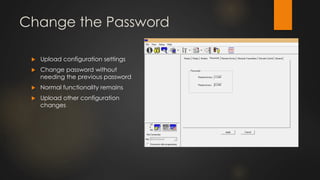
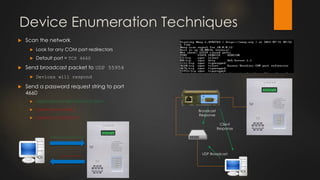
The document discusses the vulnerabilities in physical access control systems, highlighting local and remote attack methods, including brute-force and serial port exploitation. It emphasizes the importance of security measures like changing default passwords and utilizing authentication for networked controllers. Recommendations are provided for enhancing security and mitigating risks associated with these access control systems.