Embed presentation
Download to read offline






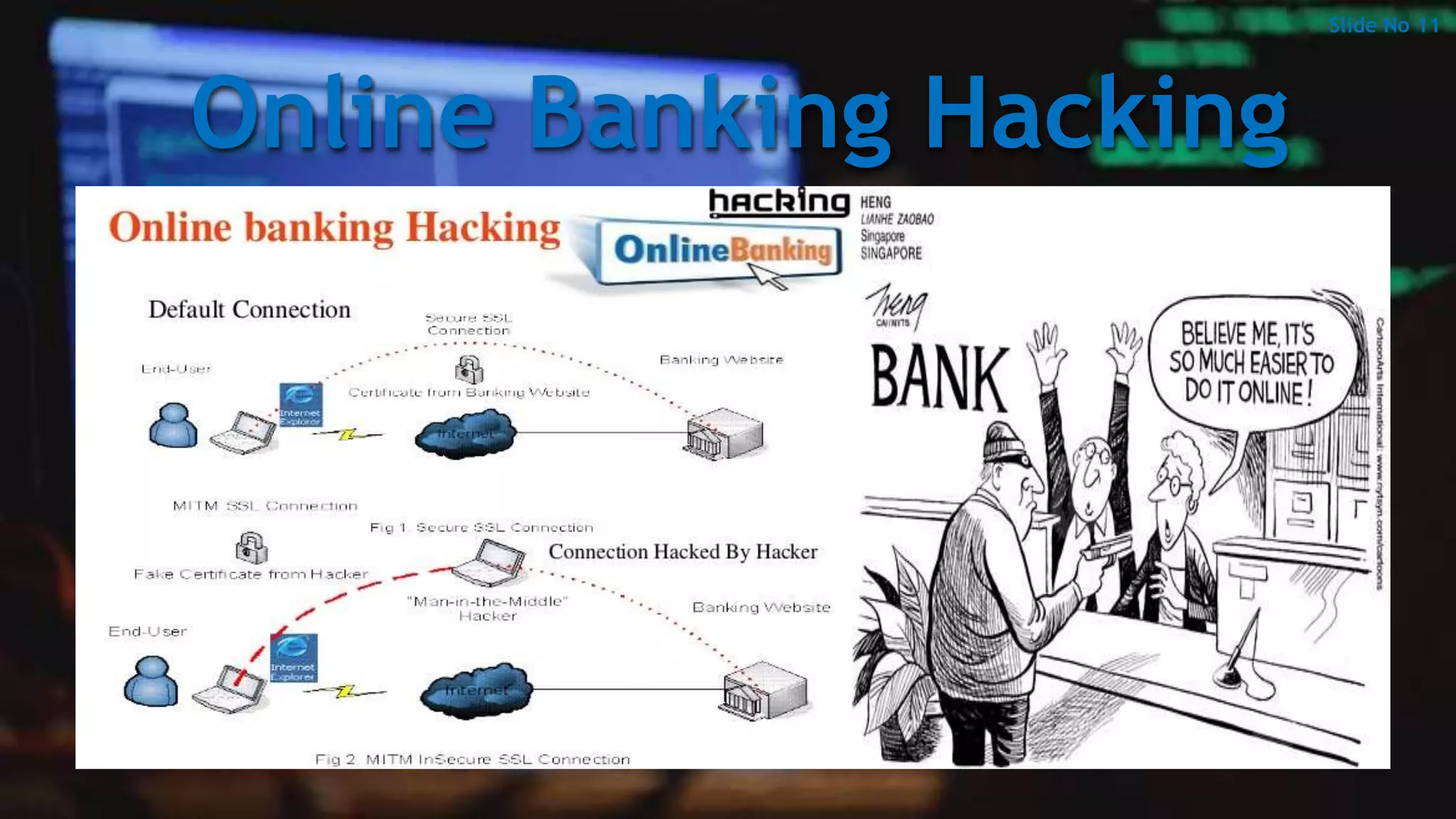


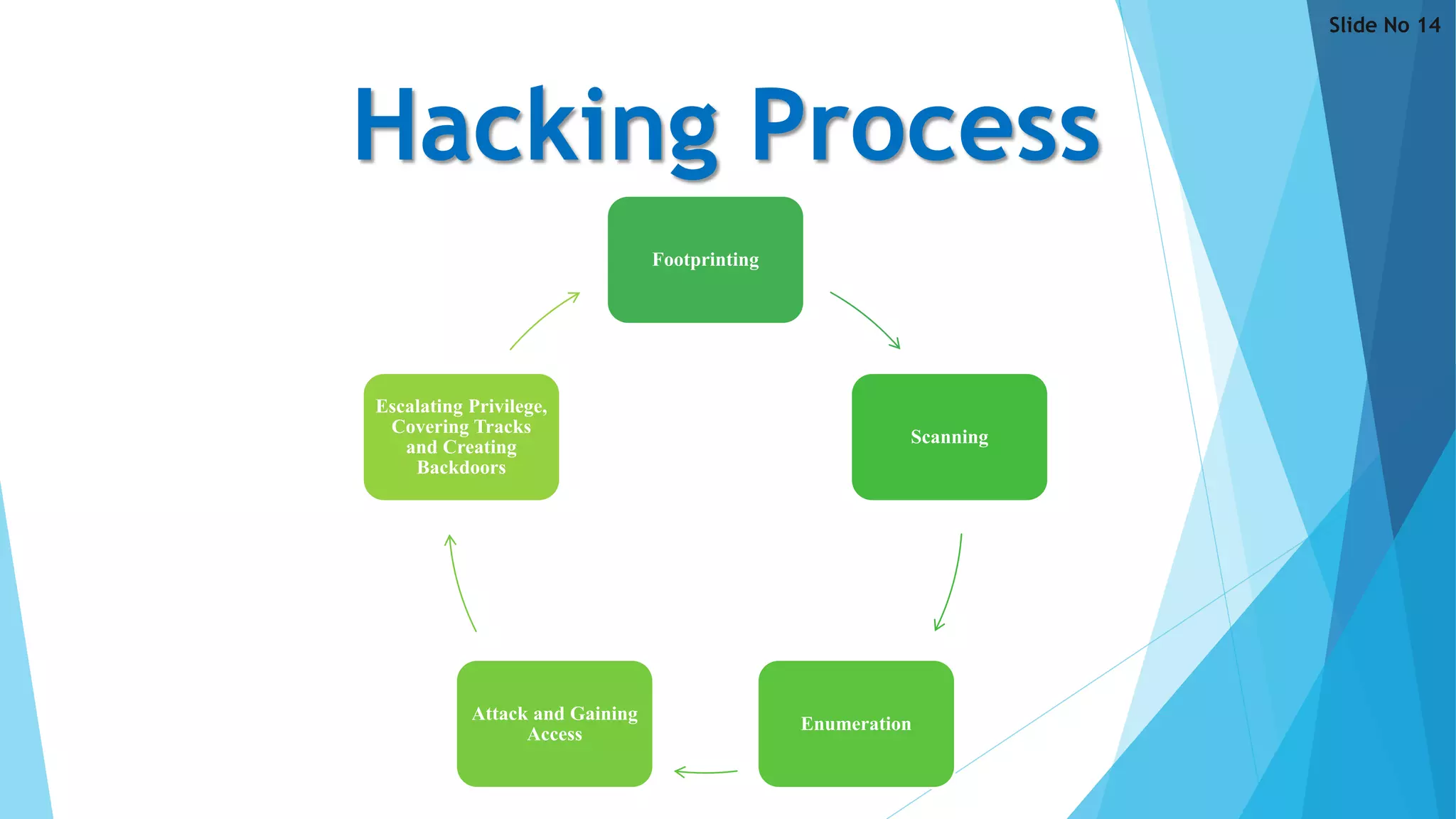






This document discusses hacking and provides an overview of the topic in 23 slides. It defines hacking and different types of hackers, explores the history and various forms of hacking including website, email, network and computer hacking. The document also examines the hacking process, famous hackers, reasons why people hack, how to secure data and accounts, and the advantages and disadvantages of hacking. It aims to give a technical overview of the threat of hacking by covering key definitions, types, methods and perspectives related to this topic.
























