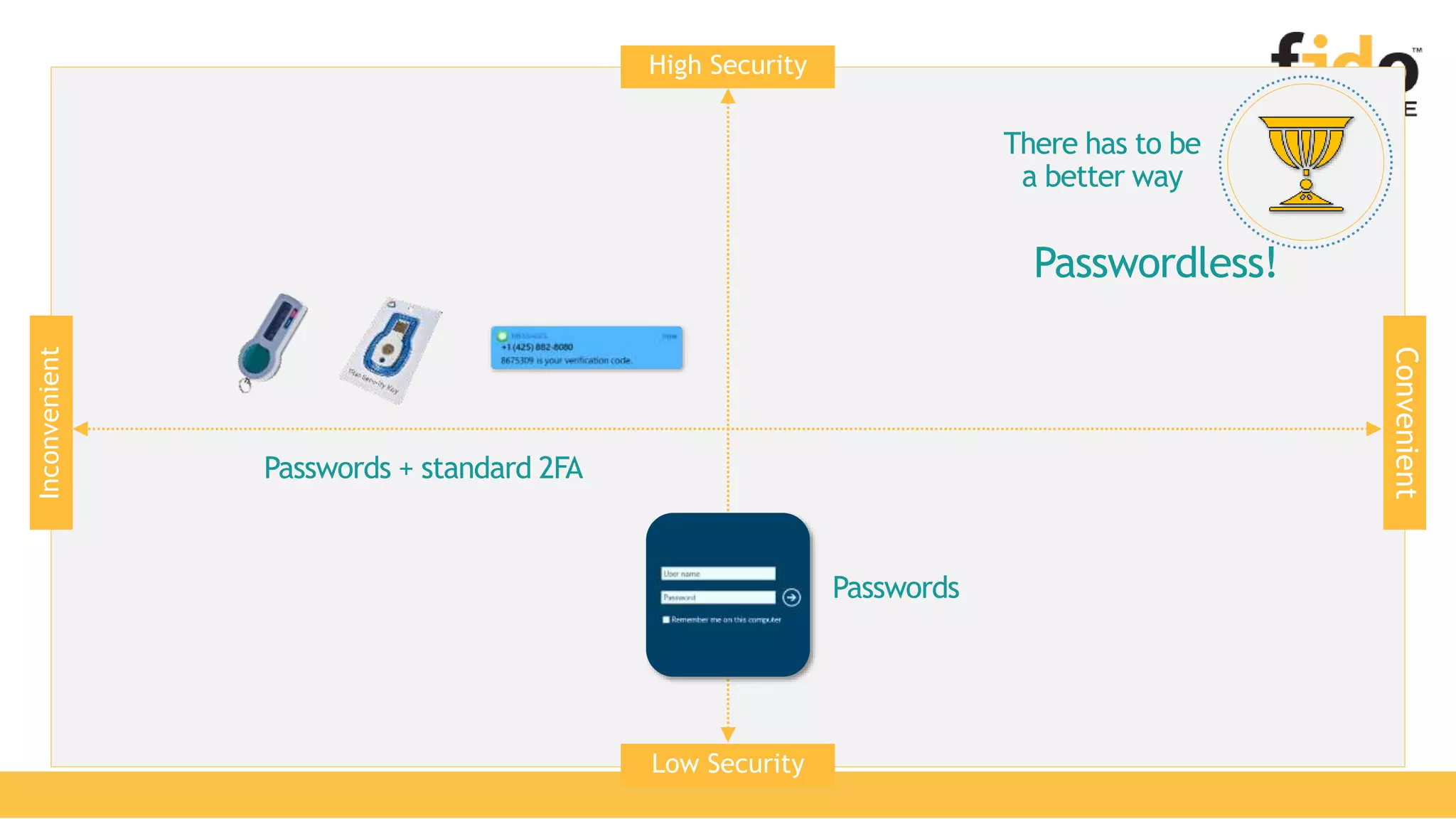
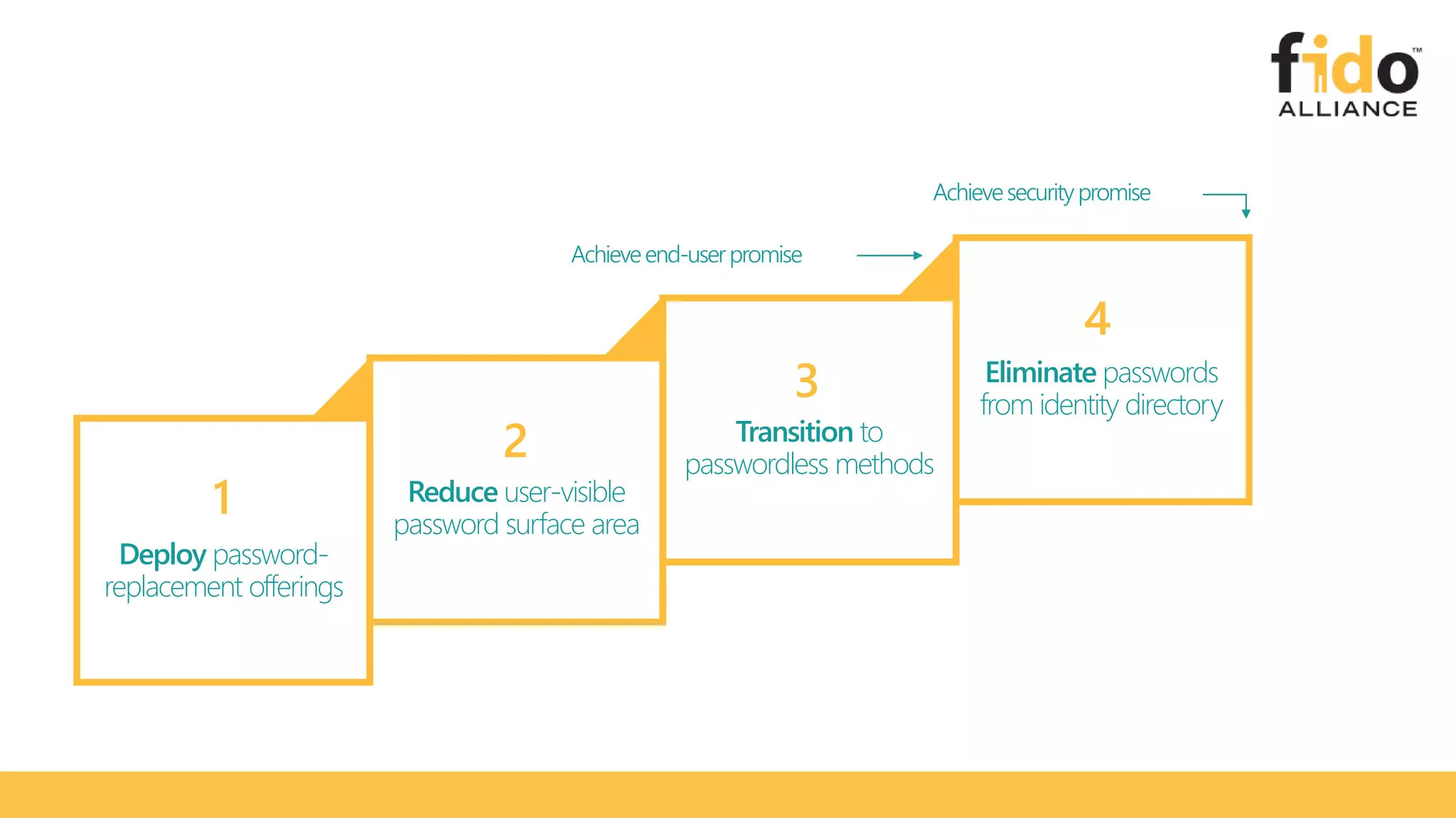
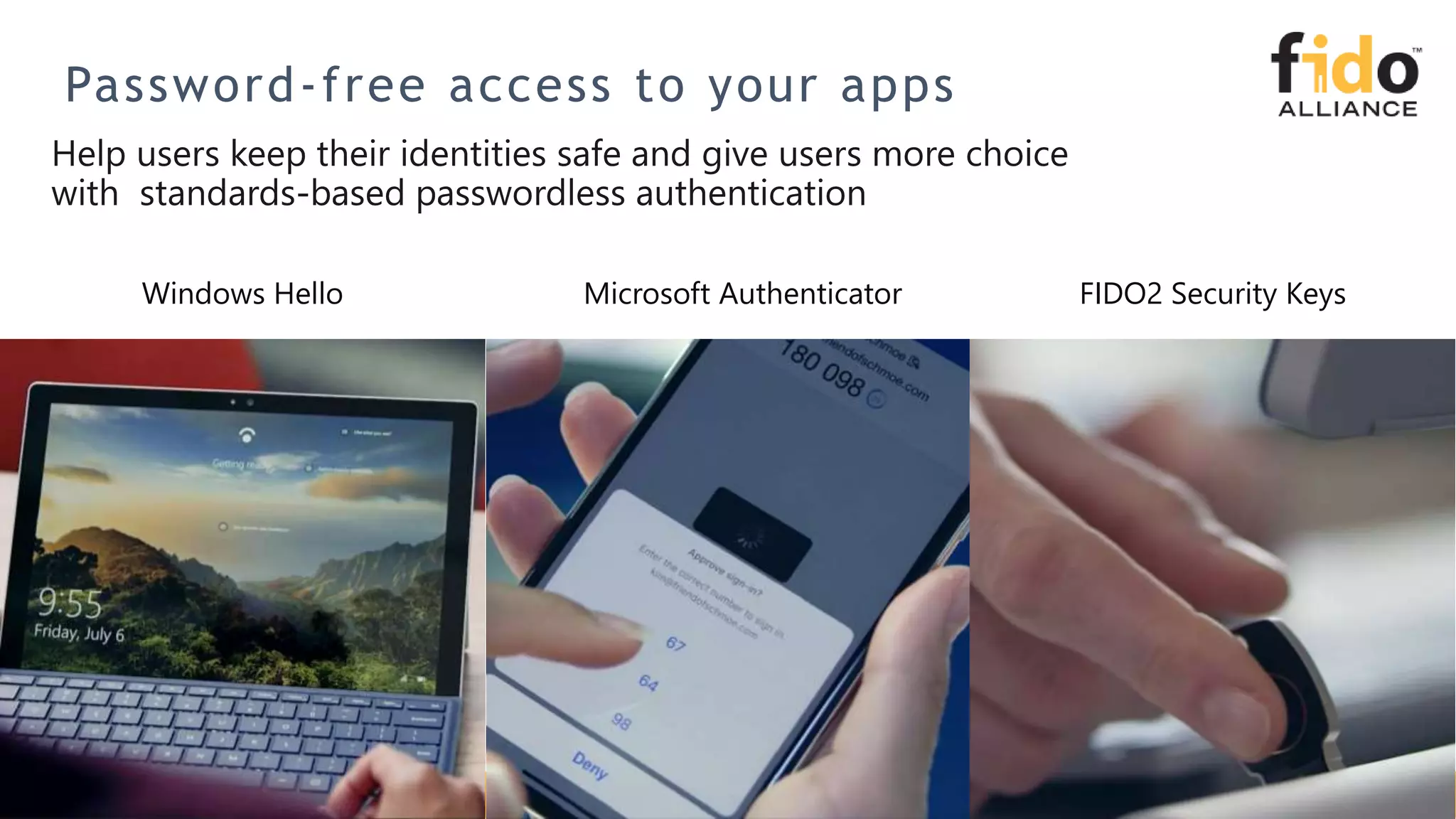
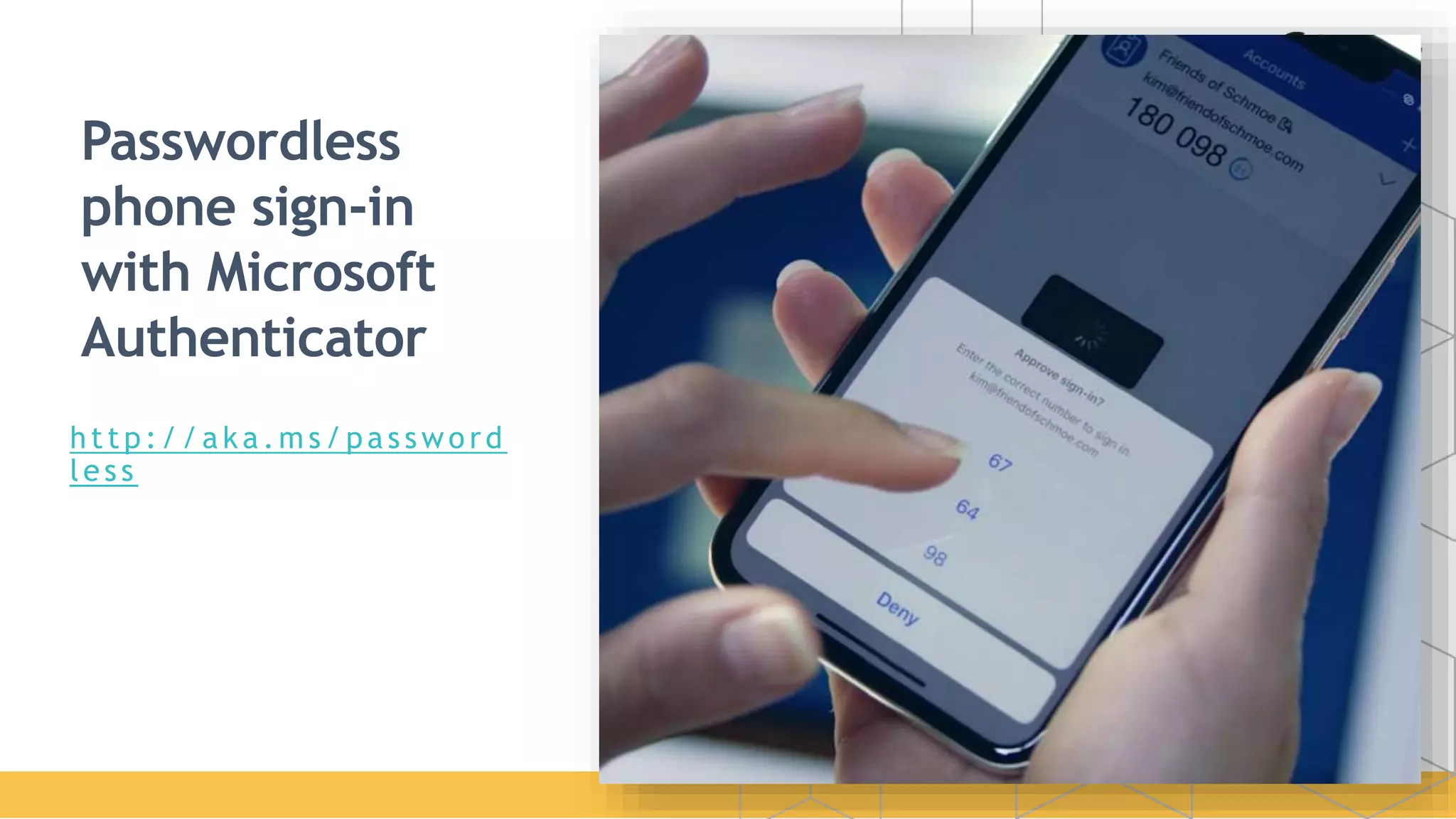
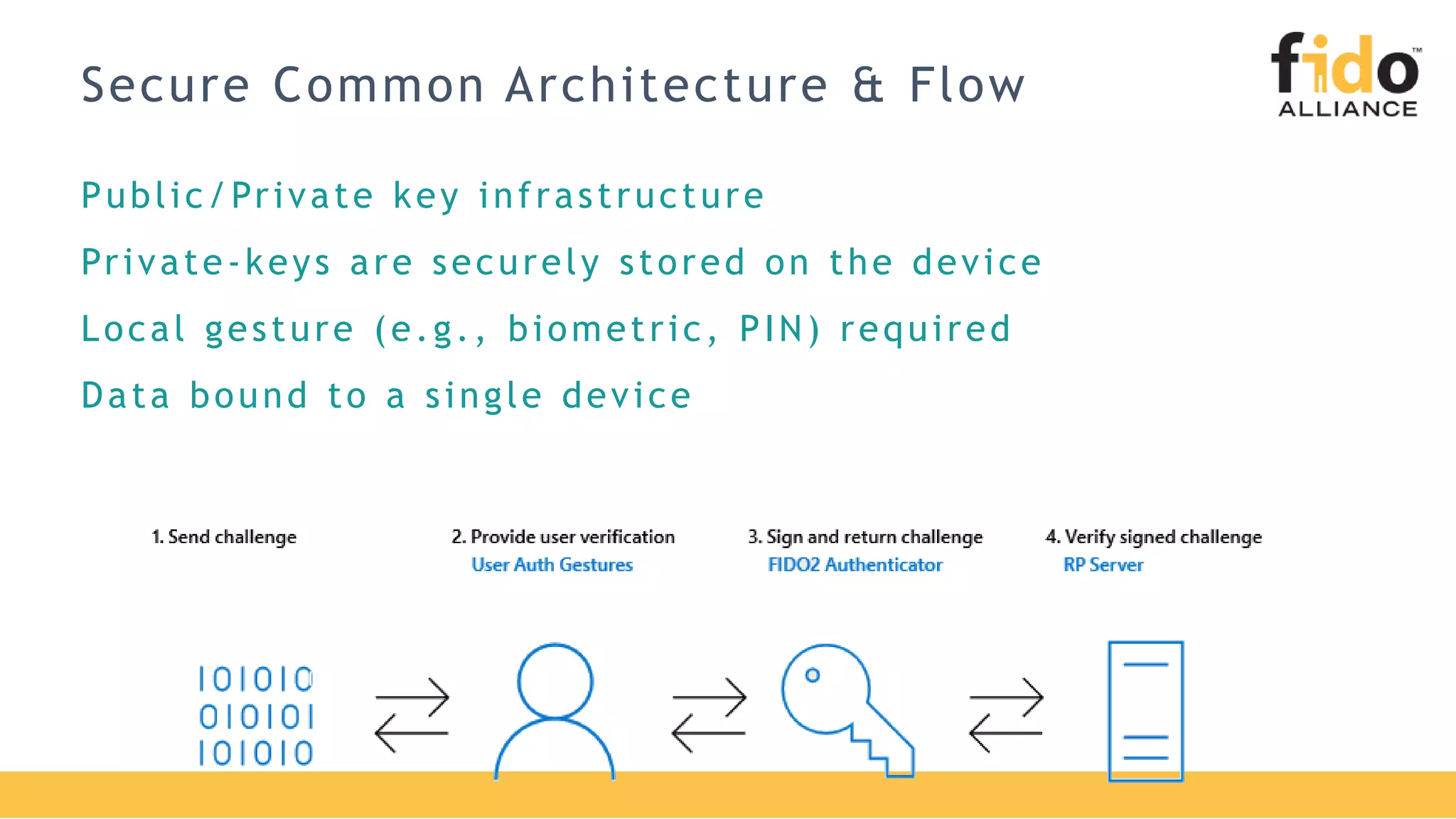
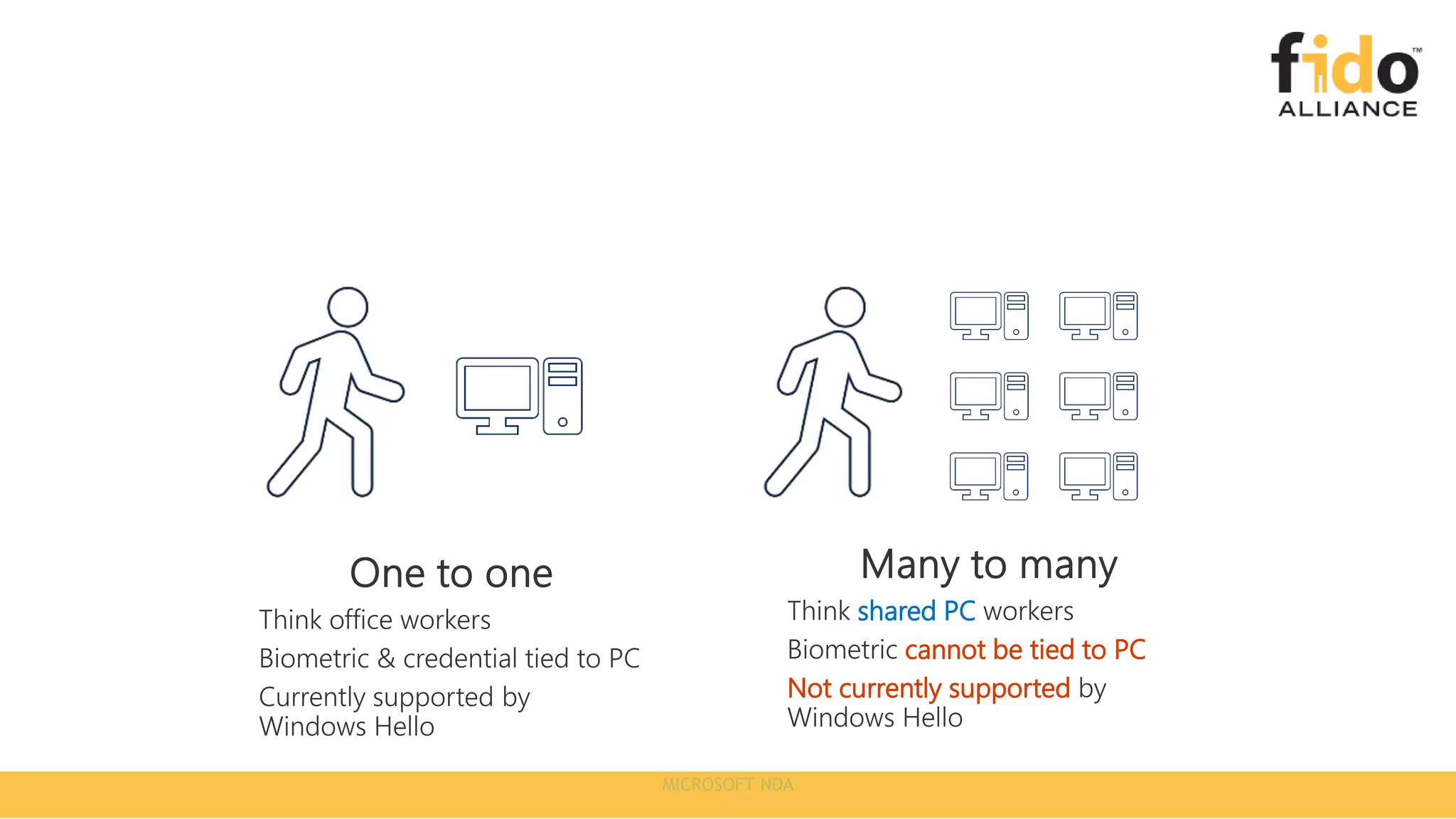
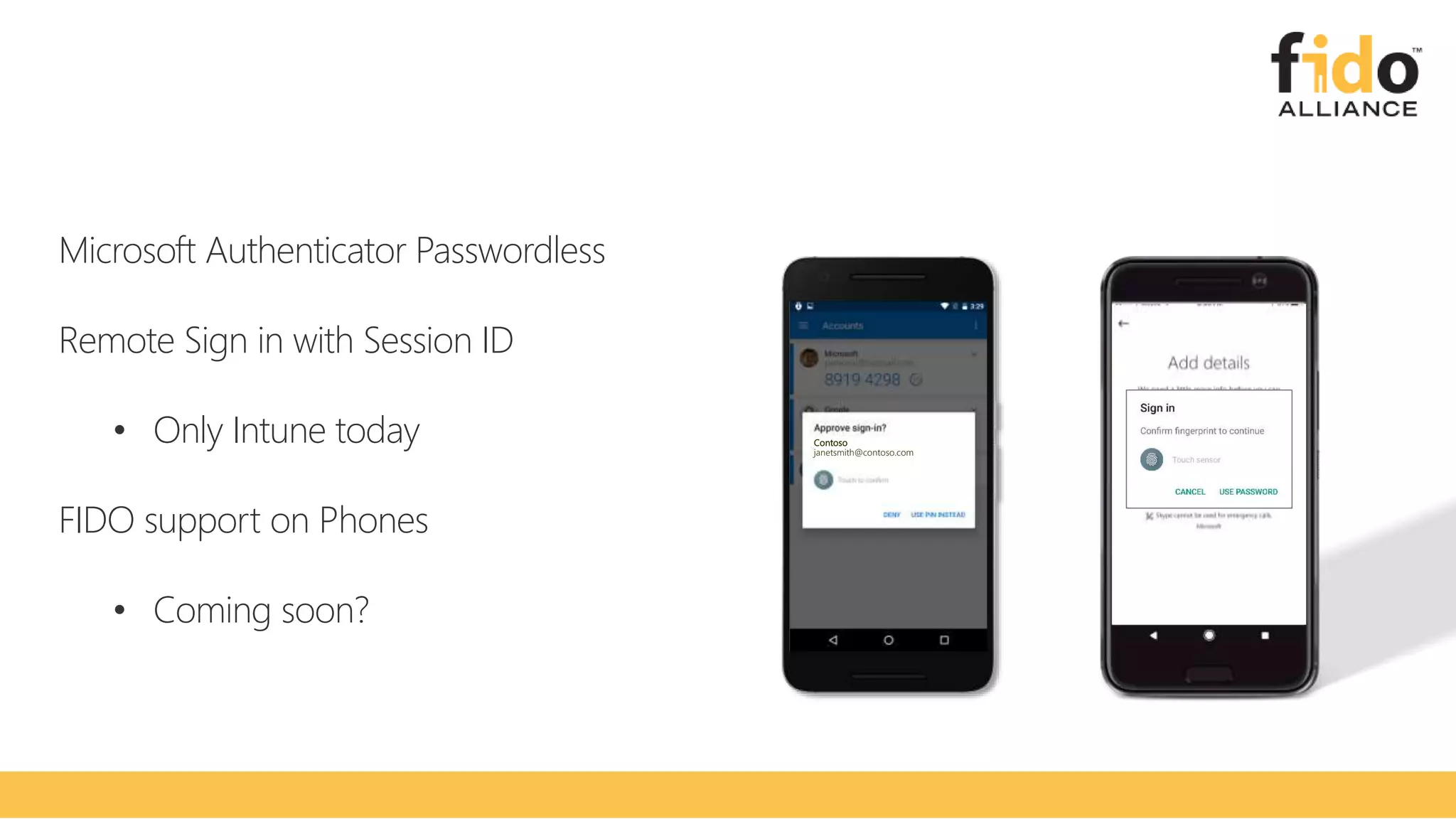
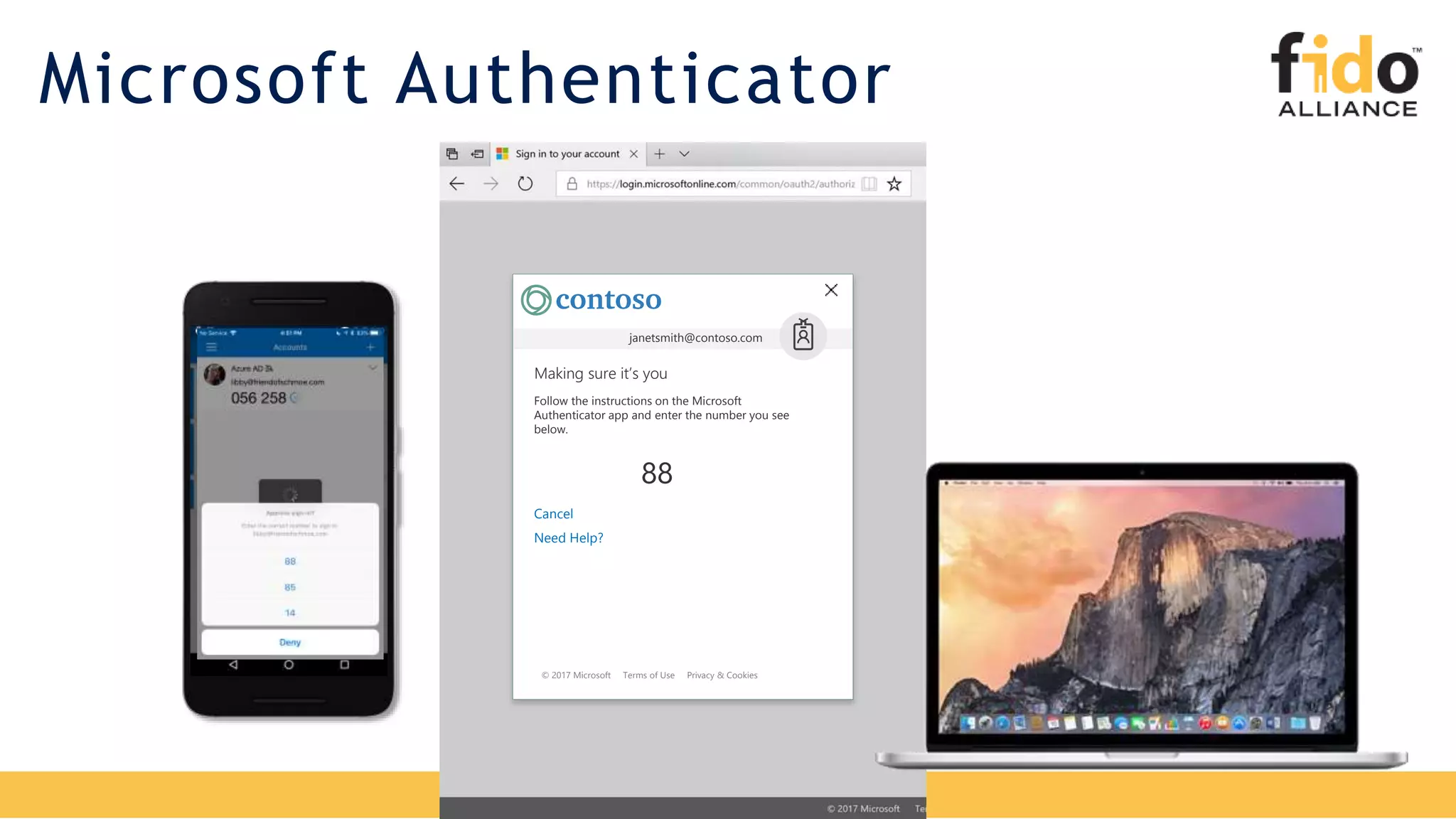
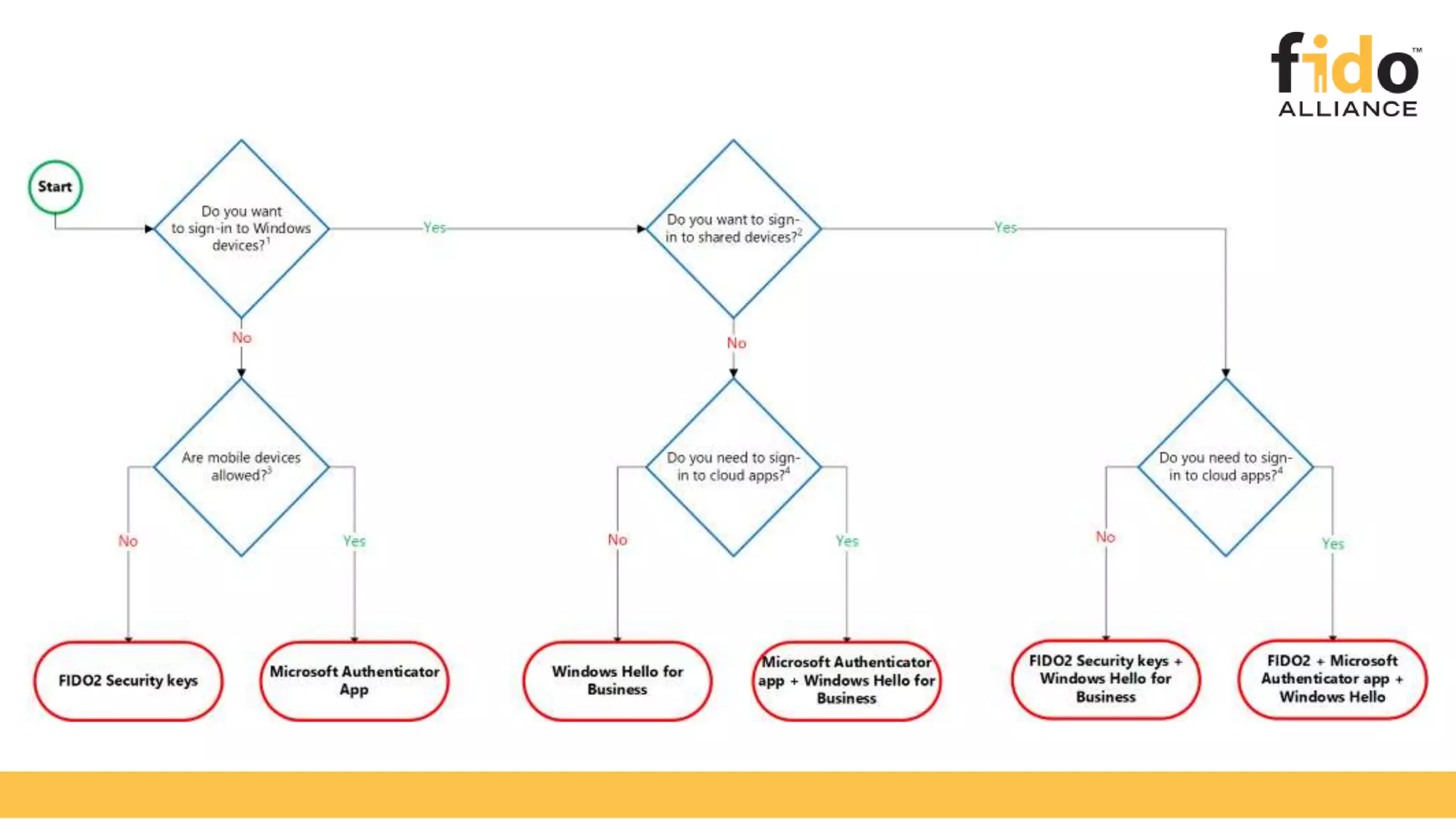
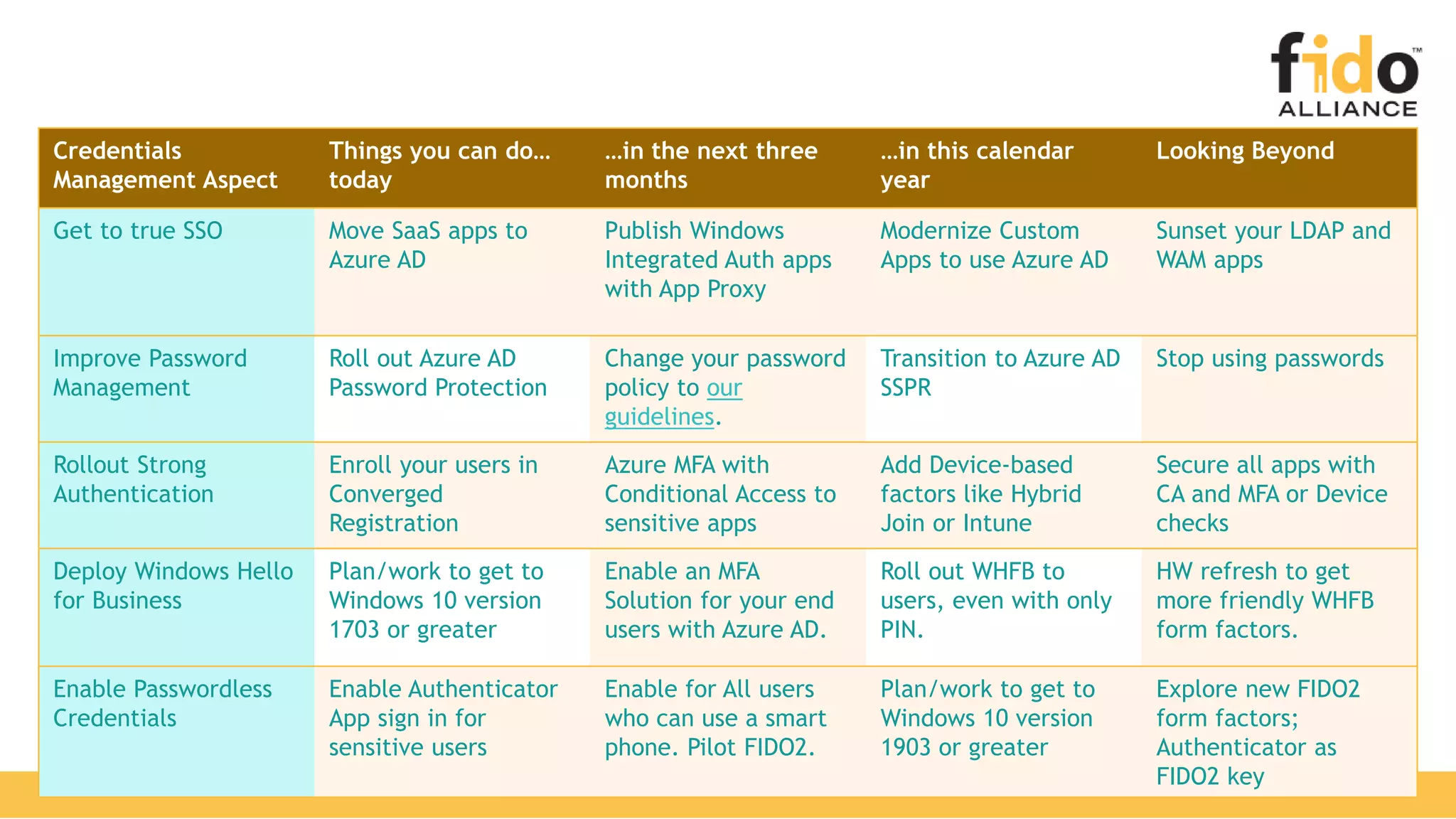
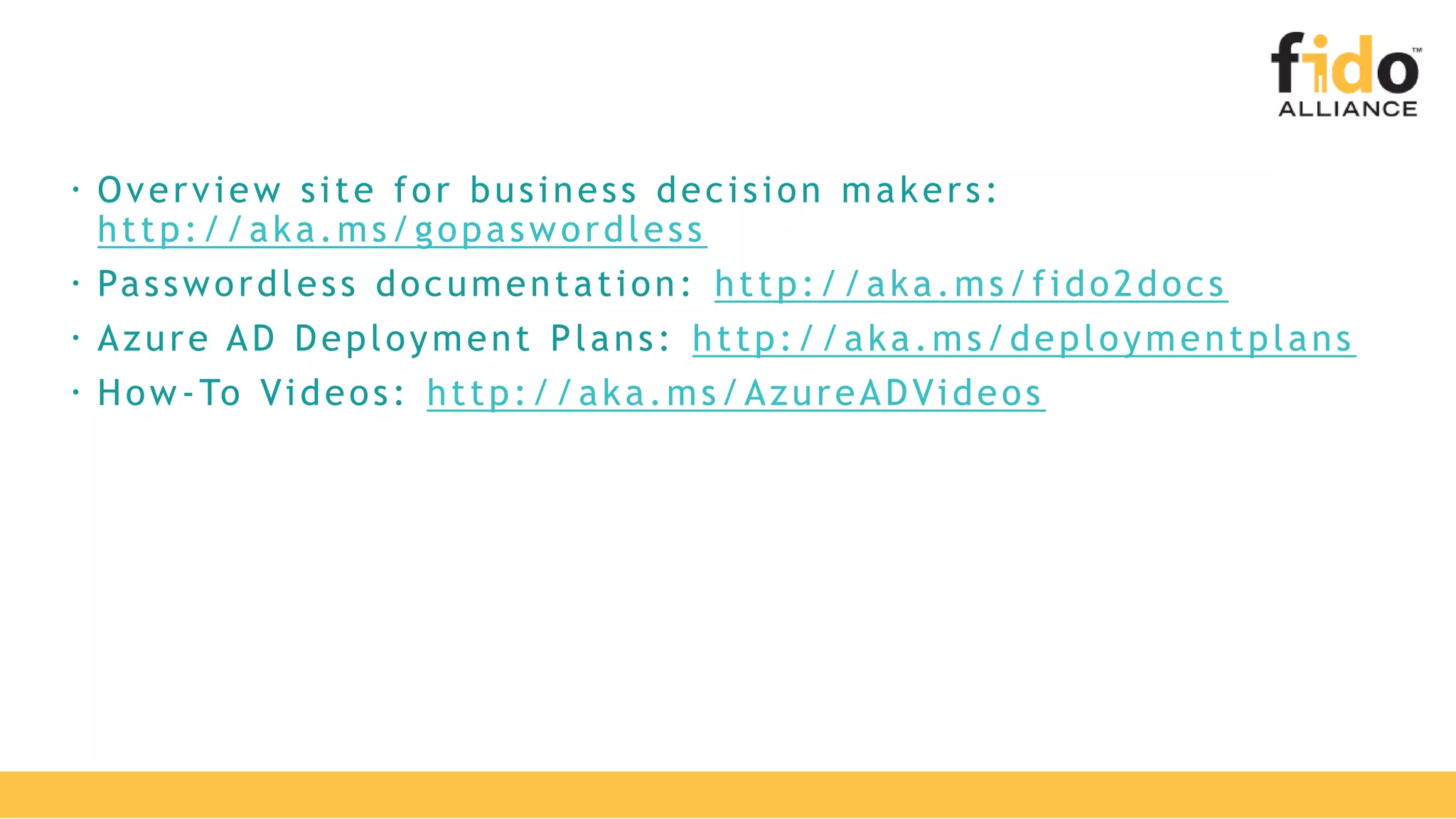
The document discusses Microsoft's strategy for going passwordless. It begins by outlining the problems with passwords, such as increased security incidents and support costs due to forgotten passwords. It then presents Microsoft's four step strategy to achieve the end-user and security promises of being passwordless: 1) deploy password replacement offerings, 2) reduce visible password surface area, 3) transition to passwordless methods, and 4) eliminate passwords from identity directories. Specific passwordless methods discussed include Windows Hello, Microsoft Authenticator, and FIDO2 security keys. The document demonstrates how these work across platforms and provides resources for learning more.