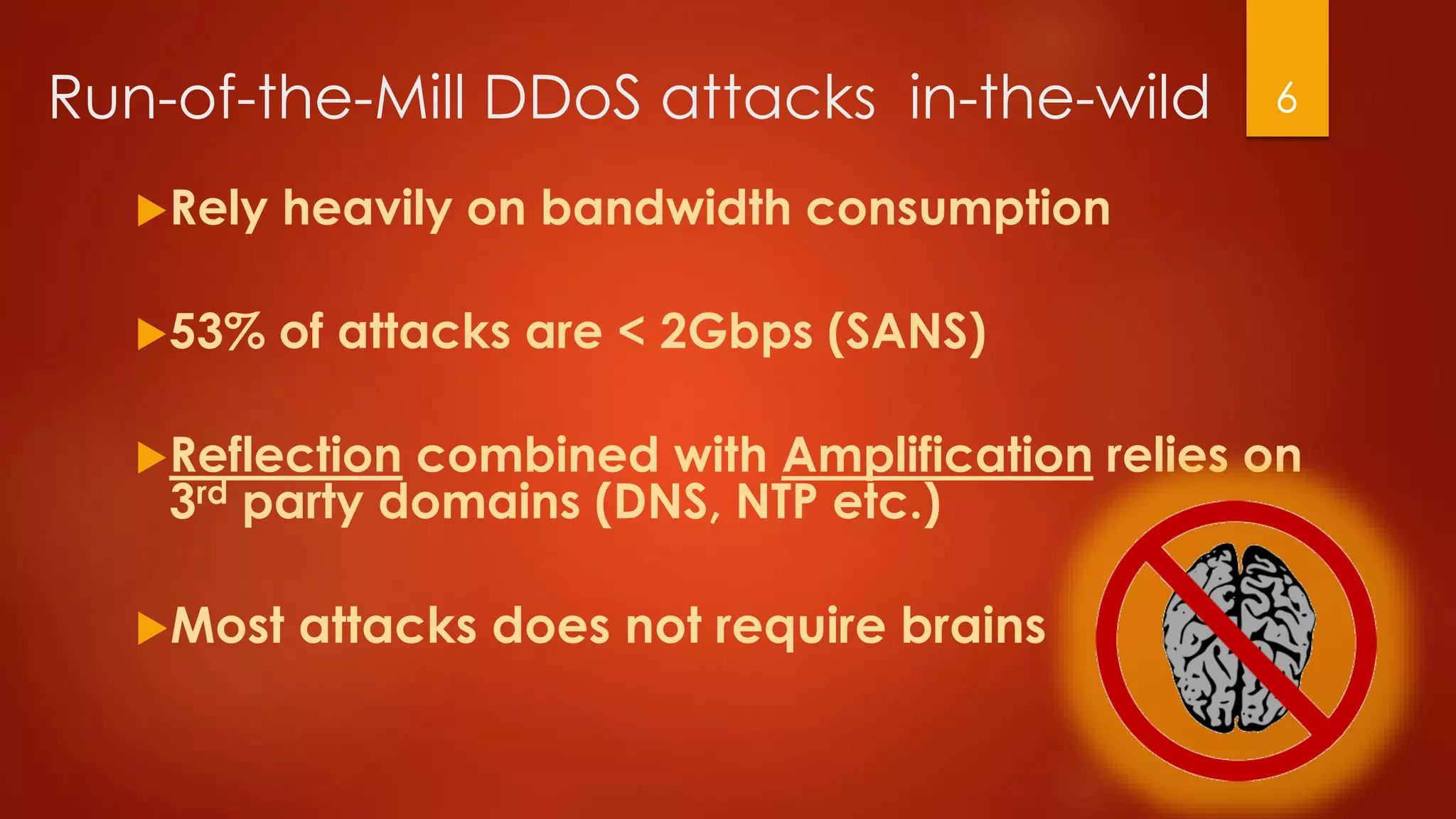
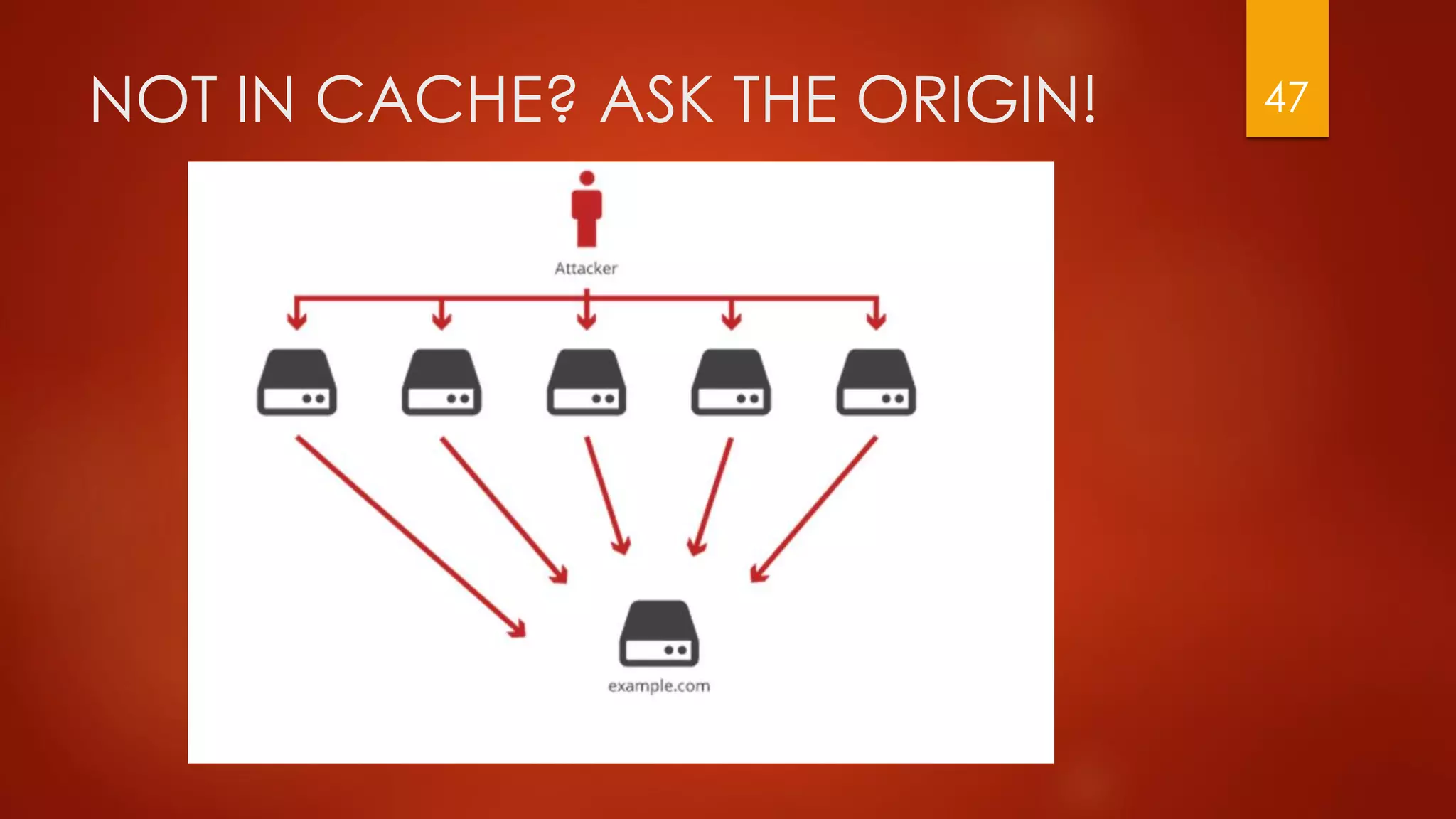
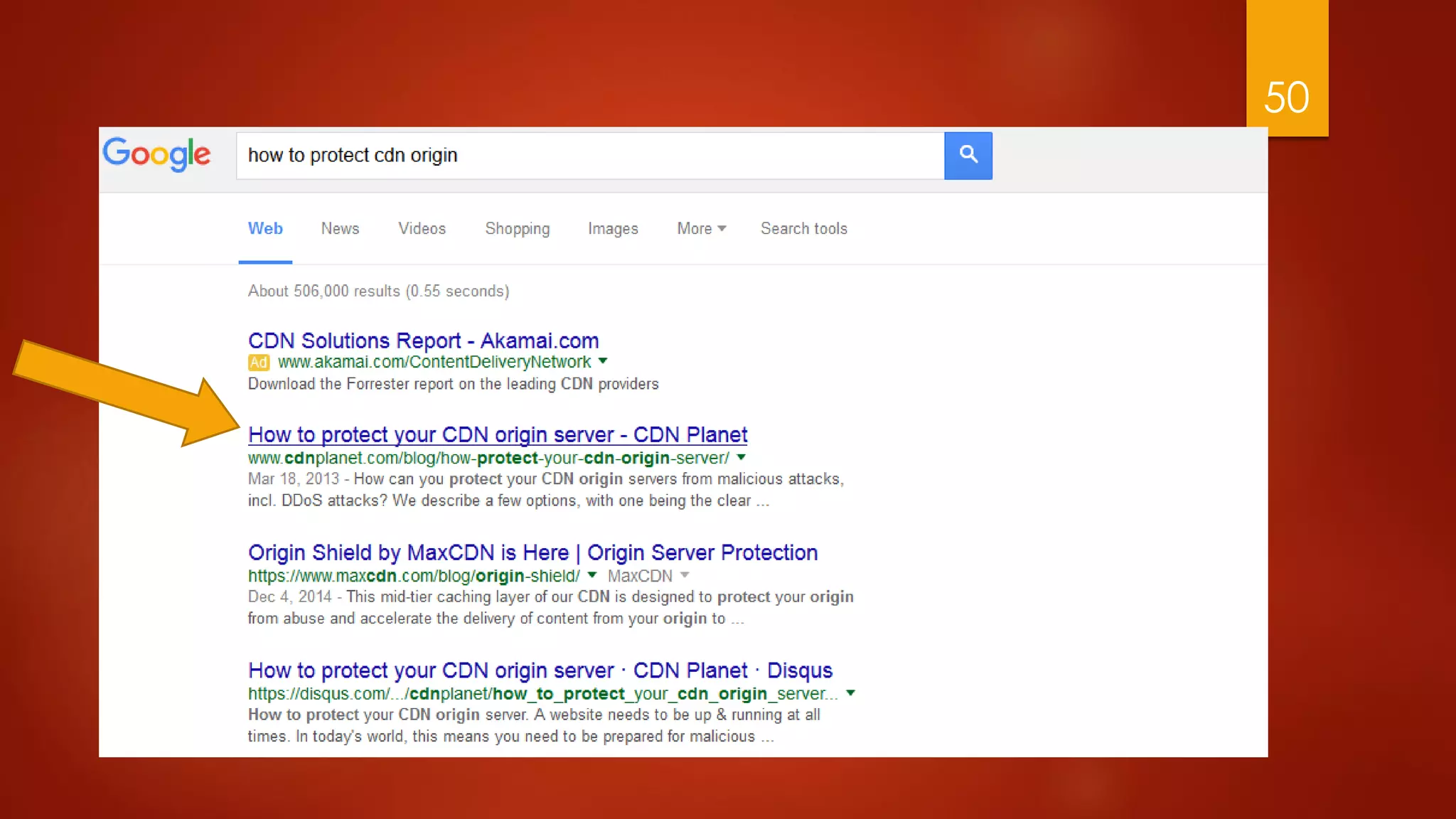
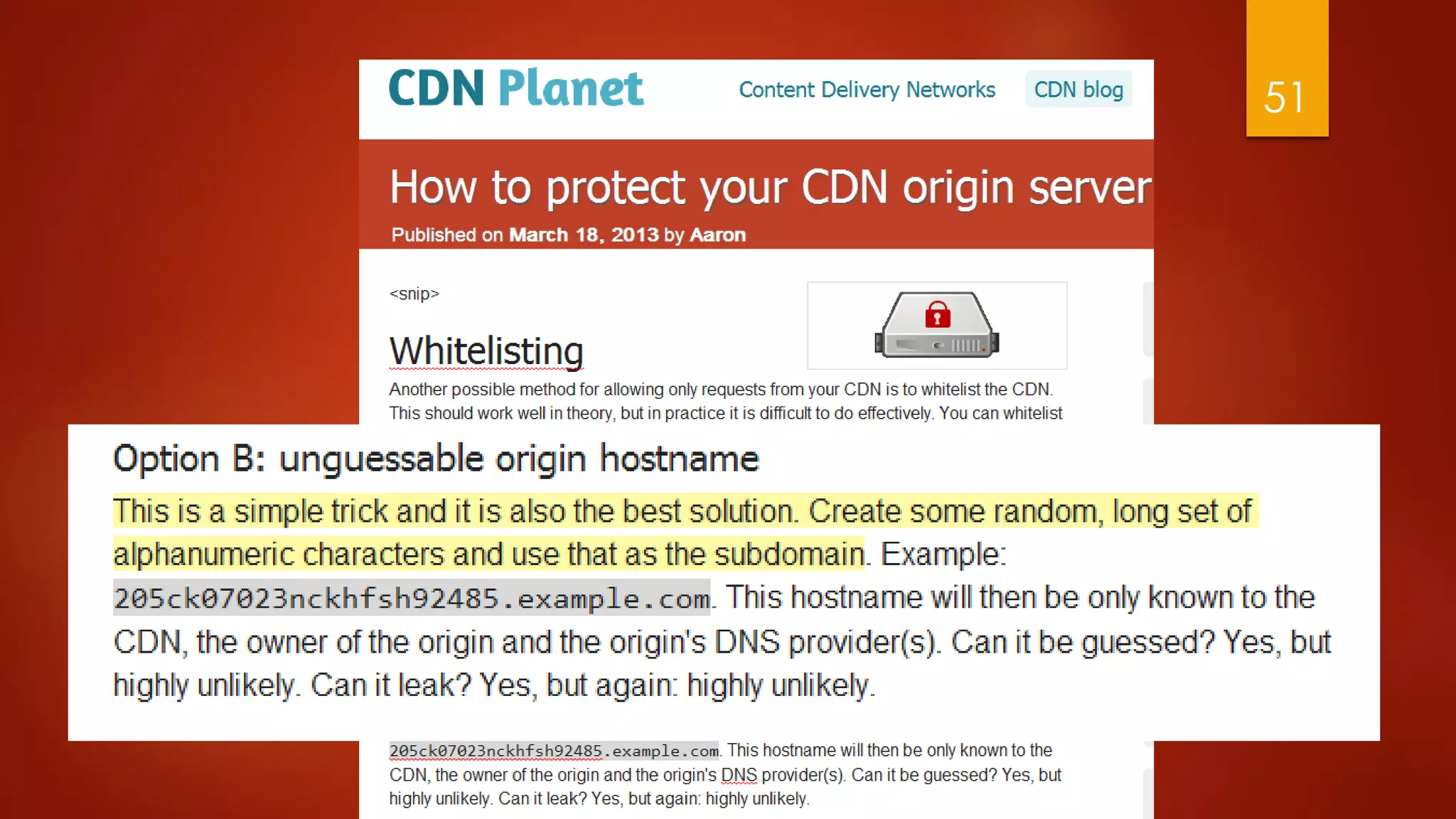
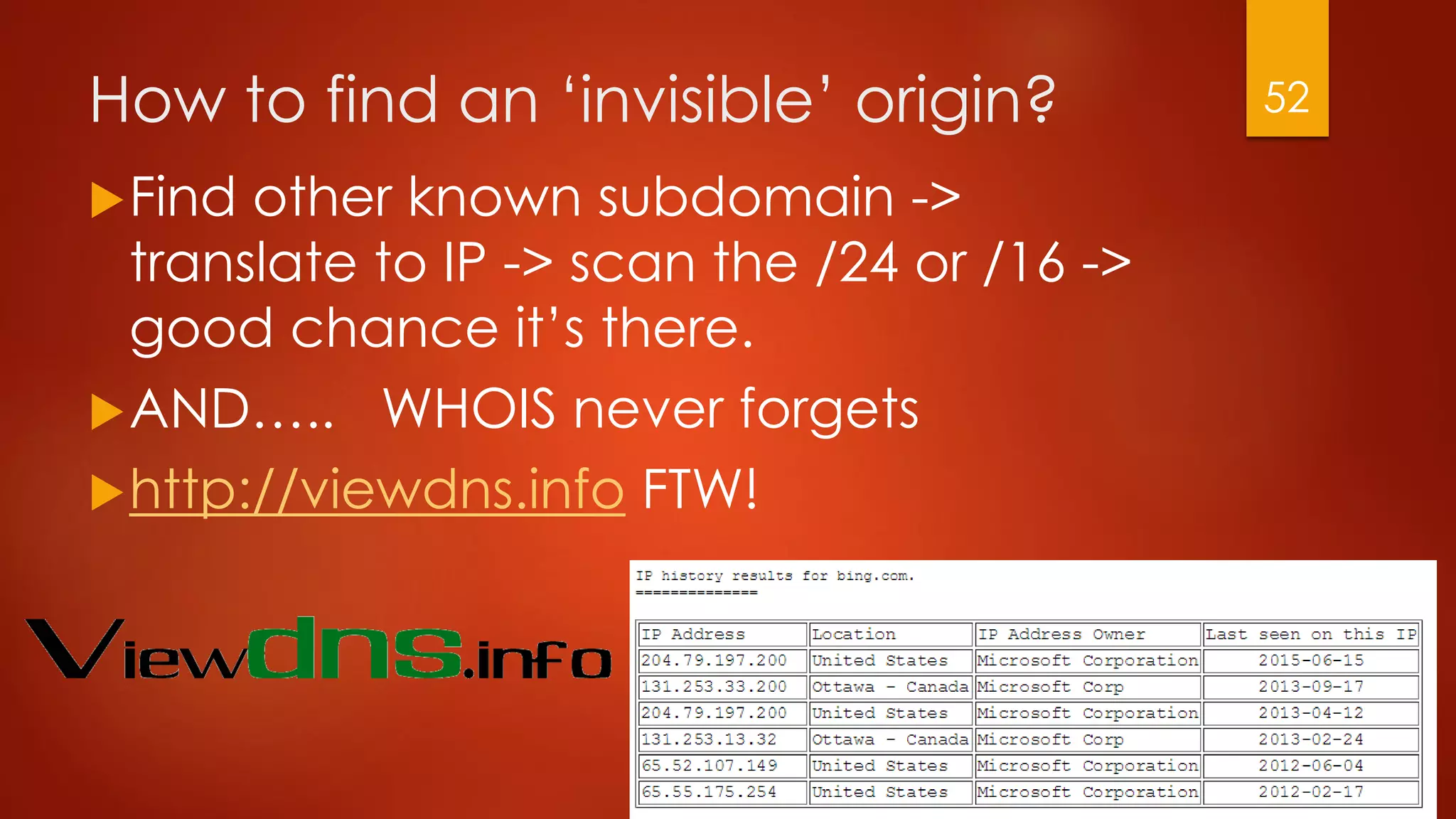
This document discusses strategies for conducting distributed denial-of-service (DDoS) attacks and bypassing mitigation tactics. It presents 10 attack strategies, including targeting backend systems like databases to cause amplification, using reflection techniques, and spoofing large ranges of IP addresses to overwhelm blocklisting defenses. The document also critiques common misconceptions that can leave systems vulnerable, such as not protecting HTTPS traffic or enabling dynamic cloud distribution without origin protection. The overall message is that comprehensive testing and planning is needed to effectively mitigate DDoS attacks.