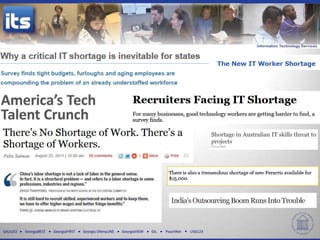
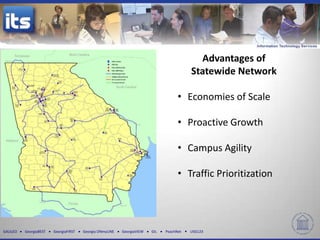
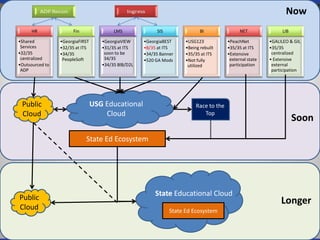
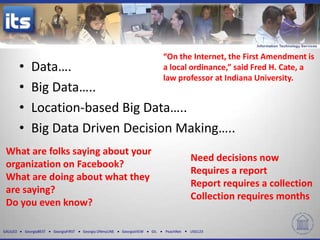
The document discusses four key trends in information technology affecting organizational security and privacy: a shortage of IT personnel, the rise of cloud services, consumerization of IT, and the importance of data-driven decision-making. It highlights the implications of these trends, such as increased hiring challenges, the need for enhanced data protection, and the effects of Bring Your Own Device policies on campus culture. The document emphasizes the complexities of managing corporate data in a rapidly evolving IT landscape.