- CARE USA implemented Fortinet network security appliances across its offices globally to simplify and centralize its previously convoluted and localized ICT systems.
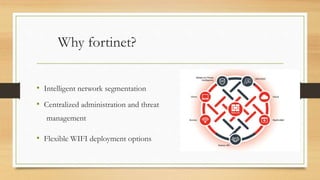
- The Fortinet appliances provide capabilities such as network segmentation, centralized threat management, application control and web filtering to improve security. They also enable remote management, dynamic reporting and VPN access.
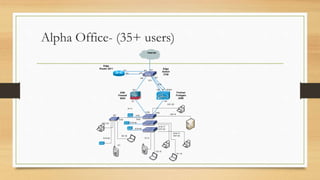
- The solution deployed Fortigate appliances tailored to office sizes, with models for medium/enterprise and small offices. This provided standardized setups for firewall policies, QoS, UTM security services and WIFI access across CARE USA's network.