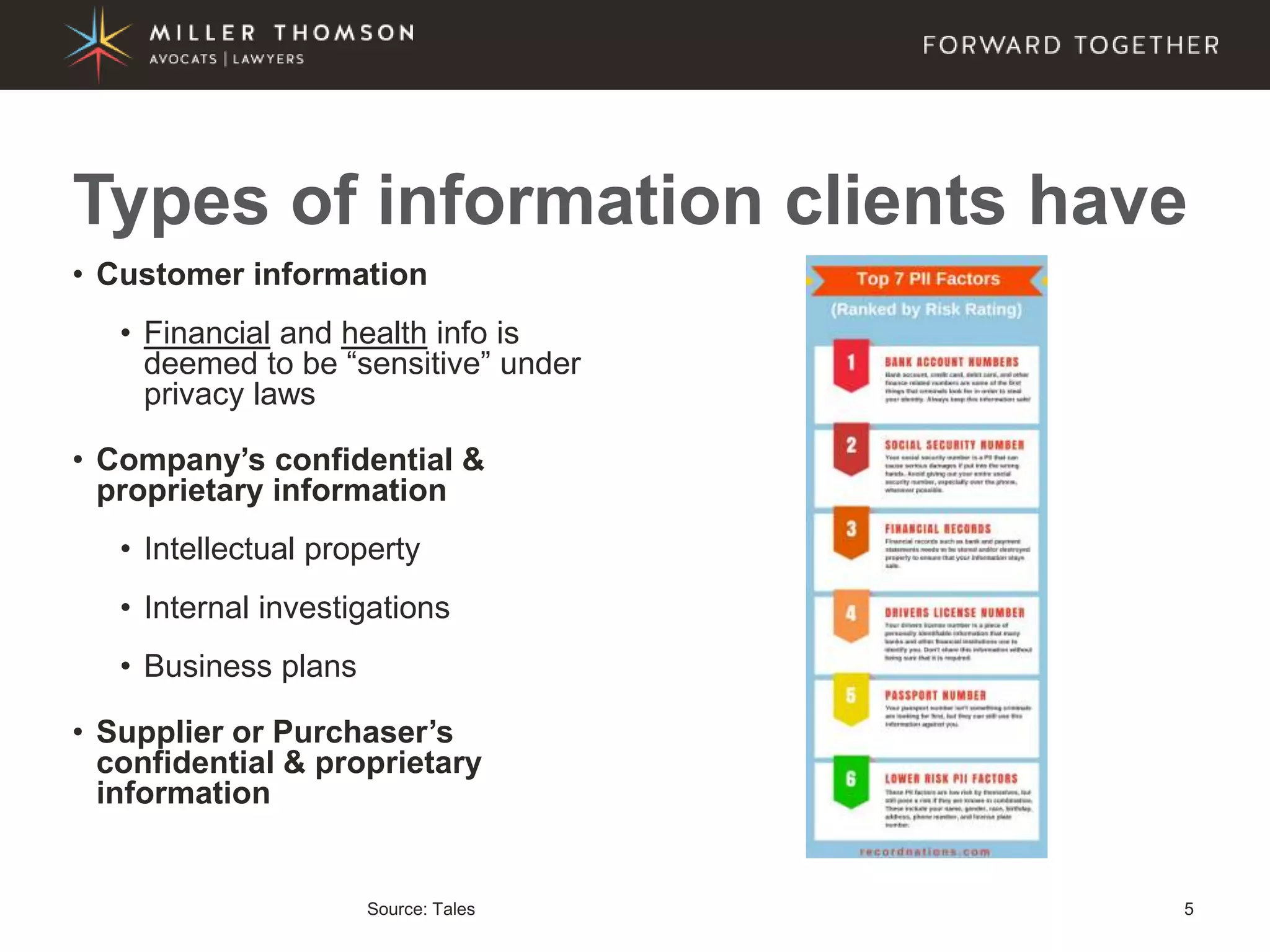
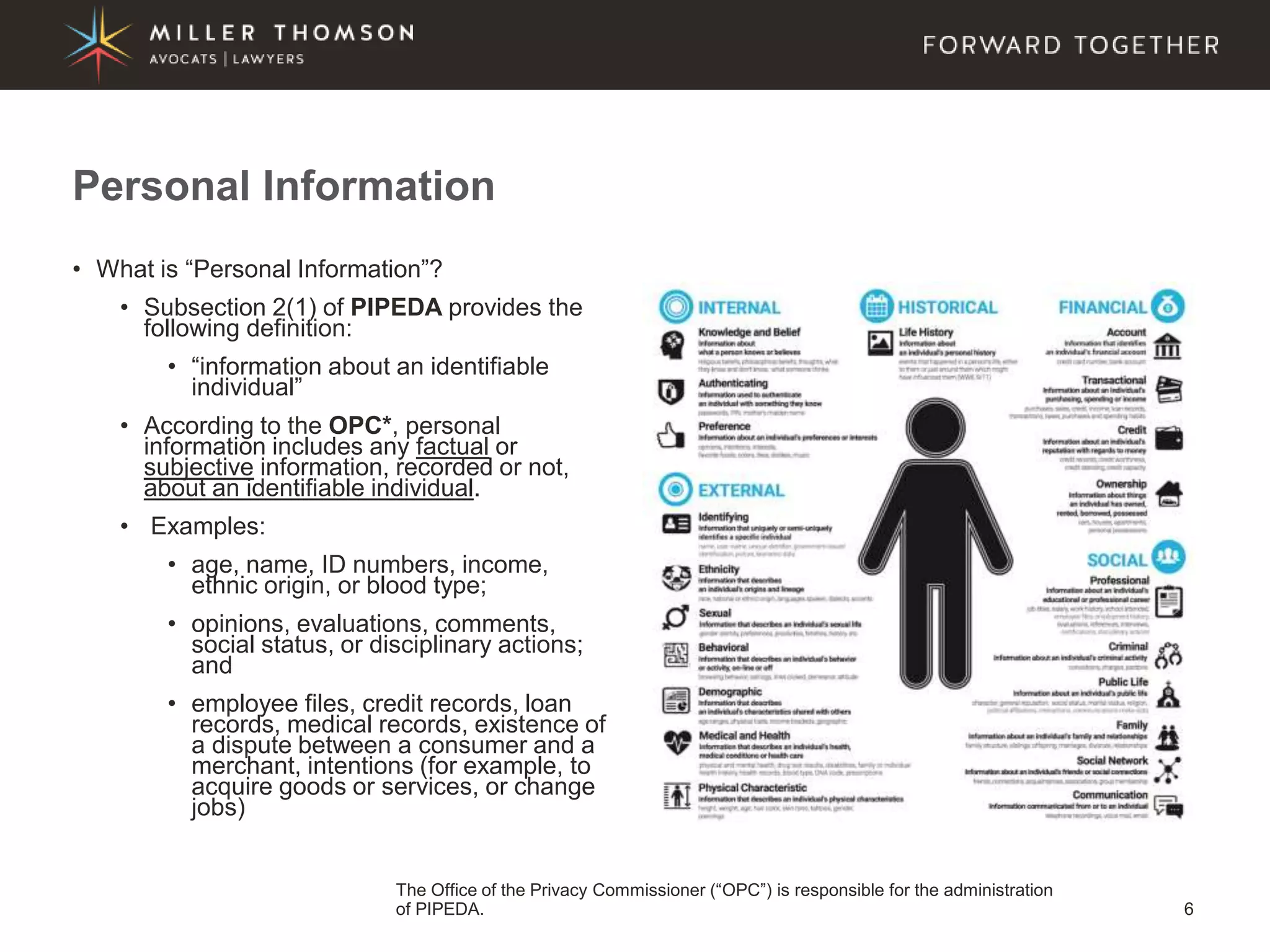
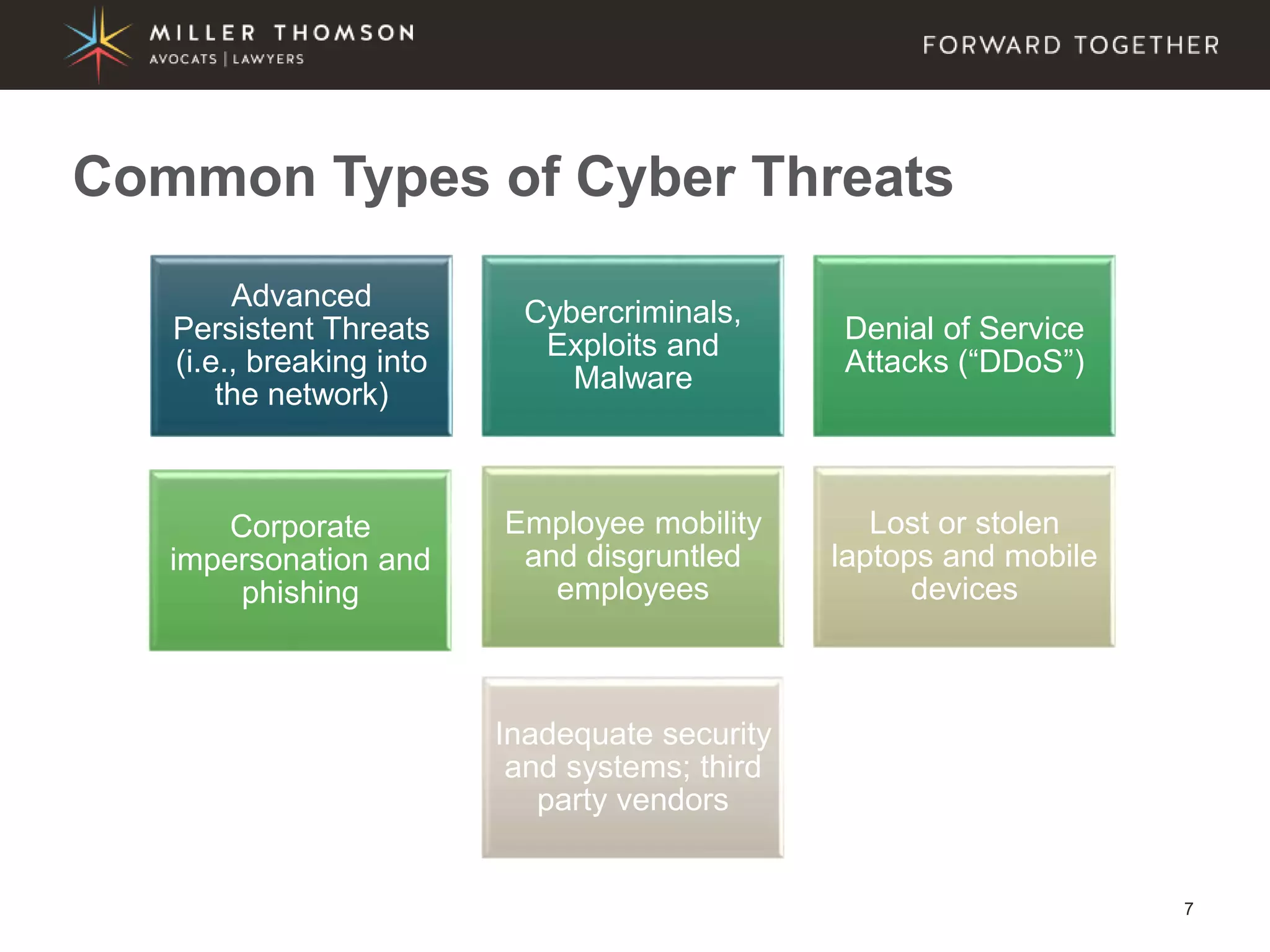
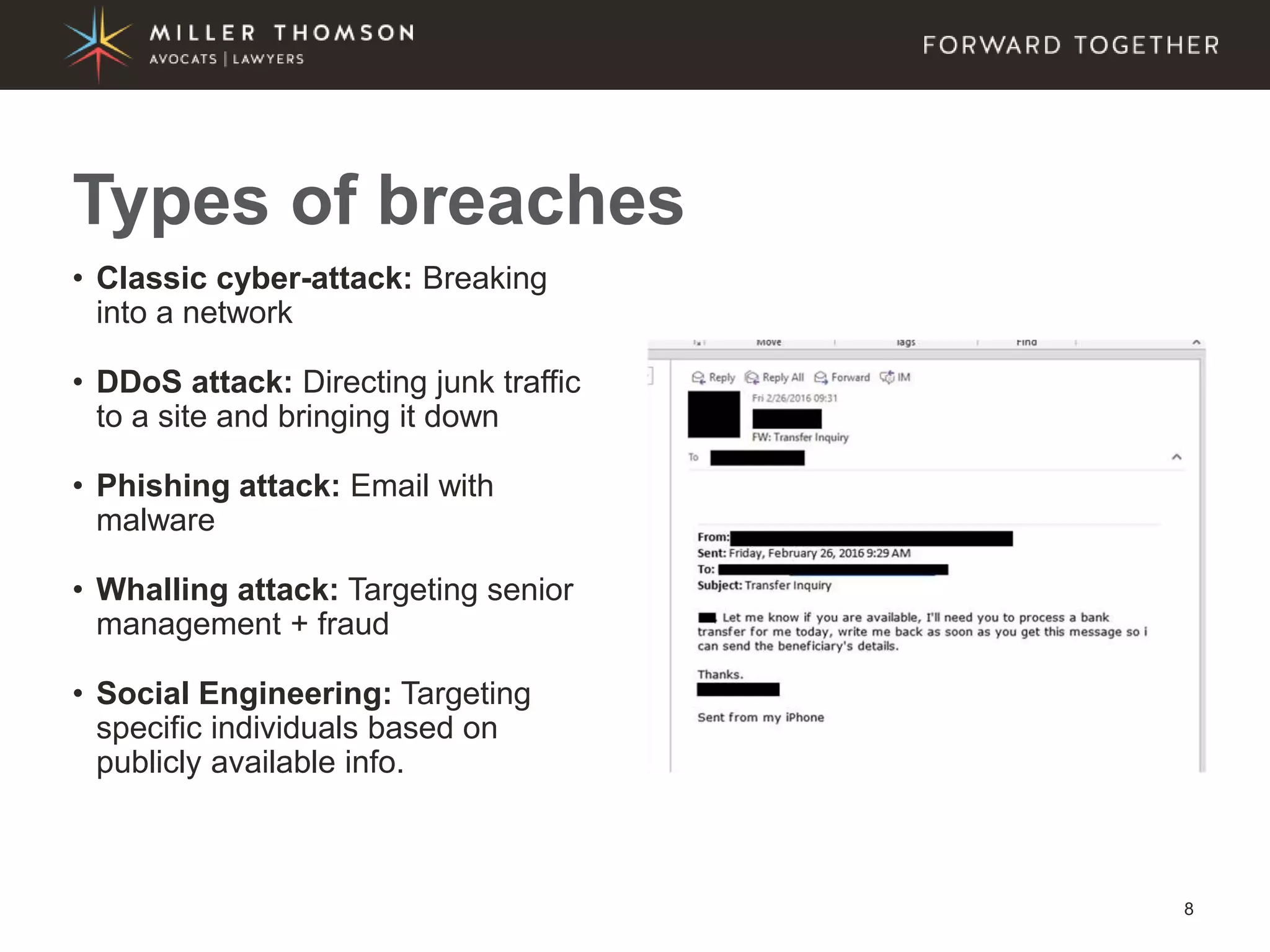
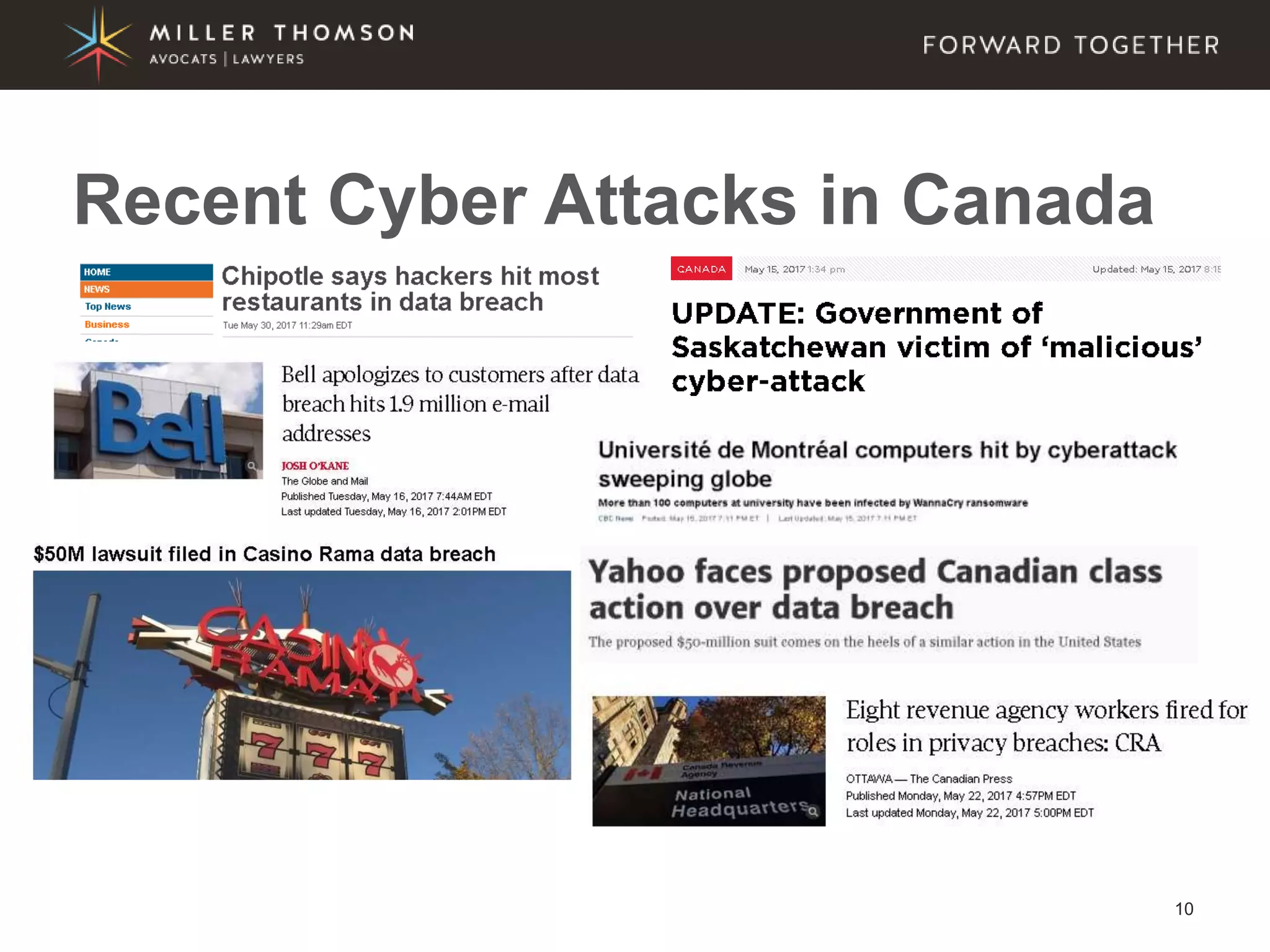
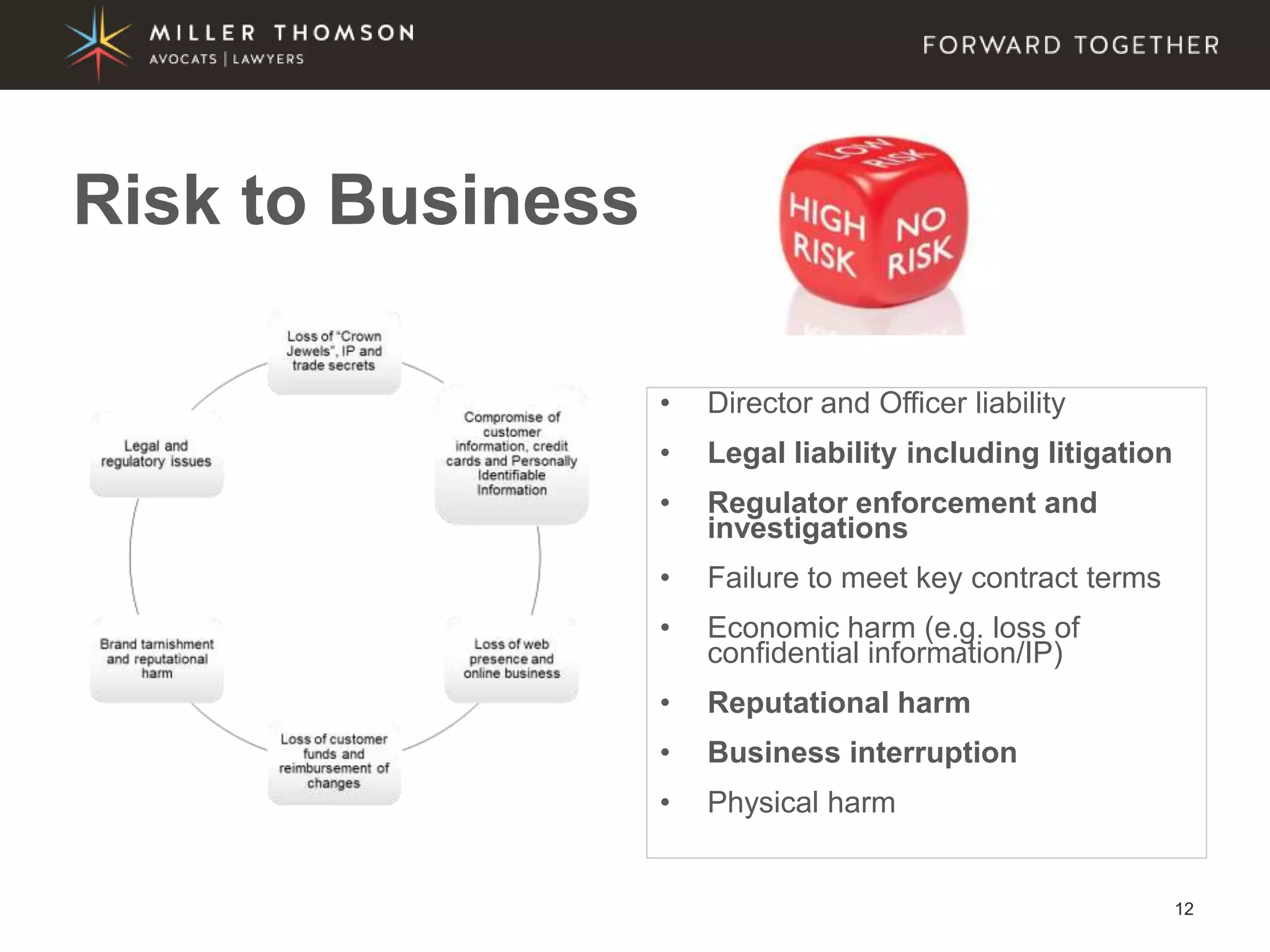
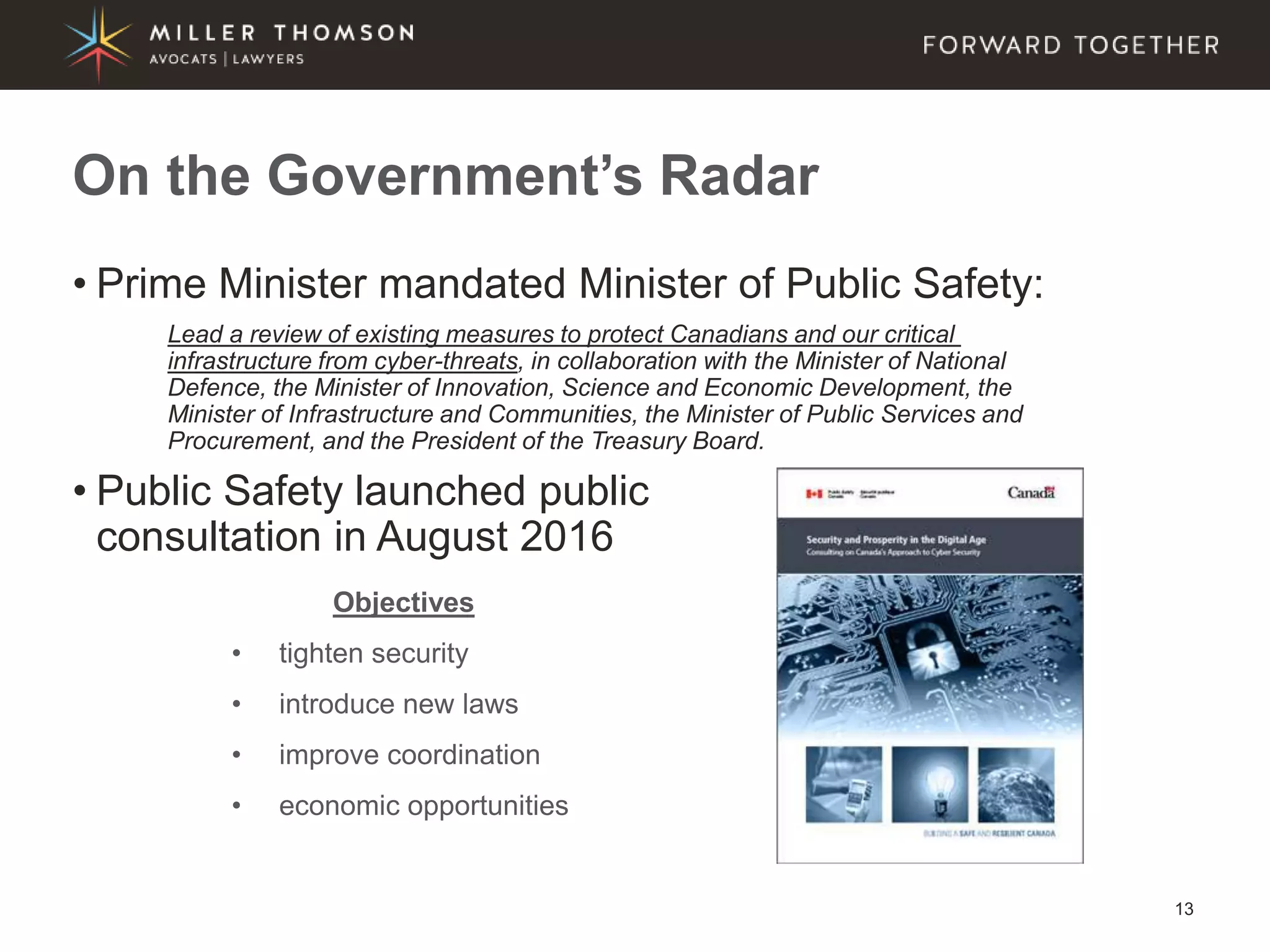
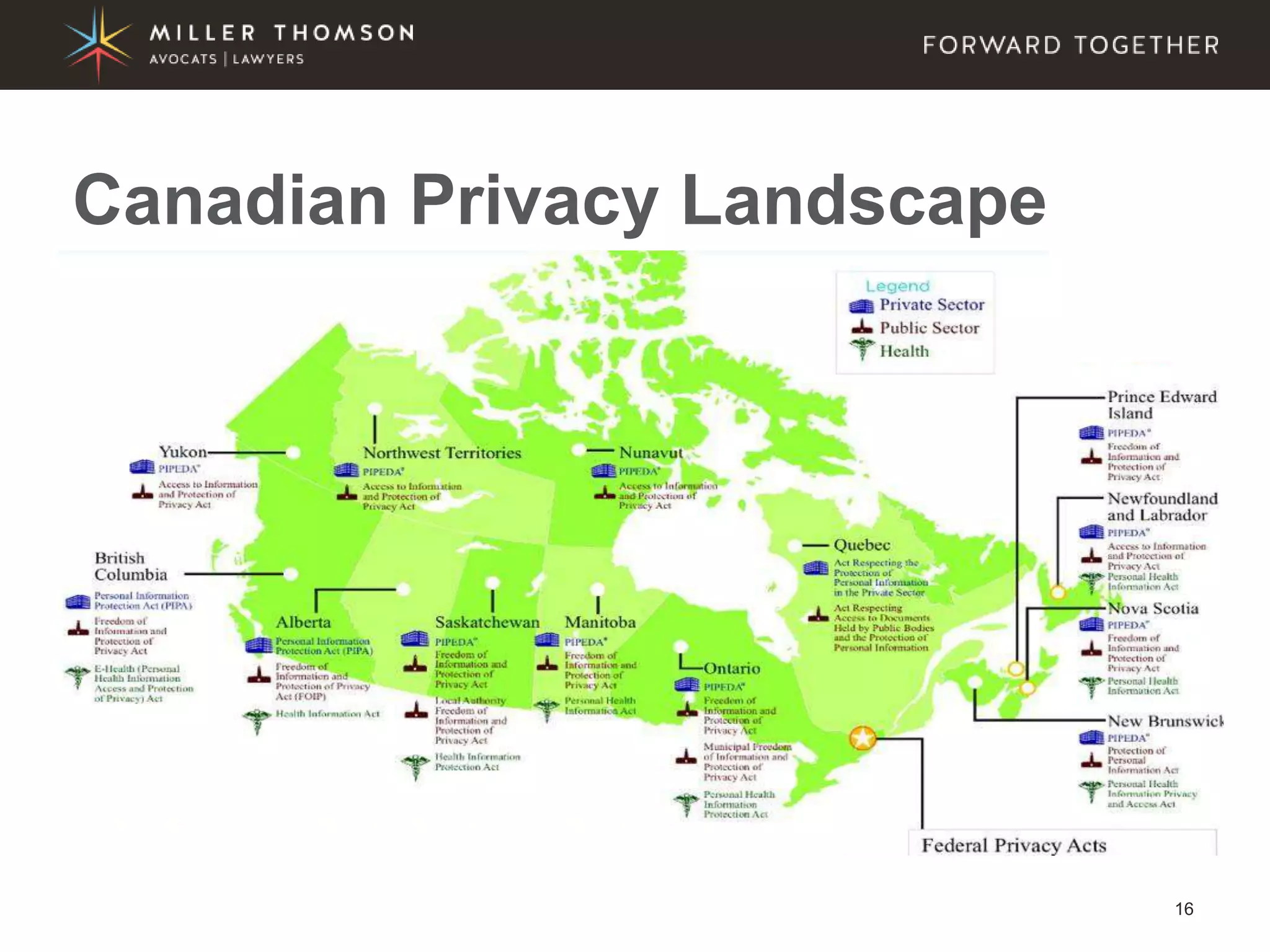
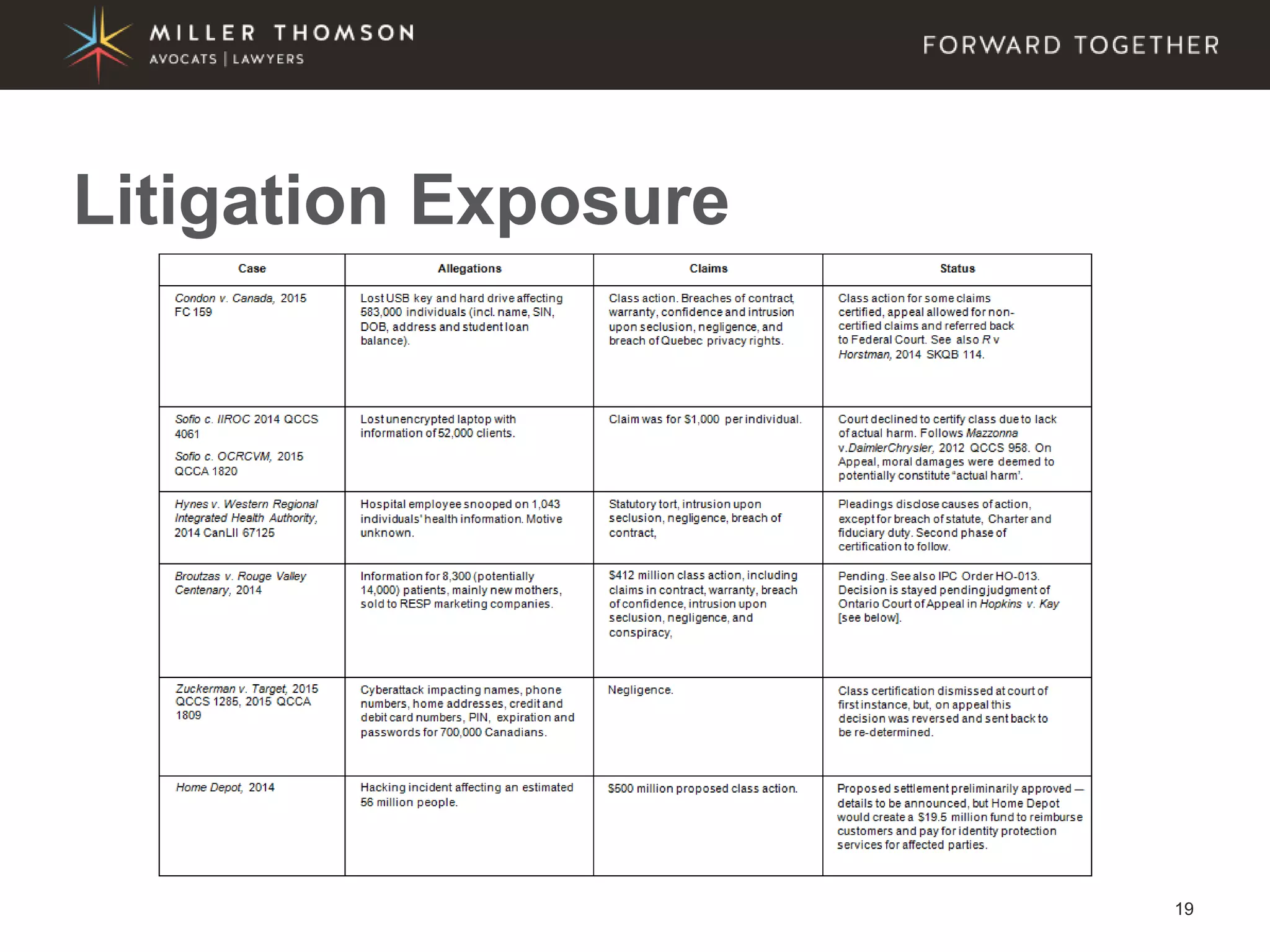
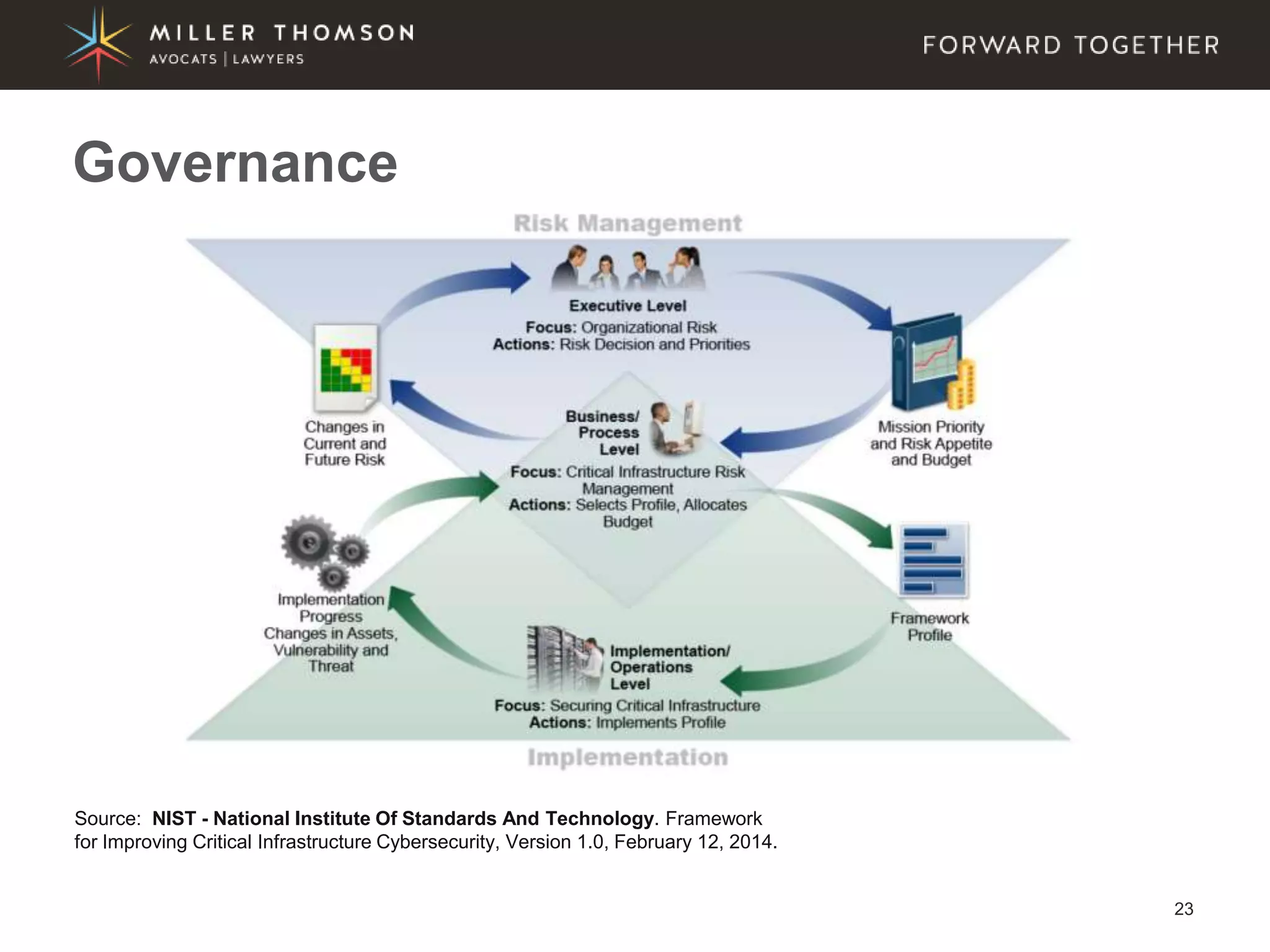
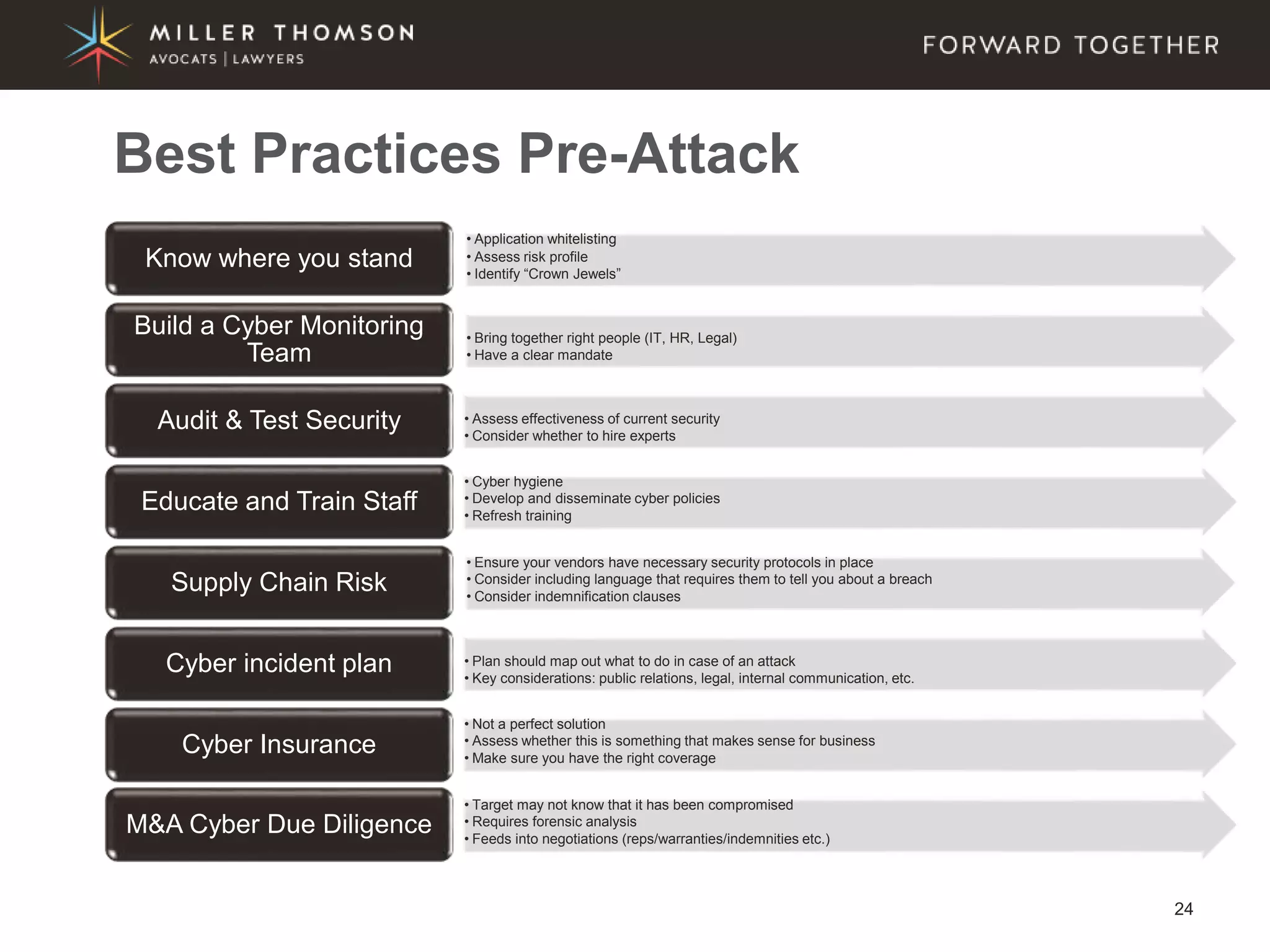
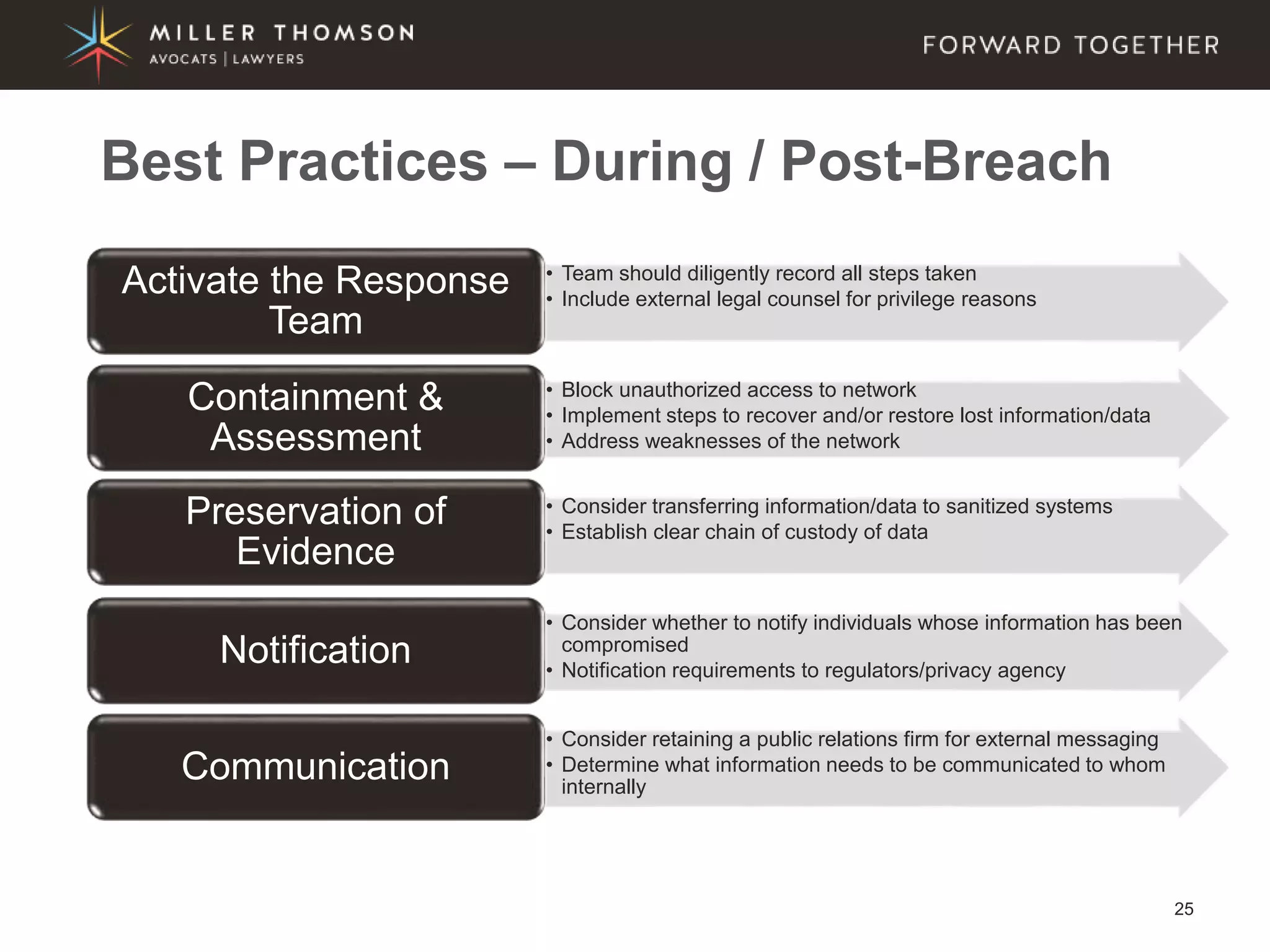
The document covers essential aspects of cybersecurity, including definitions, types of threats, recent statistics on cyber crime, and the legal landscape regarding data breaches in Canada and the U.S. It emphasizes the importance of implementing best practices for data security and outlines potential liabilities and legal implications for organizations. The document also highlights evolving legal standards and the need for organizations to prepare for and respond to cyber threats effectively.