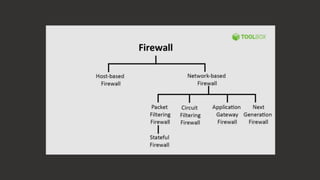
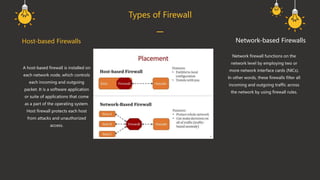
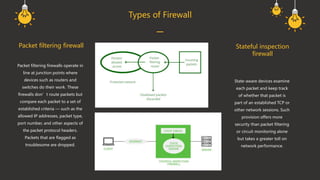
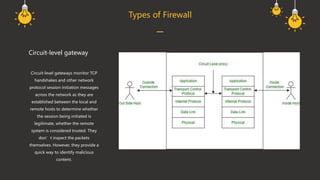
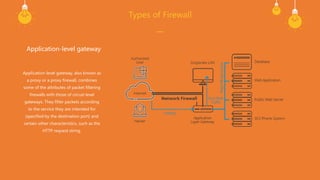
A firewall is a cybersecurity tool that monitors and filters network traffic based on predefined security rules to prevent unauthorized access and attacks. It operates through architecture components such as network policy, advanced authentication, packet filtering, and application gateways. The document outlines various firewall types, including host-based, network-based, packet filtering, stateful inspection, circuit-level gateways, next-generation firewalls, and application-level gateways, each serving different security functions.