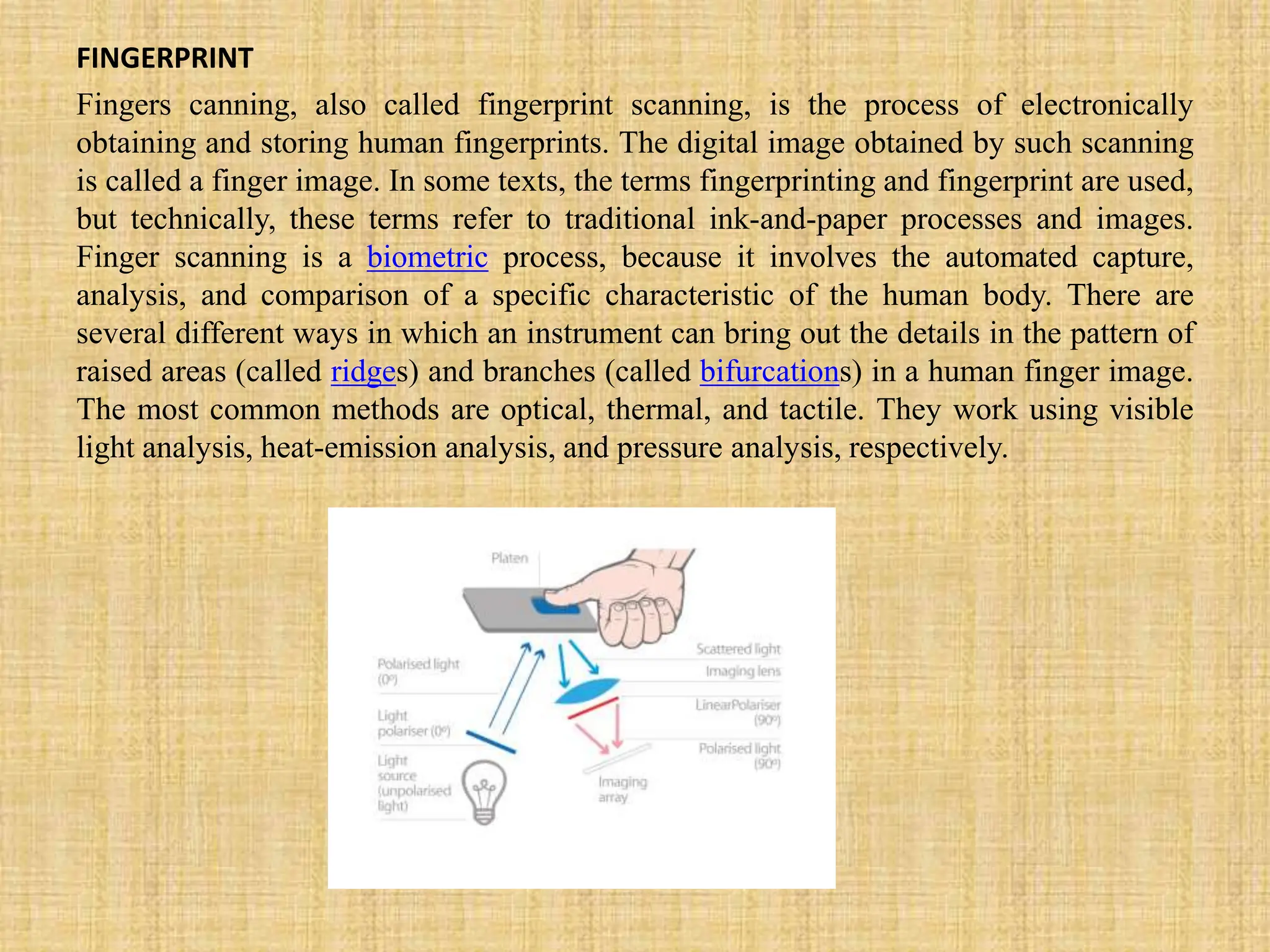
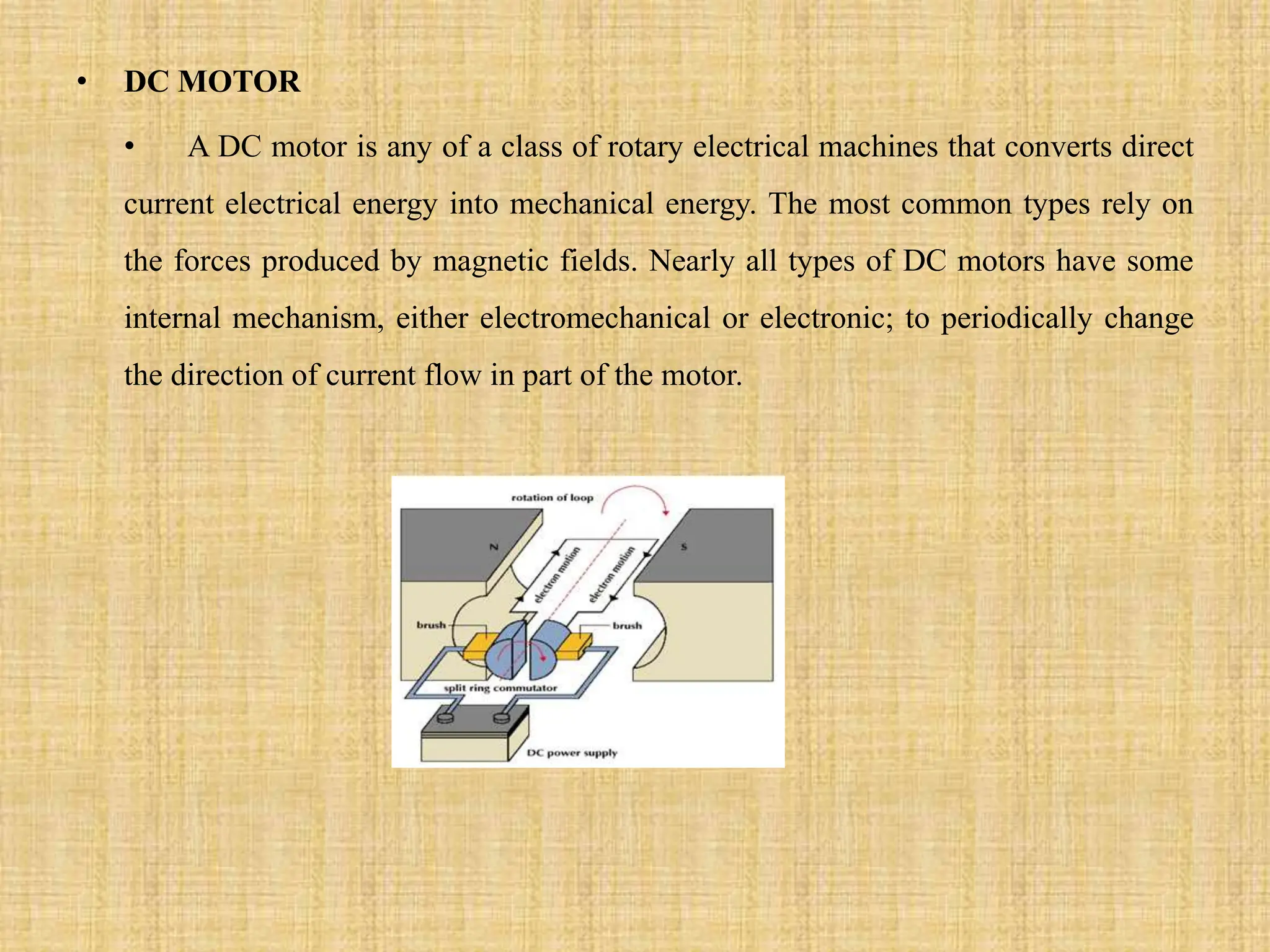
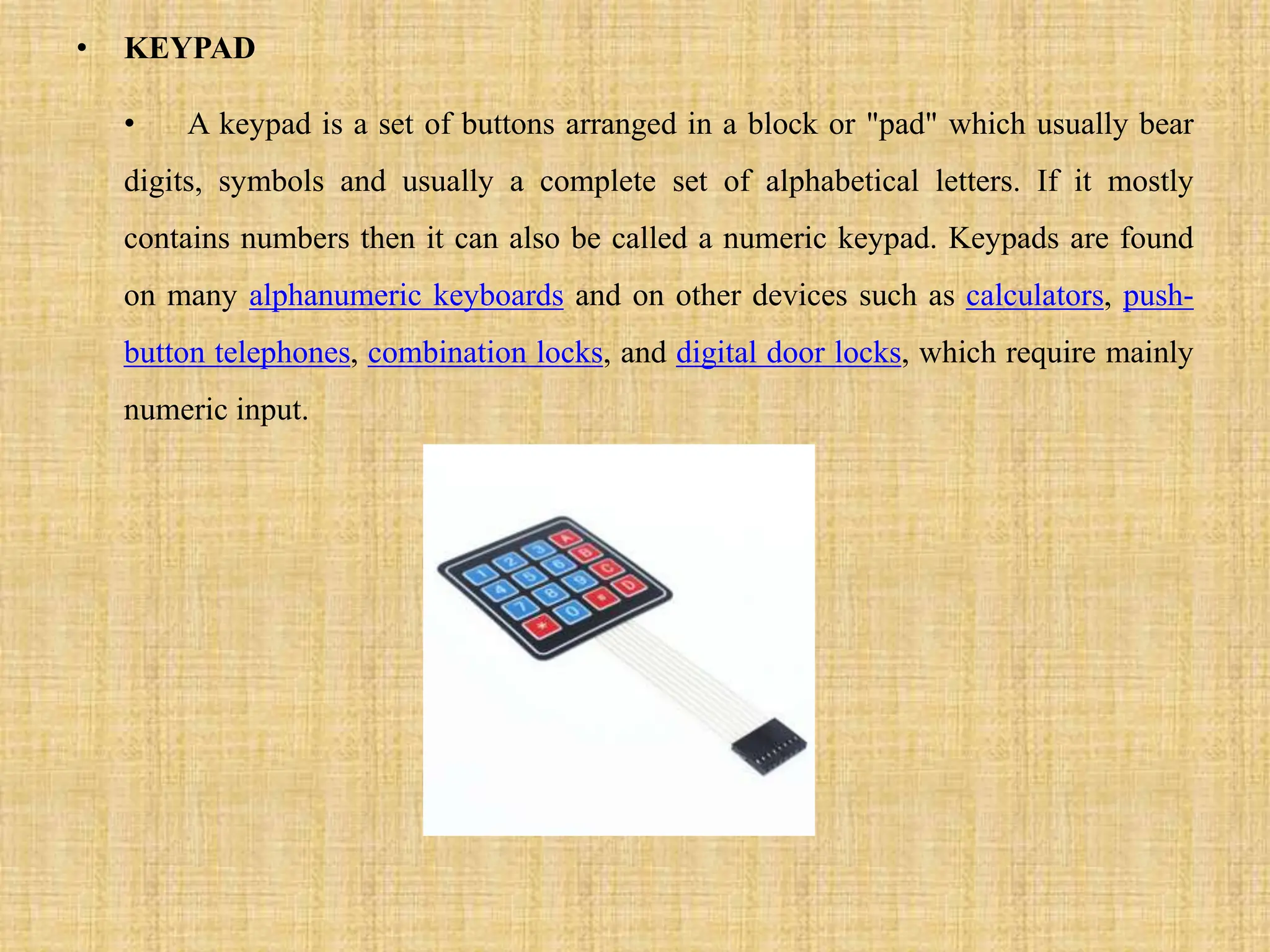
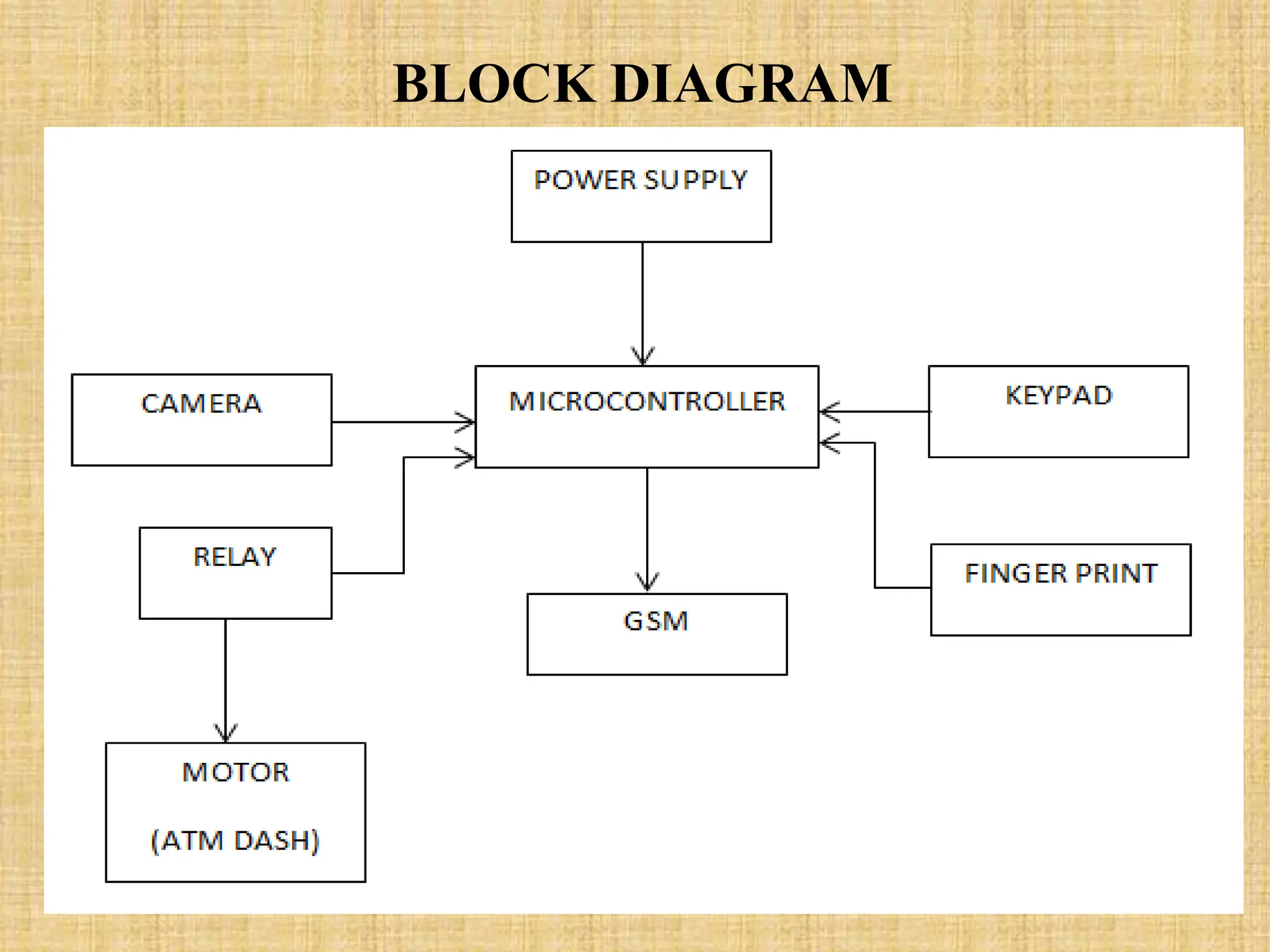
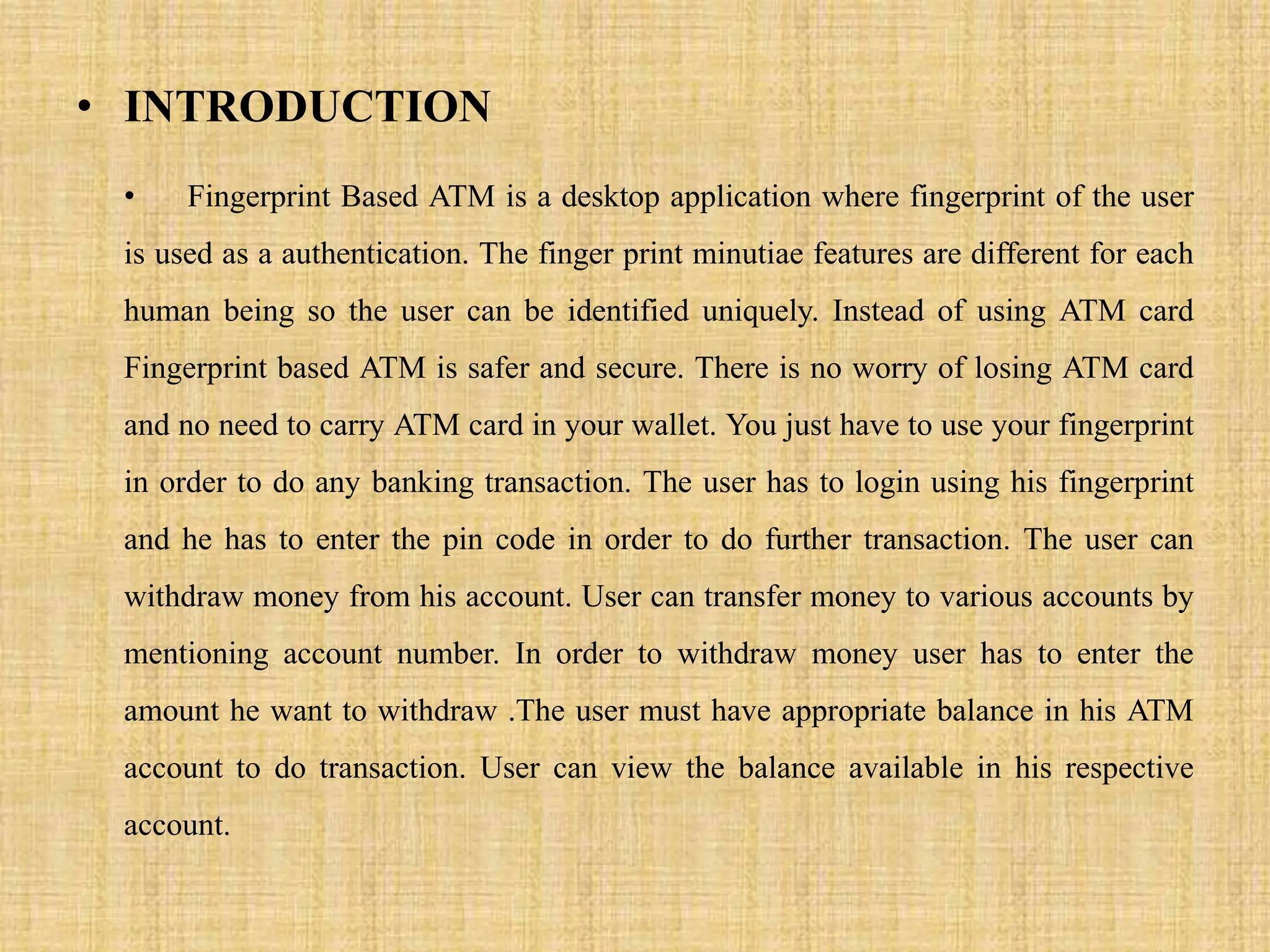
This document describes a fingerprint-based ATM system that uses fingerprint scanning as authentication for transactions. The system stores users' fingerprint data in an Aadhaar database. During transactions, the user's fingerprint is scanned and matched against the stored data. If a match is found, the transaction is completed. Otherwise, the transaction is cancelled for security. The document outlines the proposed system design, including modules for fingerprint scanning, iris detection, database storage, and transaction authorization based on biometric authentication. It concludes that the fingerprint-based system allows for secure and easy-to-use ATM transactions.





![• LED
A light-emitting diode (LED) is a two-lead semiconductor light source. It is a pn-
junction diode, which emits light when activated.]When a suitable voltage is
applied to the leads, electrons are able to recombine with electron holes within the
device, releasing energy in the form of photons. This effect is called
electroluminescence, and the color of the light is determined by the energy band
gap of the semiconductor.](https://image.slidesharecdn.com/fingerprintbasedatmsystem02-240229073838-87c3b0a5/75/FINGERPRINT-BASED-ATM-SYSTEM-13-2048.jpg)