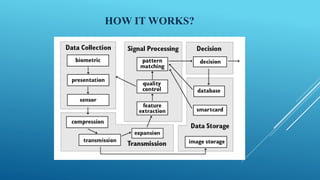
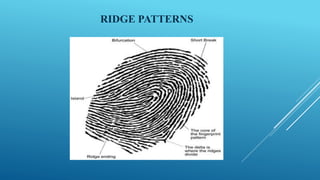
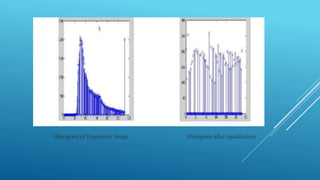
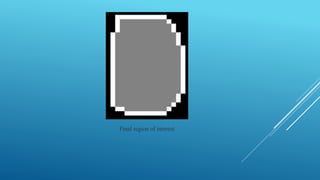
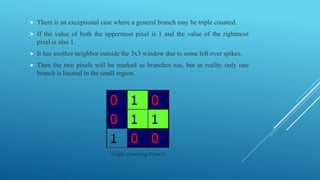
This document summarizes a study on different fingerprint recognition techniques for designing and implementing a lock using an Arduino. It discusses fingerprint verification as an important biometric technique for personal identification. The study describes the design and implementation of a prototype identity authentication system using fingerprint recognition to authenticate individuals. It reviews the literature on fingerprint identification dating back to the 17th century and discusses techniques such as minutiae extraction and matching that have been developed. The document outlines the methodology used in the study, including collecting fingerprint data, pre-processing images, segmenting regions of interest, extracting minutiae features, and referencing related work.