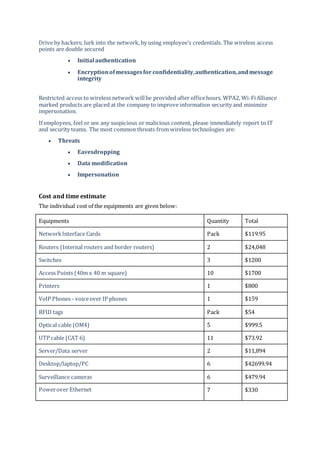
The document discusses a network solution proposed by SNM Networks for ABC Technologies. Key requirements for ABC include setting up wired and wireless networks connecting offices in Georgia and New York. The proposed solution includes a WAN connecting the two sites, wireless access points, POE, servers, switches, routers, IP phones and surveillance cameras. SNM Networks will install all hardware components within 12 weeks for under $50,000. The network aims to provide mobility, connectivity and future scalability for ABC Technologies.