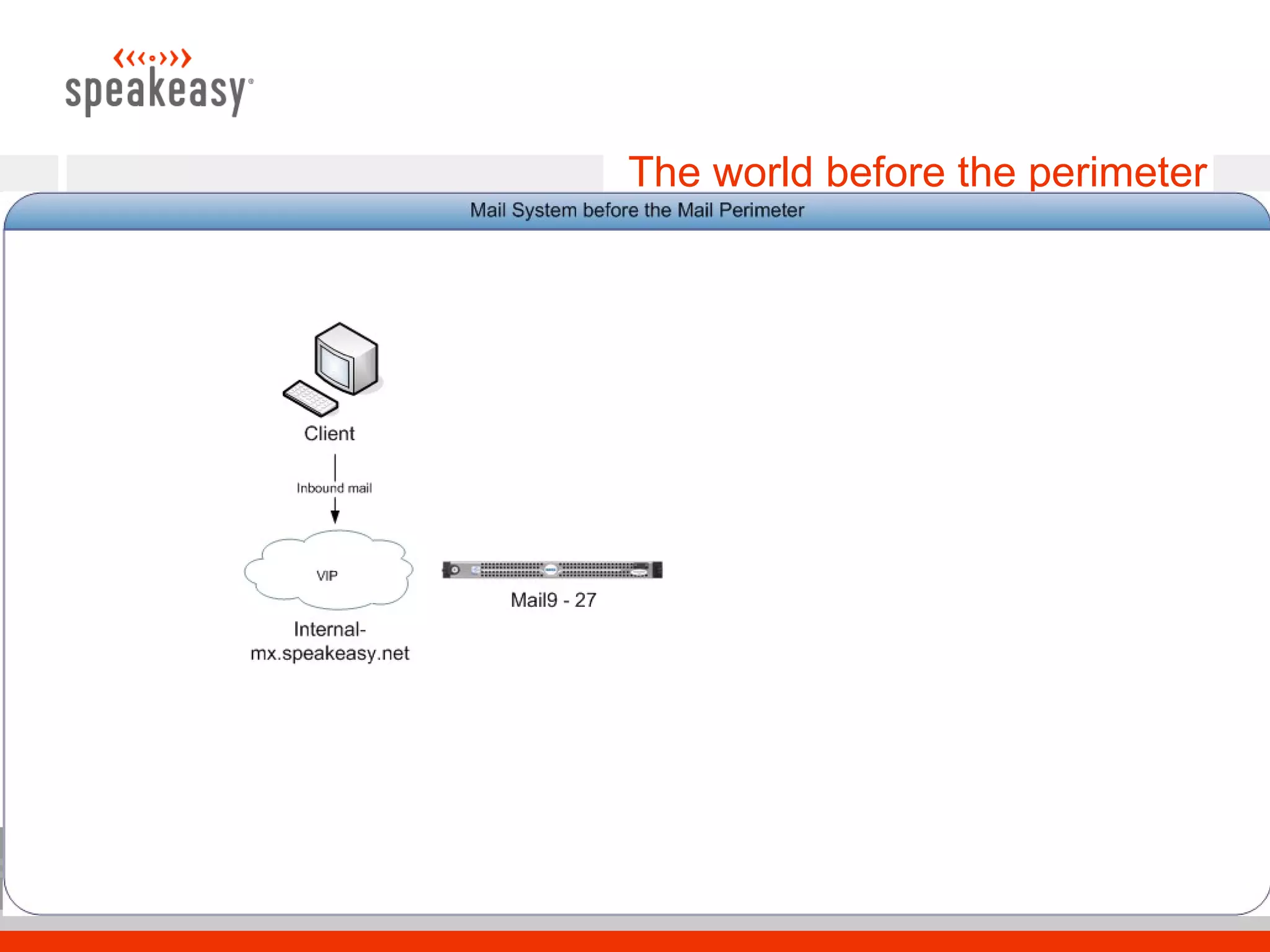
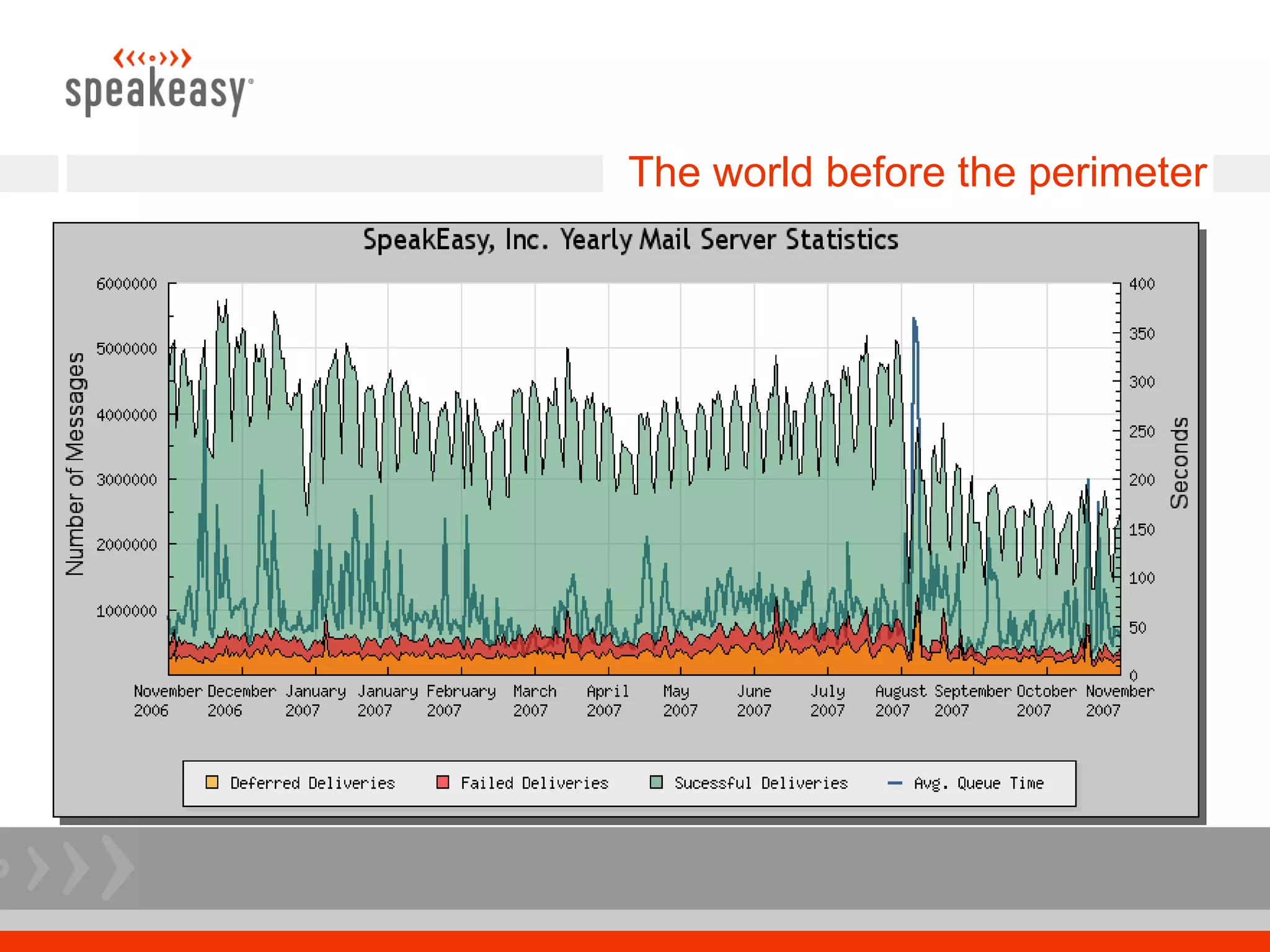
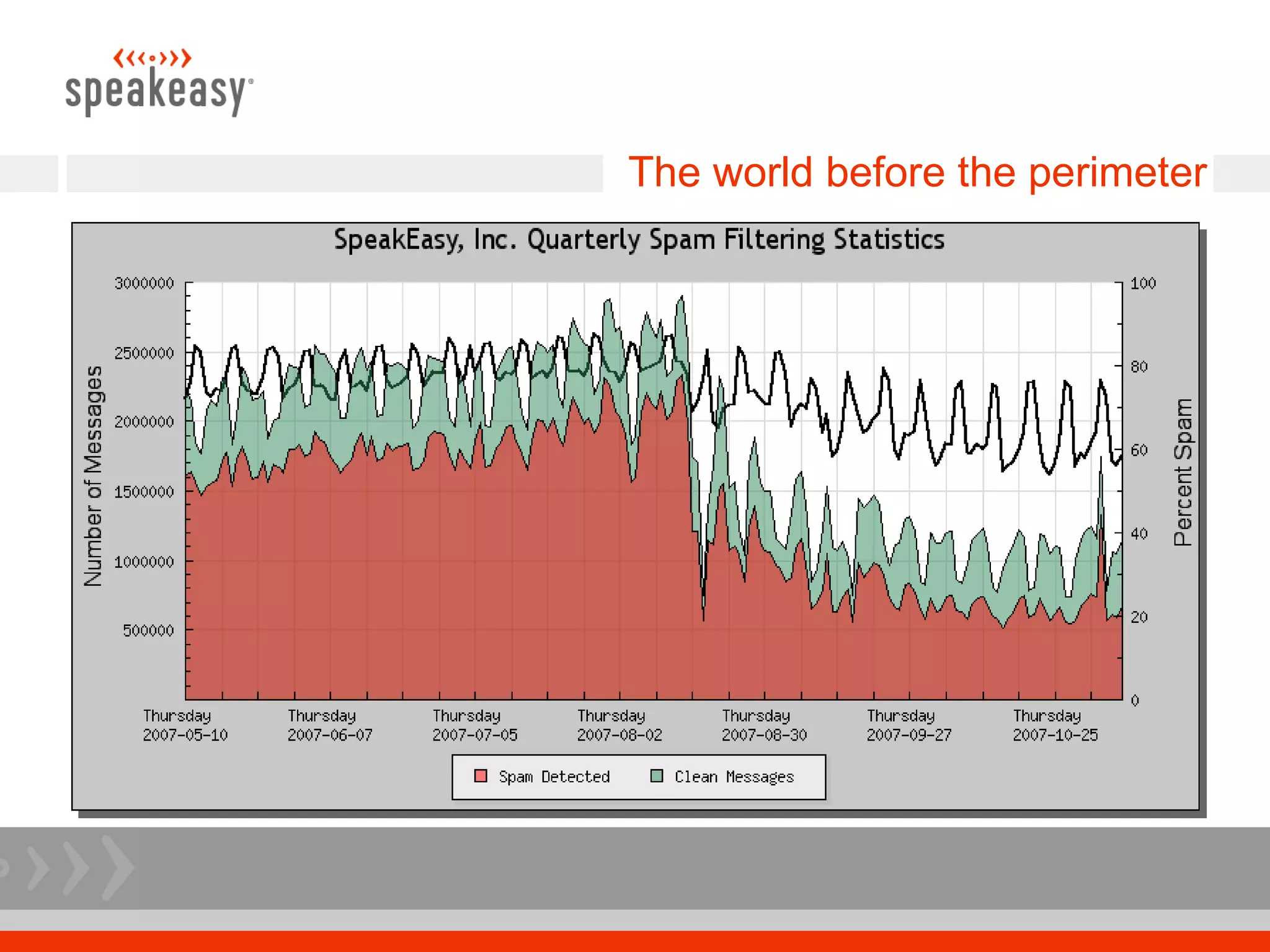
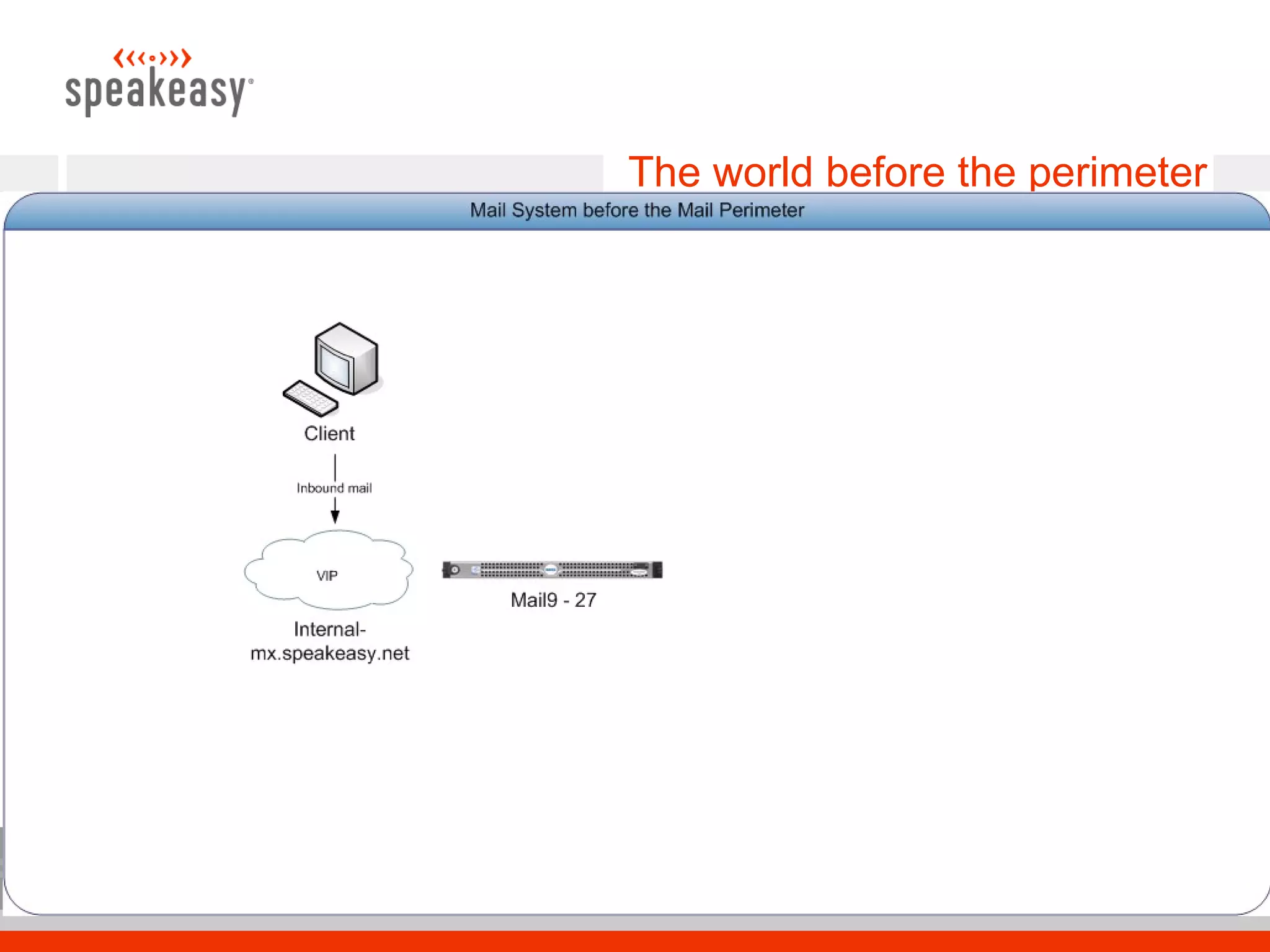
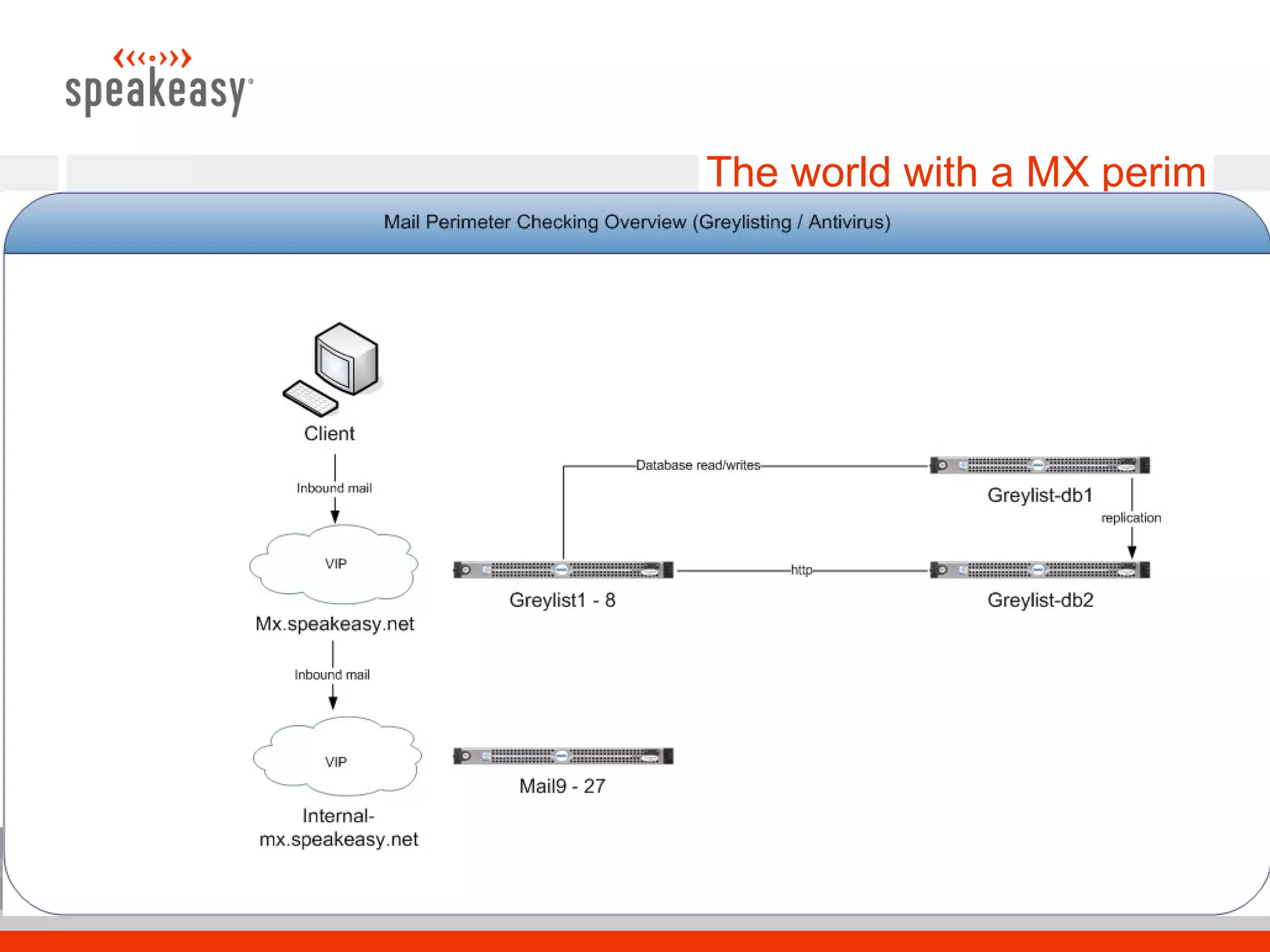
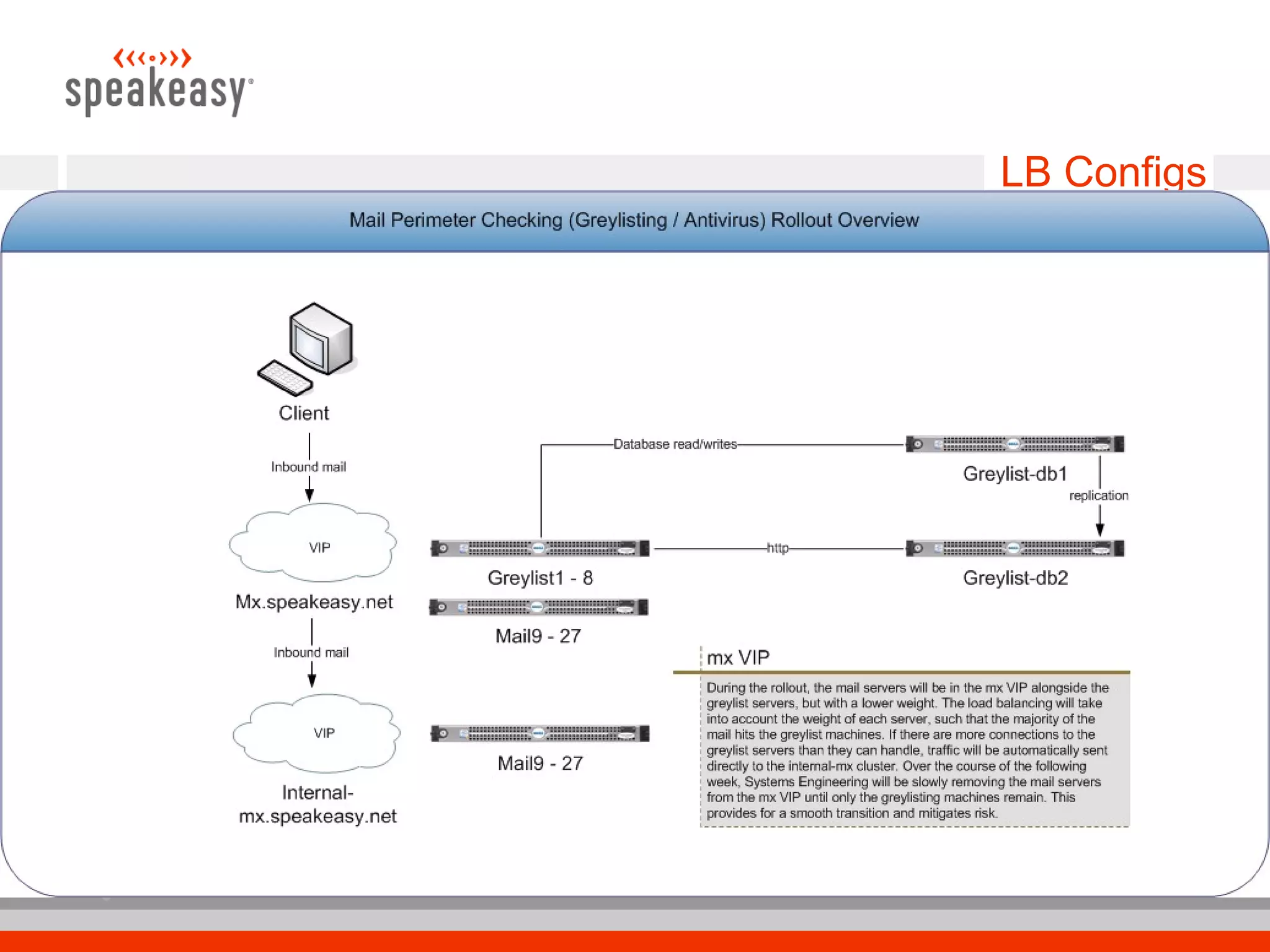
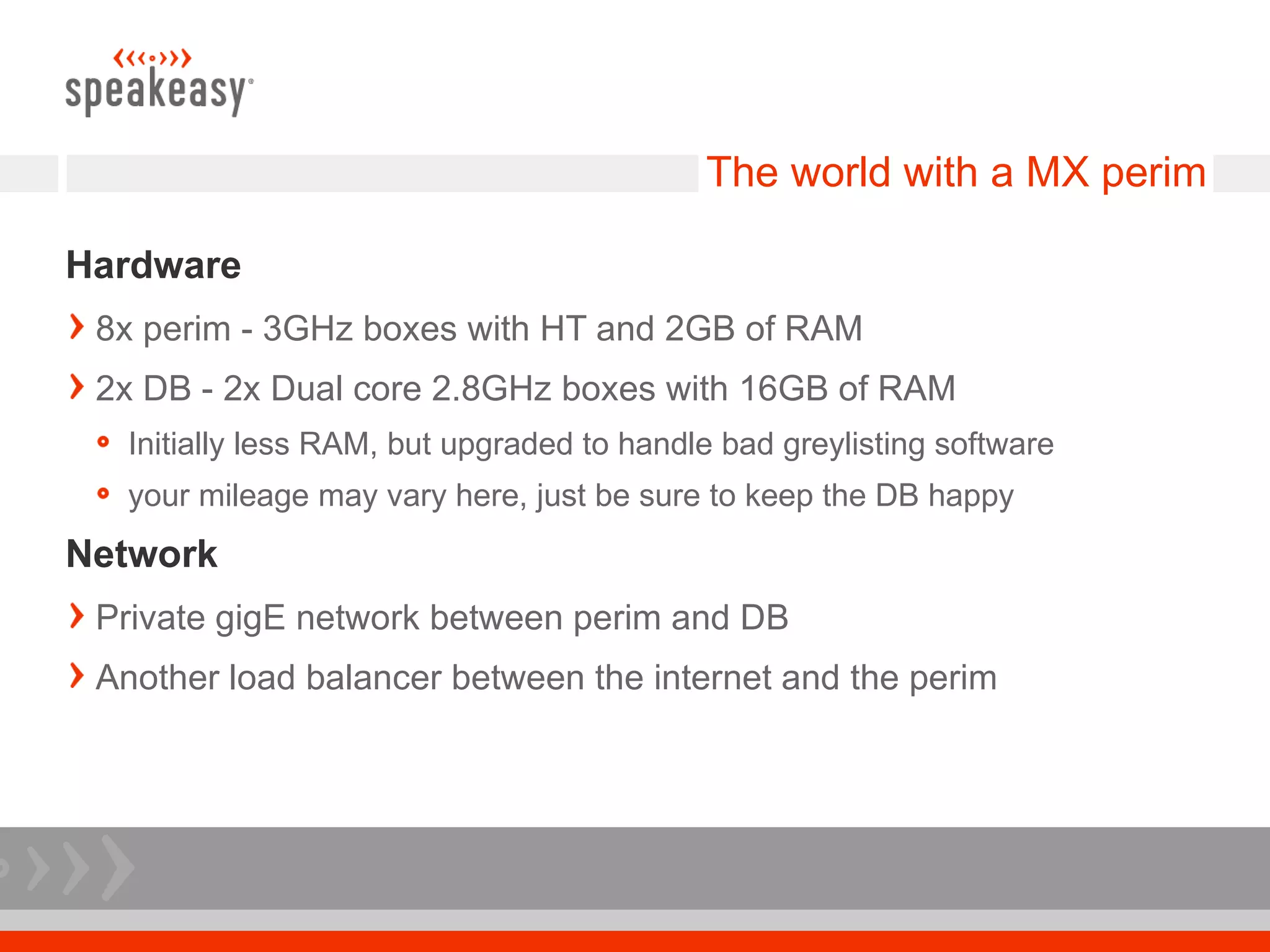
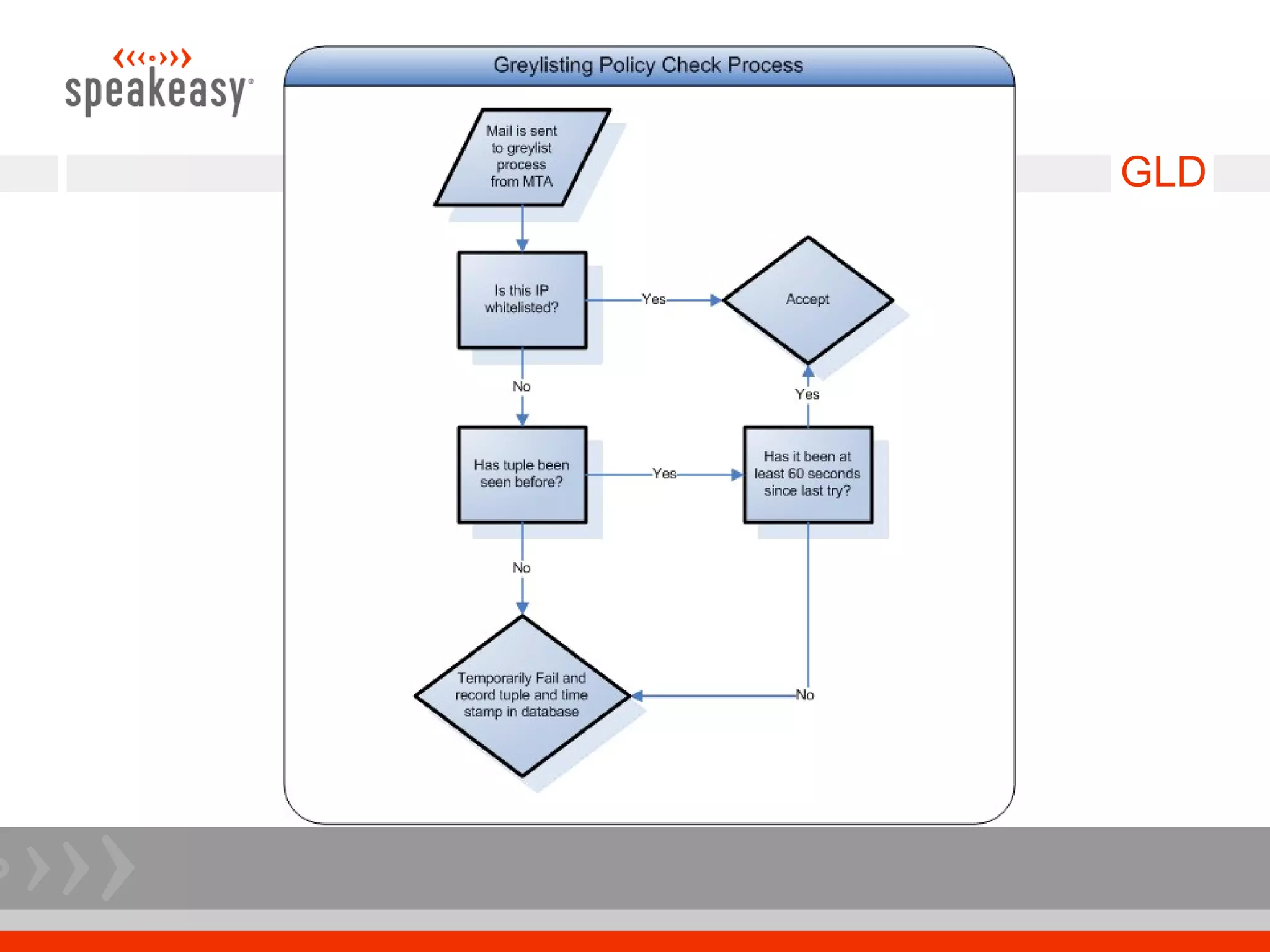
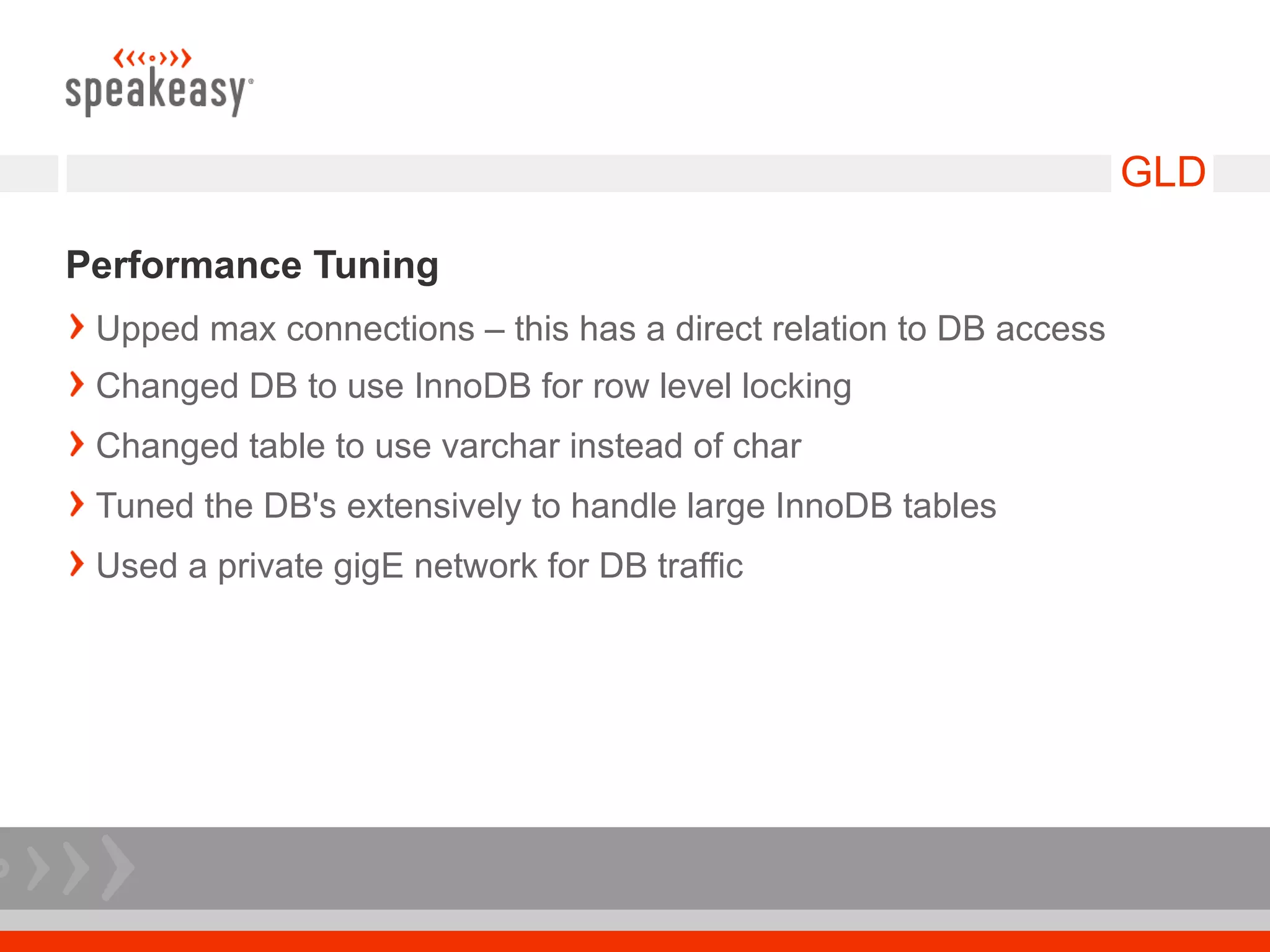
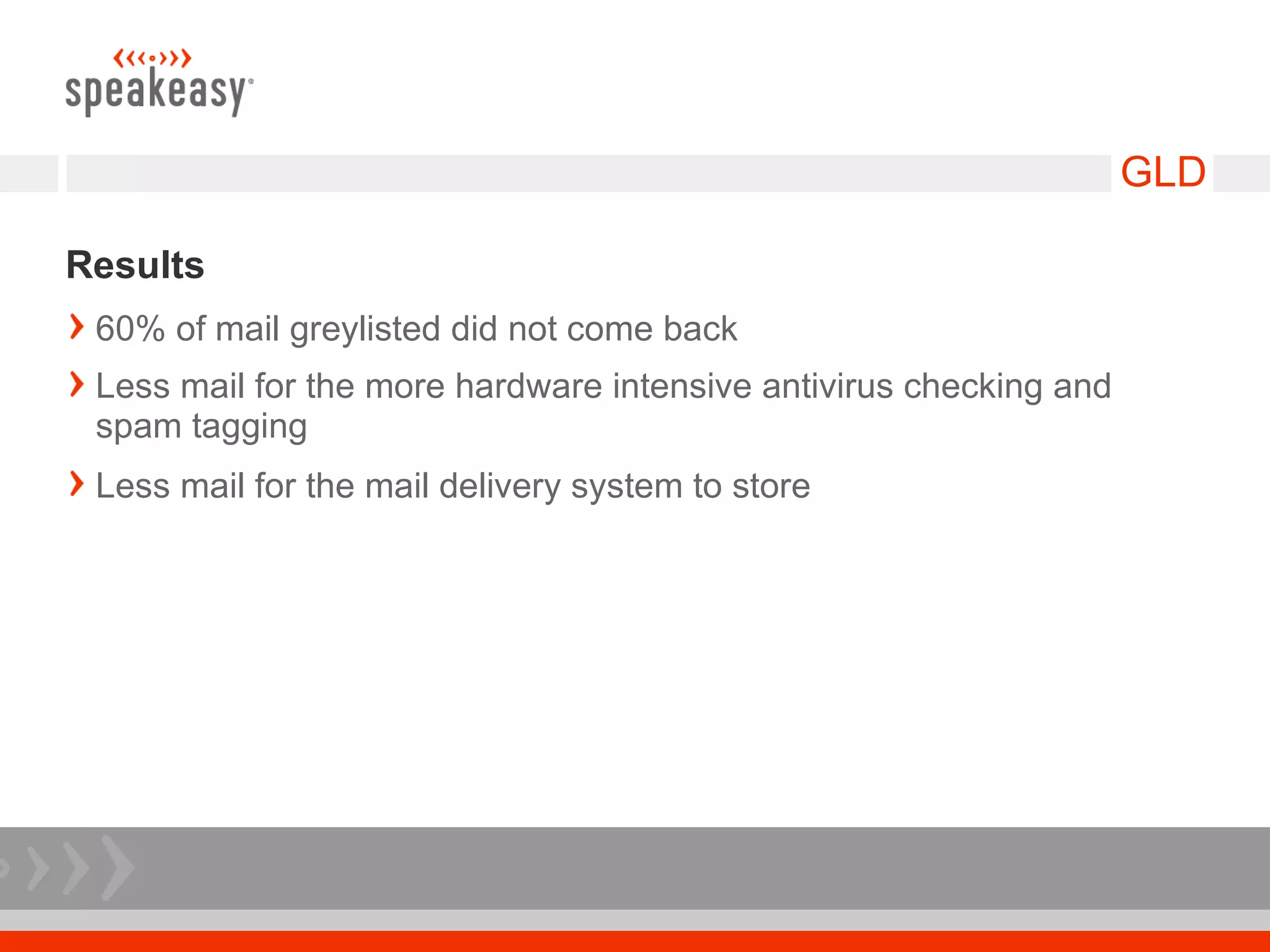
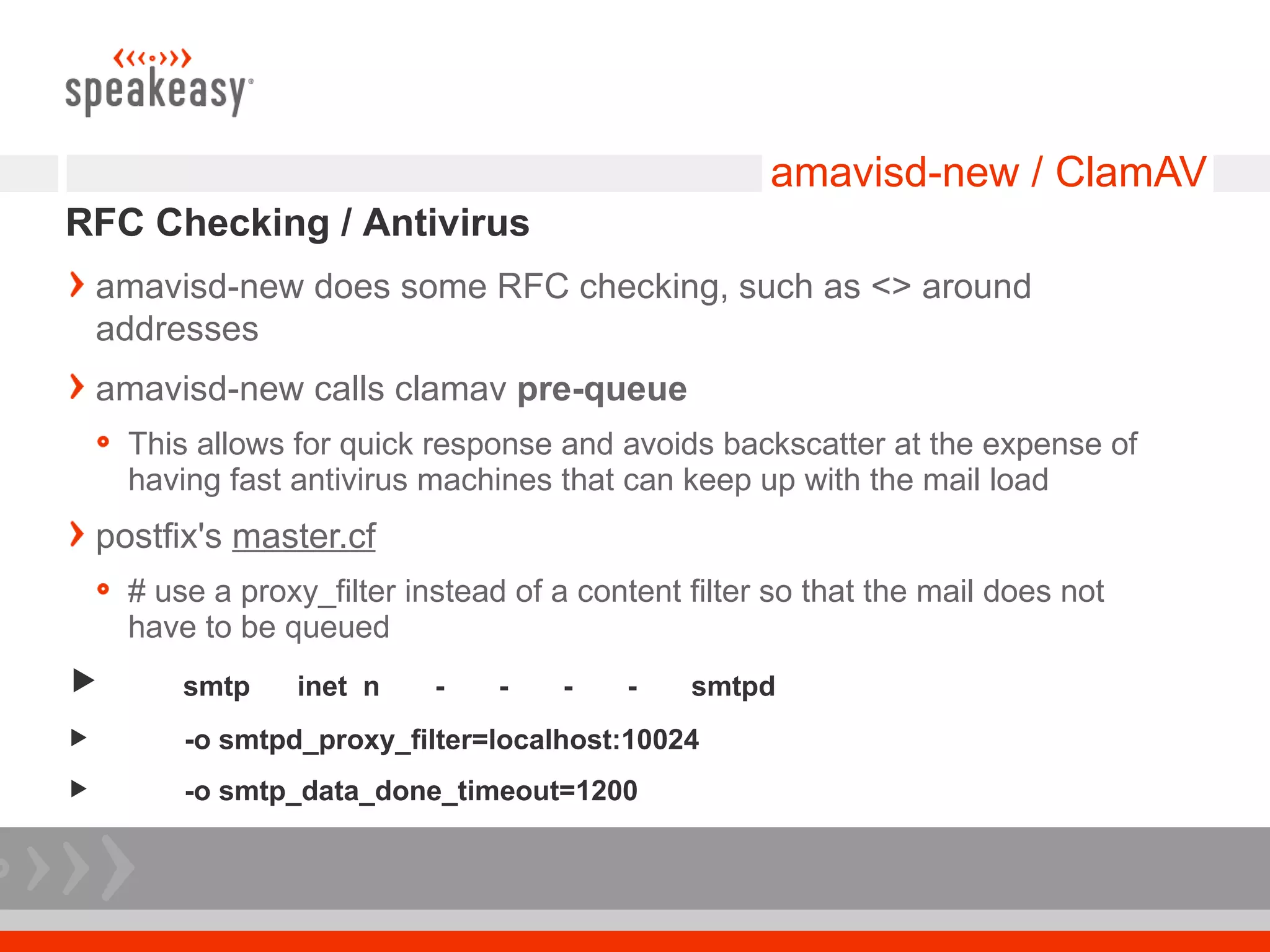
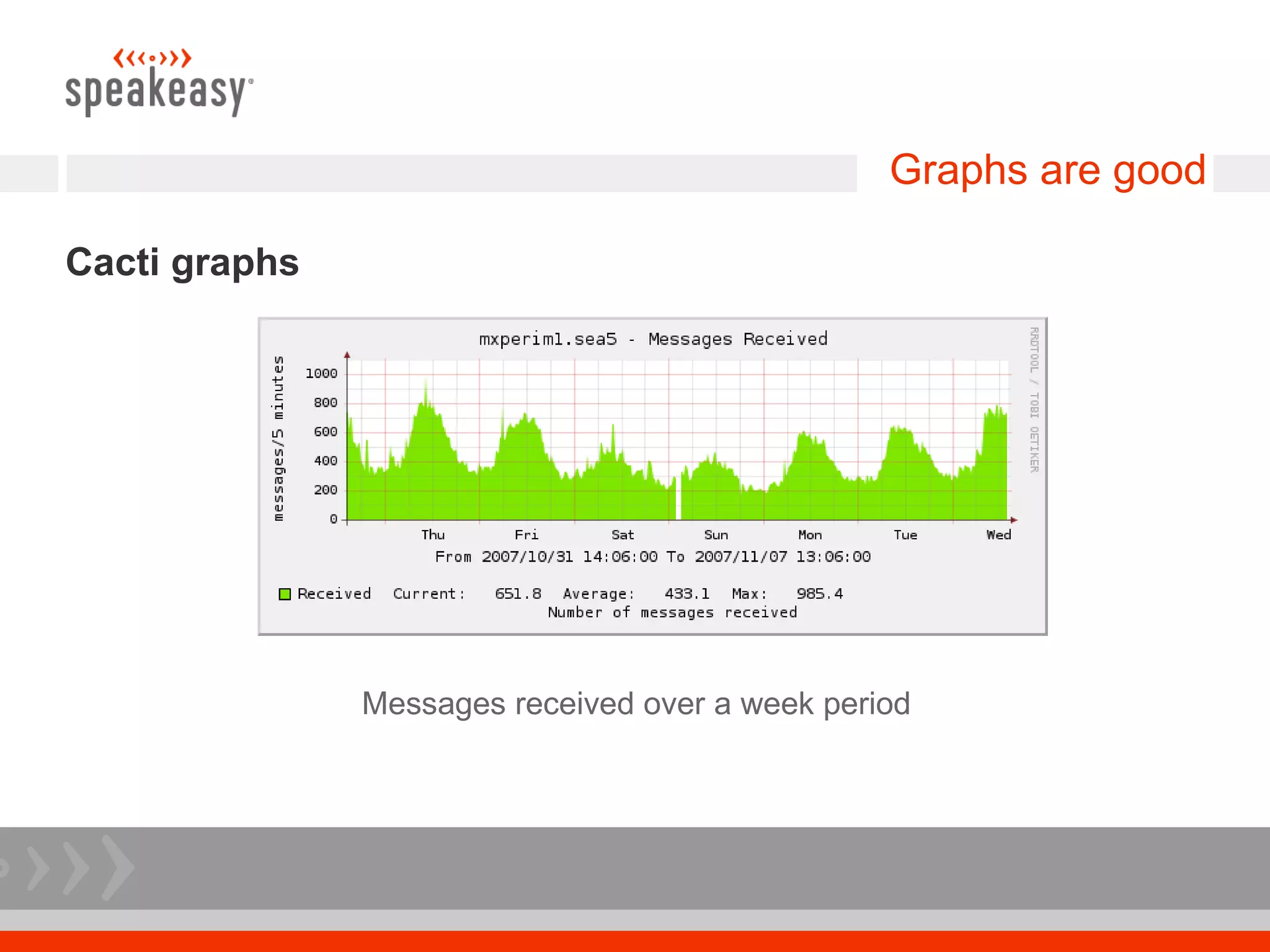
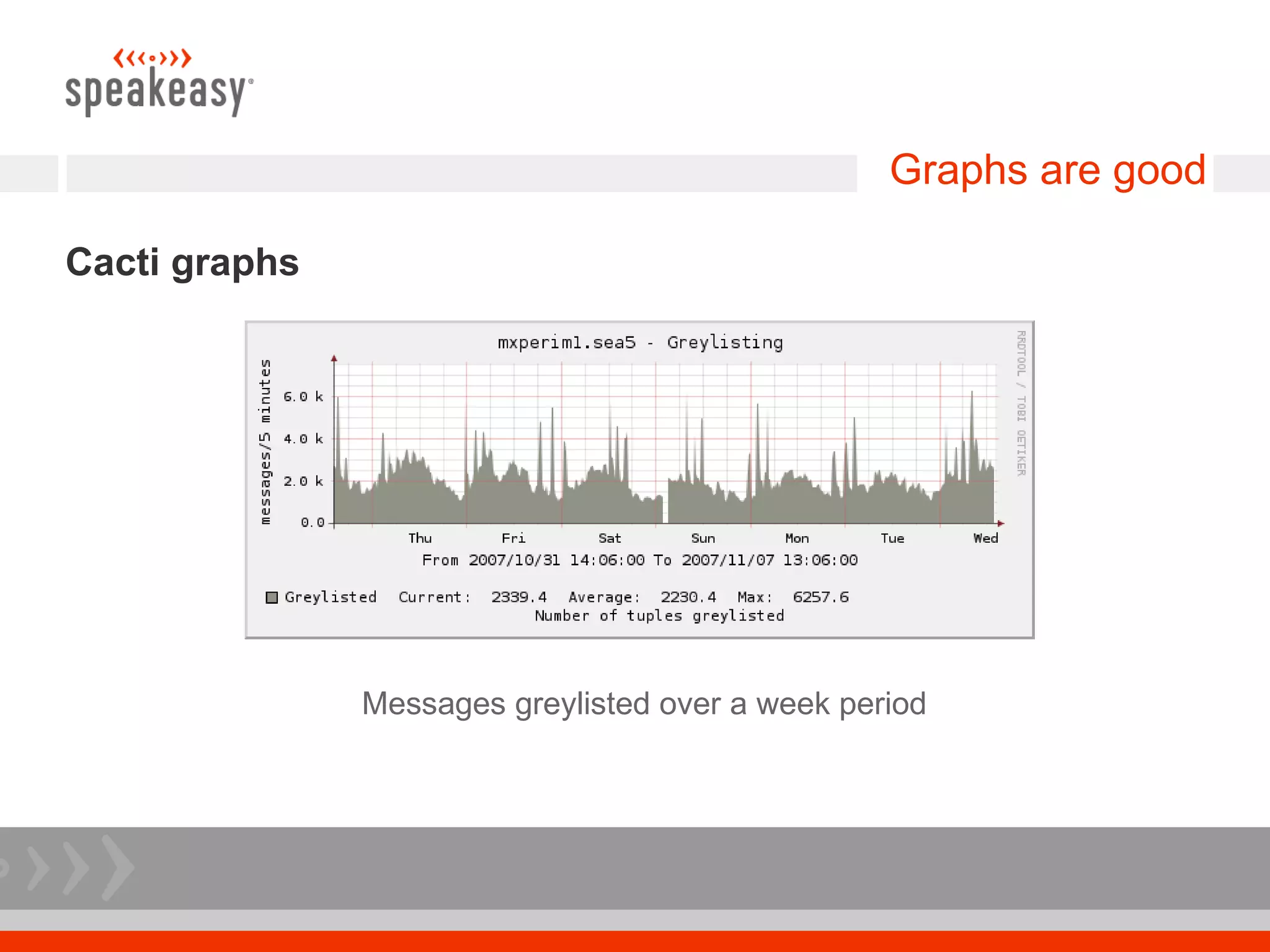
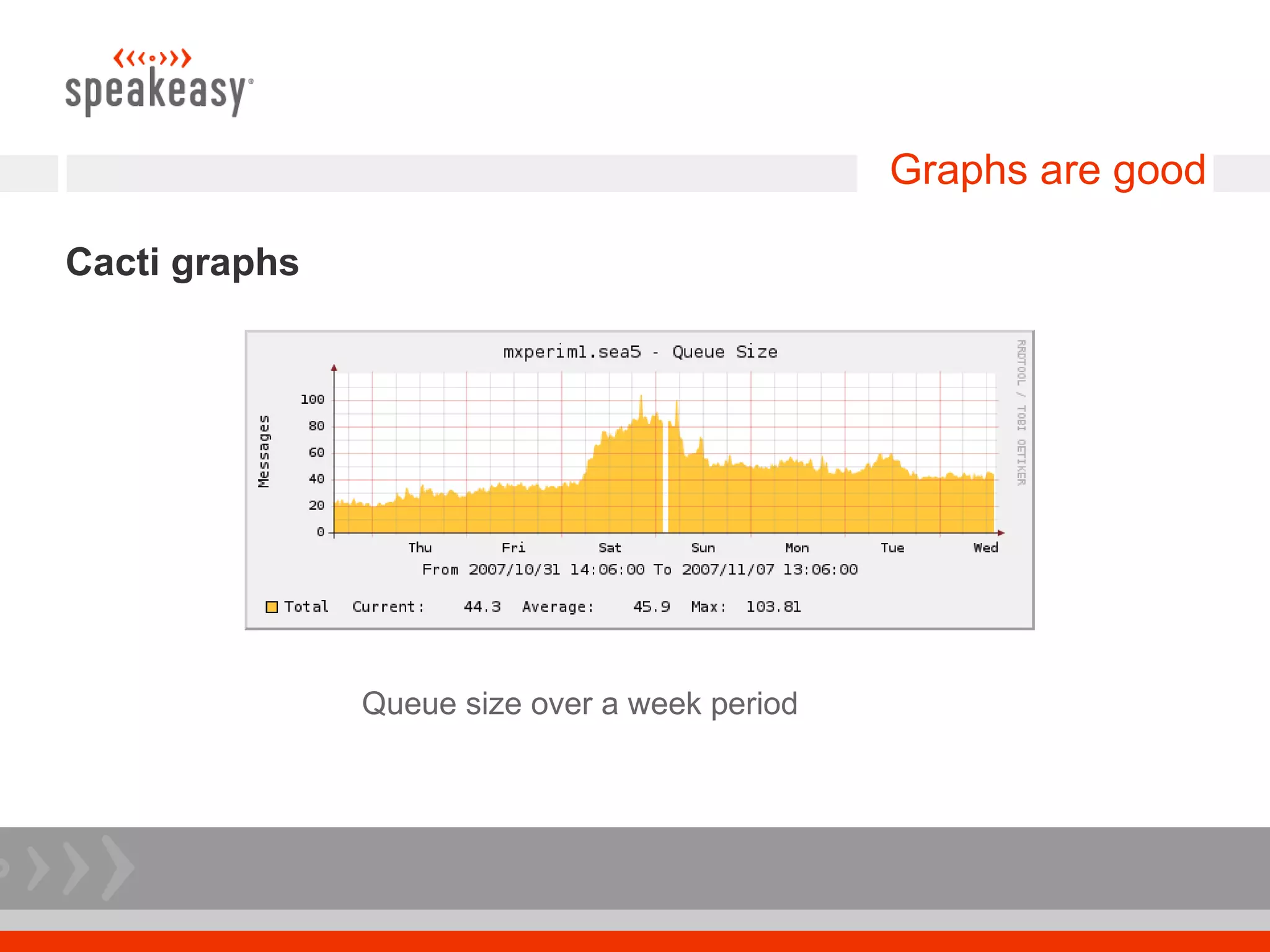
The document discusses moving to a tiered perimeter mail system to better fight spam. Some key points:
- Implement a tiered system with separate hardware for mail filtering services like greylisting, antivirus scanning, and spam tagging to improve scalability.
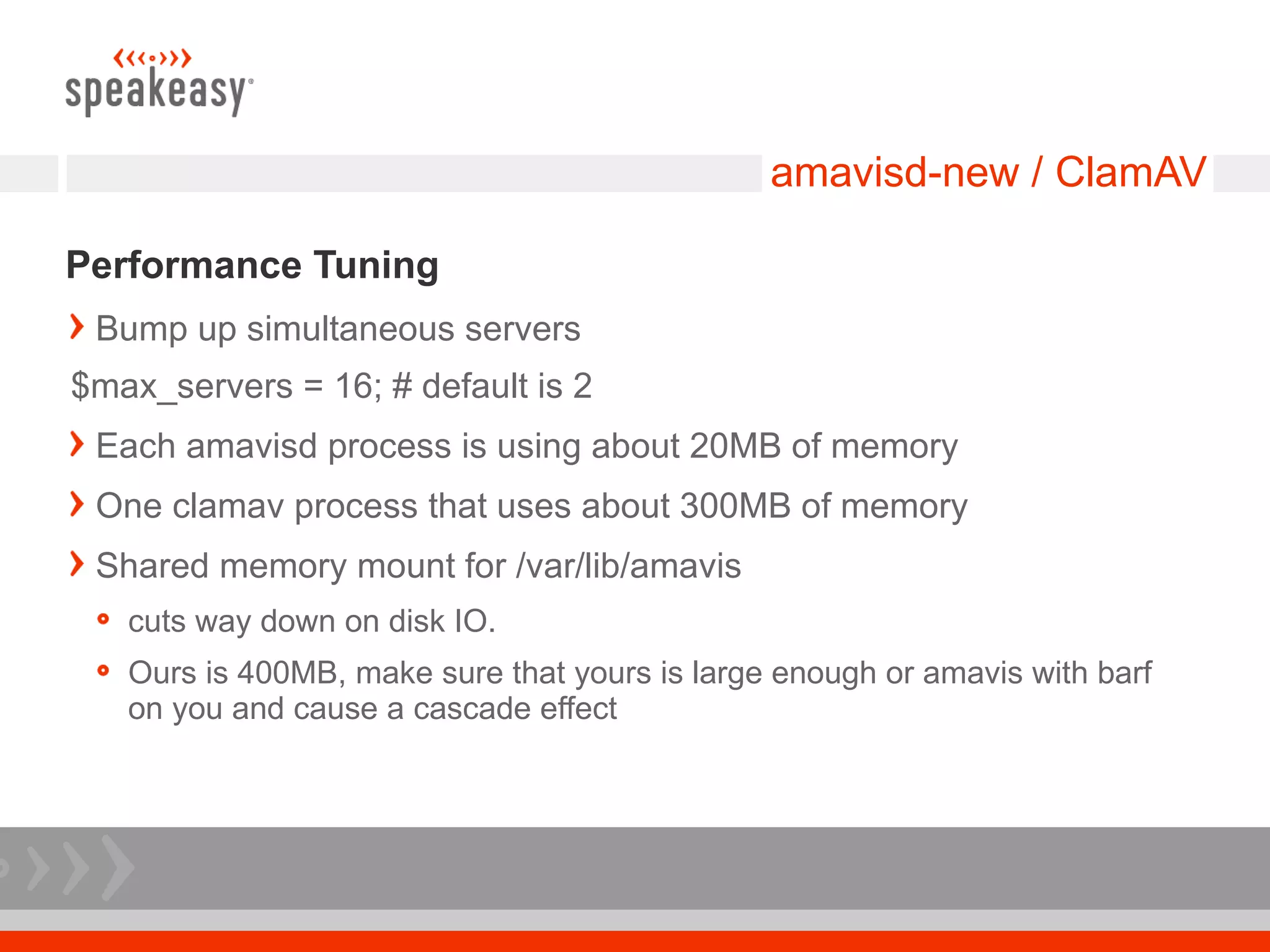
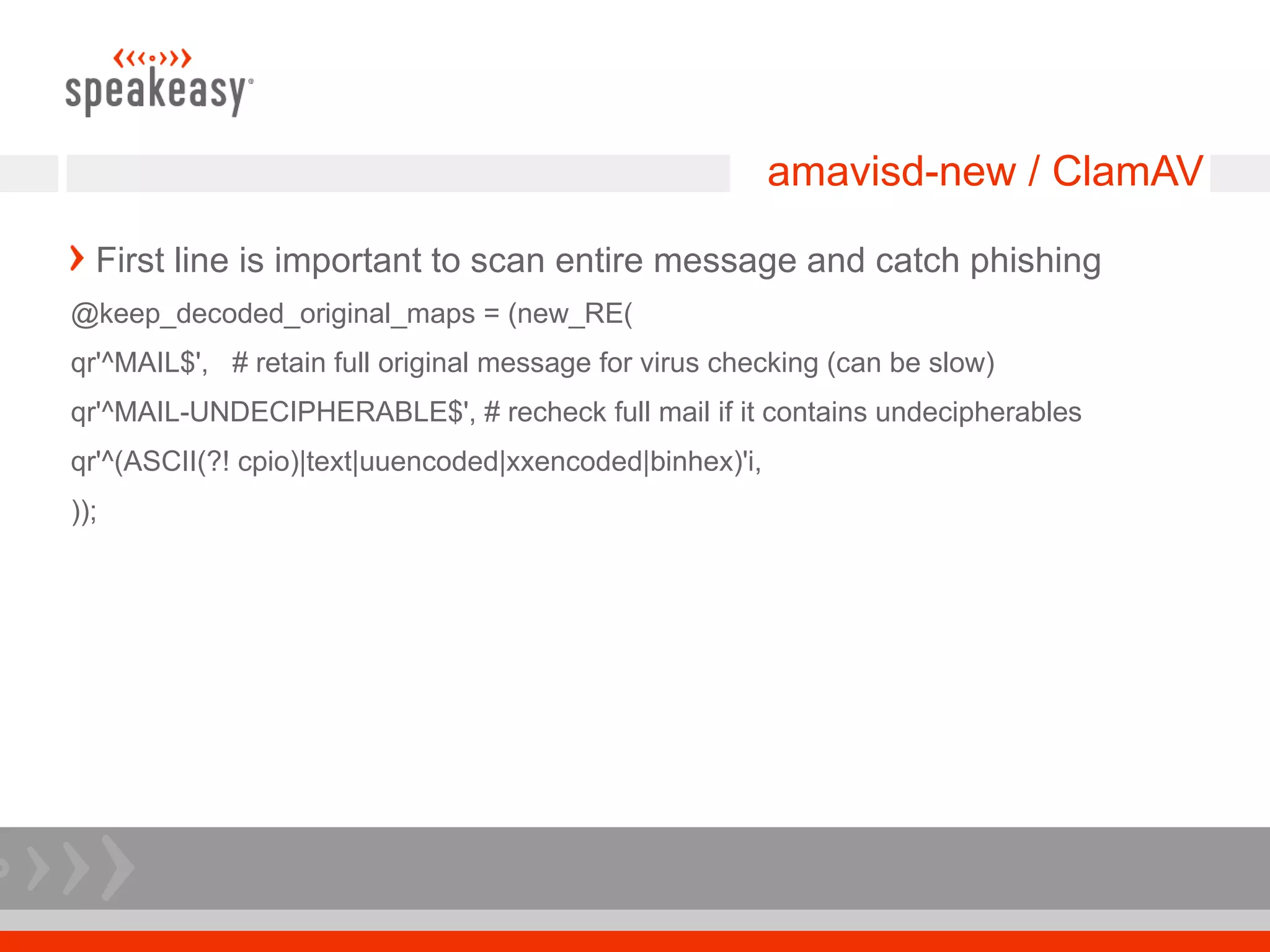
- Configure Postfix and supporting services like GLD greylisting and amavisd-new with ClamAV for antivirus to optimize performance and throughput.
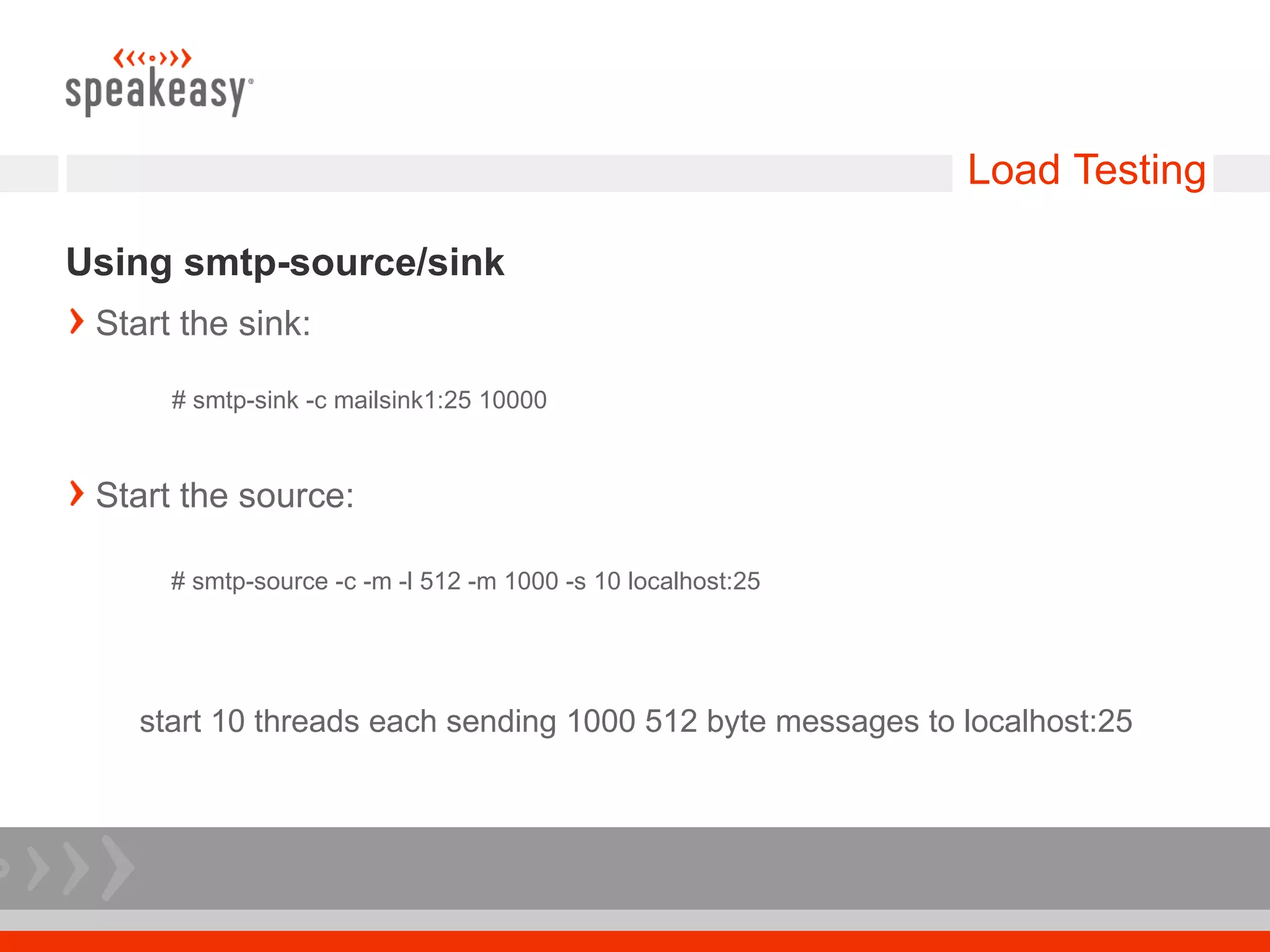
- Use load testing tools like smtp-source and smtp-sink to validate the new system can handle expected mail loads before putting into production.