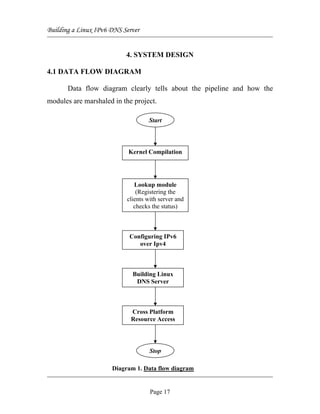
The document discusses building a Linux IPv6 DNS server. It provides an overview of the project which aims to configure a DNS server in Linux with IPv6 name resolution. It discusses the hardware and software requirements including using Red Hat Linux, kernel version 2.4 or higher, and BIND version 9. It also summarizes the key steps in building the DNS server such as creating a new kernel, making the DNS server support IPv6, and providing a backup of the existing kernel.





![Building a Linux IPv6 DNS Server
3. SYSTEM SPECIFICATION
3.1 HARDWARE REQUIREMENTS
SERVER MACHINE : Red Hat Enterprise / Workstation Linux v3.0
[Server Installation]
CLIENT MACHINE : MS-Windows / Fedora core v3.0
[Client Installation]
PROCESSOR : Intel / AMD Processors (> 533 MHz)
MAIN MEMORY : 32MB RAM
HARD DISK : Minimum 2GB
KEYBOARD : 101 keys
3.2 SOFTWARE REQUIREMENTS
PLATFORM USED : RedHat Enterprise / Workstation Linux 3
SOURCE LANGUAGE : Java, C, Shell Scripting
SHELL TYPE : Bash
KERNEL VERSION : 2.4 (Shrike)
KERNEL TYPE : Stable Kernel (Open)
BIND VERSION : 9.0
LANGUAGE TOOL KITS : J2SDK v 1.4, Gcc Compiler
PACKAGE FORMAT : .rpm for Linux, .exe format for
Windows families.
Page 6](https://image.slidesharecdn.com/building-linux-ipv6-dns-server-soft-copy-1224401388228175-9/85/Building-Linux-IPv6-DNS-Server-Complete-Soft-Copy-6-320.jpg)































![Building a Linux IPv6 DNS Server
• GUI basedconfiguration – make xconfig, make gconfig
In our project the necessary files to build a new kernel are kept under the
loading.sh file.
The following commands are used to customize the kernel
• Kernel level commands
These are the kernel commands which are included in our shell program
loading.sh to build, compile, installing the kernel modules.
# make dep >> for dependency checks.
# make clean >> parameter checks.
# make bzImage >> Extracting Kernel image.
• Modules level commands
These are the commands to install modules in the kernel
# make modules >> configuring kernel modules.
# make modules_install >> installing modules.
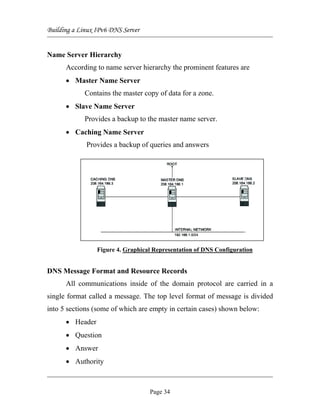
Lookup Module
The main goal of this module is to check the status of the server by
the client. Initially the server is enabled by specifying a port number which
is greater than 1024 [i.e. it should not be a default port number as assigned
by ICANN].
Then all the clients are registered with the server in the same port
number that is assigned previously at the server side programs by clicking
Page 40](https://image.slidesharecdn.com/building-linux-ipv6-dns-server-soft-copy-1224401388228175-9/85/Building-Linux-IPv6-DNS-Server-Complete-Soft-Copy-40-320.jpg)












