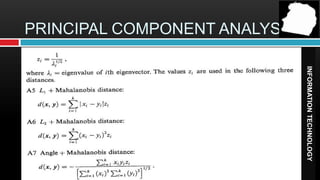
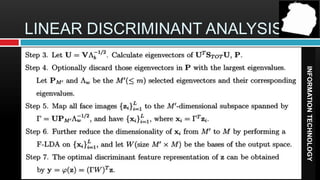
Facial recognition technology uses computer vision to identify or verify a person's identity from their face. It involves capturing an image, extracting facial features, comparing the features to images in a database, and determining a match or non-match. Facial recognition has various applications in security, human-computer interaction, and law enforcement. It uses algorithms like principal component analysis and linear discriminant analysis to analyze facial features and images. The technology has improved over time but also raises privacy concerns that must be addressed.















![IMPLEMENTATION & PERFORMANCE
IMPLEMENTATION IMPLEMENTATION
• False Acceptance Rate
•Data acquisition [FAR]
•Input processing • False Rejection Rates
[FRR]
•Face image
• Response time
classification • Decision Threshold
•Decision making • Enrollment time](https://image.slidesharecdn.com/nishant-seminar-face-120920002543-phpapp02/85/Facial-Recognition-Technology-16-320.jpg)