This document provides information about Vinay Kumar and the topics he will discuss at SPOUG18-Madrid, including:
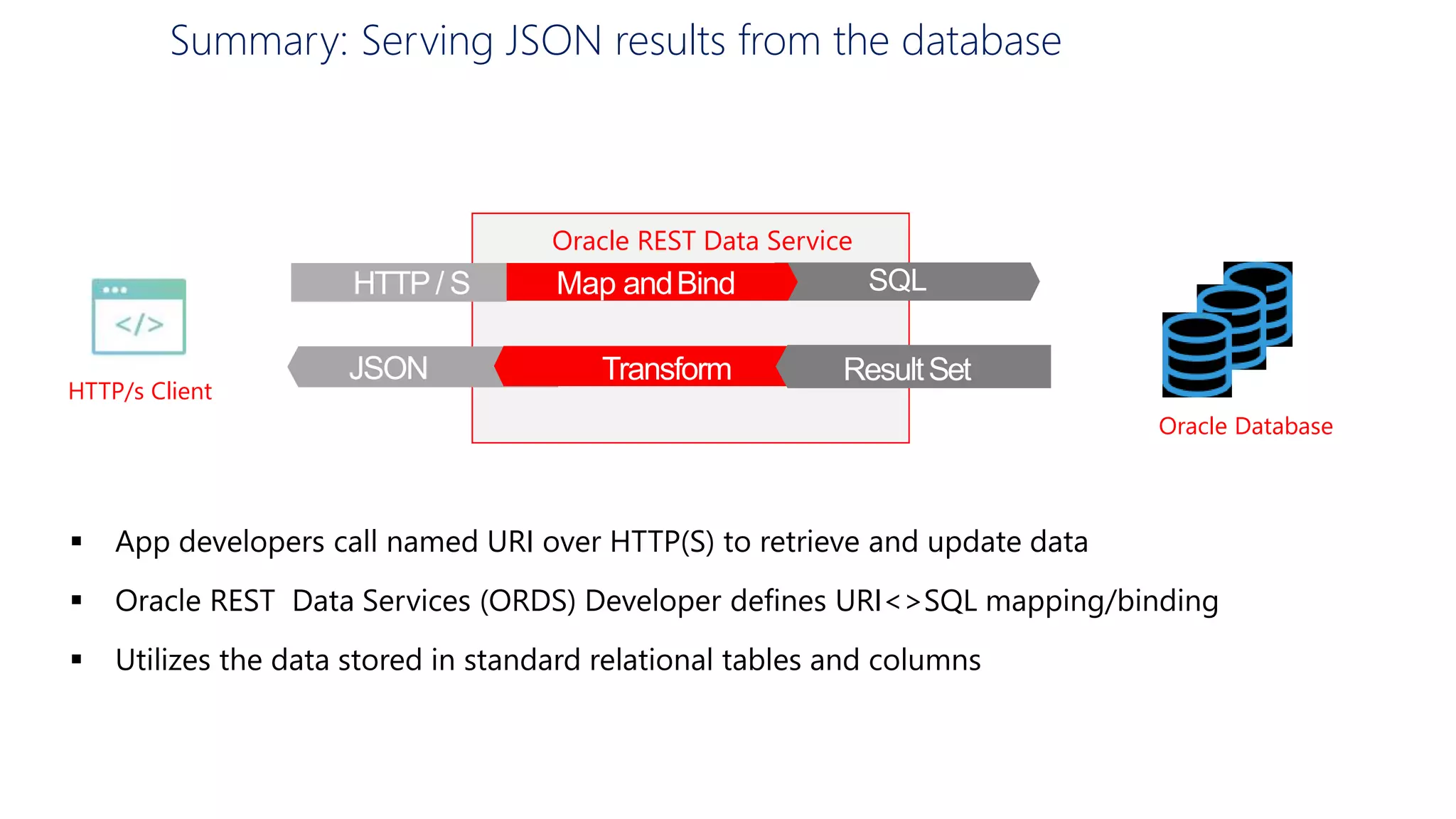
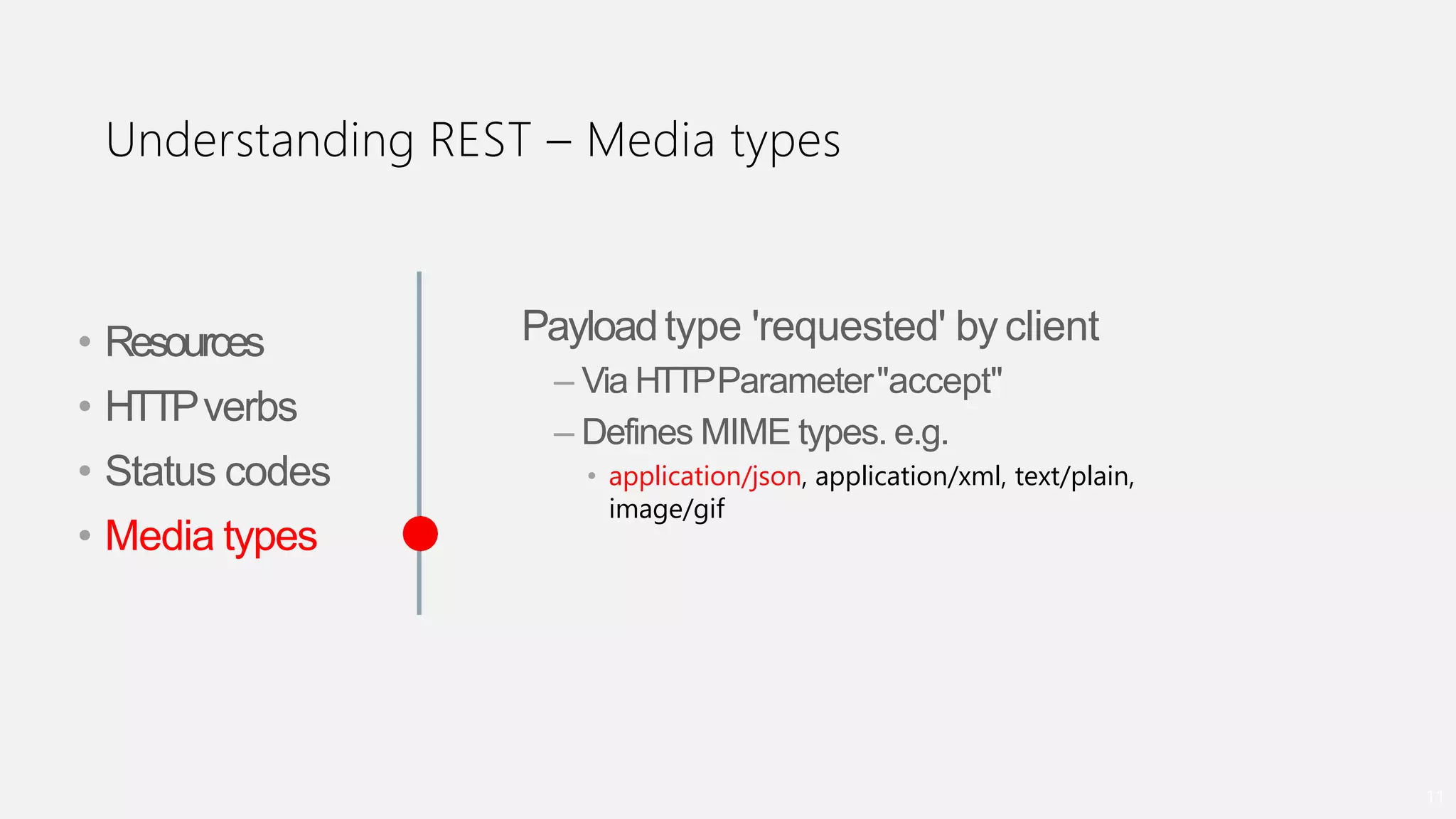
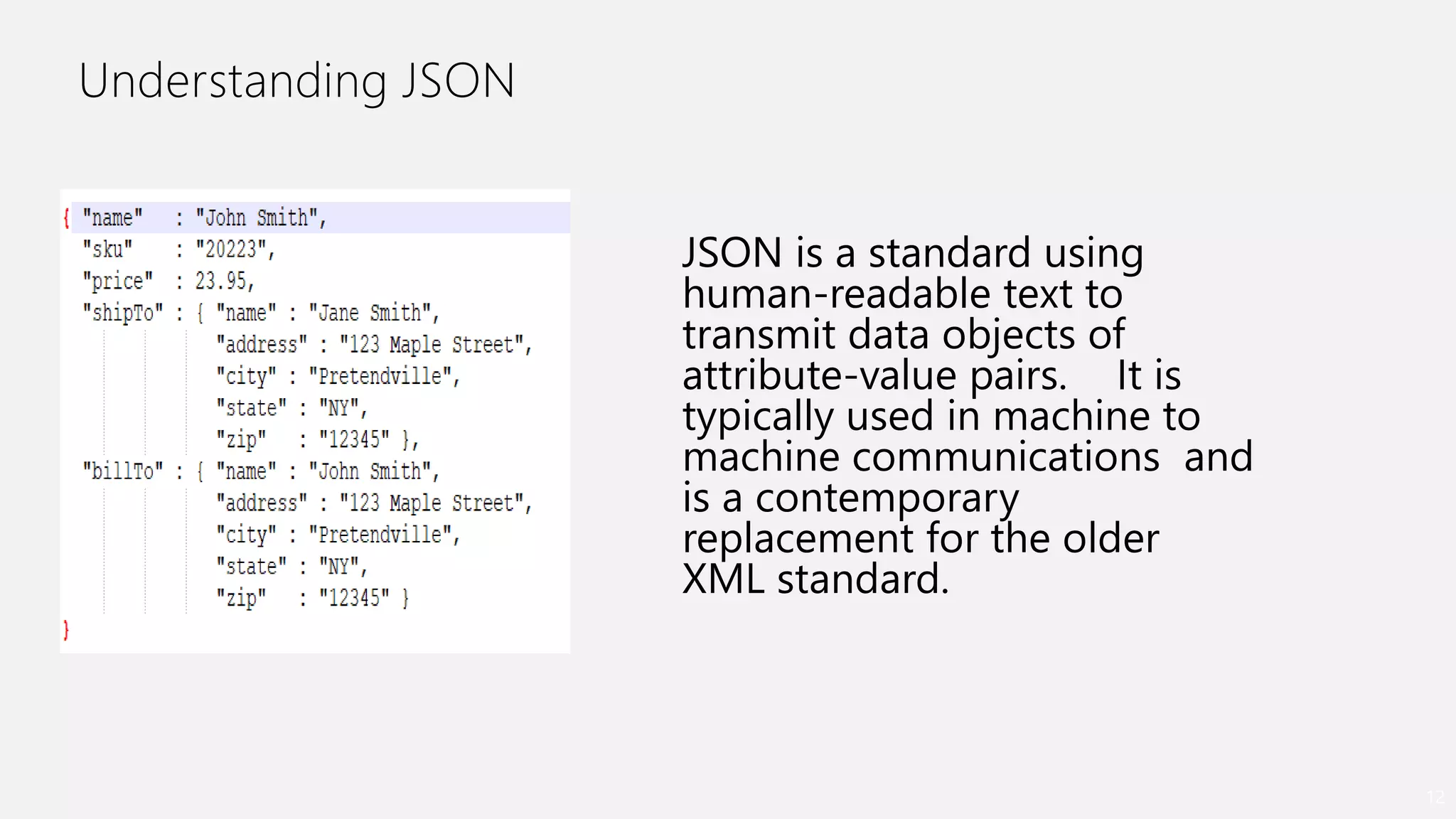
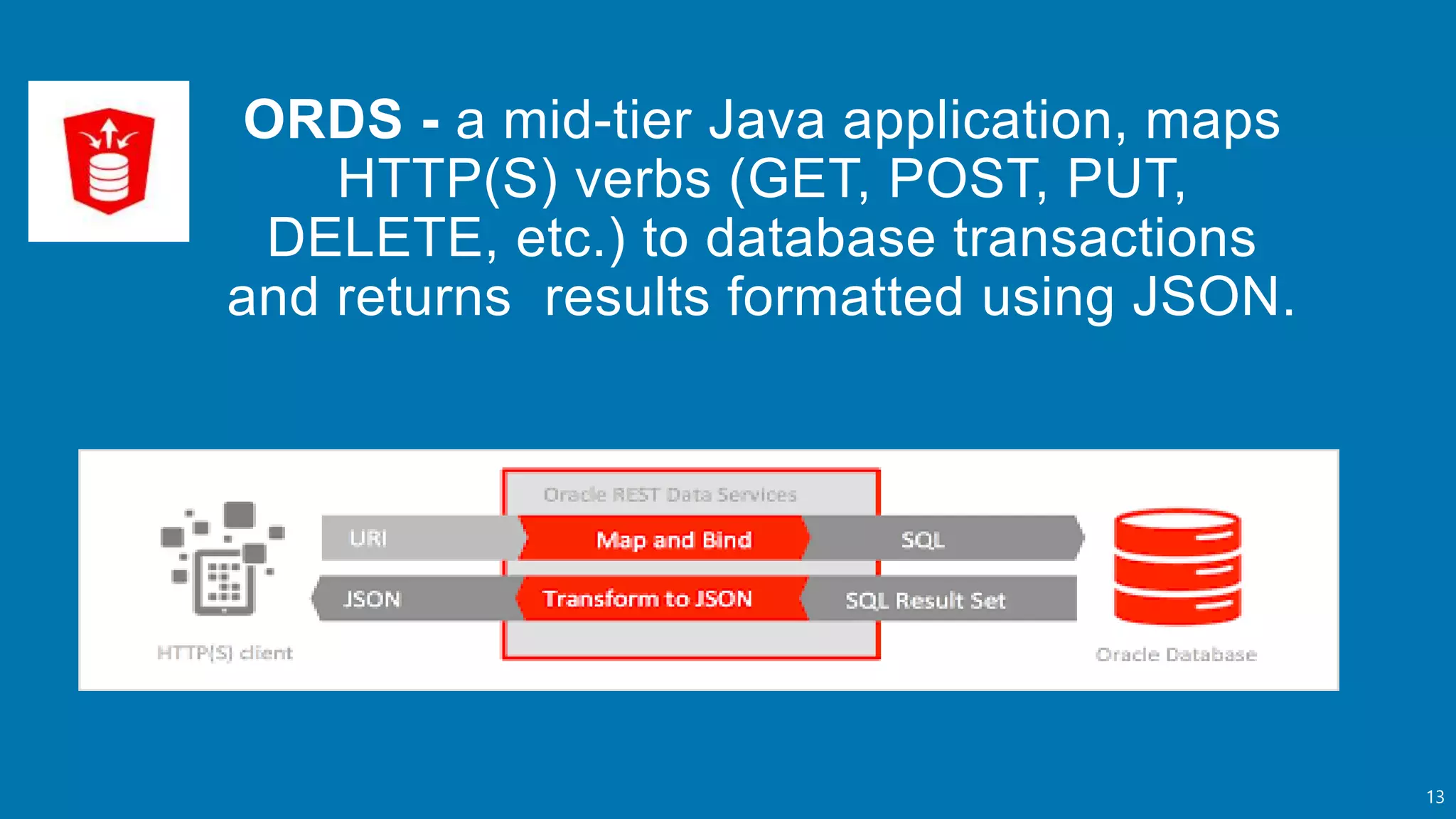
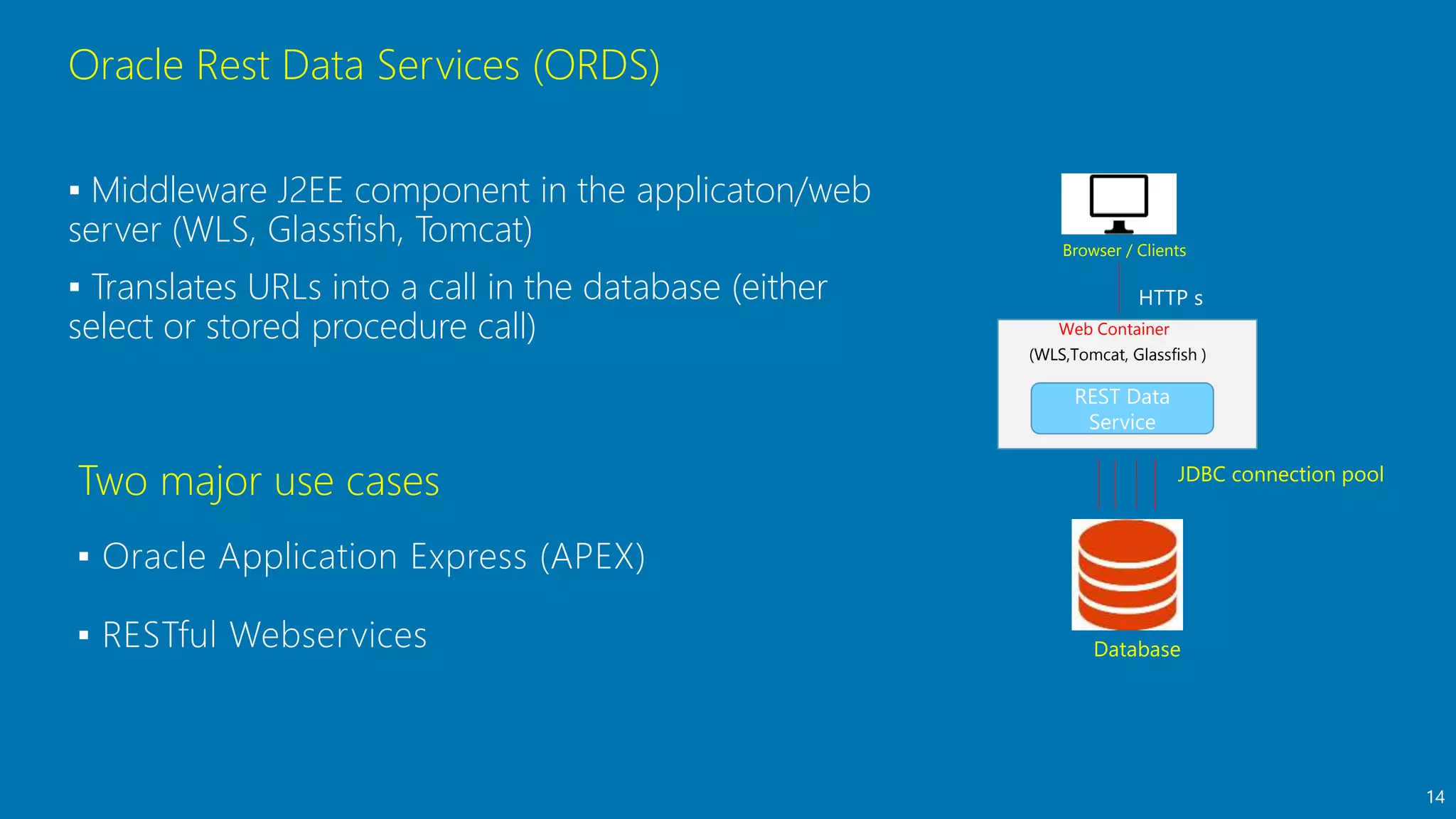
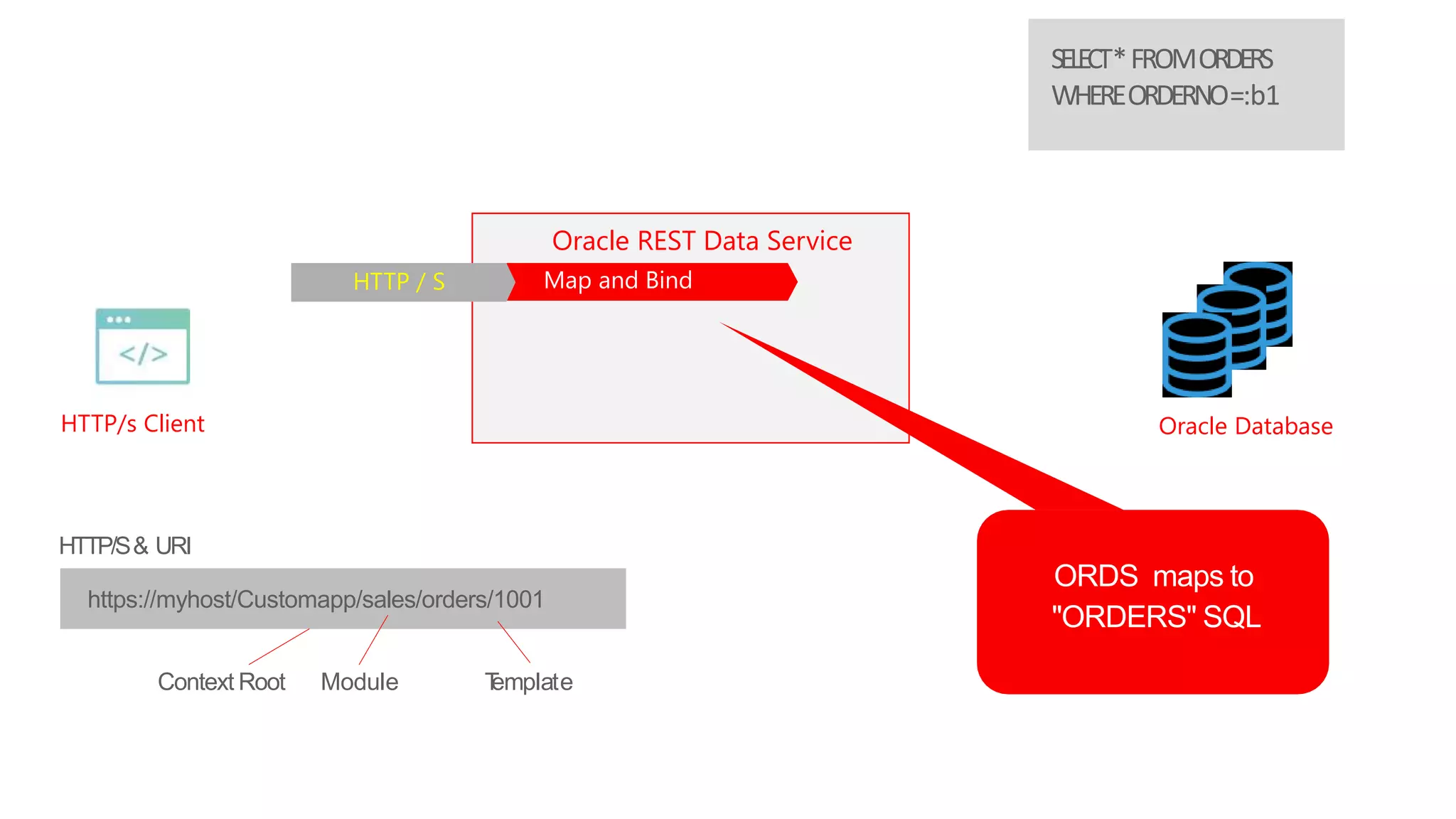
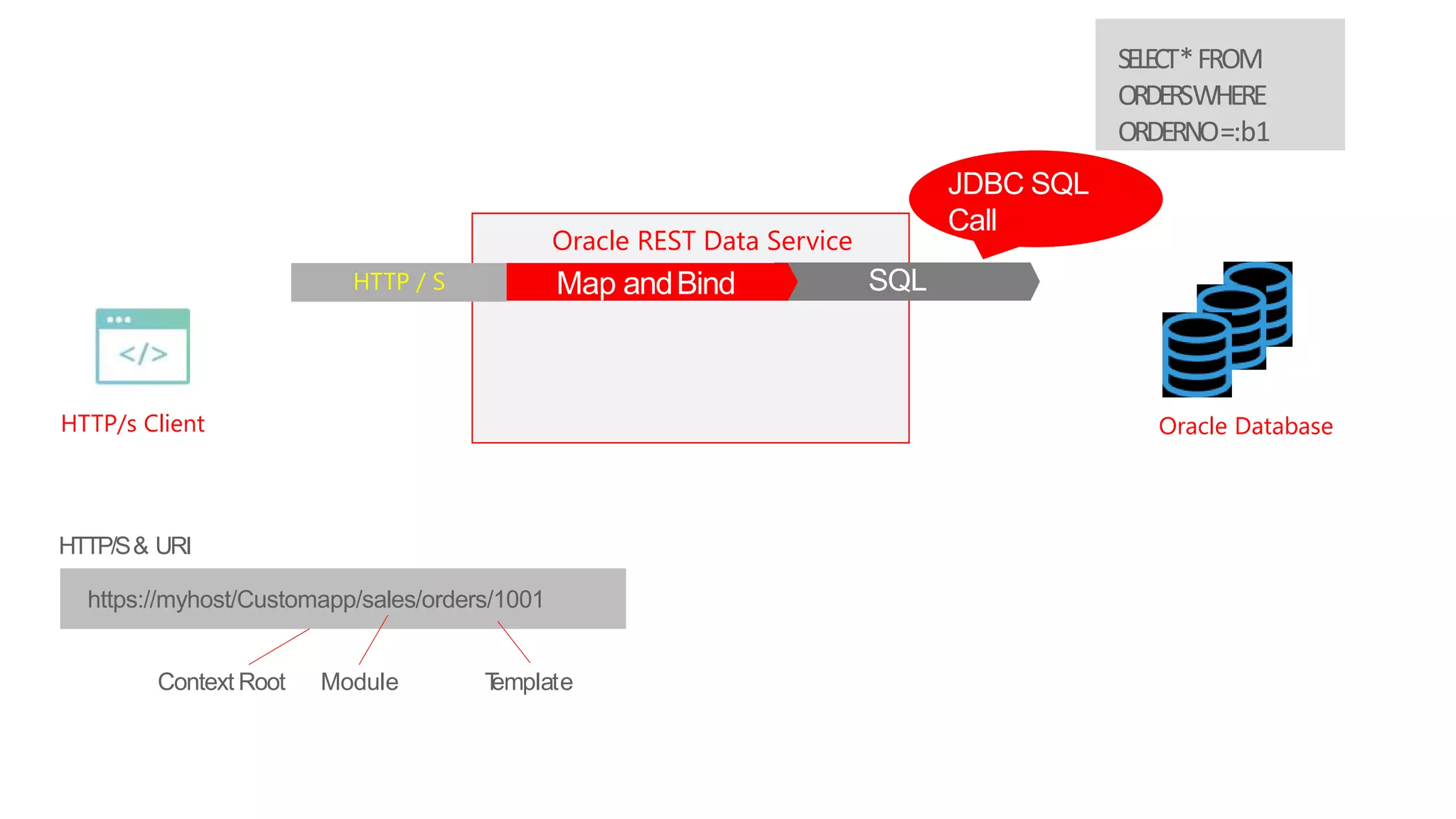
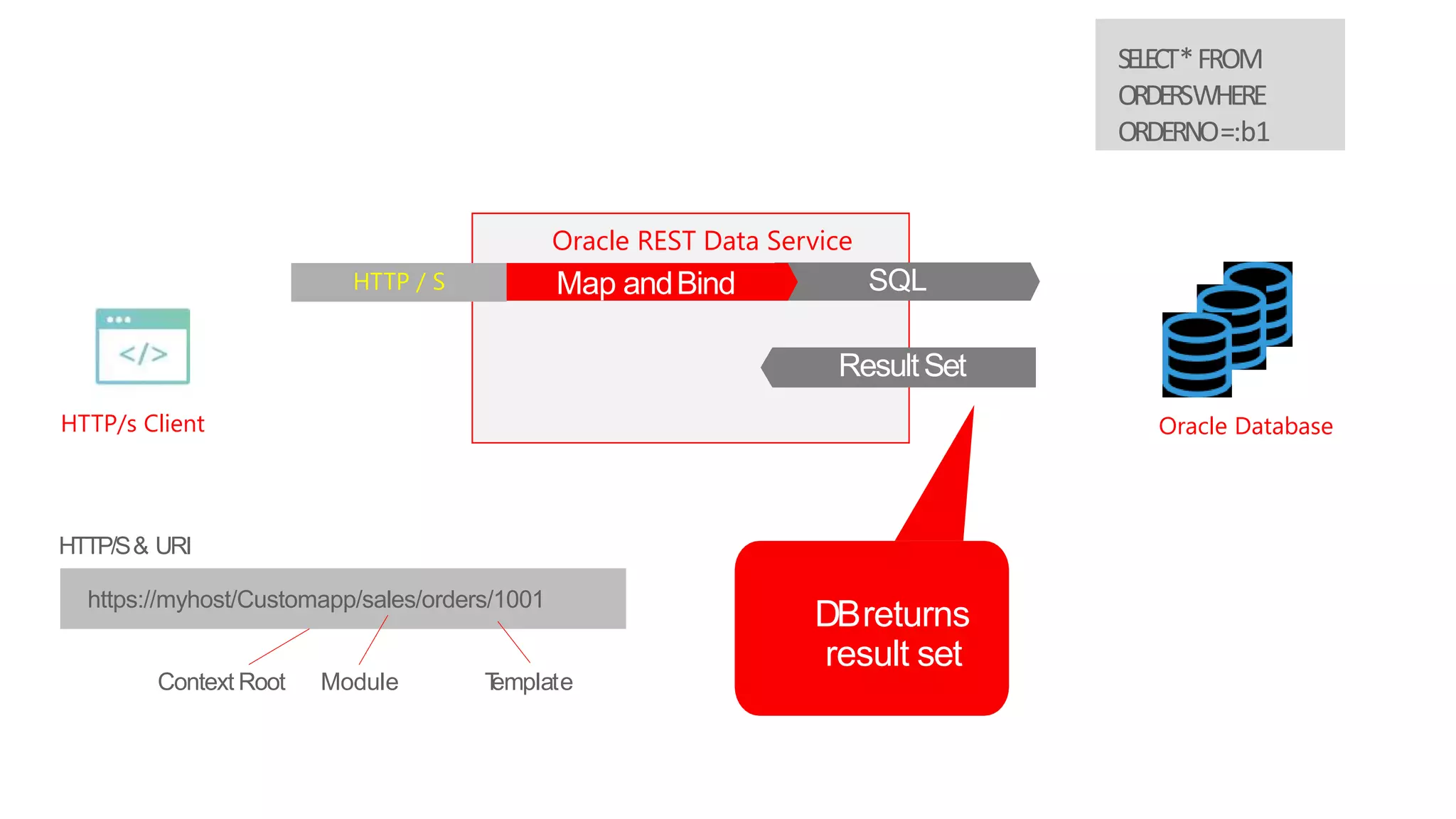
- An introduction to Oracle REST Data Services (ORDS) architecture and how it maps HTTP requests to SQL queries and transforms results to JSON.
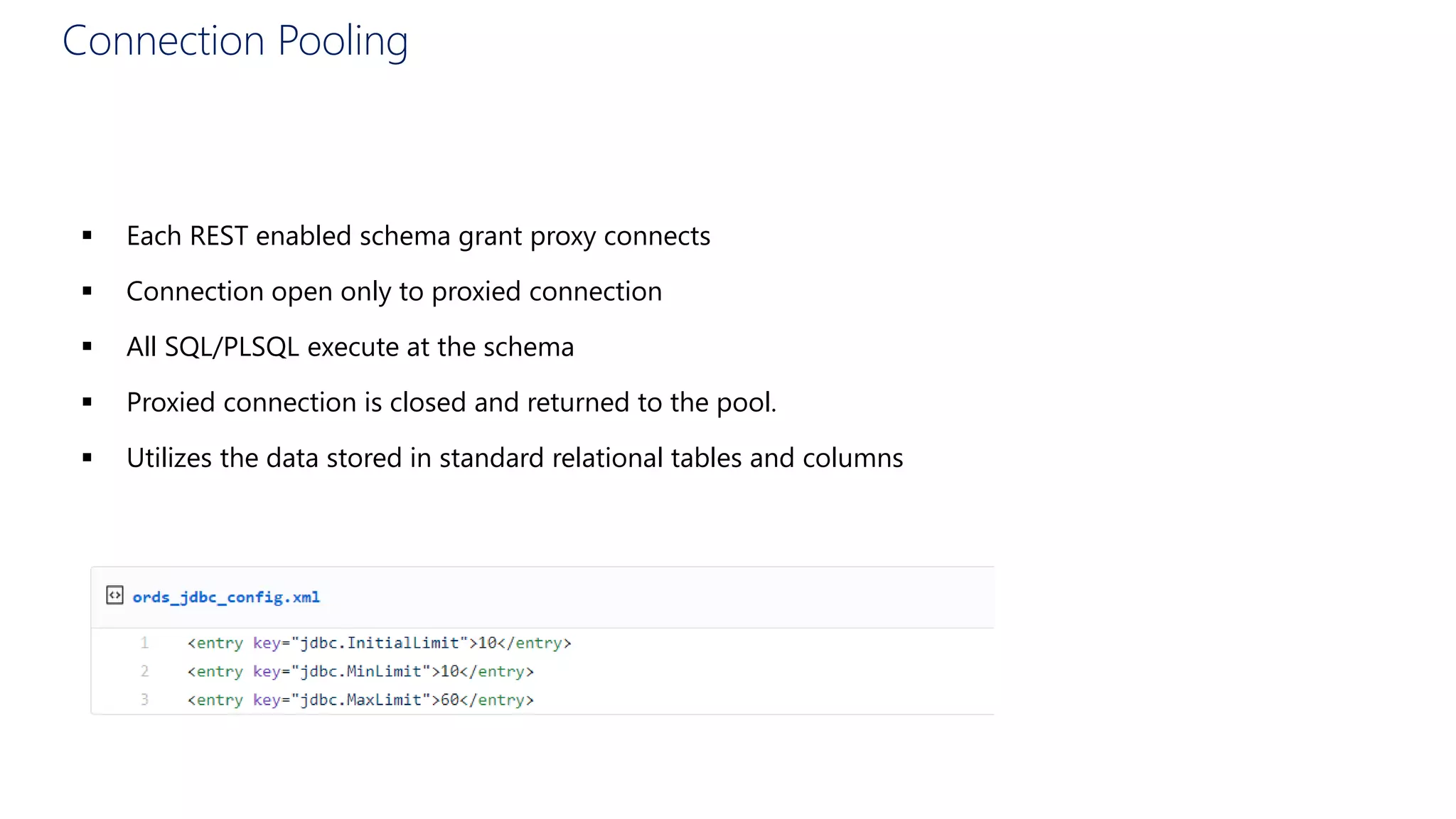
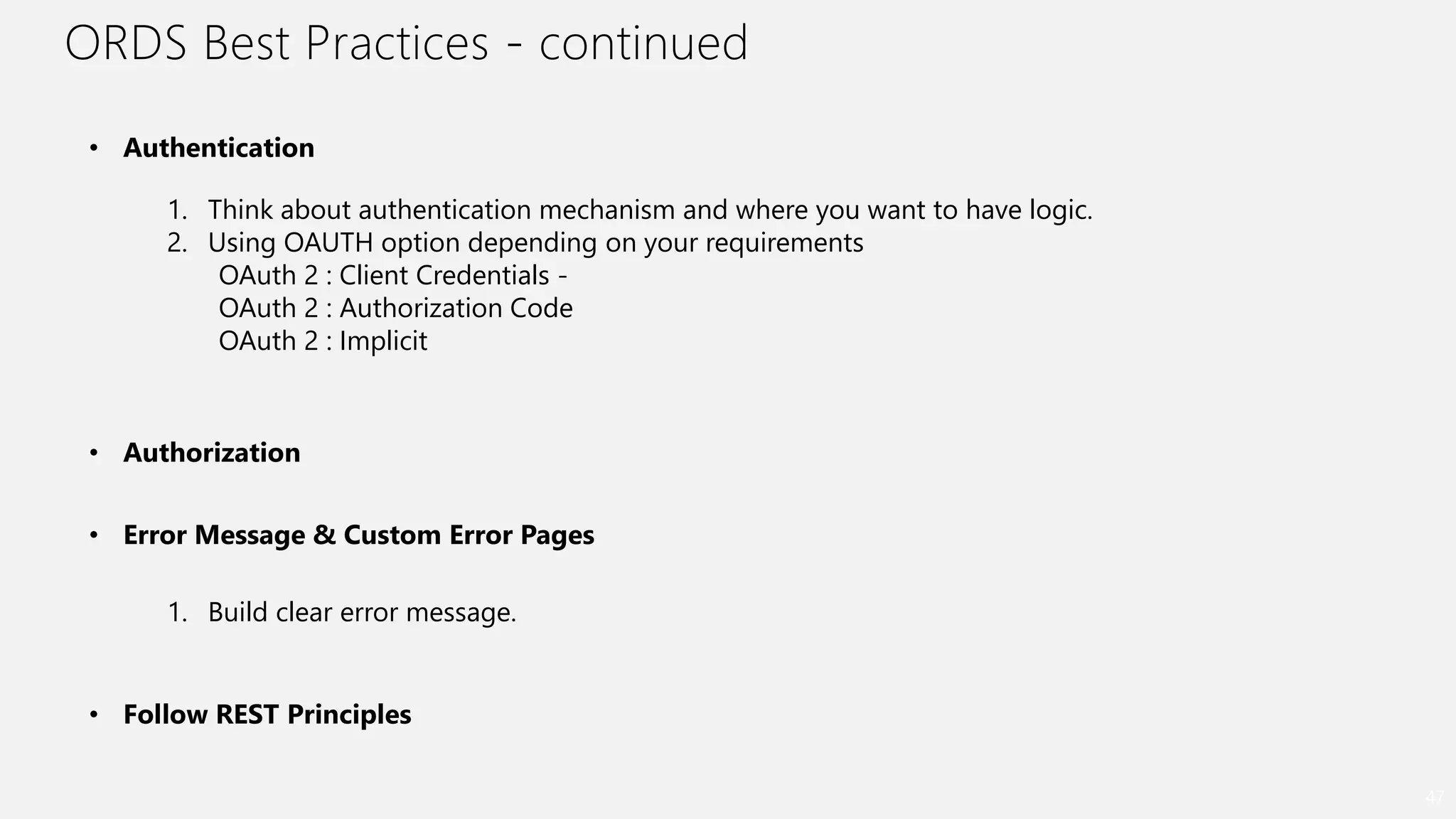
- Best practices for using ORDS, including defining modules and templates, mapping URLs to SQL, connection pooling, and publishing APIs.
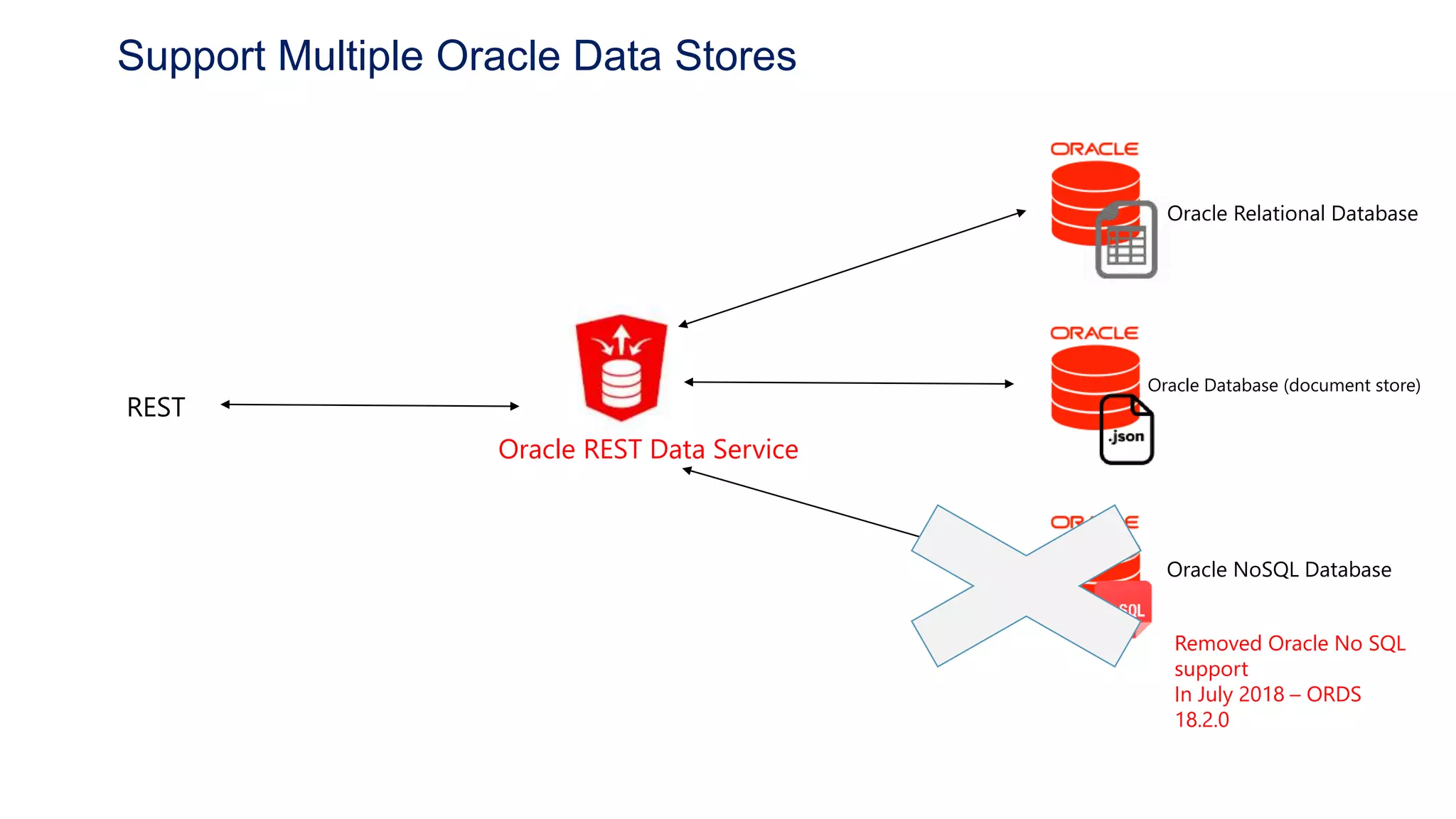
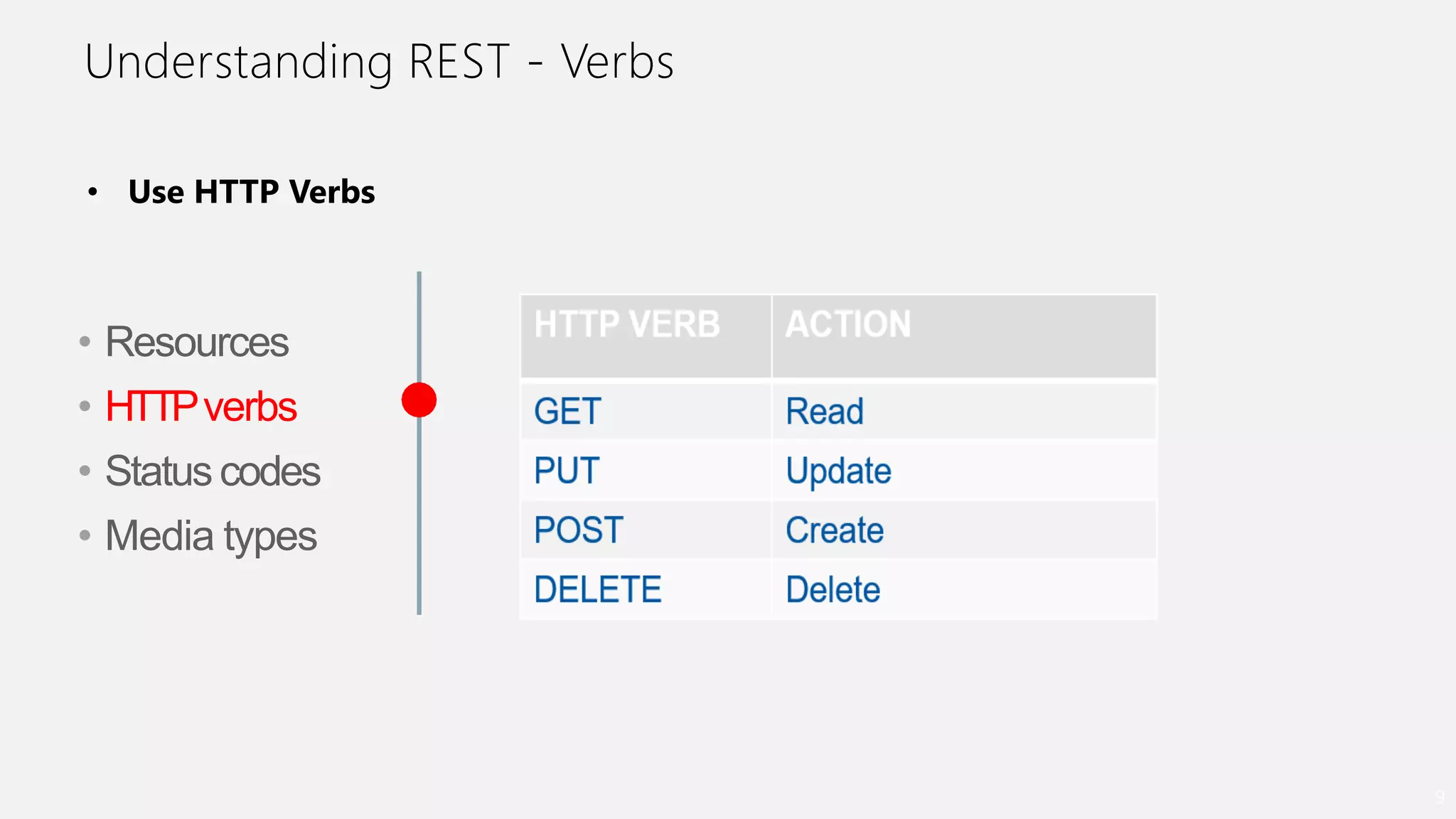
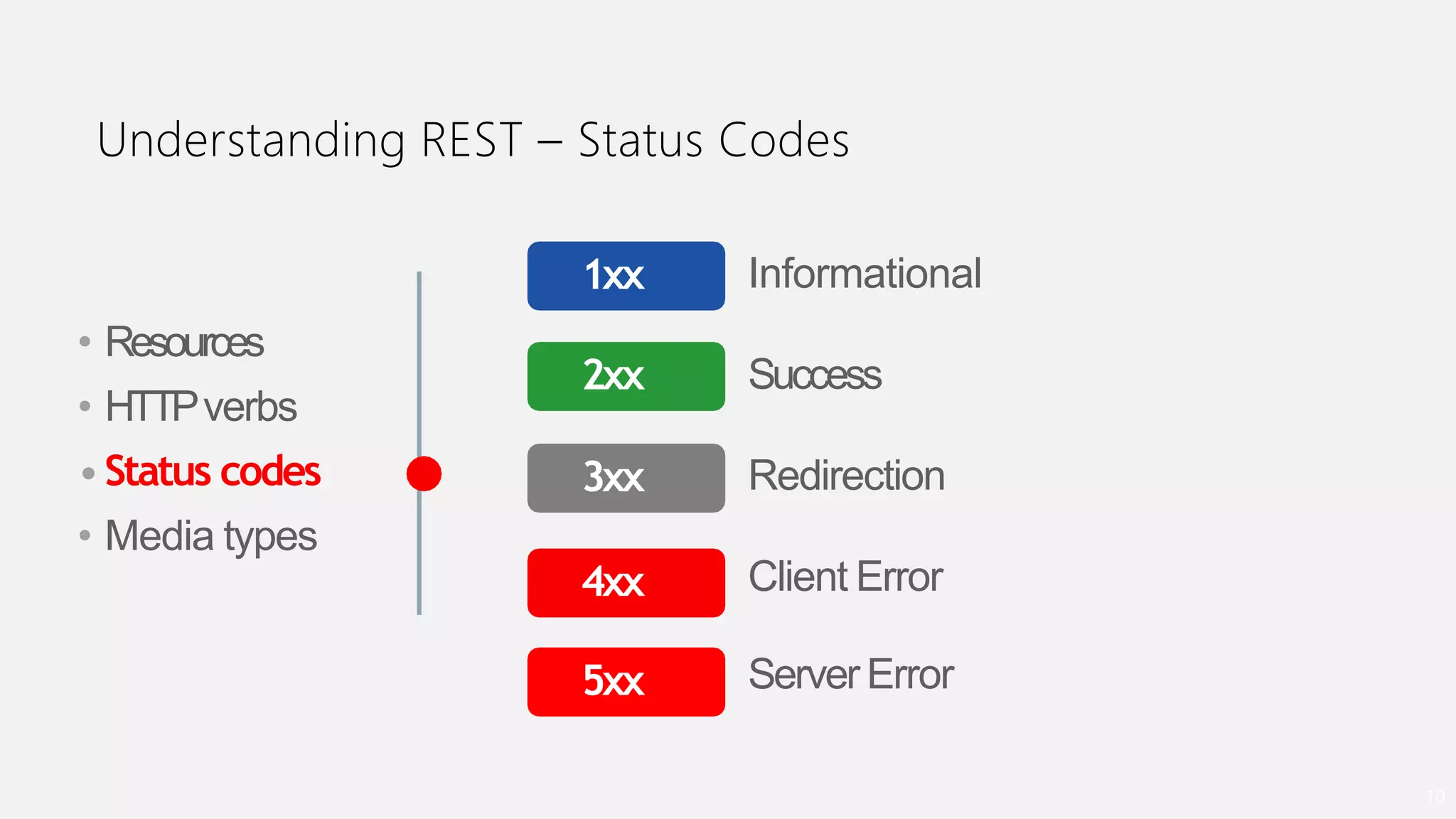
- How ORDS enables RESTful access to relational database content by allowing developers to declaratively map HTTP methods like GET, POST, PUT, DELETE to SQL operations.






![20
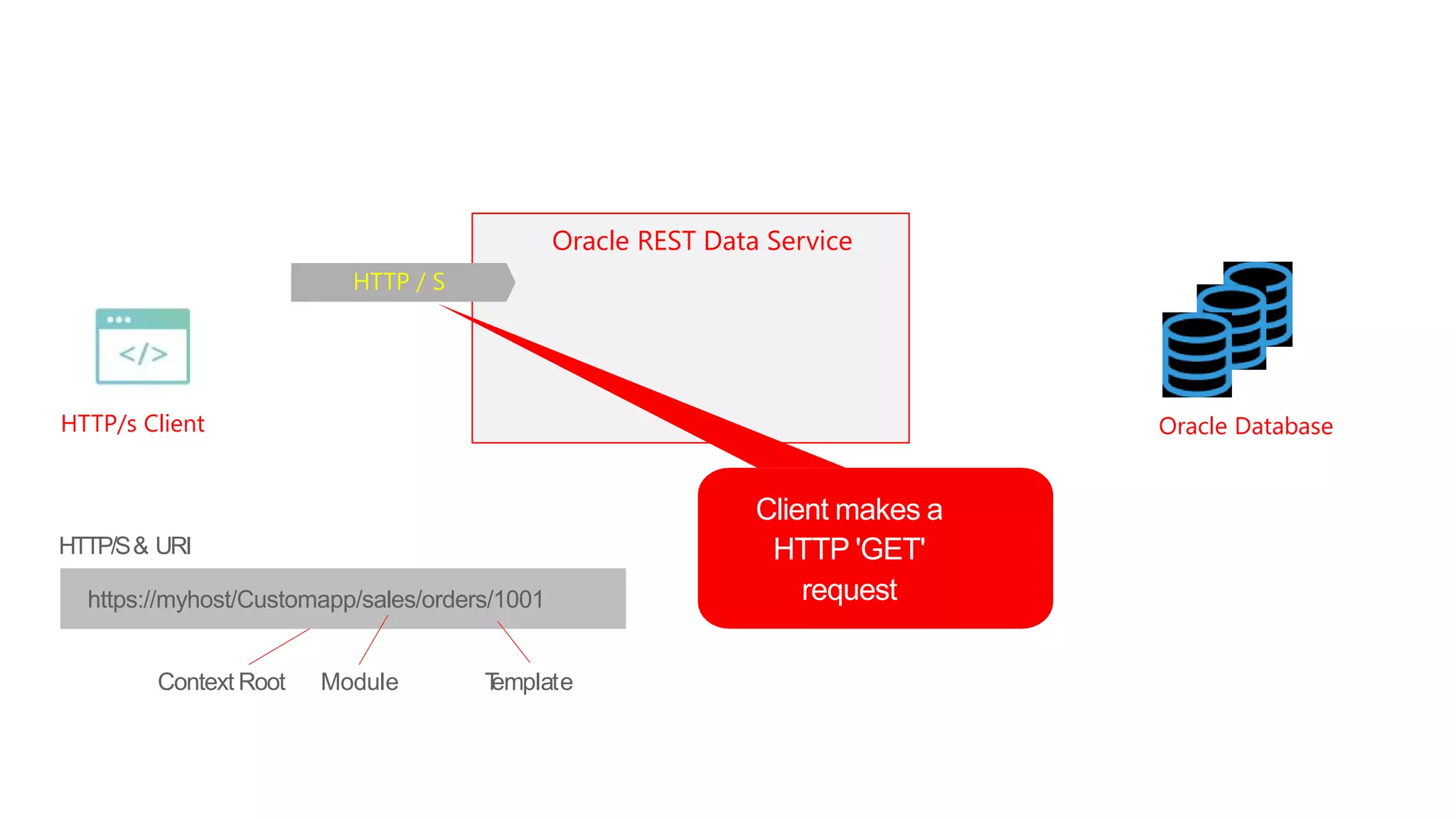
HTTP/s Client Oracle Database
Oracle REST Data Service
Client makes a
HTTP 'GET'
requesthttps://myhost/Customapp/sales/orders/1001
HTTP/S& URI
Module TemplateContext Root
ORDSmapsto
"ORDERS"SQL
SELECT*FROM
ORDERSWHERE
ORDERNO=:b1
HTTP / S Map and BindMap andBind SQL
DBreturns
result set
{"orderno": 1001,
"name": "ScottKing",
"address": "500 Main street,
Innovation CA", "items": [{
"itemno": 404,"quantity":7,
"status": "in process"},
{"itemno": 303,"quantity": 32,
"status": "closed"} ]}
Transform to JSON,
CSV, Excel or Binary
ResultSetTransform](https://image.slidesharecdn.com/exposeyourdataasanapiswithoraclerestdataservices-spoug-180927233113/75/Expose-your-data-as-an-api-is-with-oracle-rest-data-services-spoug-Madrid-20-2048.jpg)
![21
HTTP/s Client
Oracle Database
Oracle REST Data Service
Client makes a
HTTP 'GET'
request
https://myhost/Customapp/sales/orders/1001
HTTP/S& URI
Module TemplateContext Root
ORDSmapsto
"ORDERS"SQL
SELECT*FROM
ORDERSWHERE
ORDERNO=:b1
HTTP / S Map and BindMap andBind SQL
DBreturns
result set
{"orderno": 1001,
"name": "ScottKing",
"address": "500 Main street,
Innovation CA", "items": [{
"itemno": 404,"quantity":7,
"status": "in process"},
{"itemno": 303,"quantity": 32,
"status": "closed"} ]}
JSON
Response to HTTP
request
Transform ResultSet](https://image.slidesharecdn.com/exposeyourdataasanapiswithoraclerestdataservices-spoug-180927233113/75/Expose-your-data-as-an-api-is-with-oracle-rest-data-services-spoug-Madrid-21-2048.jpg)