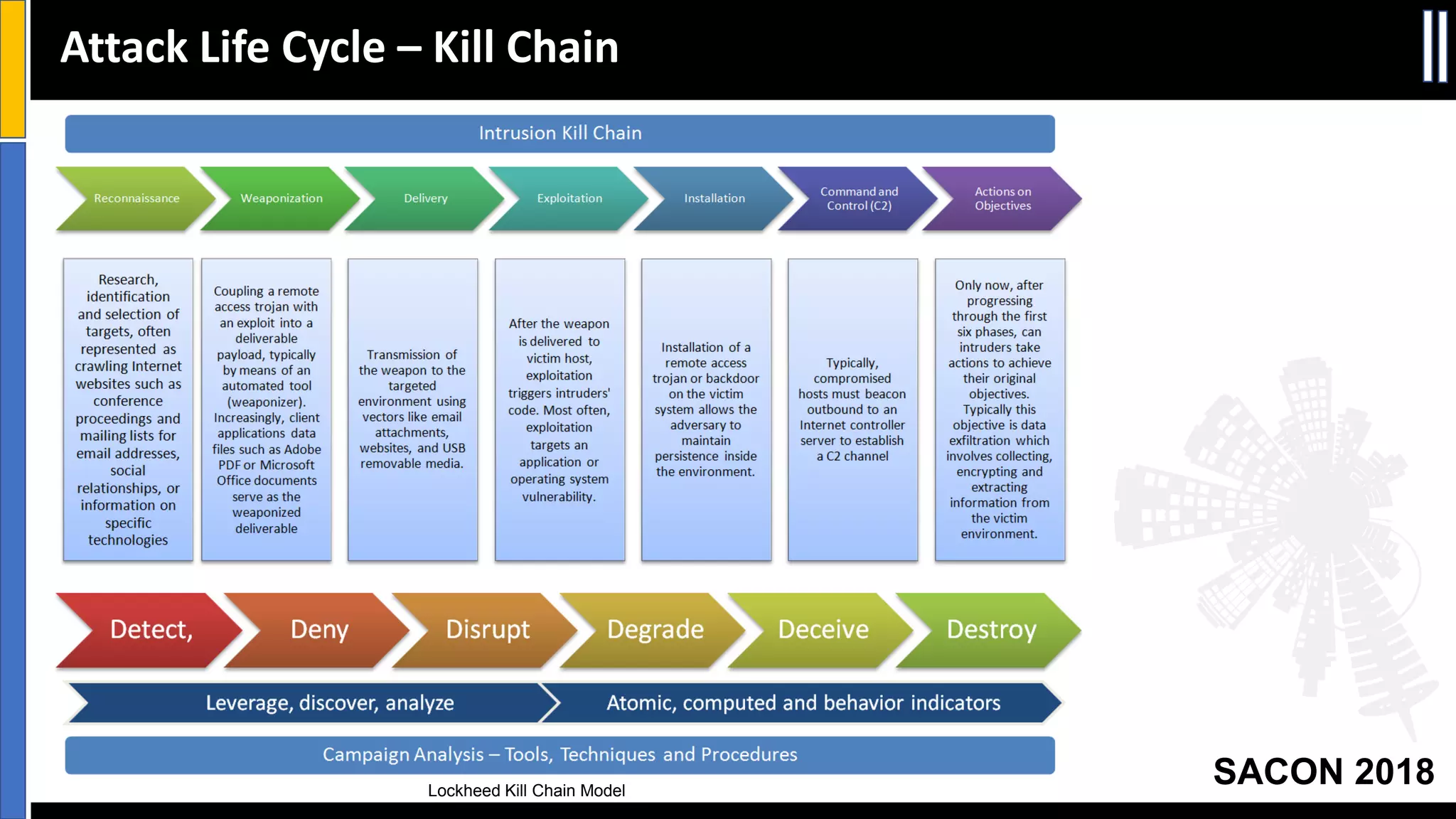
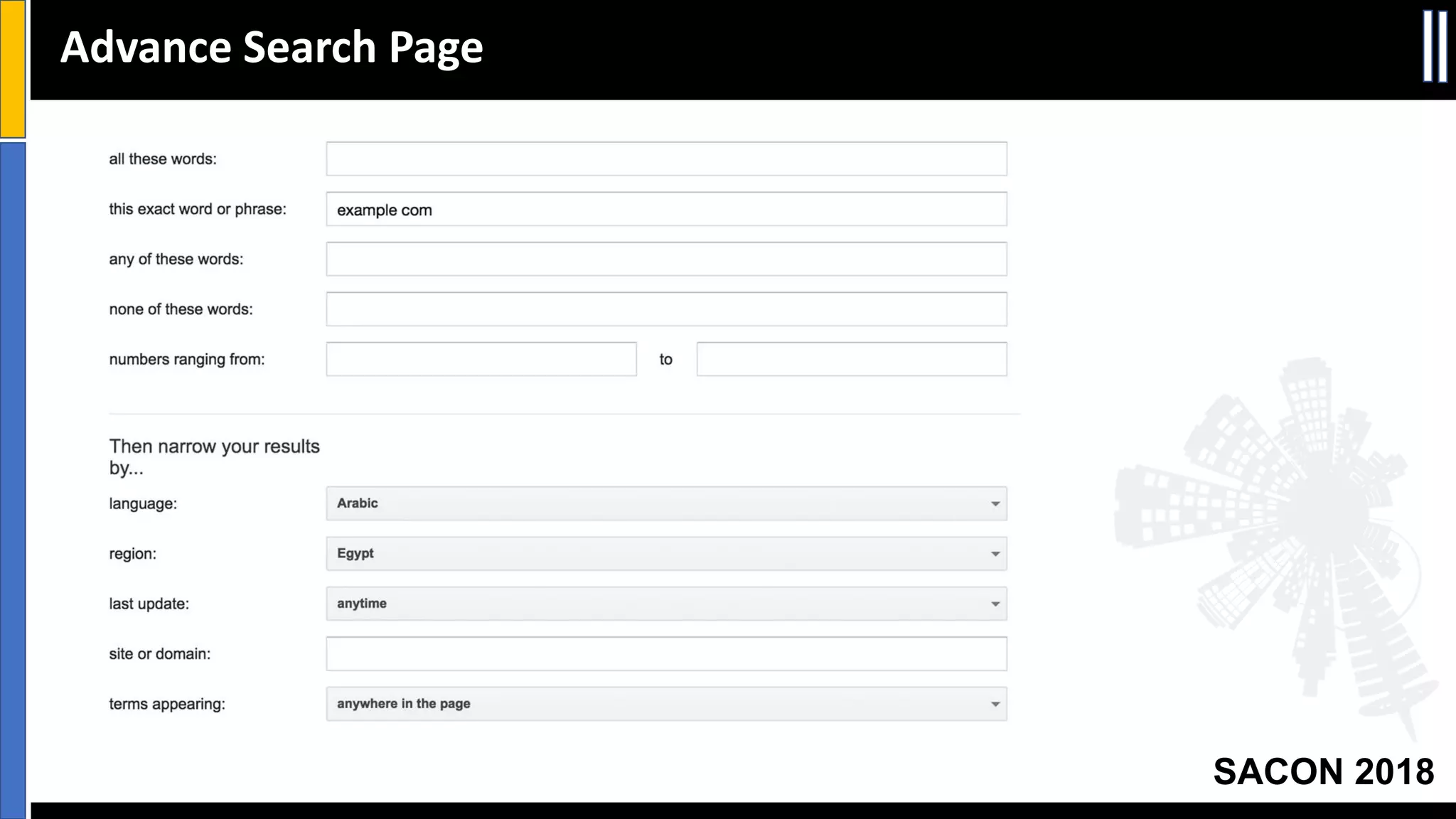
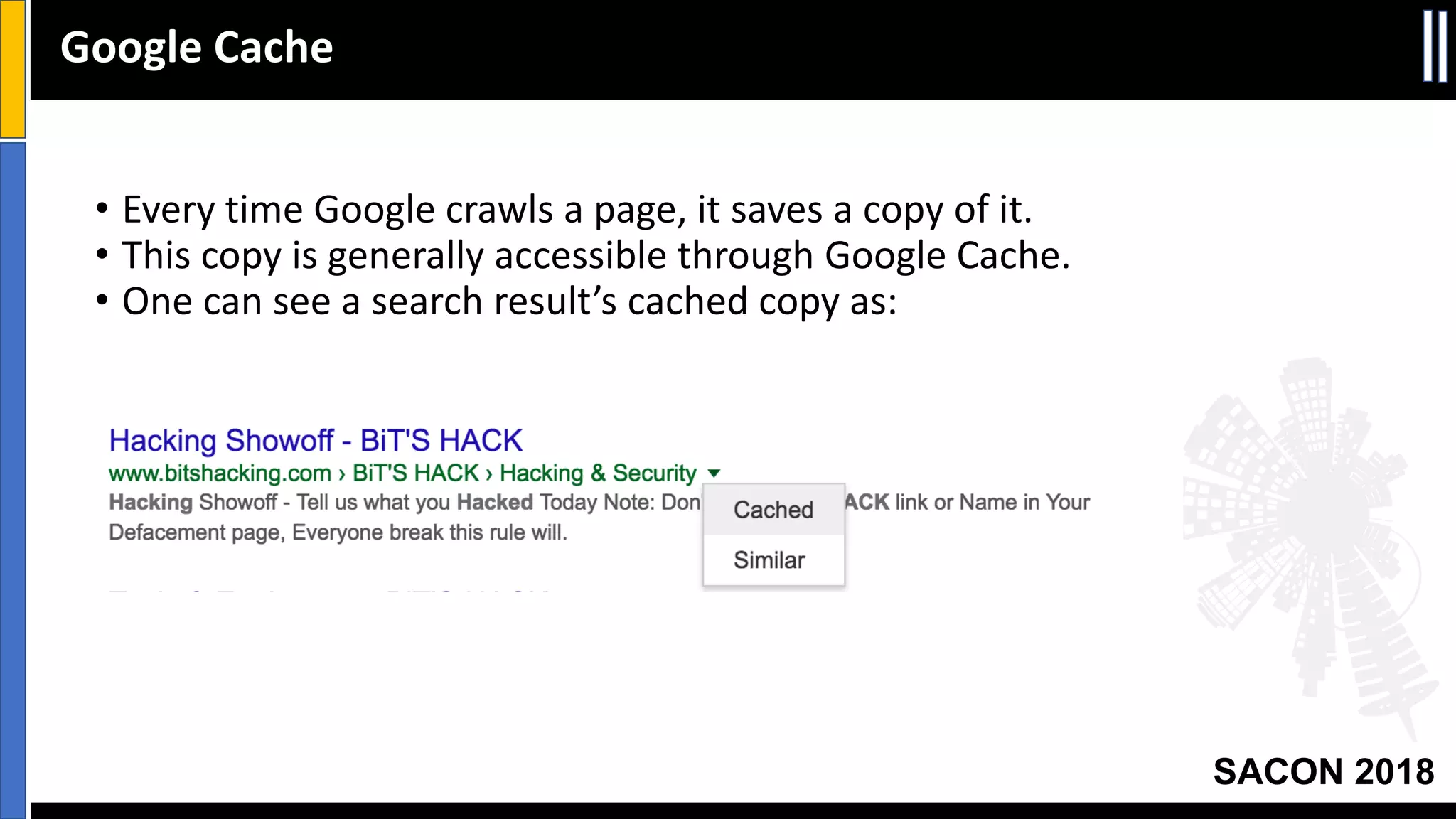
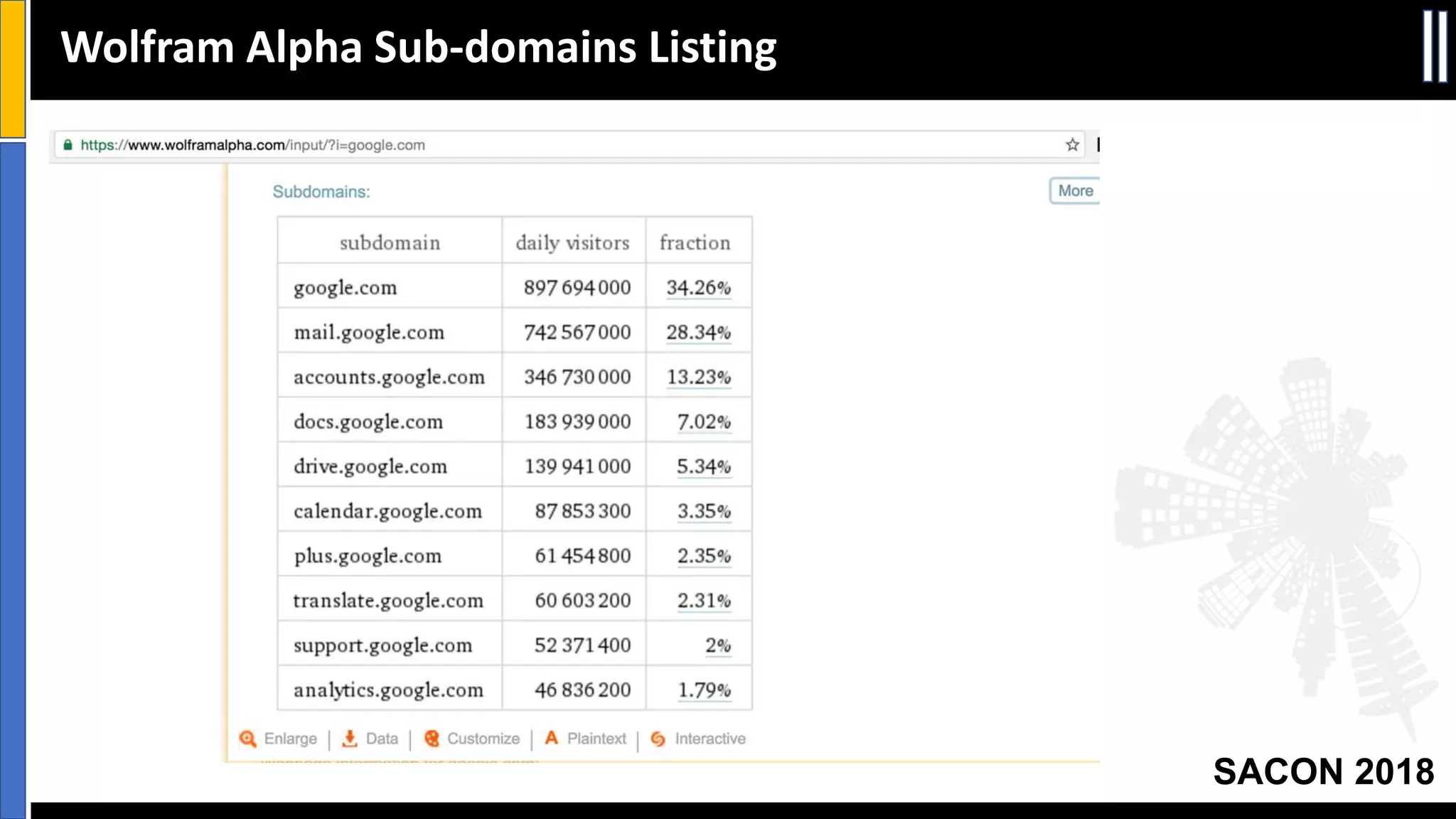
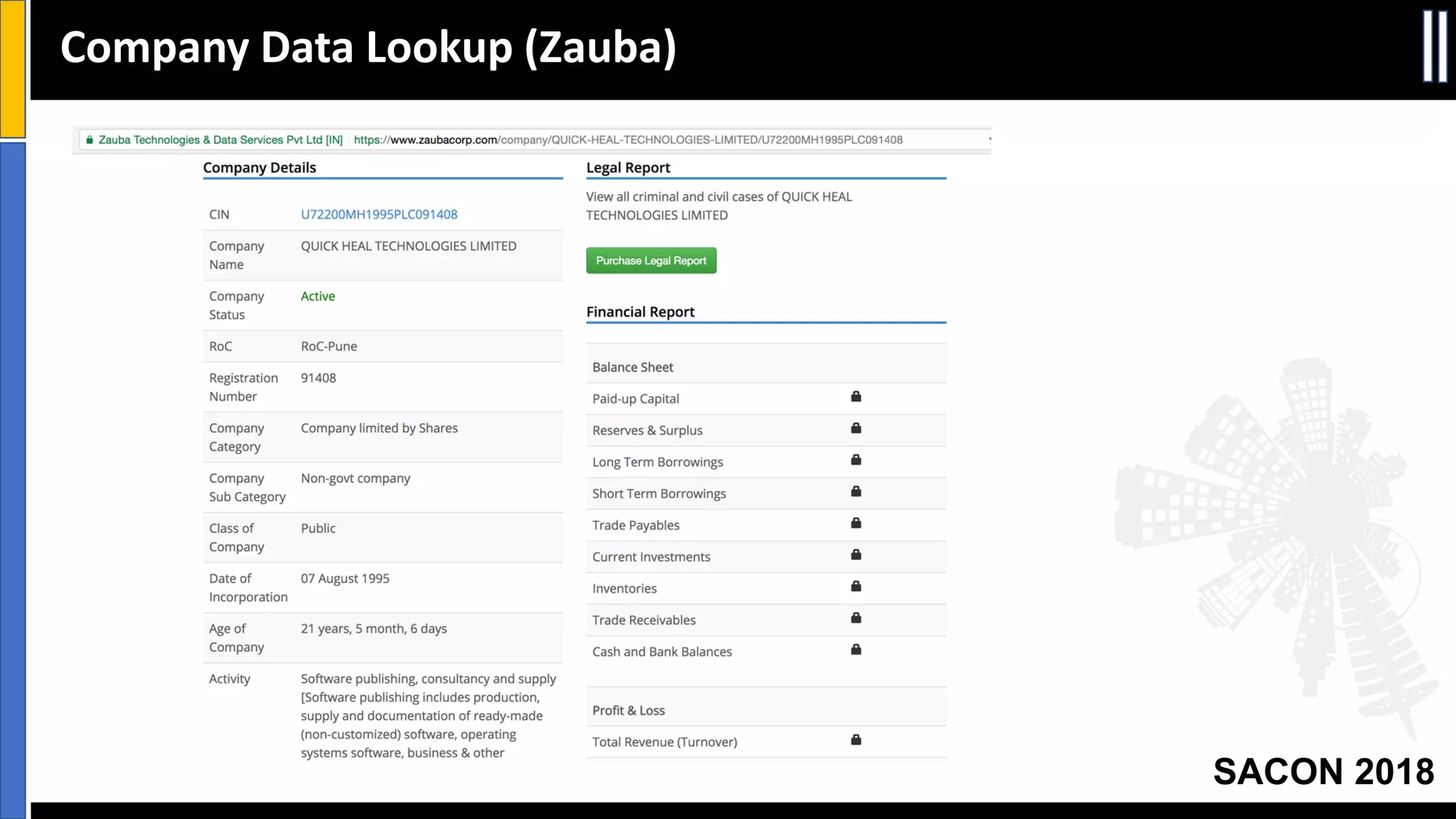
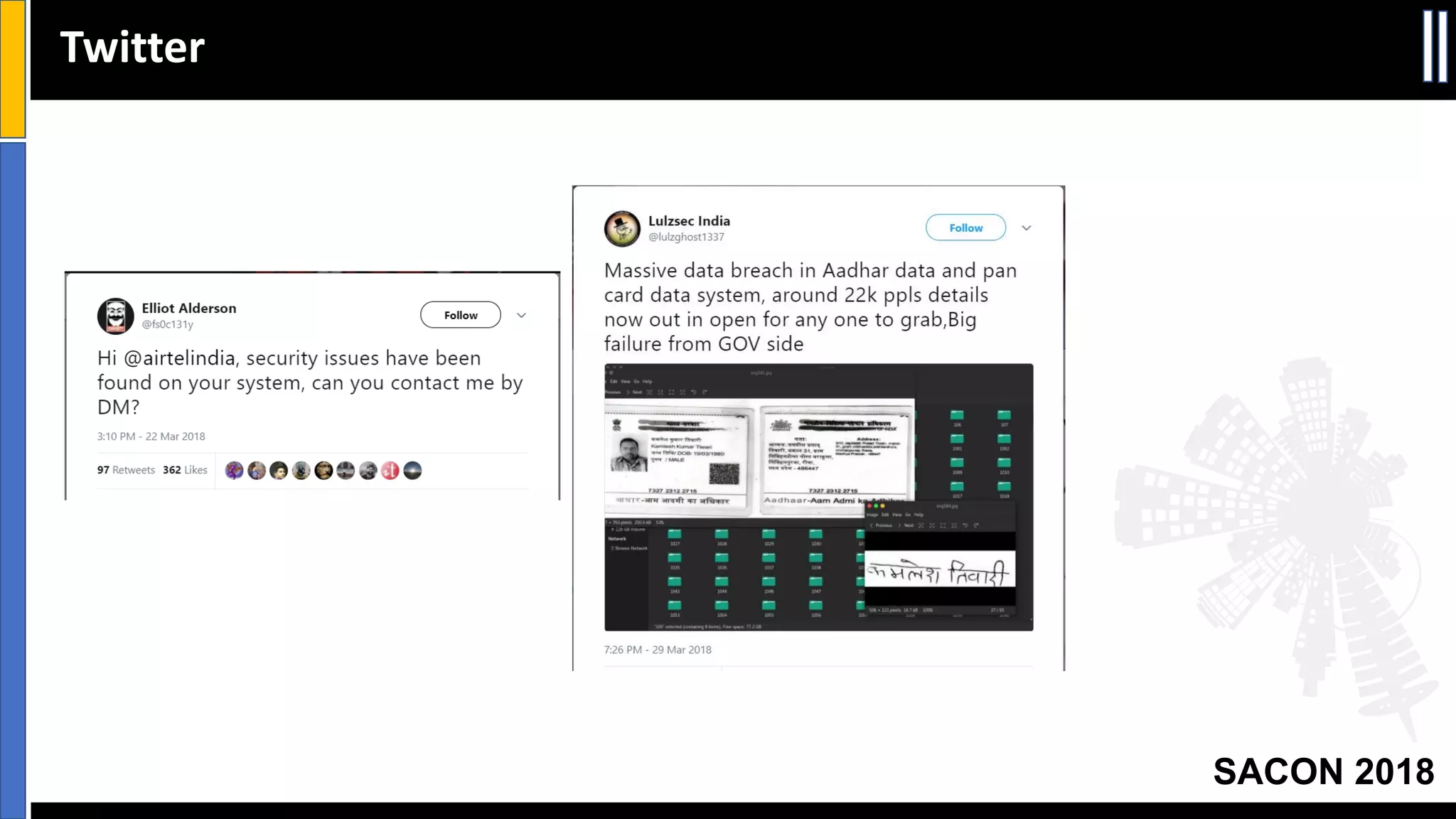
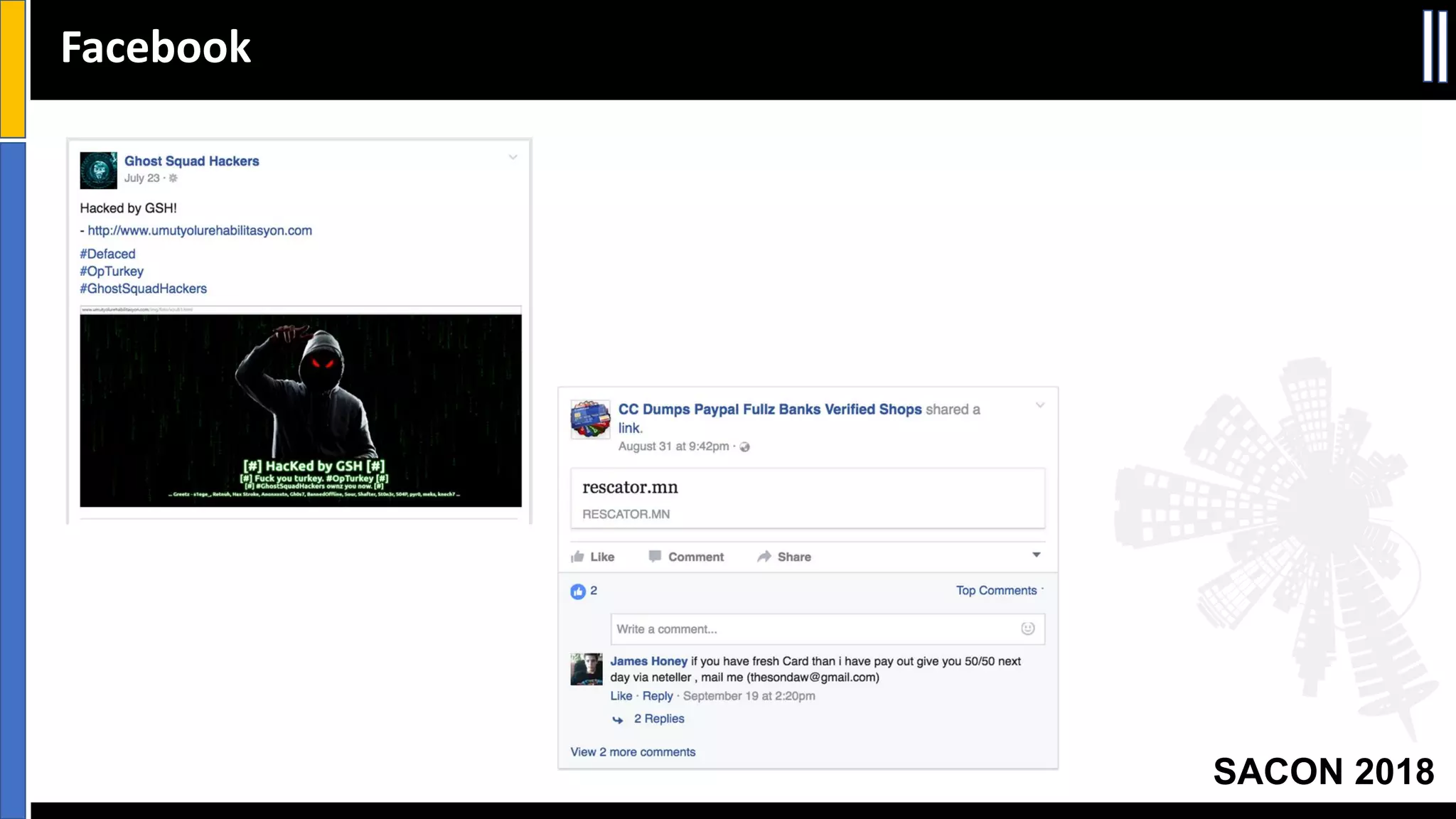
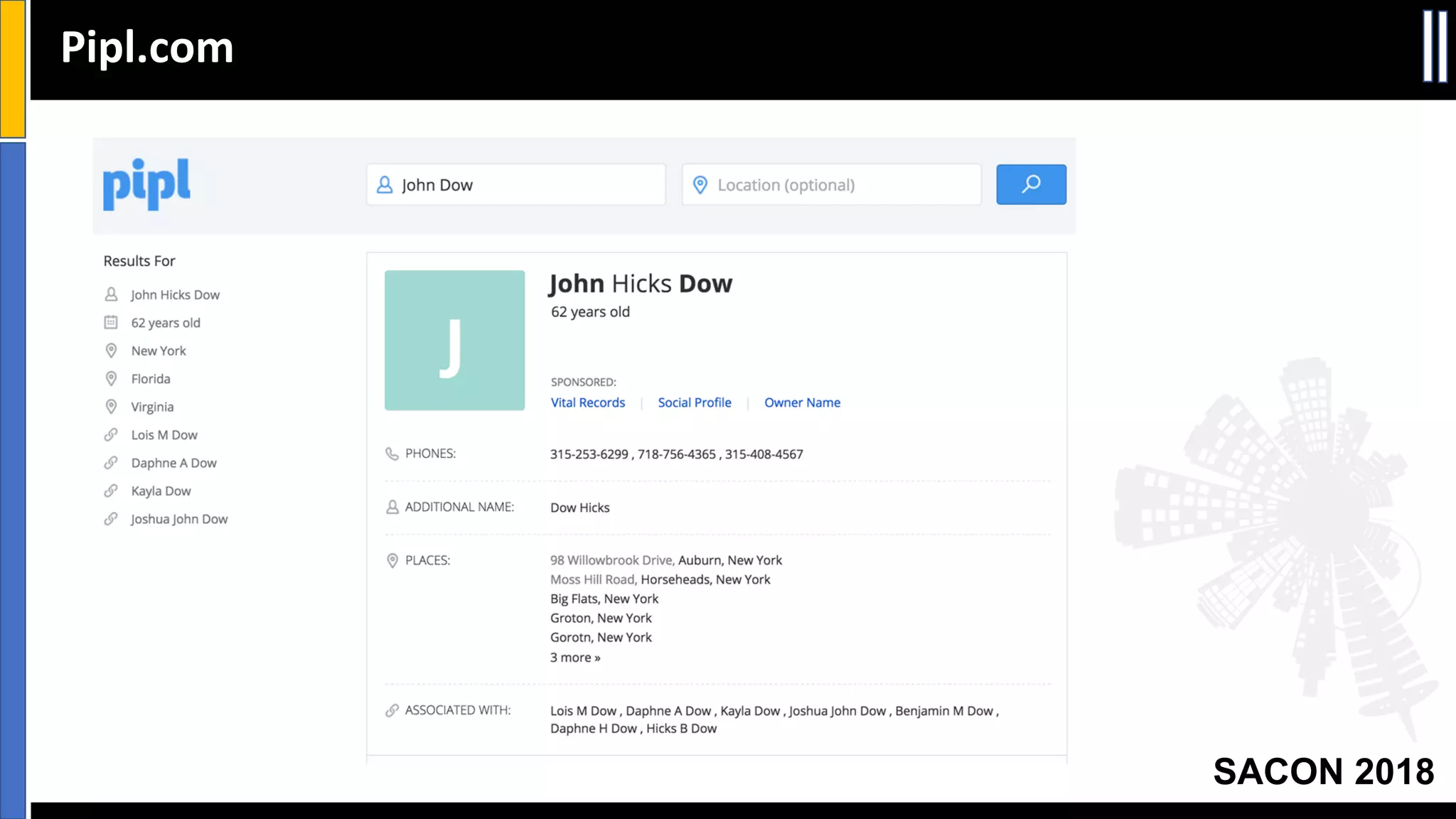
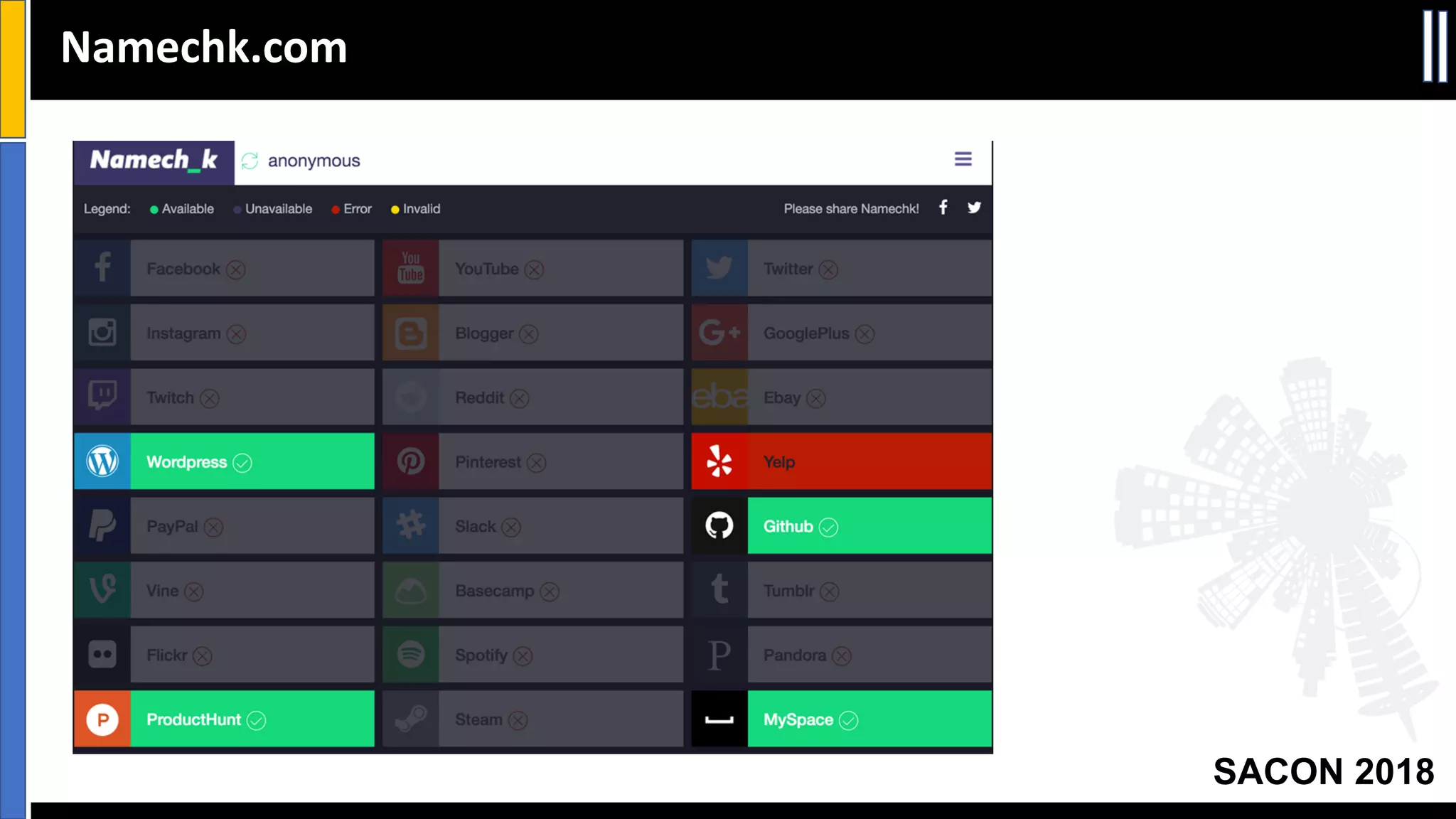
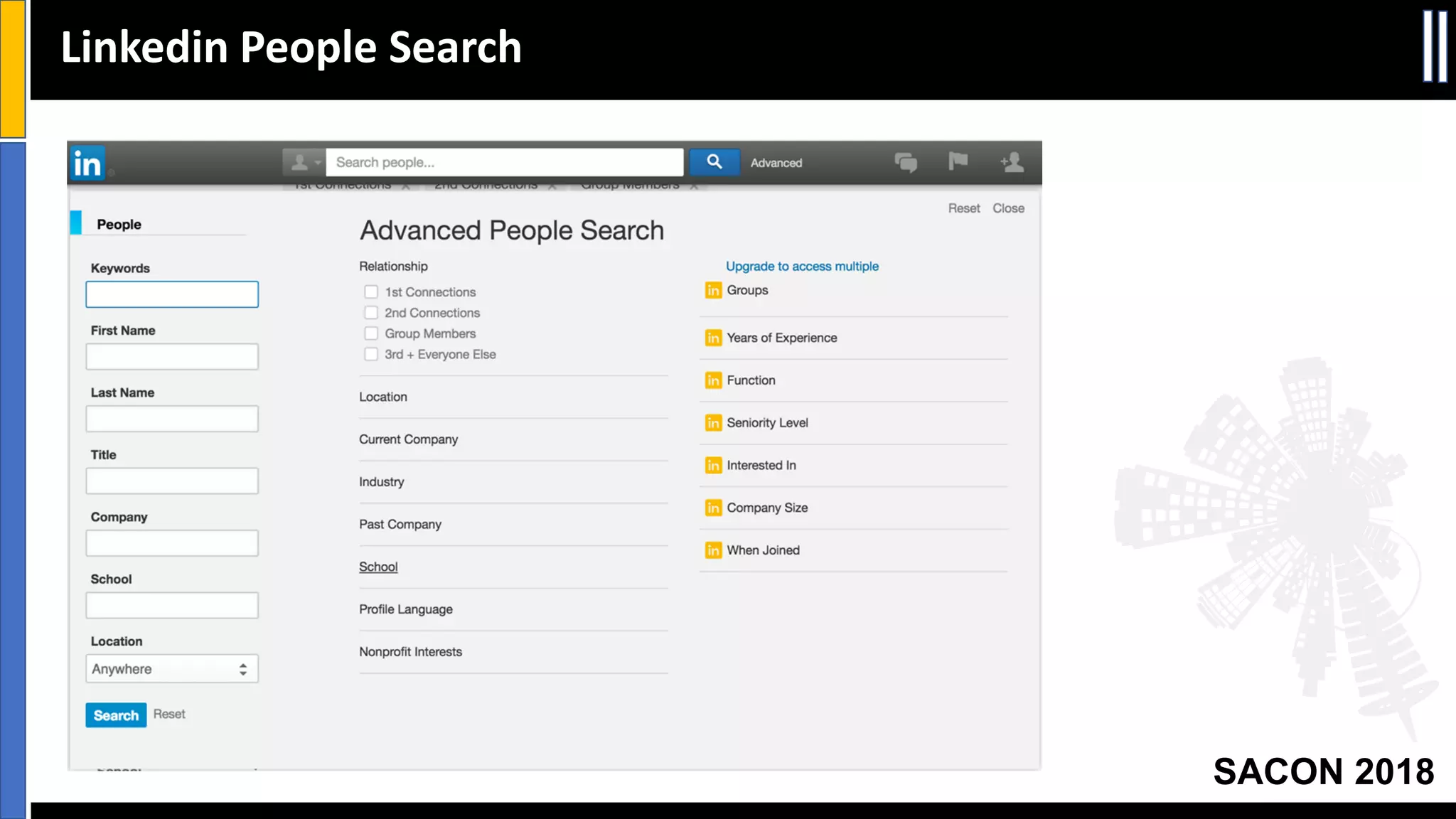
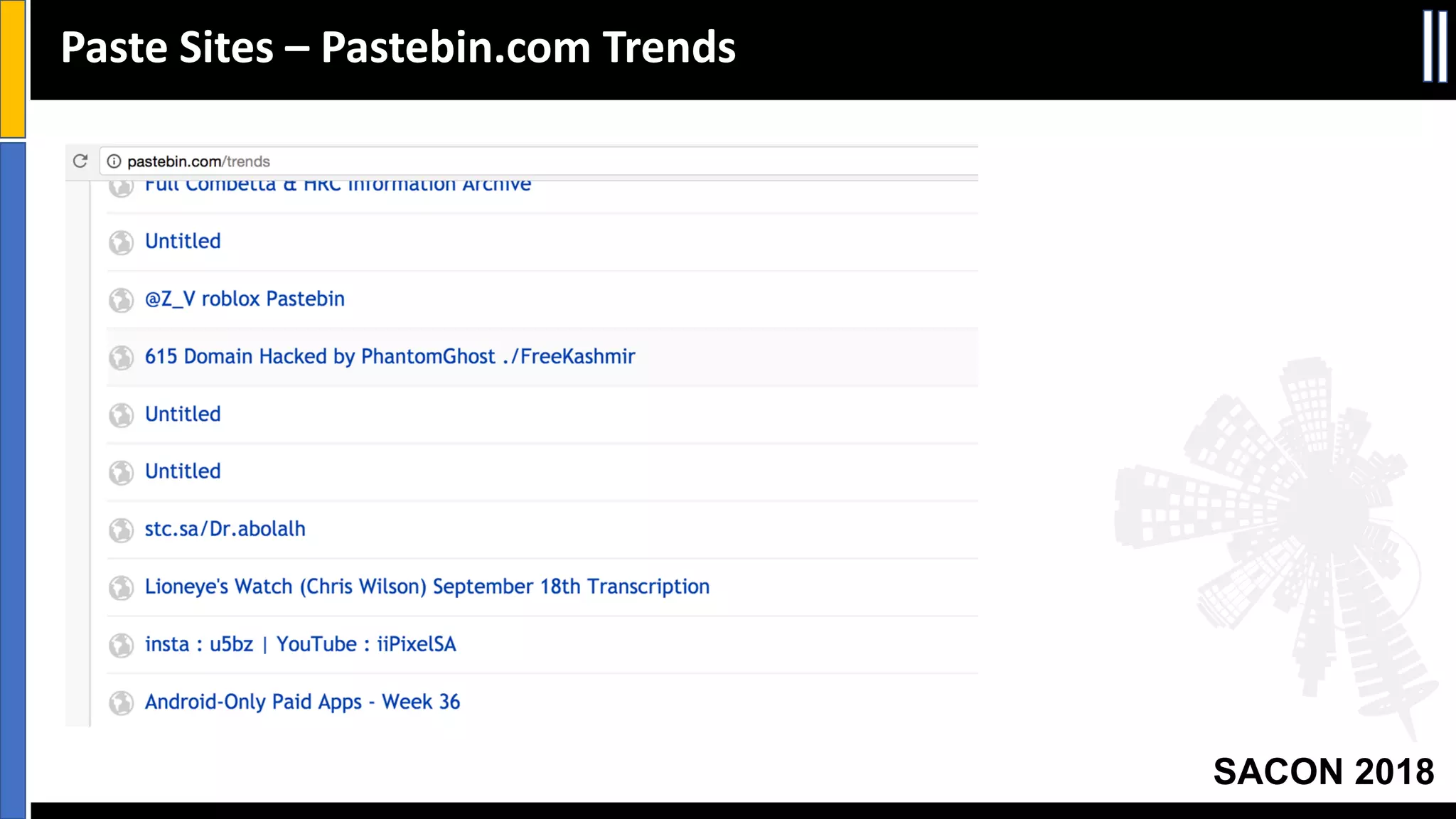
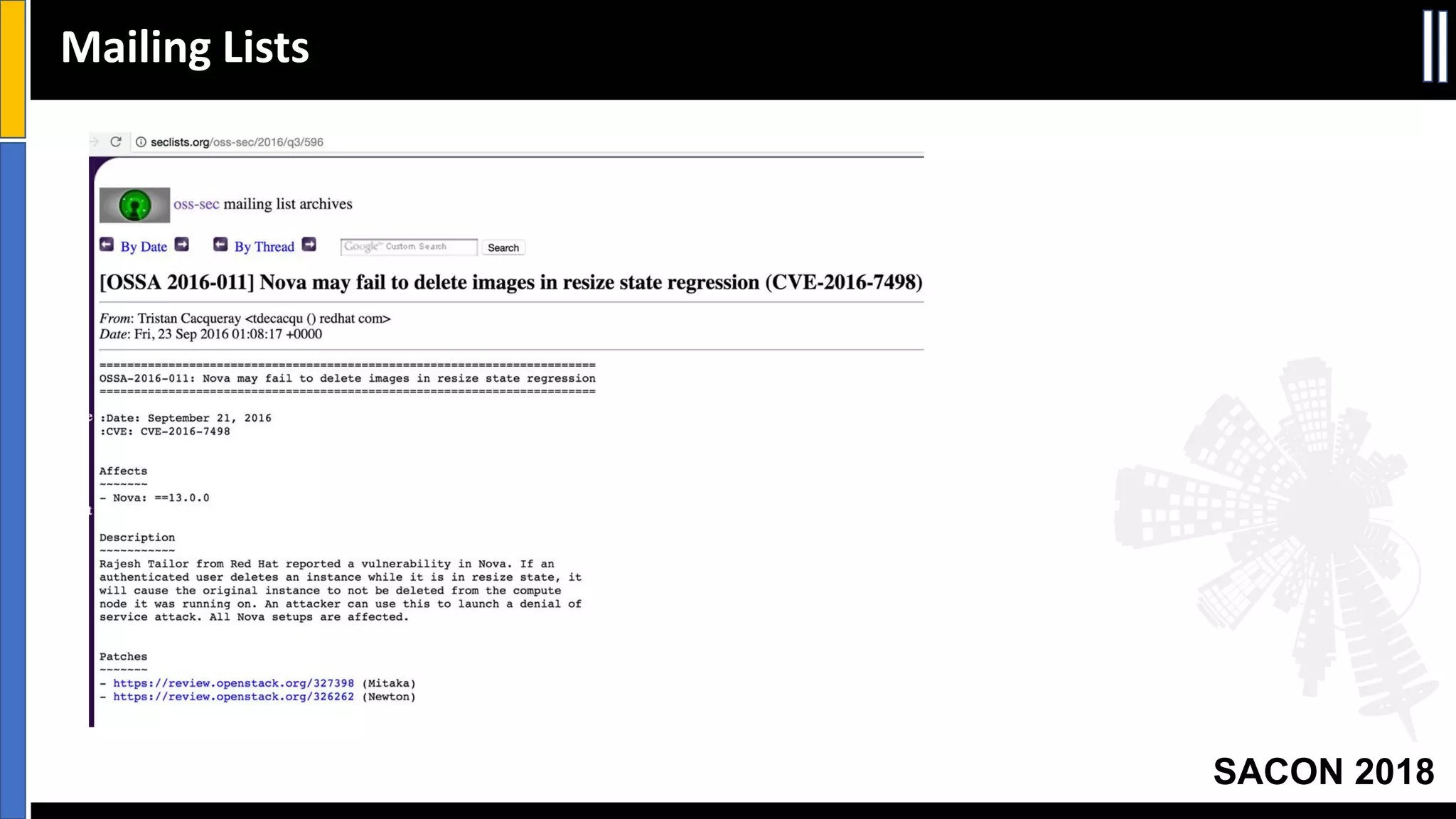
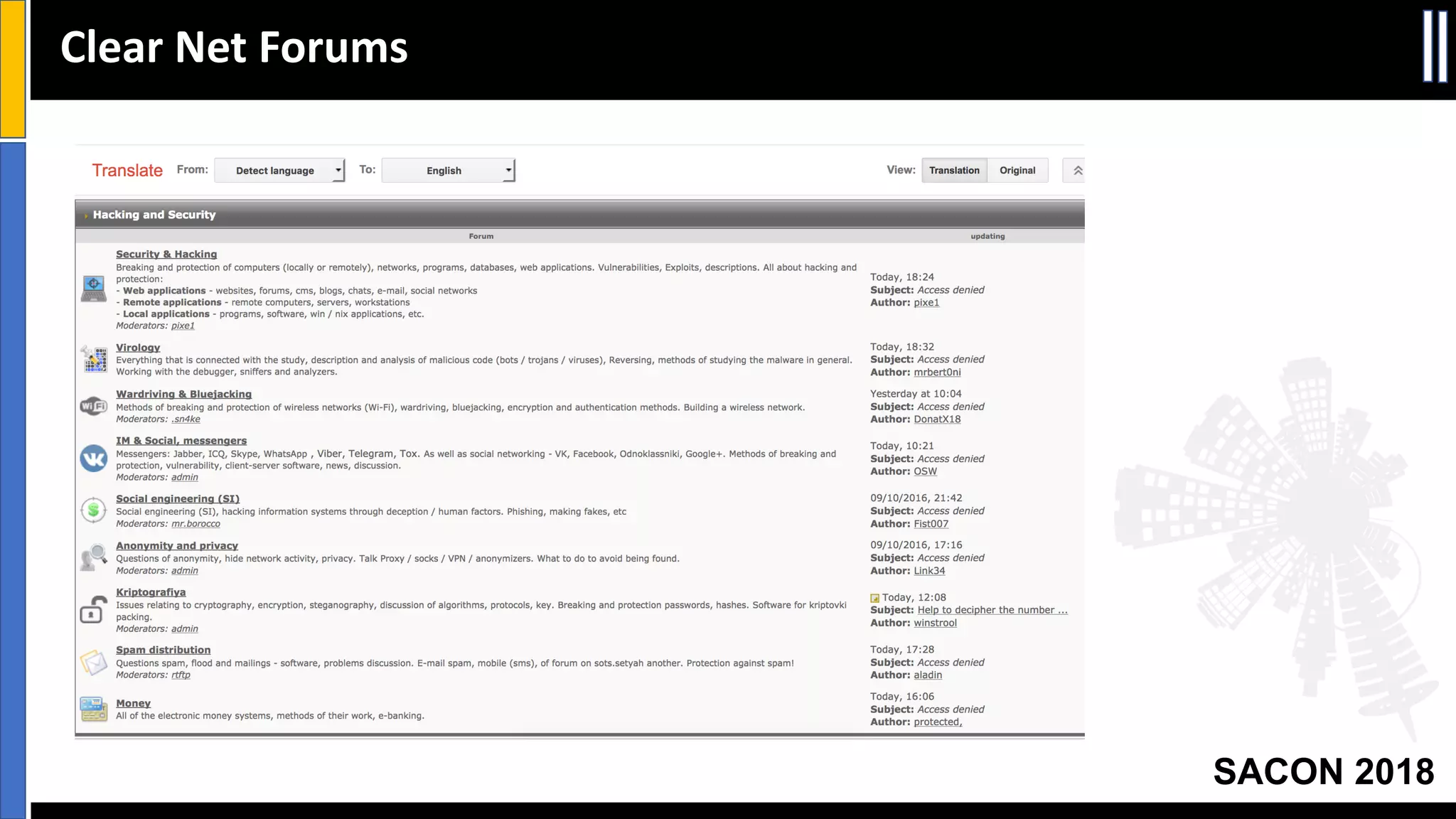
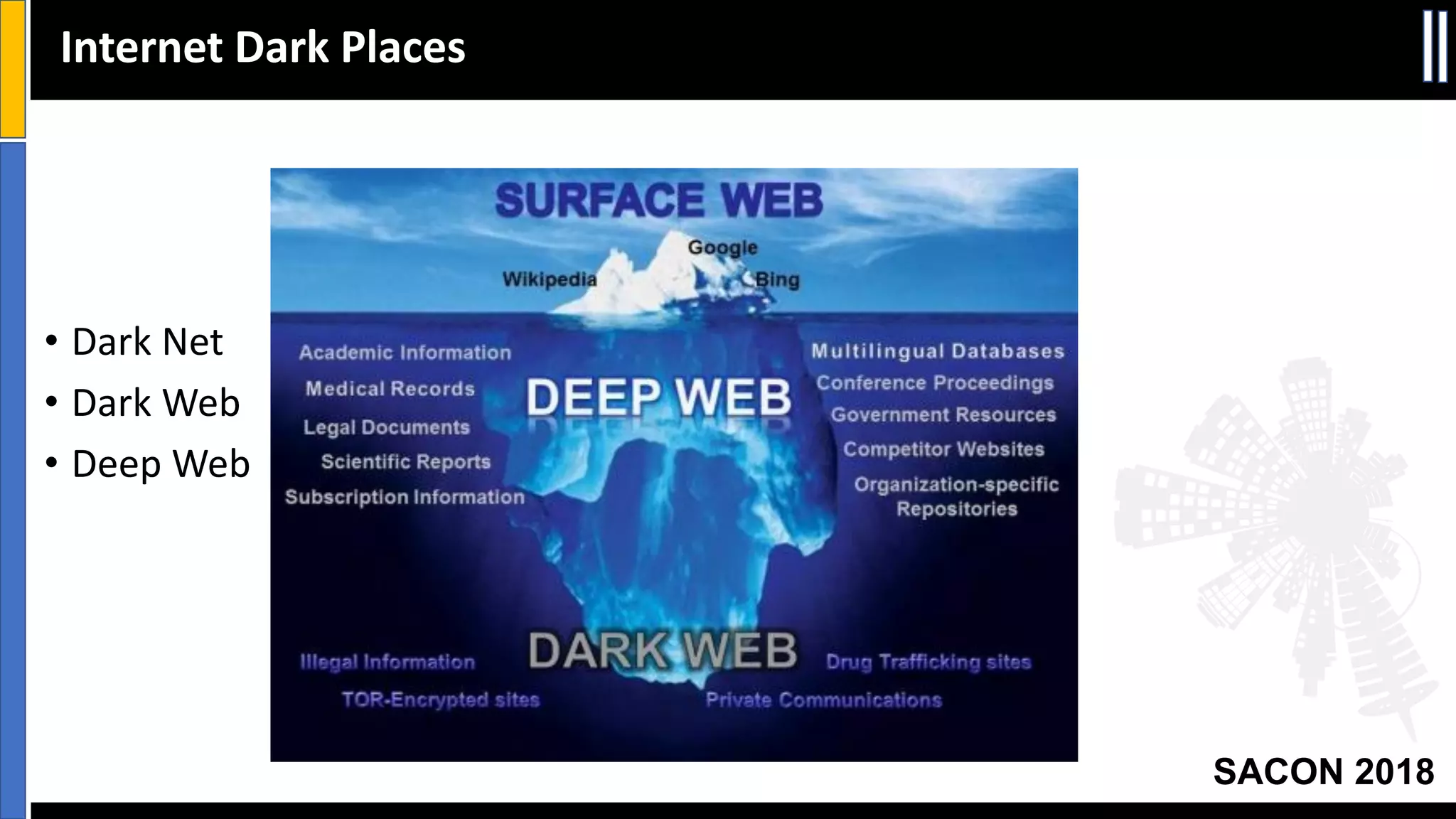
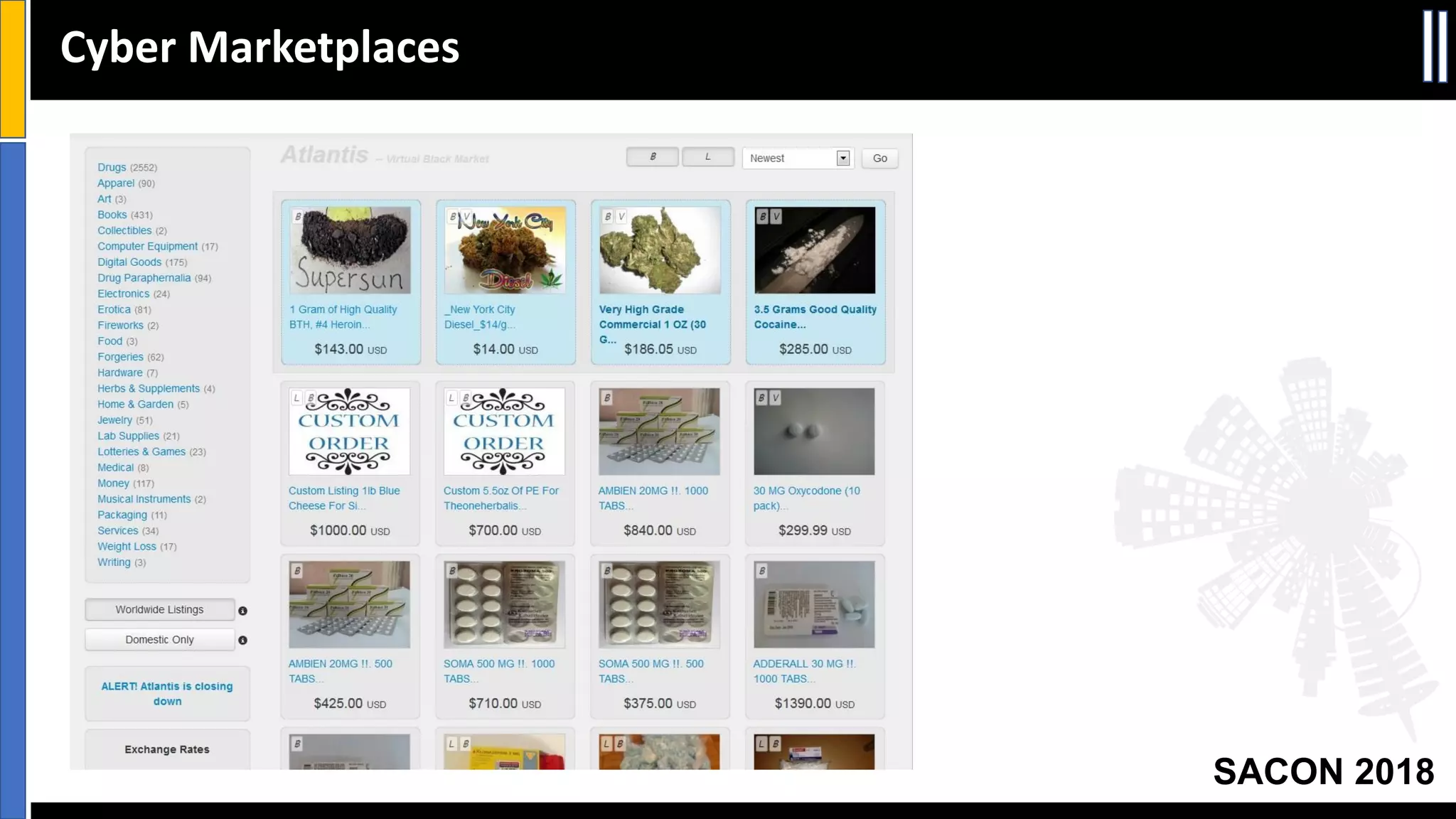
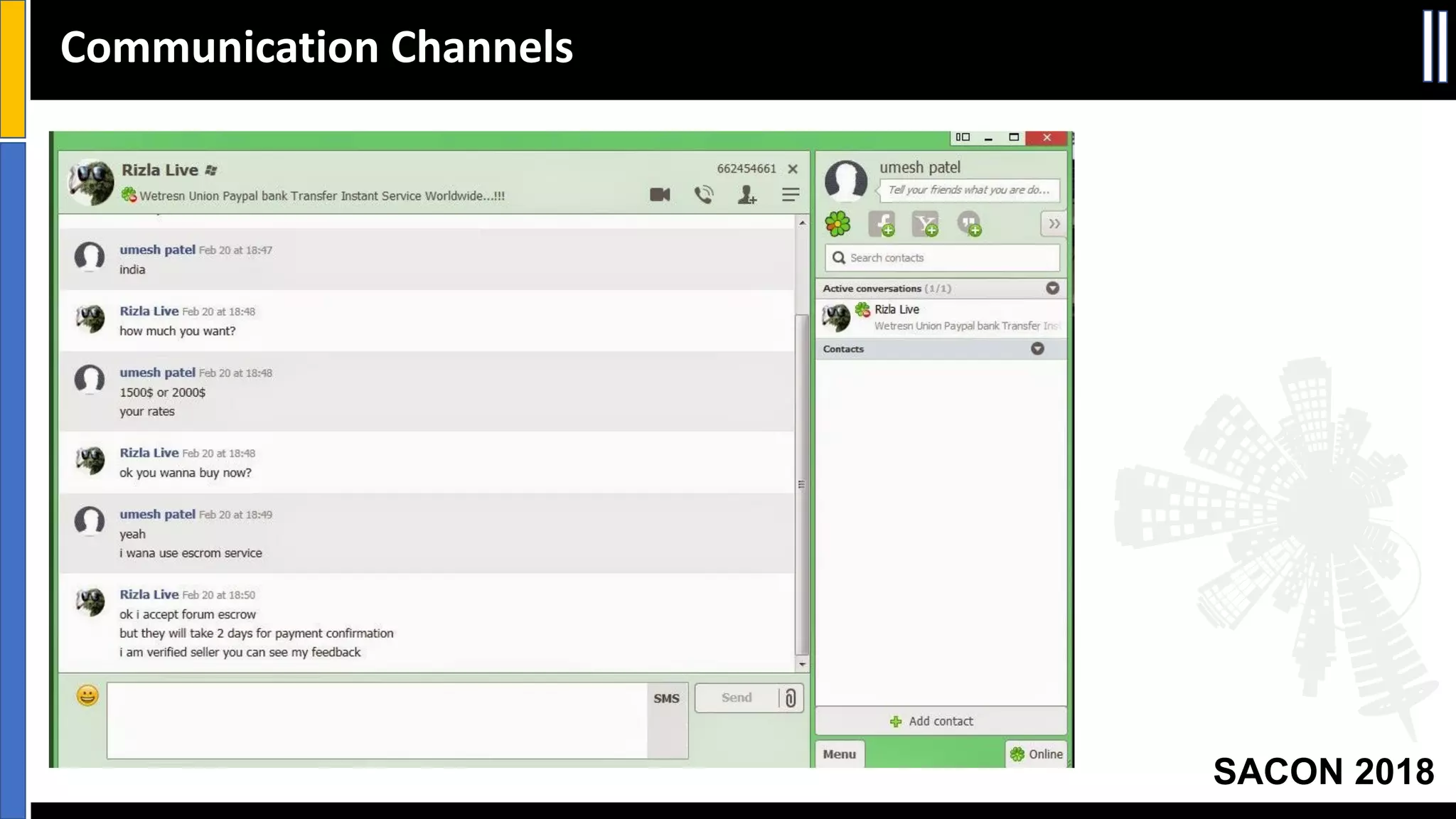
The document presents insights from a conference on cyber threat intelligence and information security held in Pune, India, in 2018. It discusses various types of cyber attacks, including targeted and non-targeted attacks, and emphasizes the importance of threat intelligence, operational security (opsec), and research ethics in managing these risks. Additionally, the document explores tools and strategies for utilizing open source intelligence (OSINT) effectively, as well as best practices for ensuring online privacy and security.