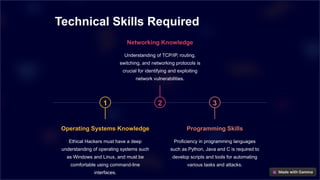
Becoming an ethical hacker requires a mix of technical skills like operating systems knowledge, networking, and programming, alongside non-technical skills such as creativity, attention to detail, and communication. The role is crucial for improving cybersecurity by identifying vulnerabilities and preventing data breaches. As cyber threats grow, ethical hackers play a vital role in protecting sensitive information in an increasingly interconnected world.