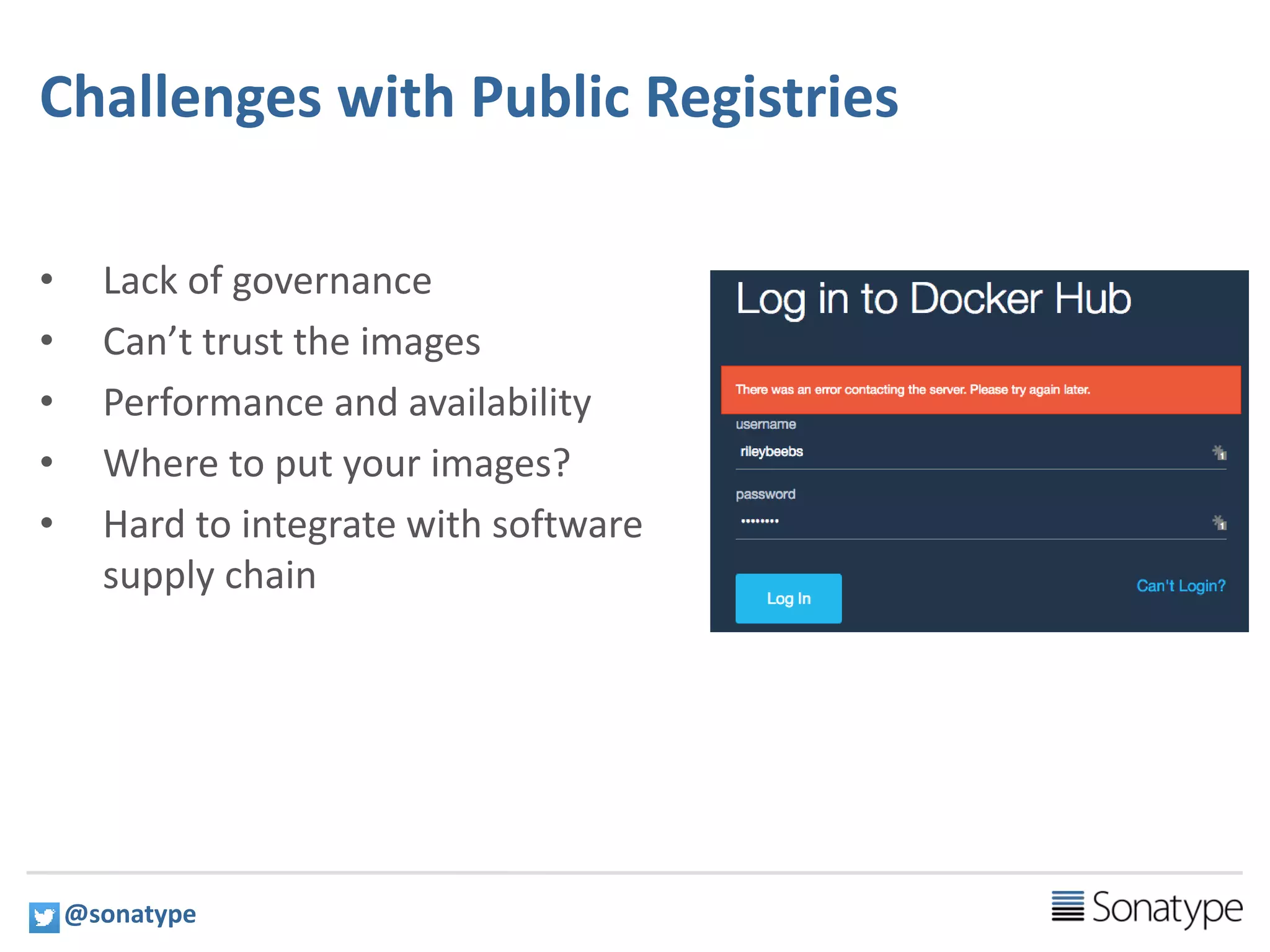
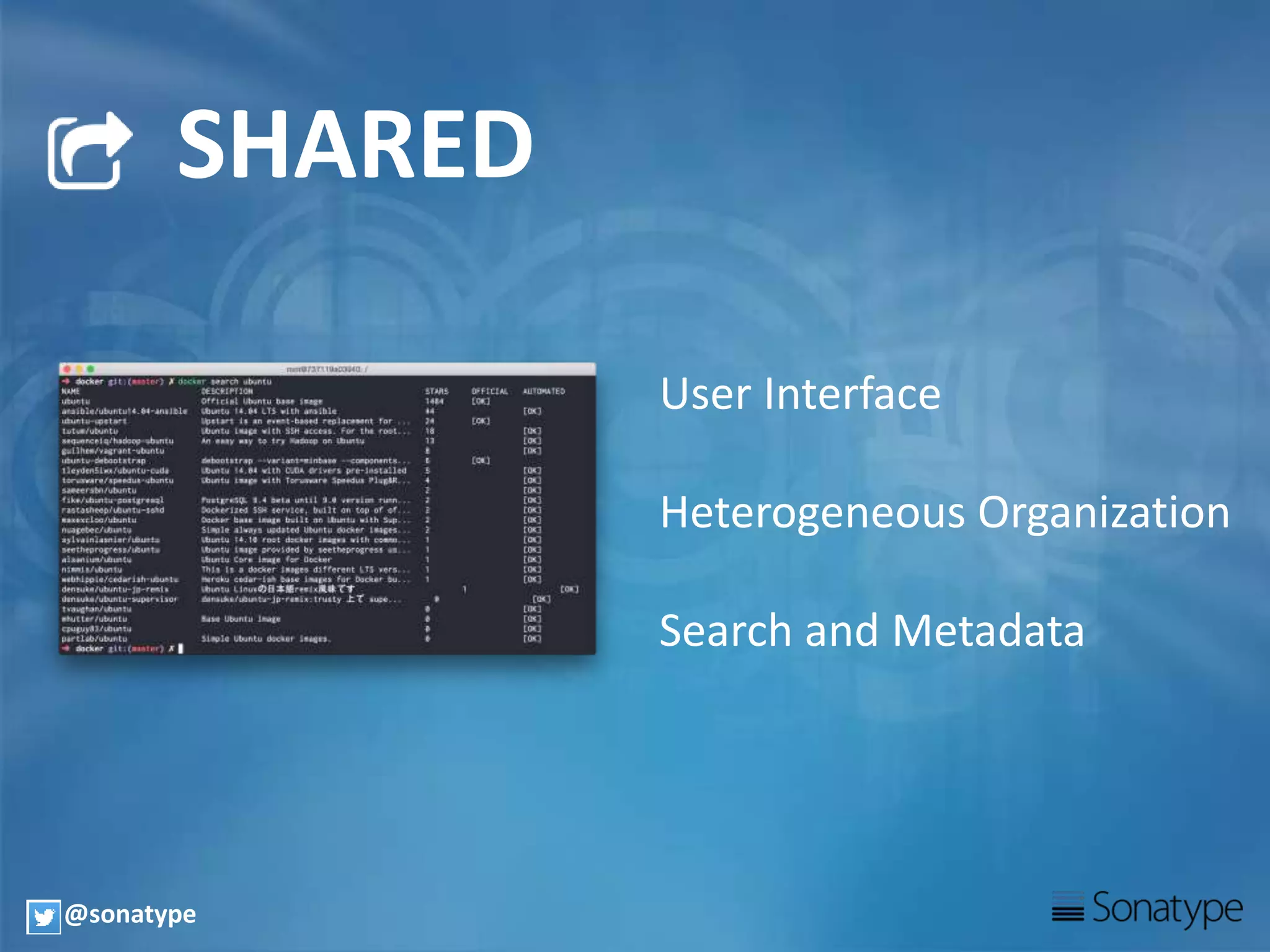
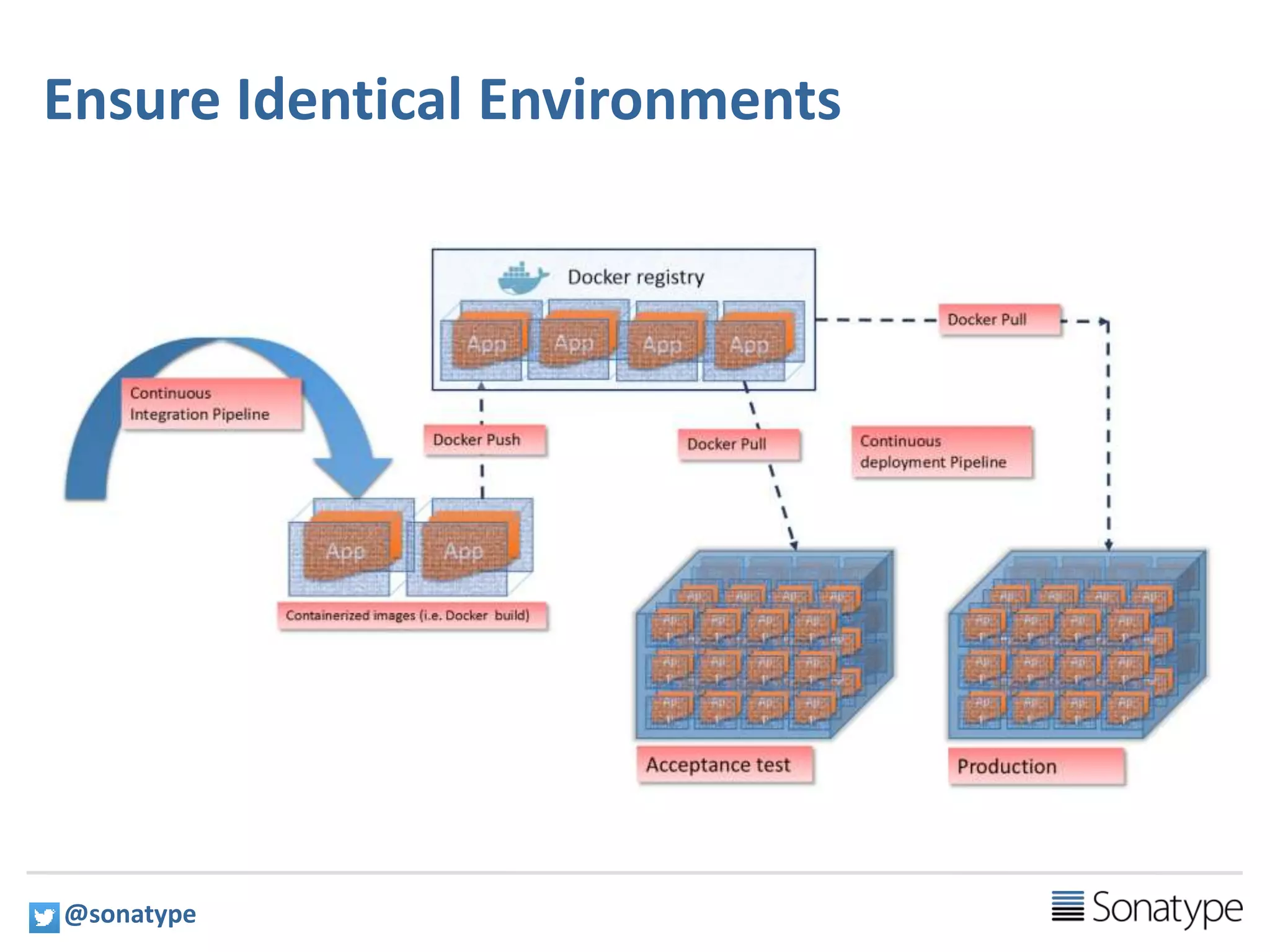
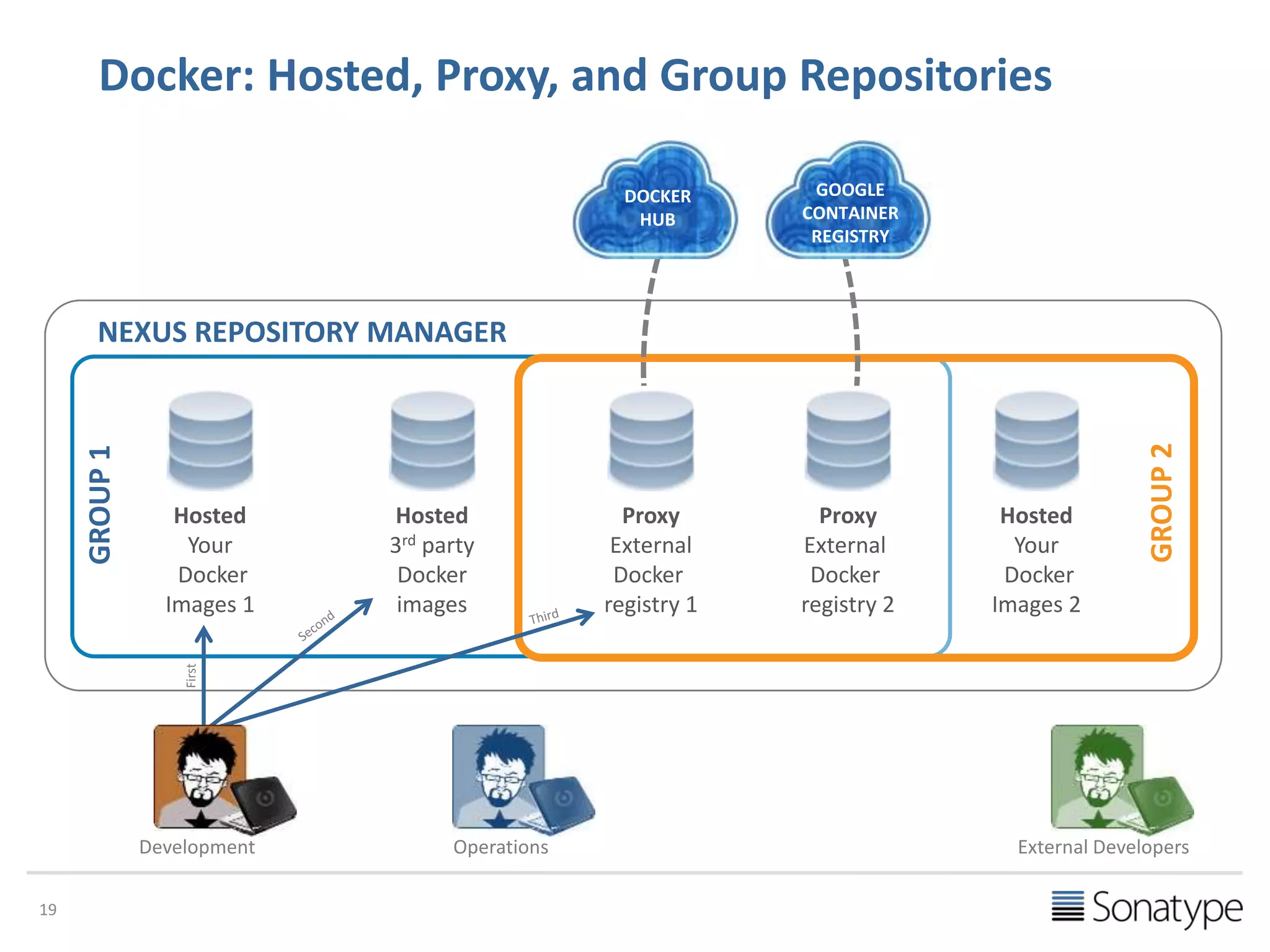
The document discusses the necessity of a premium private Docker registry for running Docker in production environments, citing challenges associated with public registries such as governance, trust, and integration. It emphasizes the need for features like consistency, governance, high availability, and integration with the software supply chain. The presentation also outlines the capabilities of Nexus Repository Manager as a solution for hosting, proxying, and managing Docker images.