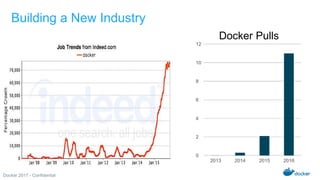
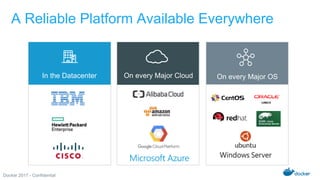
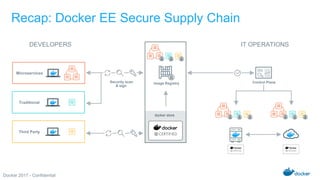
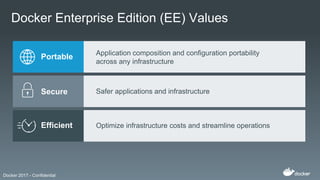
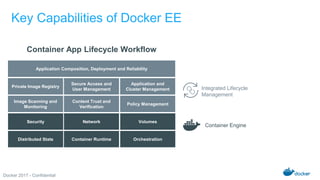
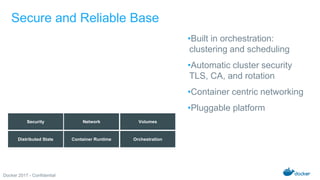
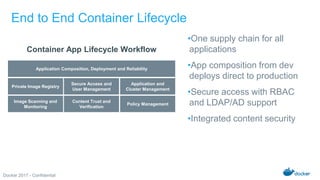
The Docker Federal Summit 2017 showcased the growth and impact of Docker technology across various industries, highlighting its use in critical applications for sectors like healthcare, finance, and public services. The event featured sessions on modernizing legacy applications, implementing secure supply chains, and leveraging Docker's enterprise edition for efficiency and cloud portability. Attendees were encouraged to participate in initiatives that support healing for families through the Boulder Crest Retreat organization.