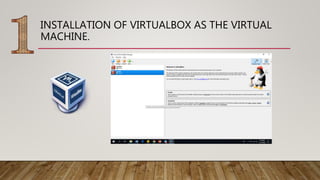
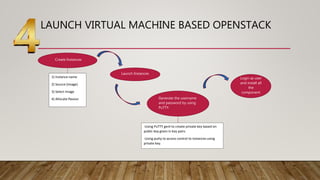
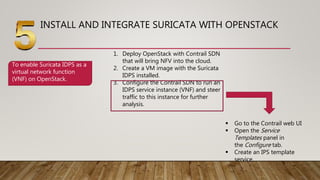
This document discusses enhancing security of virtual machines in OpenStack using Suricata intrusion prevention system (IPS). The objectives are to configure OpenStack, install and integrate Suricata IPS, and test the integration. Suricata IPS will be deployed to secure instances from attacks by monitoring traffic over the virtualized network. The framework involves installing OpenStack on a CentOS 7 virtual machine using VirtualBox, launching instances, and configuring Suricata IPS to integrate with OpenStack SDN to enable deep packet inspection and intrusion detection. The expected result is to improve security of virtual machines in OpenStack cloud platform.











![EXAMPLE OUTPUT
10/06/2012-11:40:49.018377 [Drop] [**] [1:1:0] facebook is blocked [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1]
{TCP} 192.168.122.48:57113 -> 173.252.100.16:80 10/06/2012-11:40:49.020955 [Drop] [**] [1:1:0] facebook is blocked [**] [Classification:
Potential Corporate Privacy Violation]
[Priority: 1] {TCP} 192.168.122.48:57114 -> 173.252.100.16:80 10/06/2012-11:40:51.991876 [Drop] [**] [1:1:0] facebook is blocked [**]
[Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.122.48:57115 -> 173.252.100.16:80
Create local.rules in /etc/suricata/rules/ using a text editor.
drop tcp any any -> any any (msg:"facebook is blocked"; content:"facebook.com";
http_header; nocase; classtype:policy-violation; sid:1;)
Restart Suricata:
service suricata restart
Now open Firefox, and try to go to http://www.facebook.com/, the
request should time out.
The logfile /var/log/suricata/fast.log will have:](https://image.slidesharecdn.com/presentation2-181212204354/85/Enhance-Virtual-Machine-Security-in-OpenStack-Using-Suricata-IPS-17-320.jpg)
