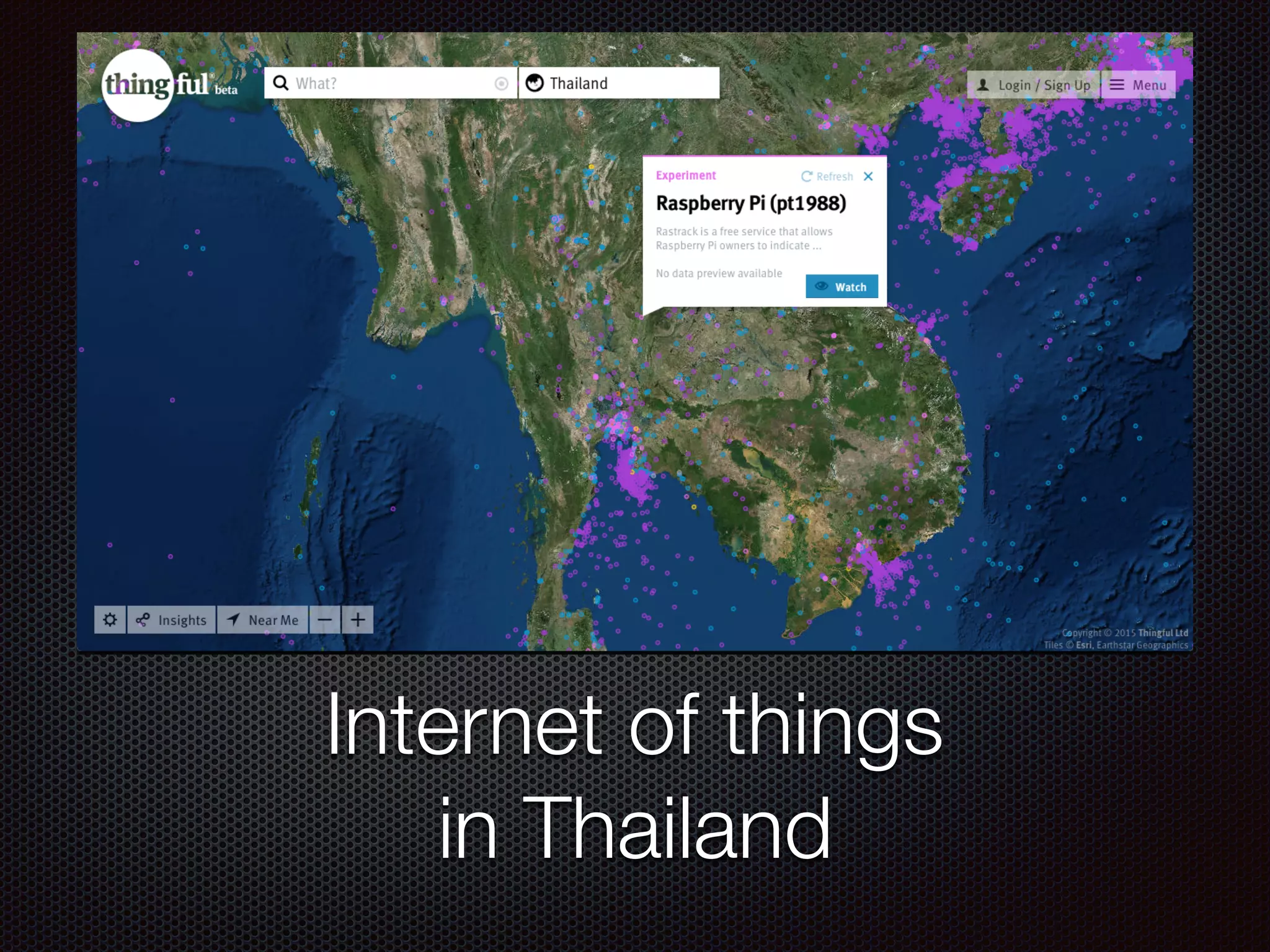
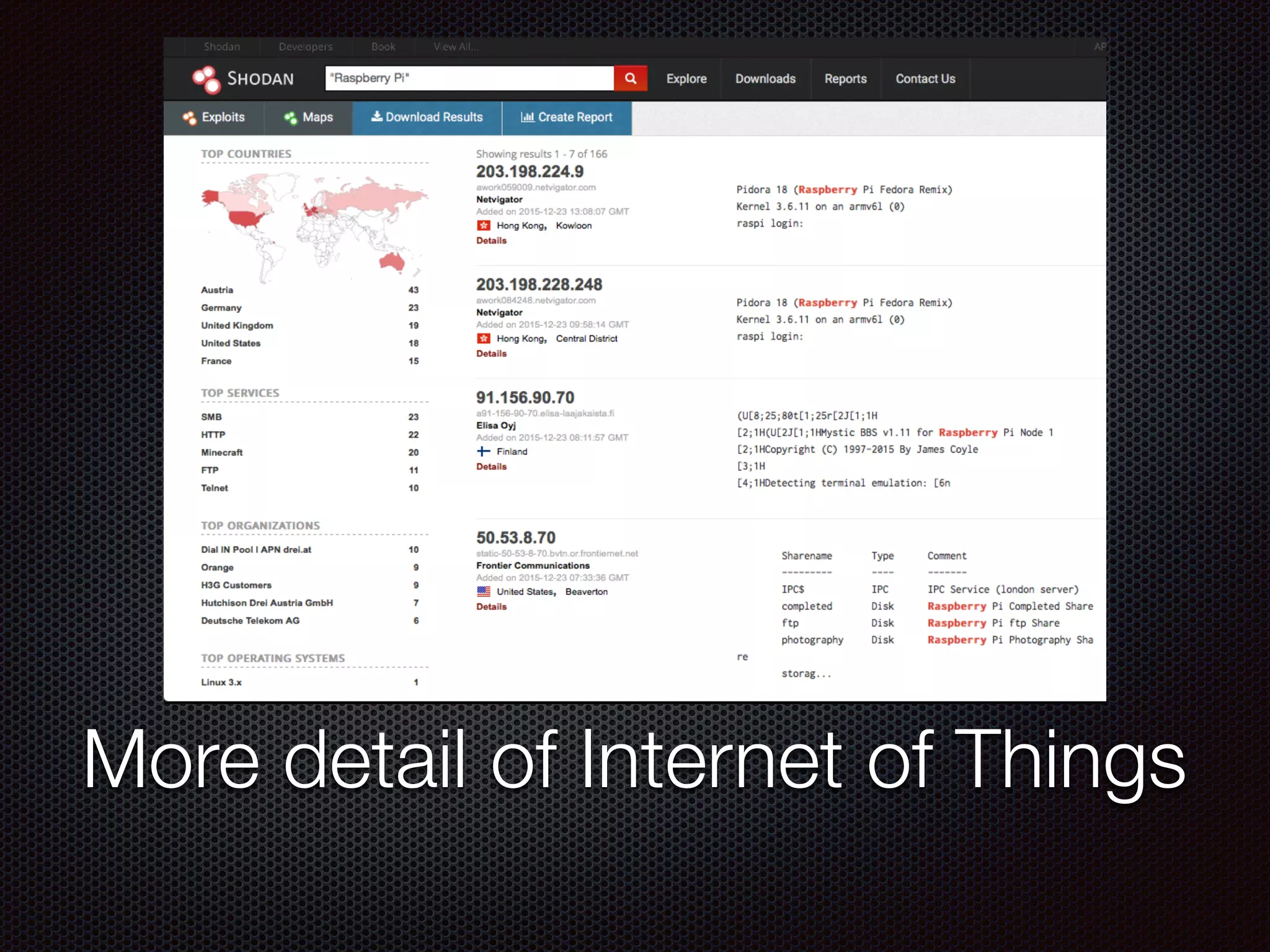
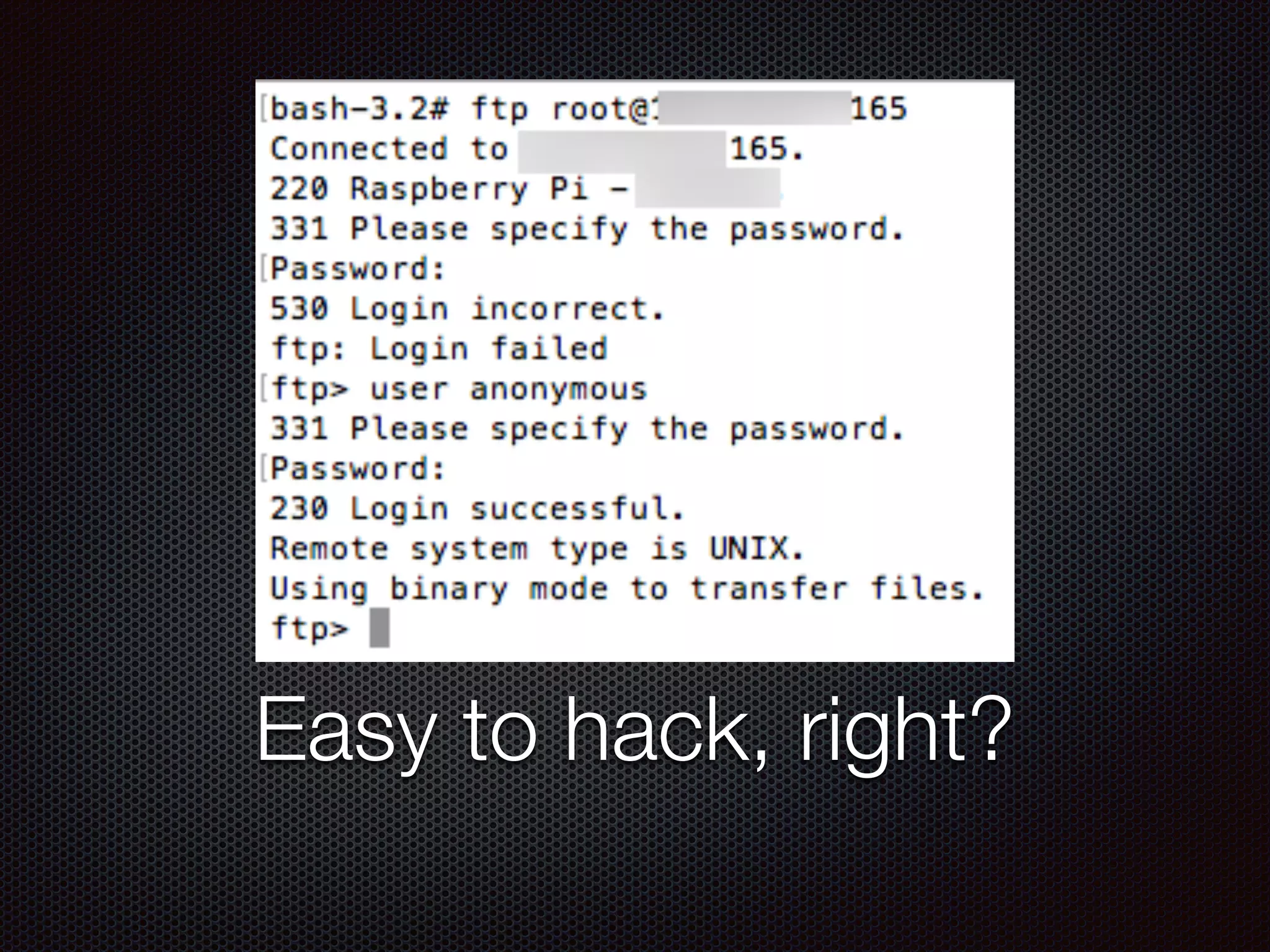
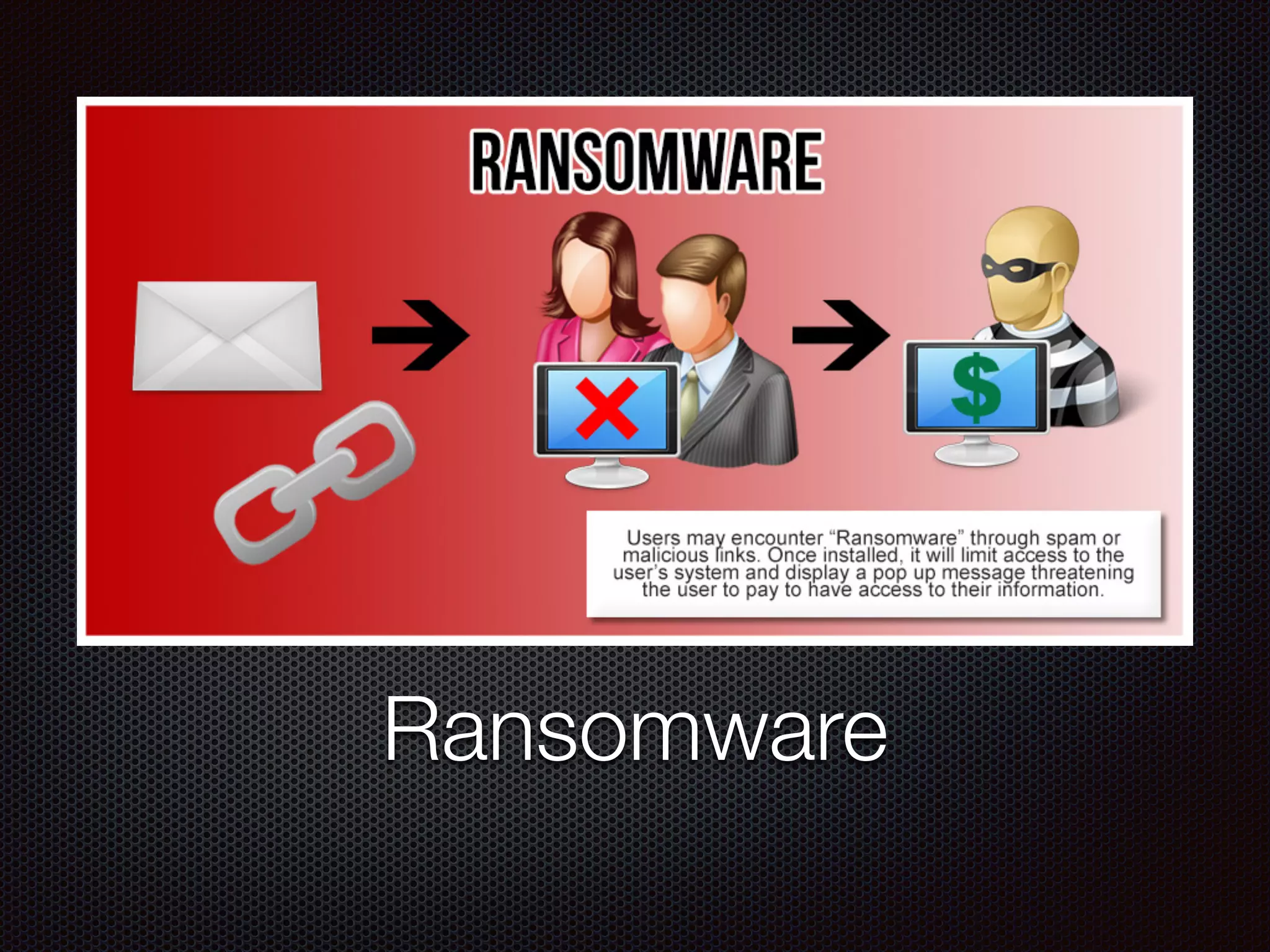
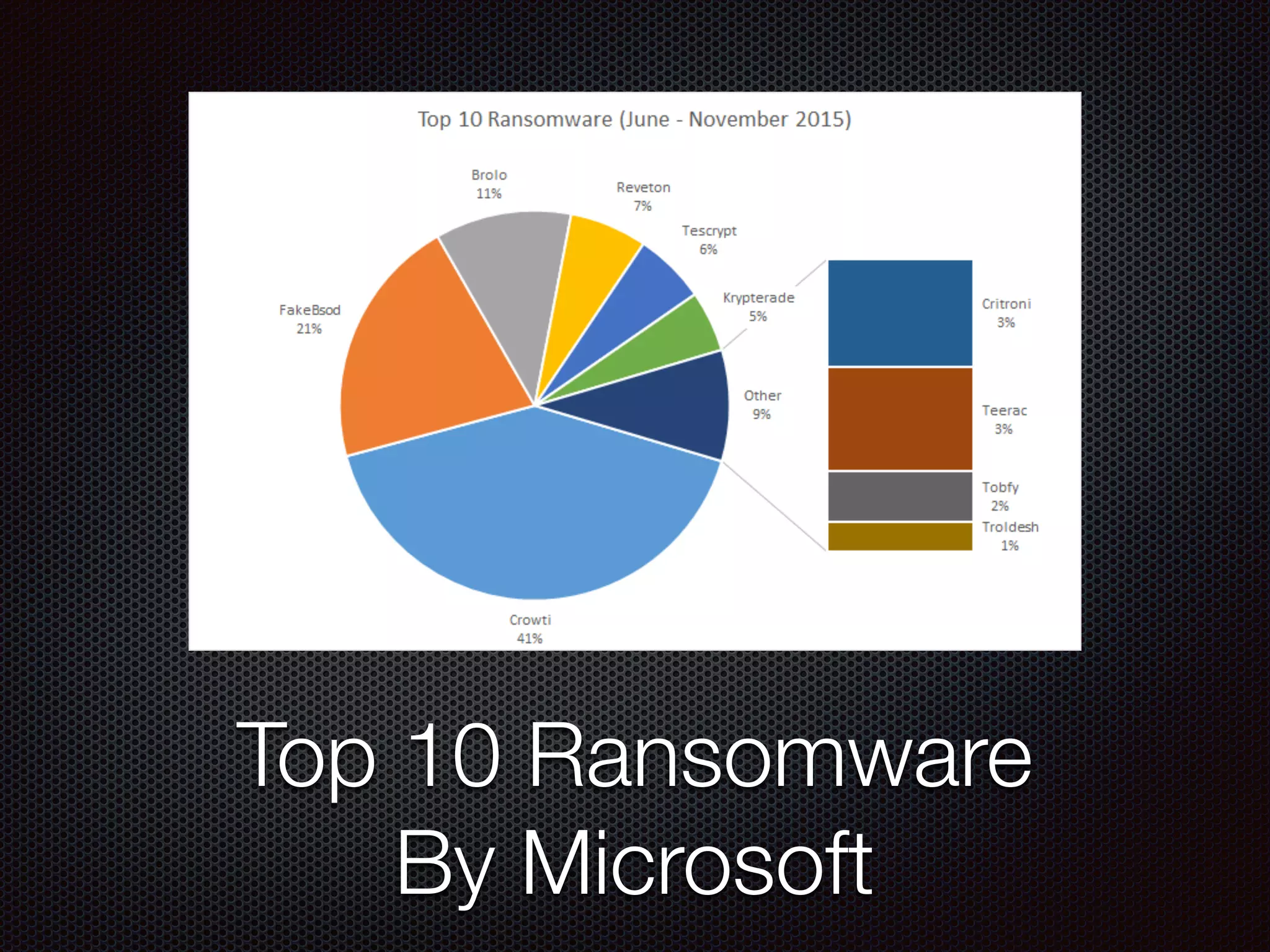
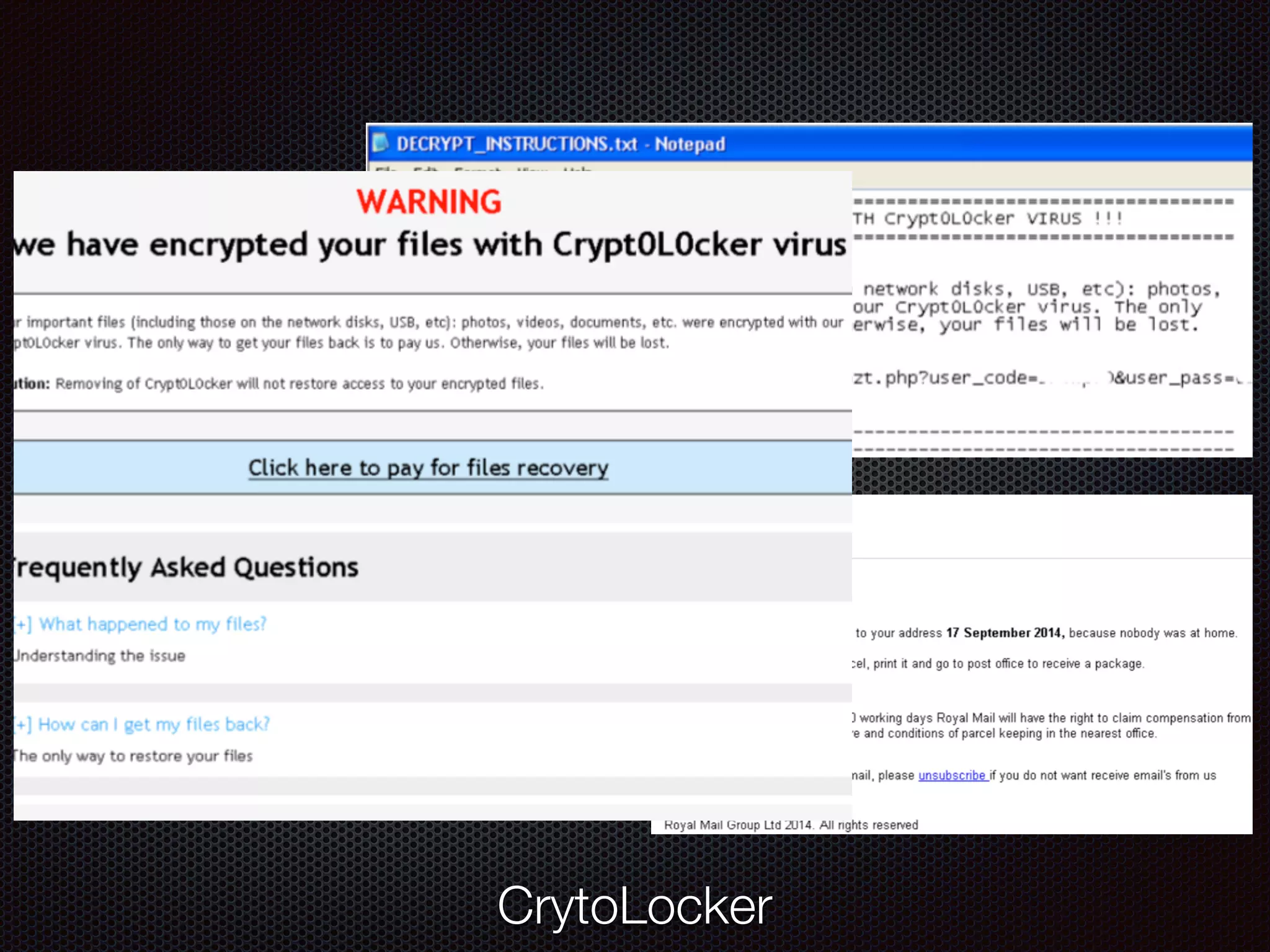
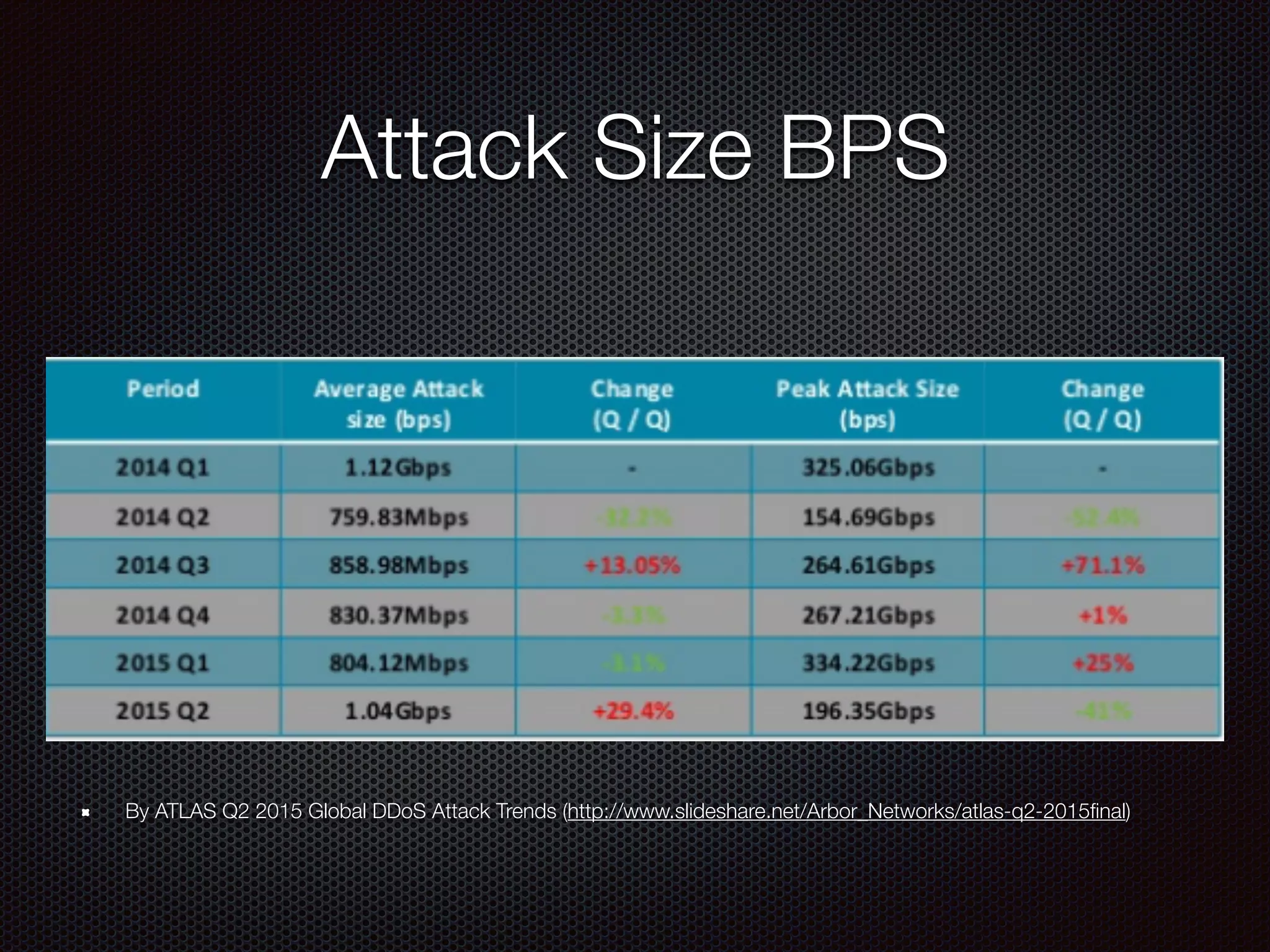
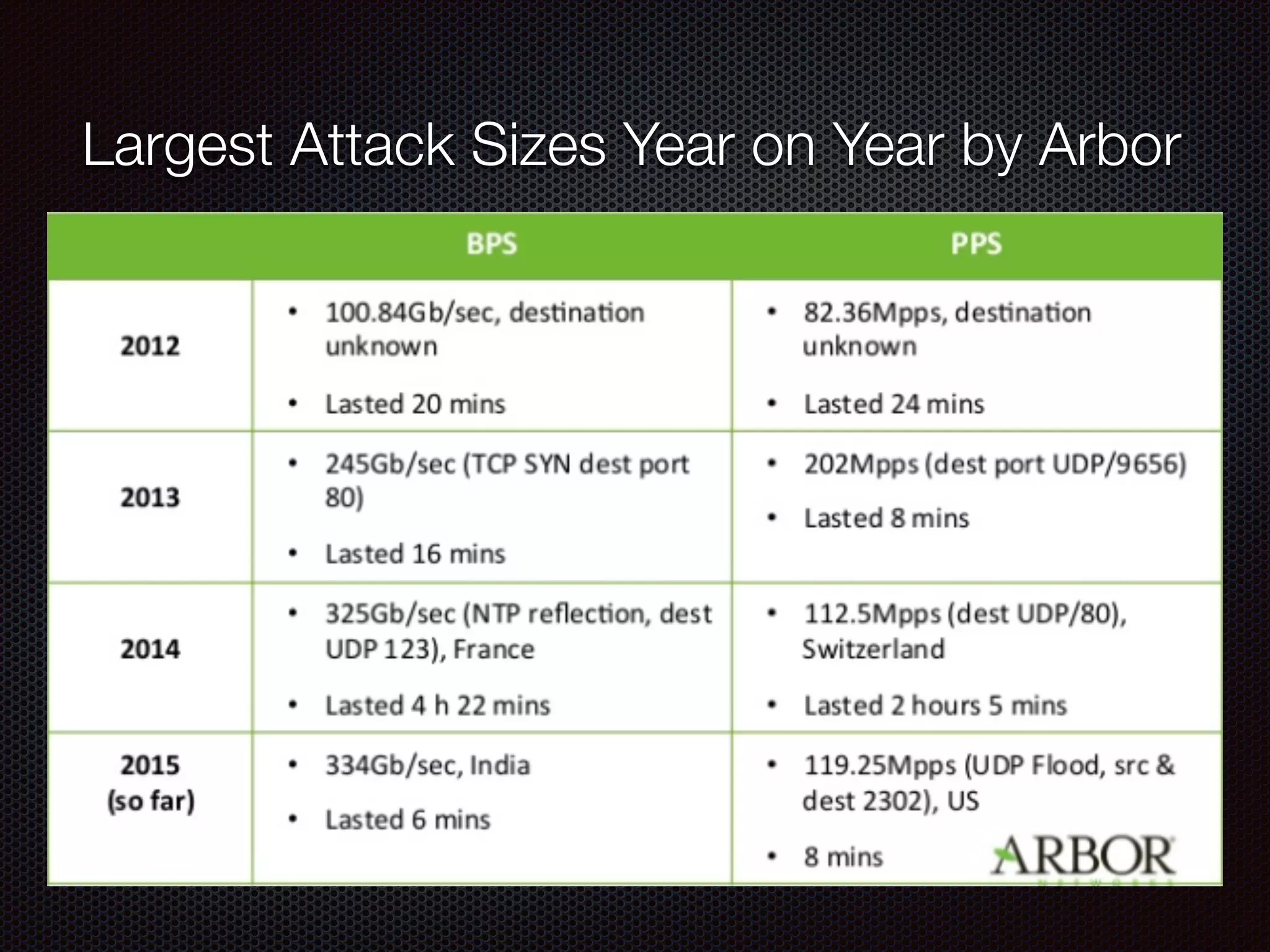
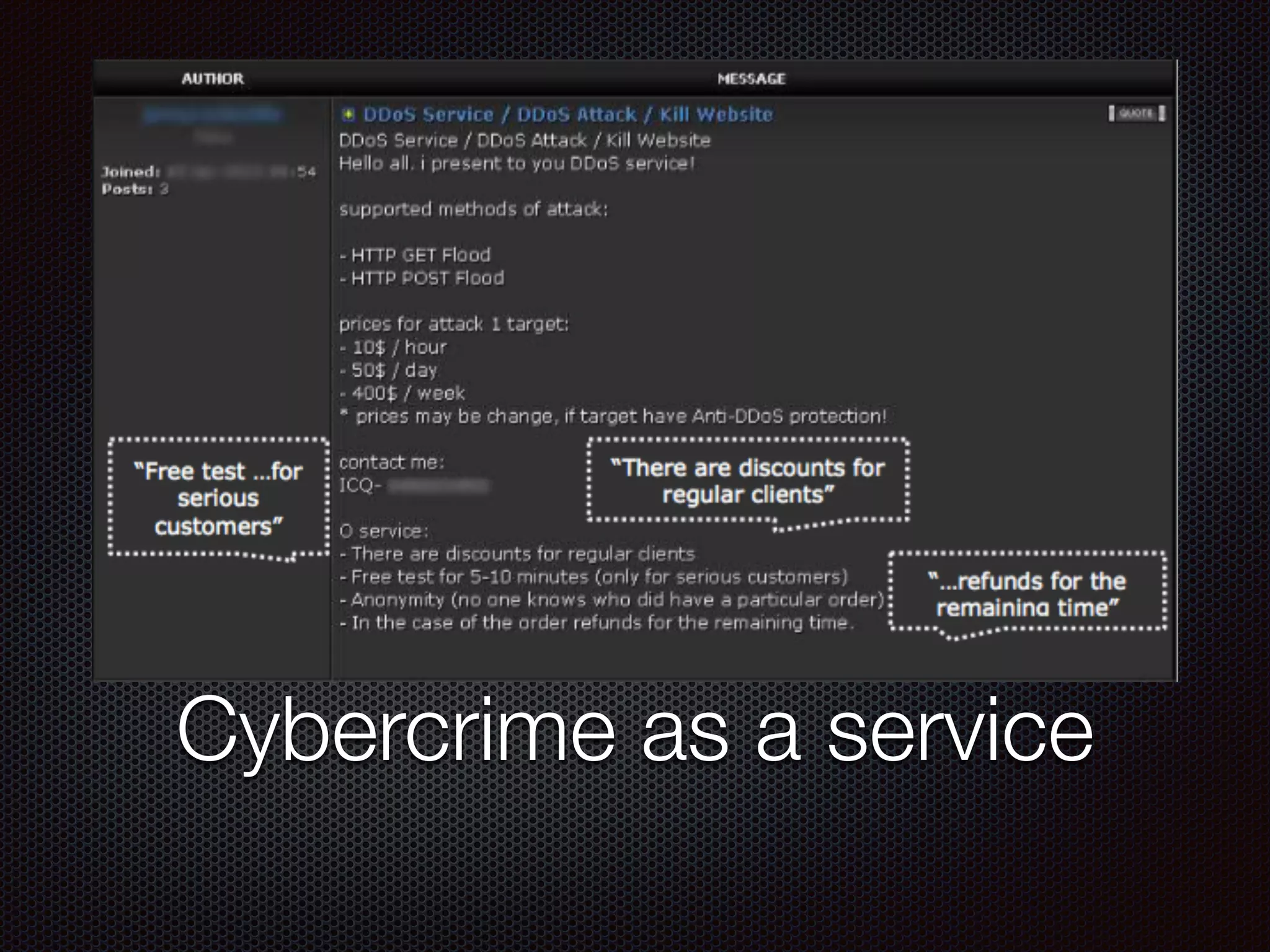
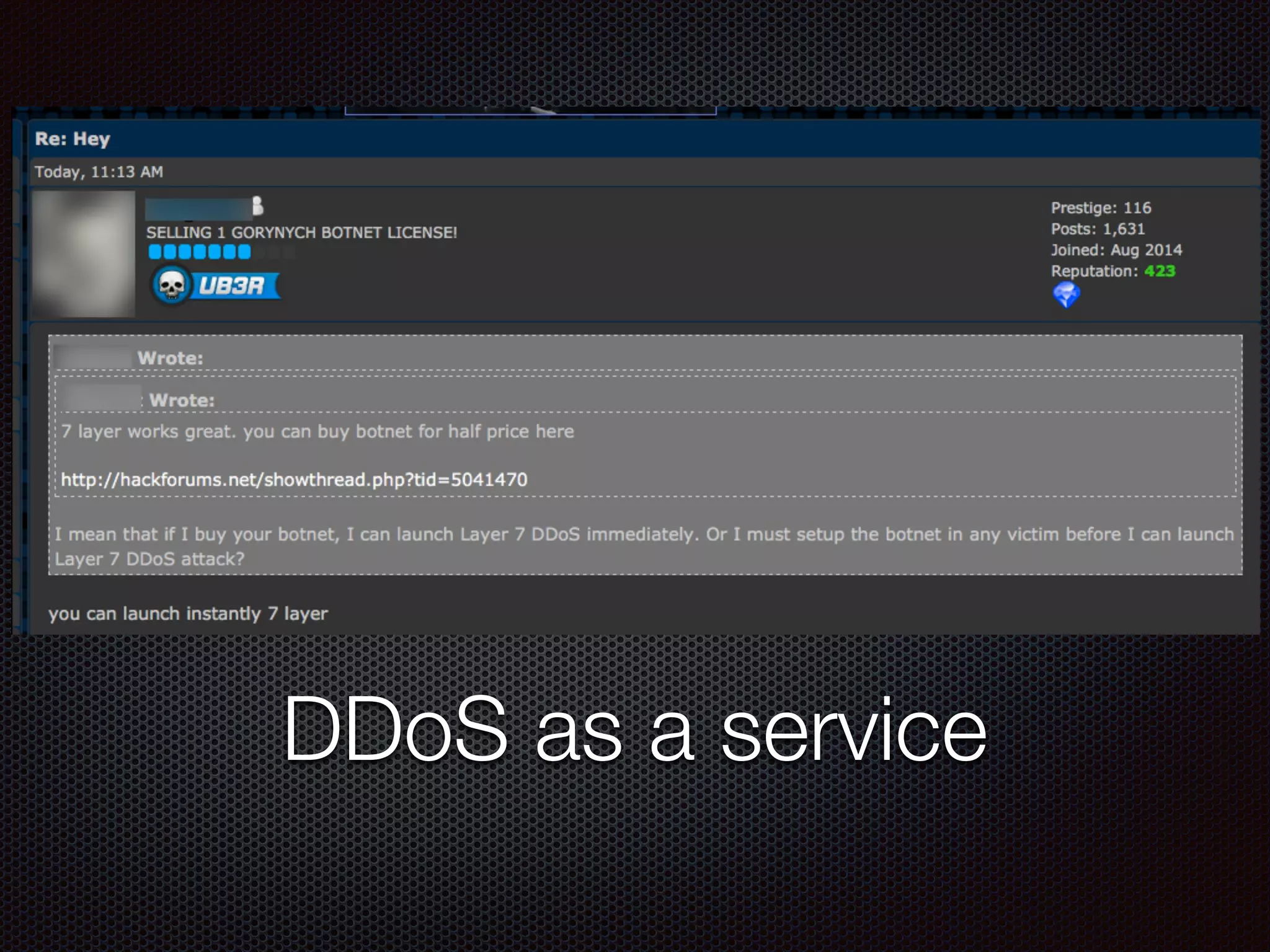
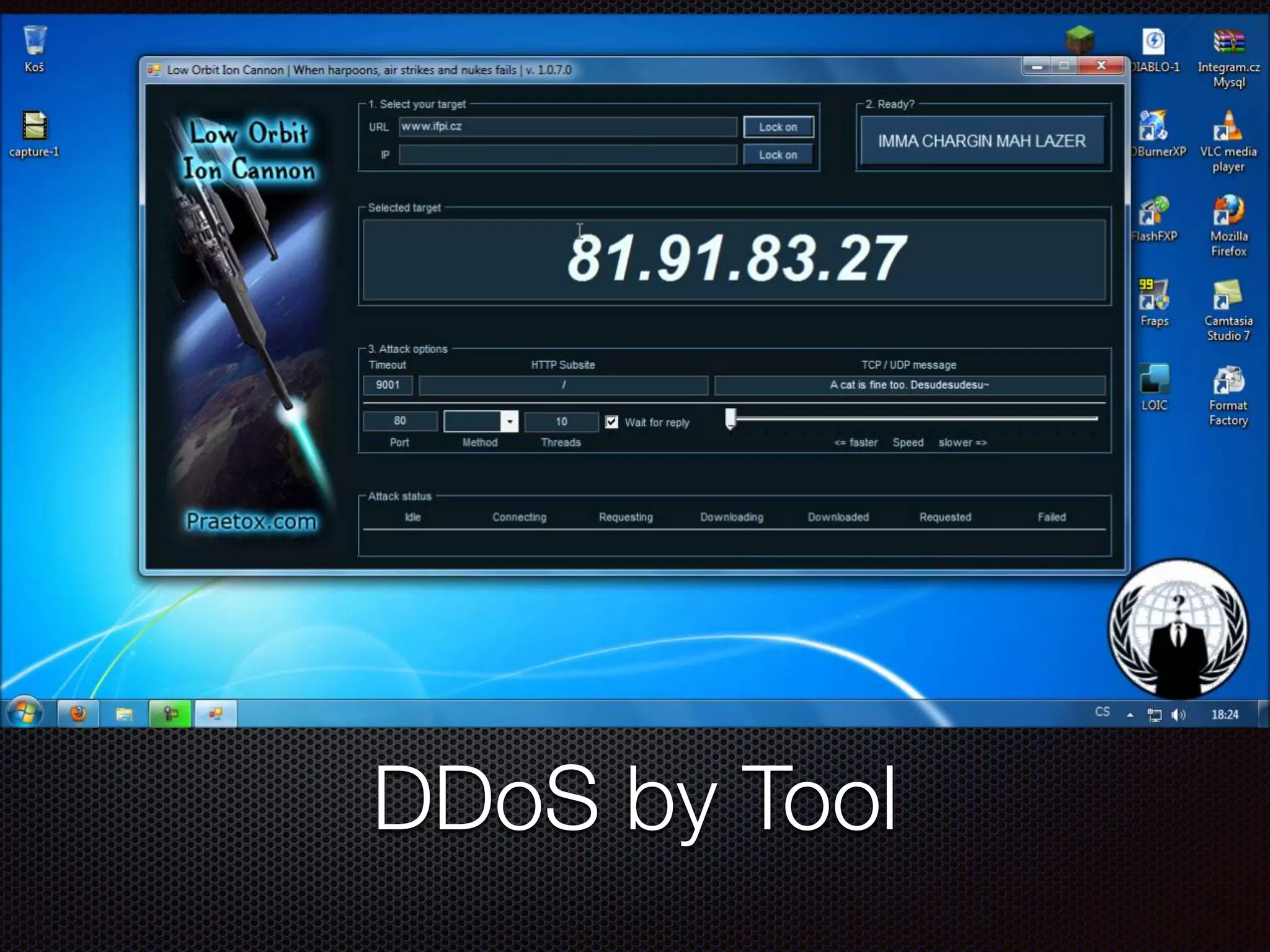
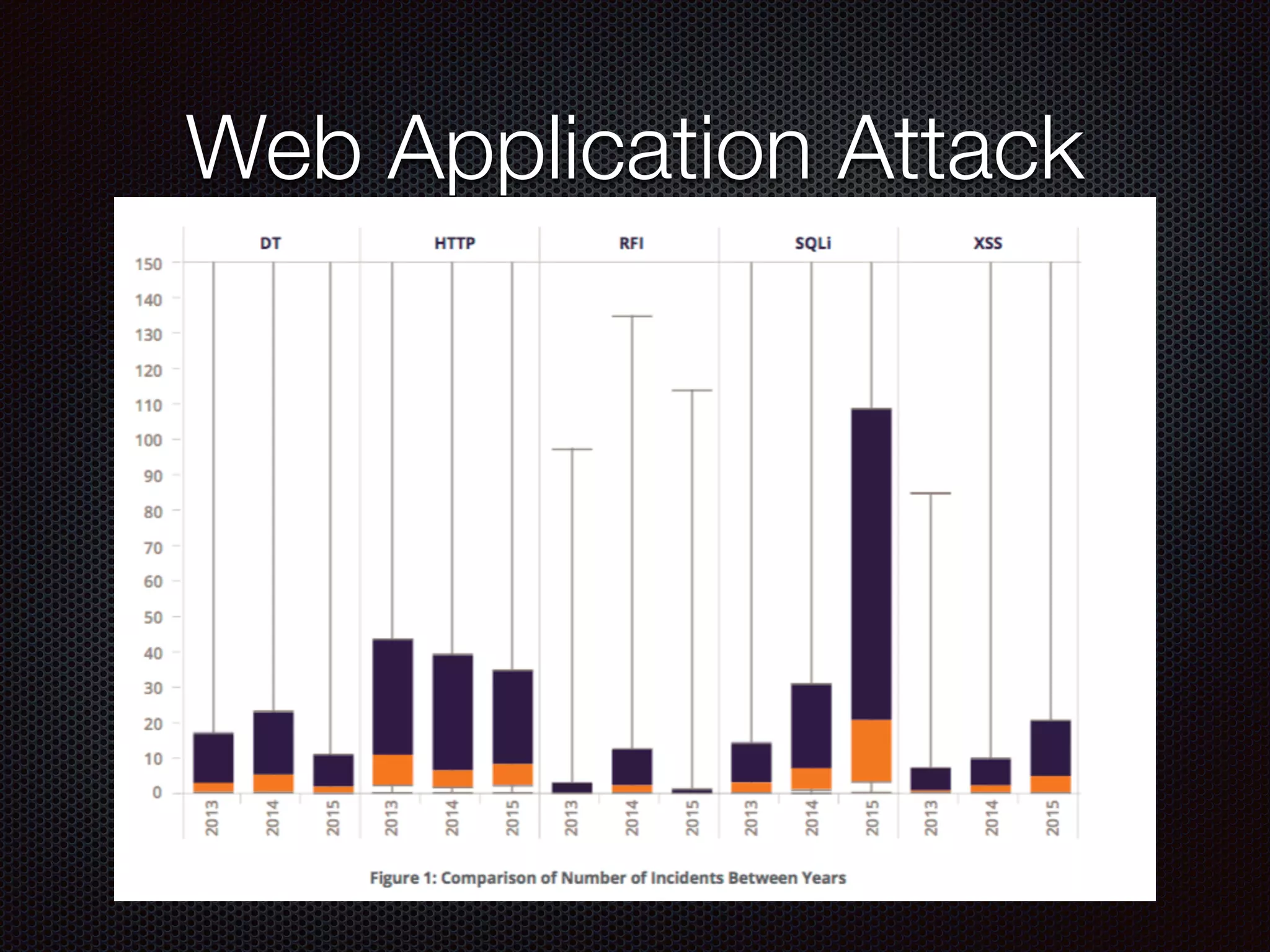
This document discusses various cybersecurity topics including the rise of cybersecurity, internet of things, ransomware, denial of service (DDoS) attacks, and web application attacks. It provides examples of popular ransomware like CryptoLocker and CryptoWall. It discusses the size and source of DDoS attacks according to reports from organizations like Arbor Networks and Verisign. Methods of carrying out DDoS and ransomware attacks are demonstrated. Defense strategies against each threat are also outlined. The document concludes by emphasizing the importance of security awareness, thinking like an attacker, and risk management in cybersecurity.





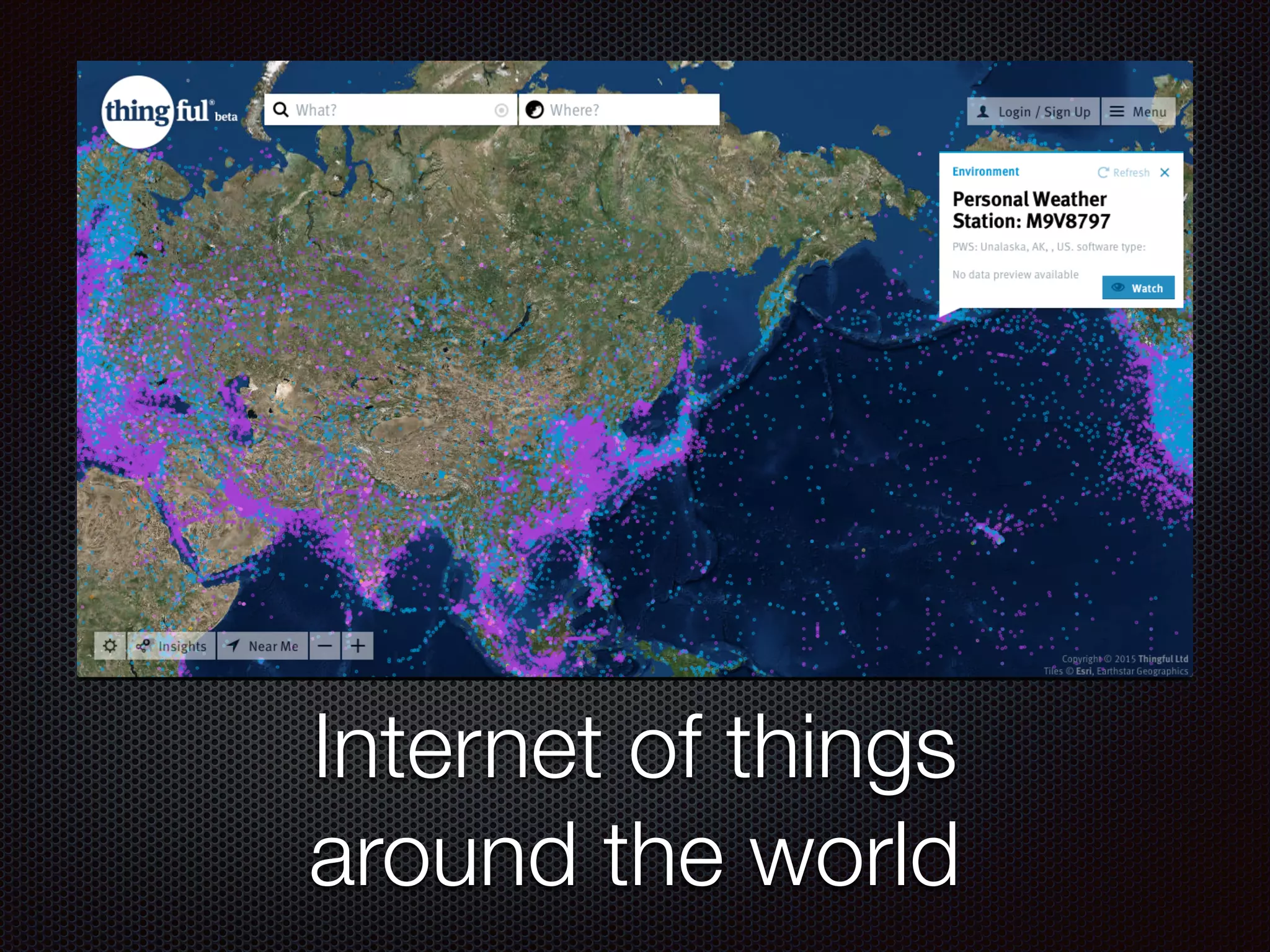





















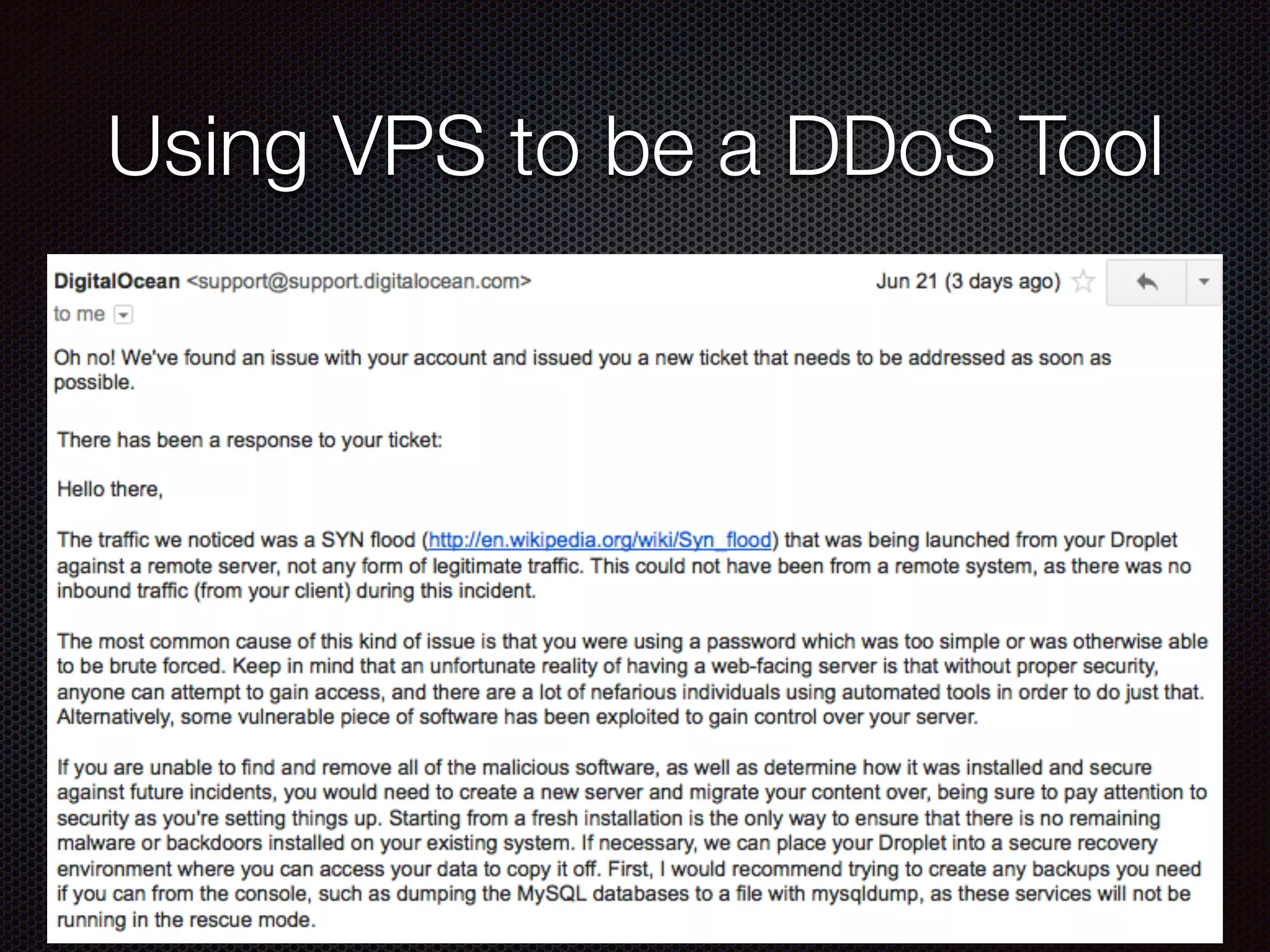
![Damage of website got hack
Defame the company [Defacement]
Stealing information
Stealing internal information
Use as DDoS Tool
Spread the malware](https://image.slidesharecdn.com/ruhacked-151226090811/75/R-u-hacked-43-2048.jpg)