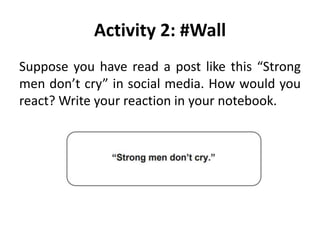
This document provides an overview of information and communication technologies (ICT). It discusses key topics like the current state of ICT in the Philippines, trends in ICT including social media and mobile technologies, online safety and security issues, and netiquette guidelines. The objectives are to compare online platforms to achieve class goals, apply safety standards, and use the internet for research. It also includes activities for students to engage with the material.