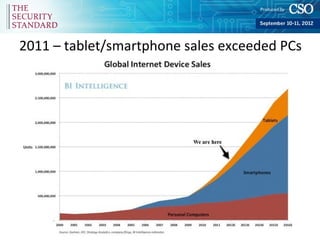
Barry Caplin, CISO of the MN Dept. of Human Services, discusses embracing consumerization and the security challenges of tablets and smartphones. He outlines the rapid adoption of these devices and consumer apps. Some key security risks include exposure of data, malware, lack of vetting and updates for third party apps, and privacy issues. Caplin provides an overview of potential technical solutions like mobile device management, virtualization, and containerization as well as the importance of policy, legal considerations, and user education when implementing a BYOD or mobile strategy.