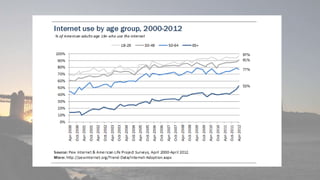
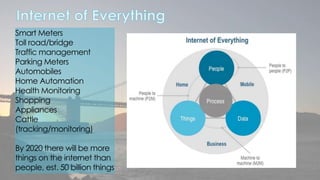
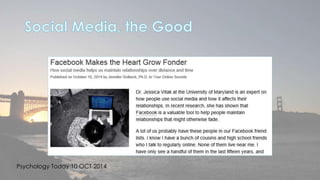
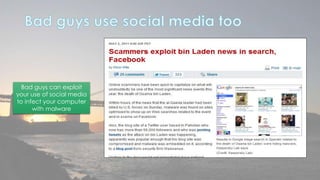
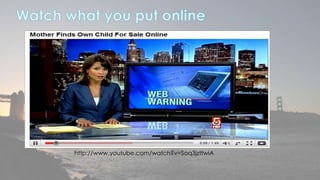
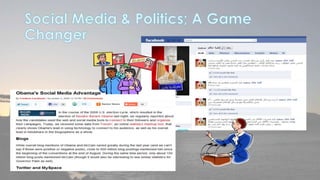
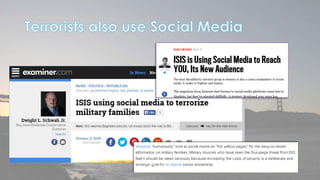
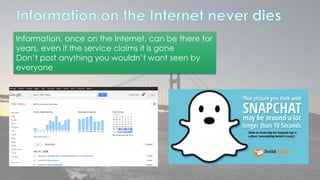
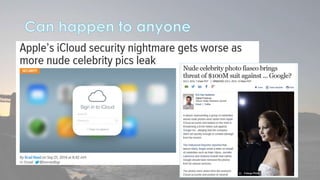
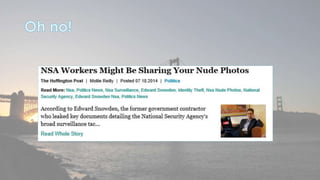
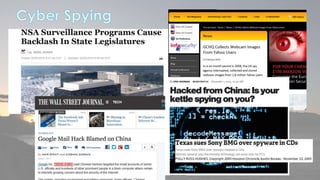
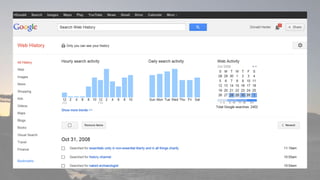
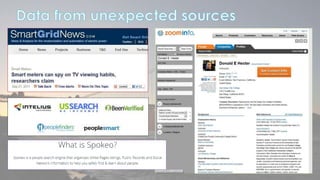
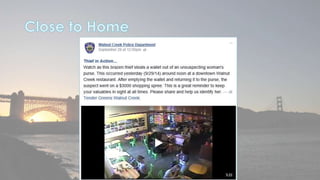
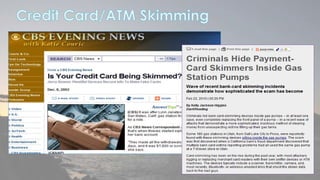
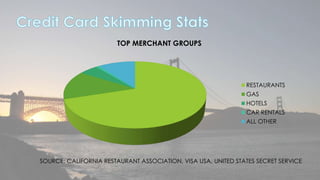
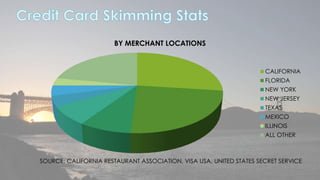
This document discusses cyber security issues related to social media and personal information online. It notes that the amount of data created annually has grown exponentially and this data can remain online for years. Both personal profiles created by individuals and those created about people by others shape their online reputation. The document warns that employers, insurers, and other parties increasingly check social media and that anonymity online allows false posts that can damage credibility. Various risks of oversharing personal information are outlined, as are strategies to monitor and control one's online profile and reputation.