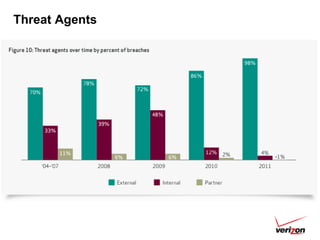
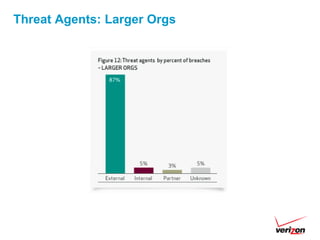
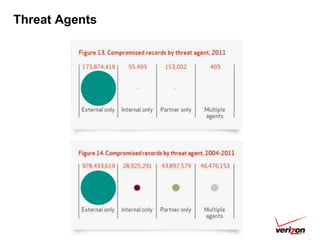
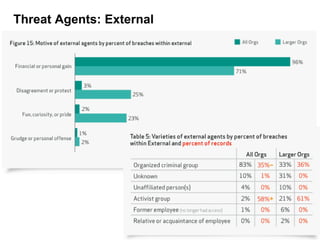
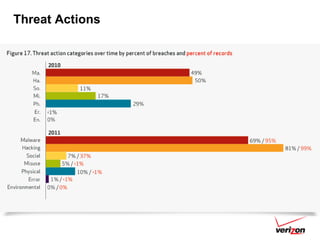
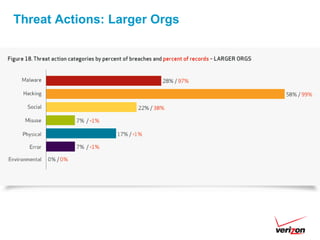
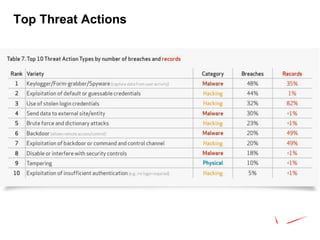
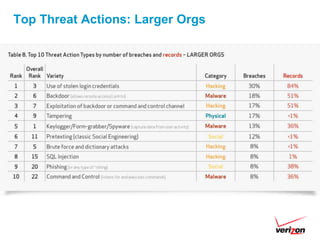
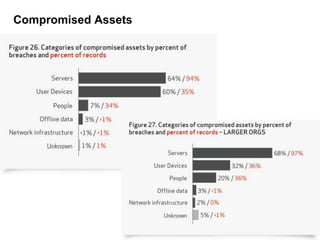
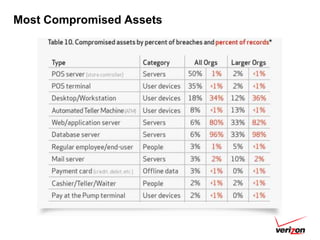
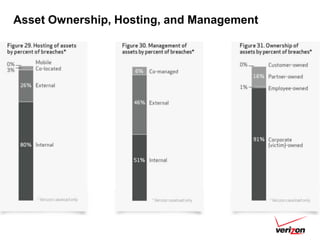
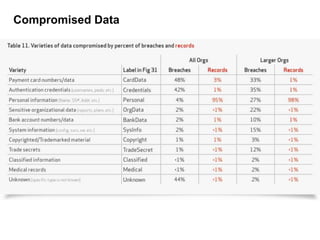
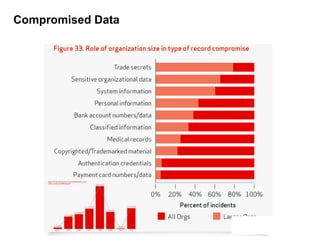
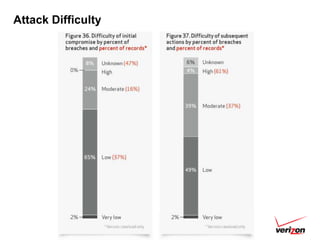
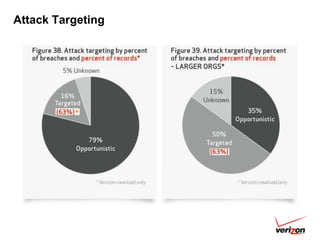
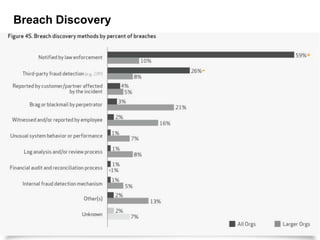
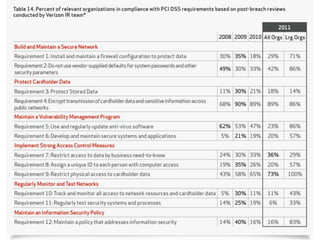
The 2012 Data Breach Investigations Report is a study conducted by Verizon with law enforcement agencies from several countries that analyzes data breaches to understand how data is stolen, who is responsible, their motives, and how to prevent future breaches. The report finds that external actors carried out most breaches, the most common threat actions were hacking and malware, and compromised credentials were the most common type of stolen data. It provides recommendations for organizations to strengthen security practices to reduce the risk of data breaches.