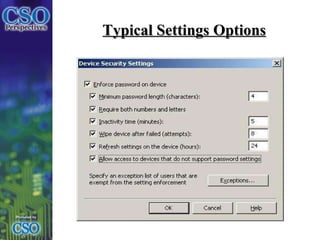
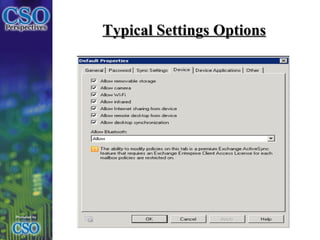
The document discusses the impact of consumerized IT, particularly the trends of Bring Your Own Device (BYOD) policies, and the challenges they pose in balancing user productivity with security risks. It emphasizes the need for companies to develop adaptable policies to manage personal and corporate devices while ensuring security measures are in place. Ultimately, the successful adoption of consumerized IT relates to understanding the cultural relevance within the organization and effectively communicating policies to all users.