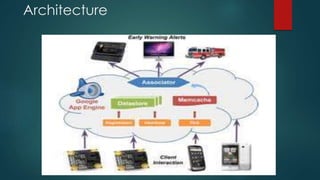
The document presents two novel techniques for authenticating short encrypted messages, designed to enhance efficiency for mobile and pervasive computing applications. These techniques leverage the security of encryption algorithms to deliver faster and more efficient authentication mechanisms, addressing limitations of existing message authentication codes (MACs). The proposed system outlines a framework that includes modules for authenticating messages, ensuring data privacy, and evaluating the security of authenticated encryption compositions.