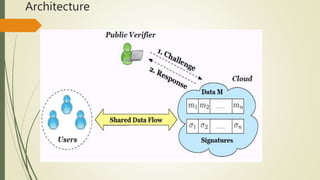
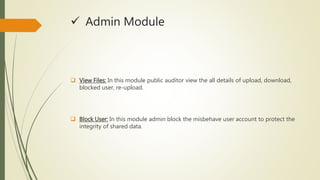
This document presents a novel public auditing mechanism for verifying the integrity of shared data in the cloud, with a focus on efficient user revocation. It allows the cloud to re-sign data blocks on behalf of existing users, mitigating the inefficiencies associated with user revocation while ensuring public verifiers can audit data integrity without full retrieval. The proposed system addresses security concerns by preventing unauthorized access and detailing architectural modules for user registration, file upload, verification, and administration.