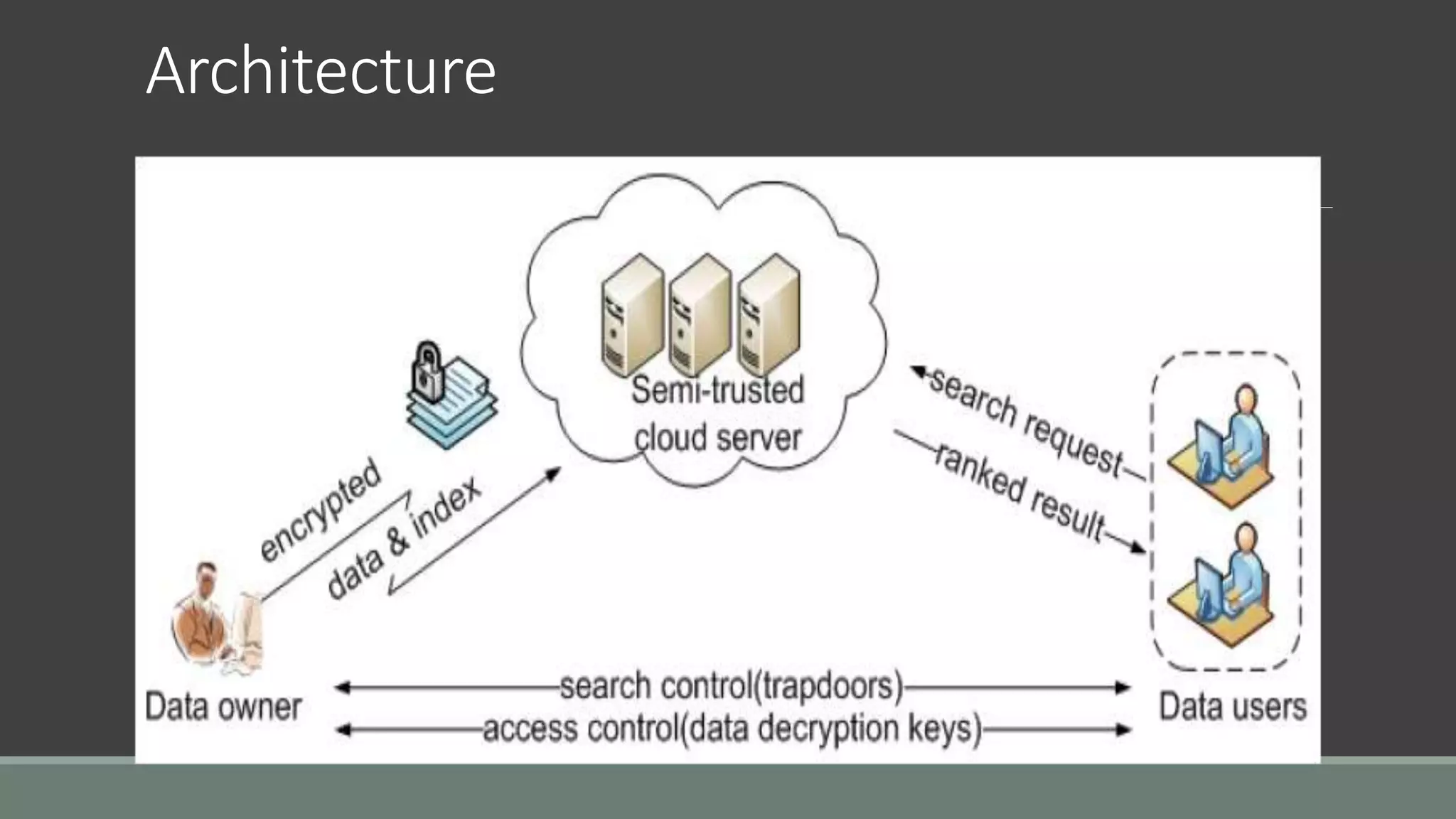
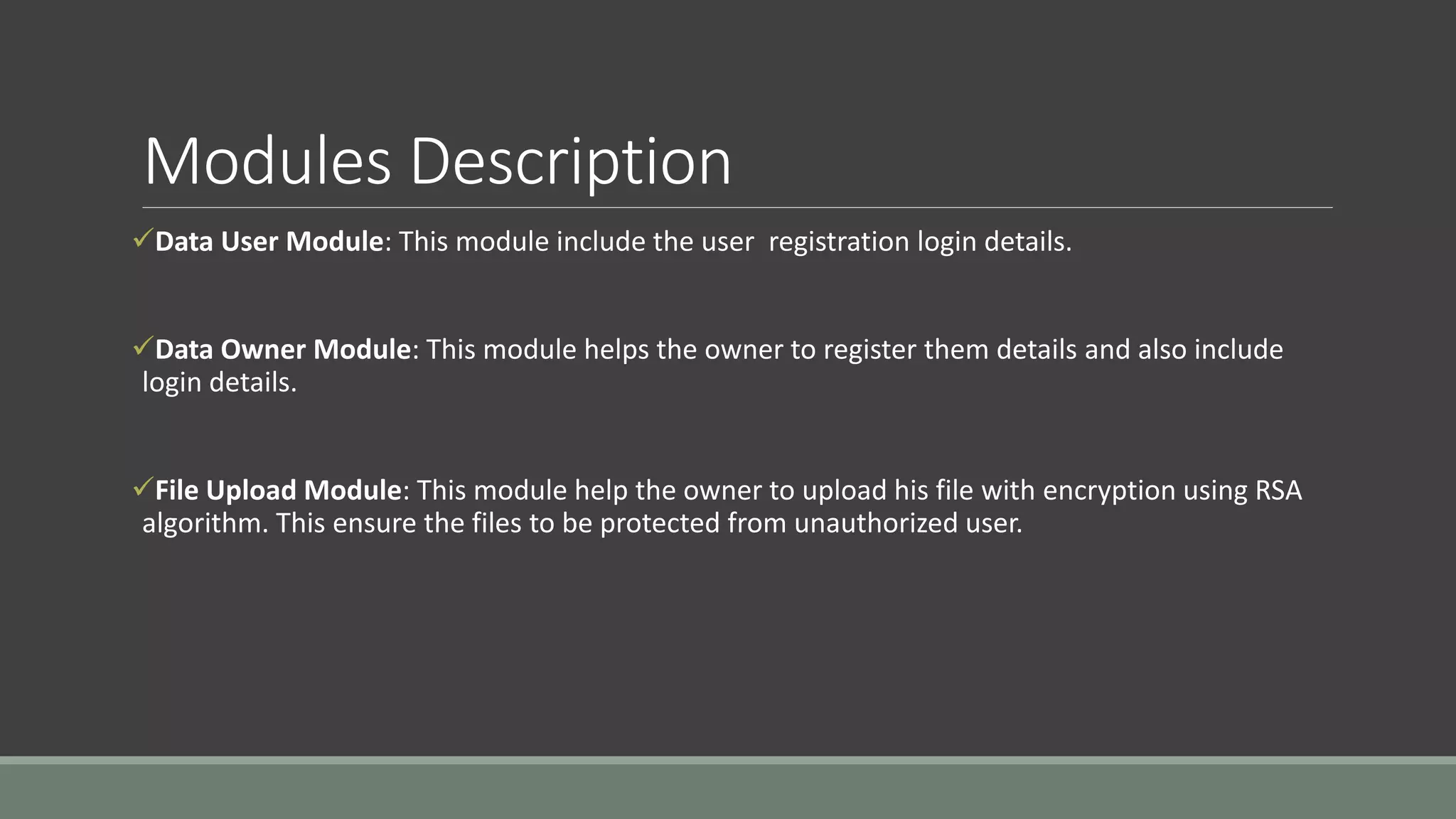
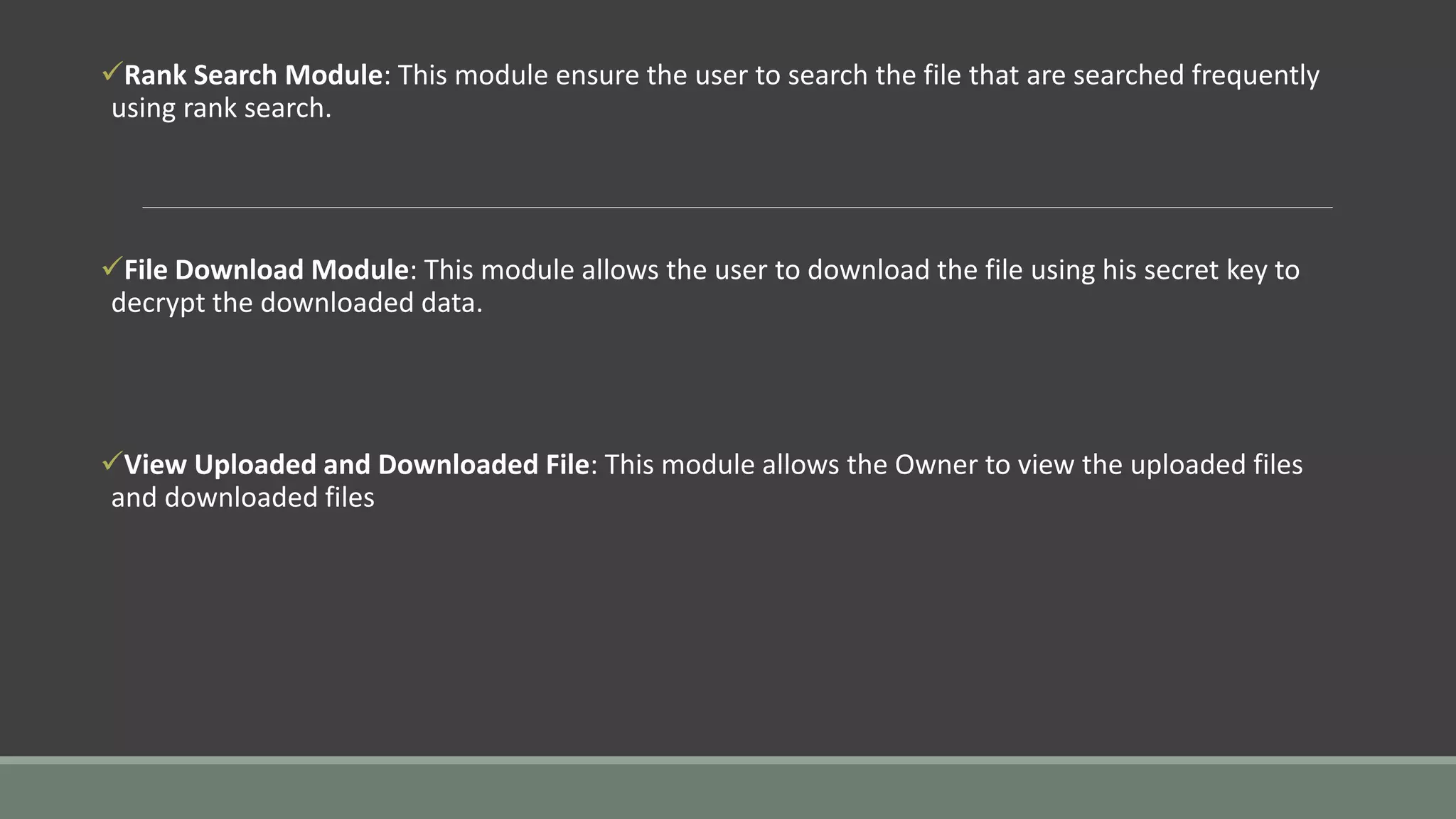
The document discusses a privacy-preserving multi-keyword ranked search (MRSE) system for encrypted cloud data, addressing the limitations of existing searchable encryption methods that typically focus on single or Boolean keyword searches. It establishes strict privacy requirements and introduces a new relevance measure called 'coordinate matching' to evaluate search results. The proposed system architecture includes modules for user registration, file upload with encryption, ranked searching, and secure downloads, demonstrating low computational and communication overhead.