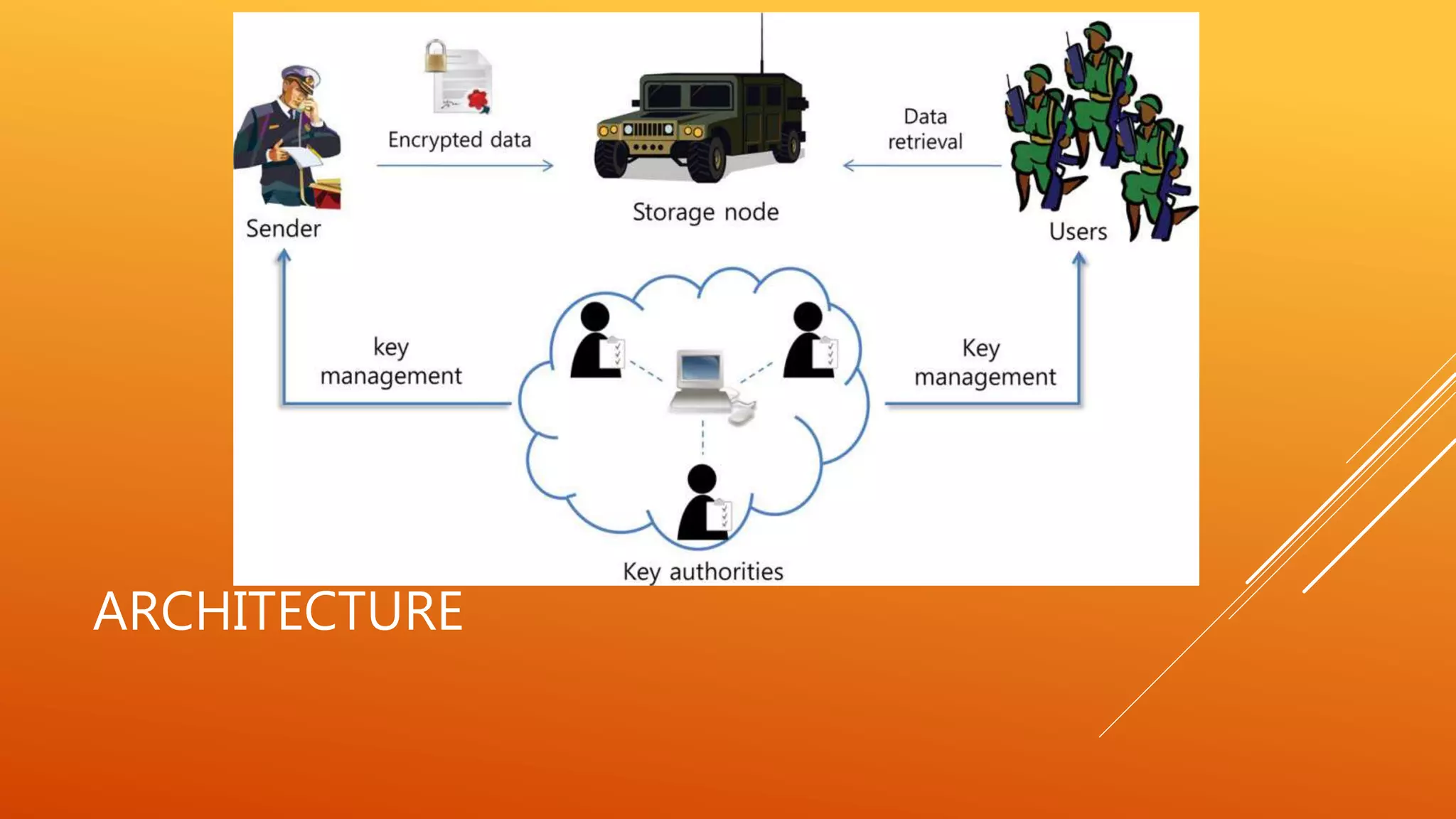
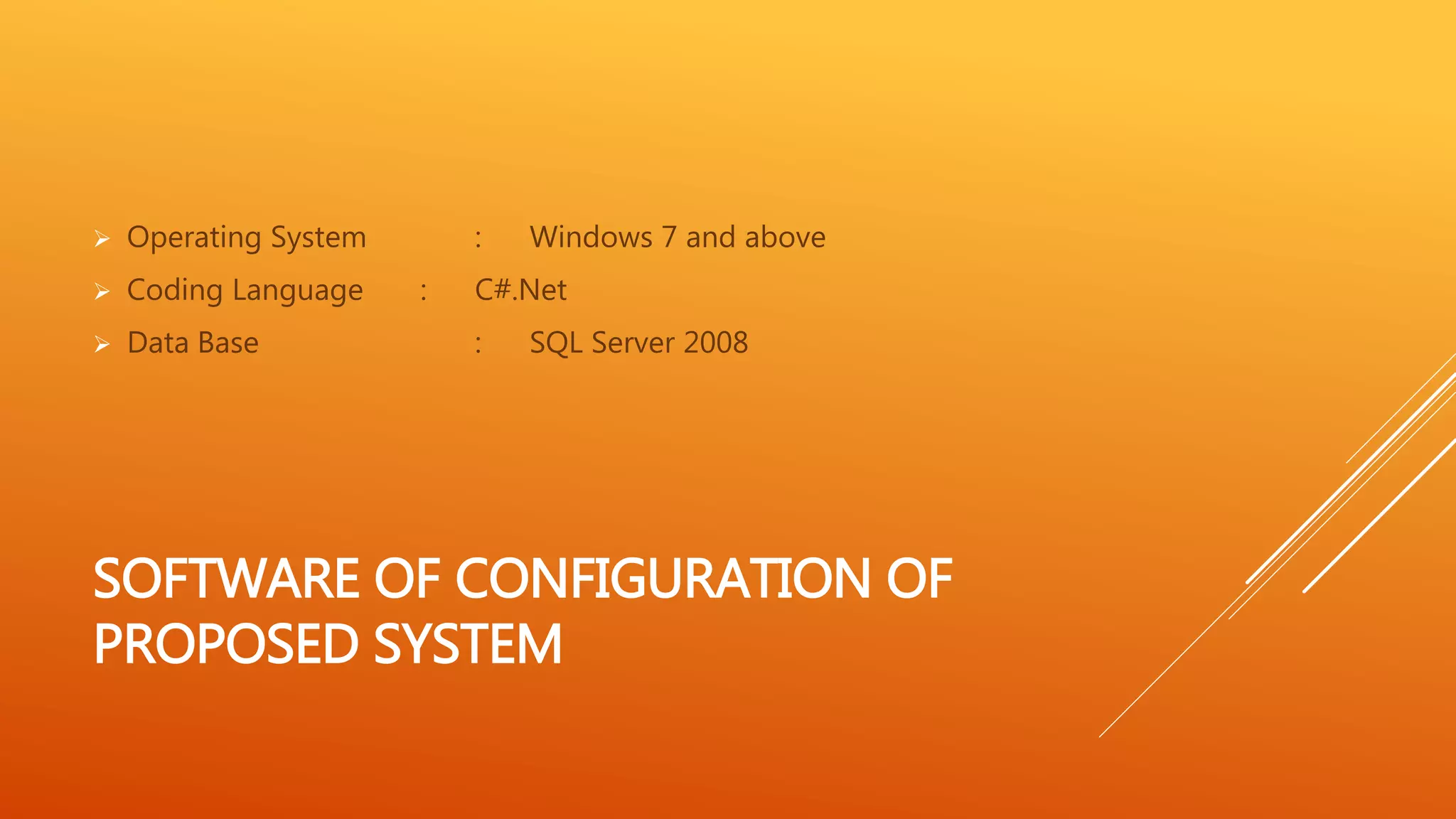
The paper presents a secure data retrieval scheme using ciphertext-policy attribute-based encryption (CP-ABE) for decentralized disruption-tolerant military networks, addressing challenges such as key revocation and security in hostile environments. It highlights the limitations of existing systems, particularly the risks of key authorities being compromised, and proposes a decentralized approach that allows independent management of attributes by multiple authorities. The proposed system enhances data confidentiality and reduces vulnerabilities through immediate attribute revocation and an escrow-free key issuing protocol.