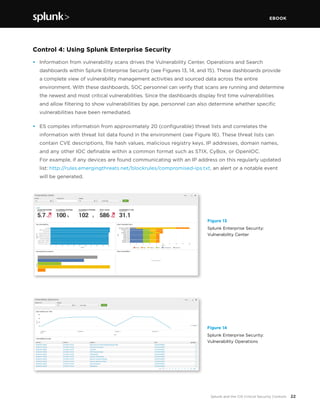
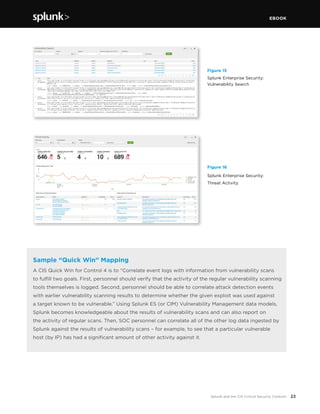
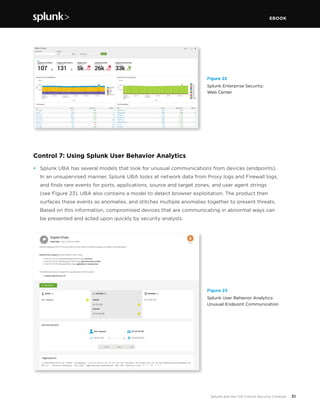
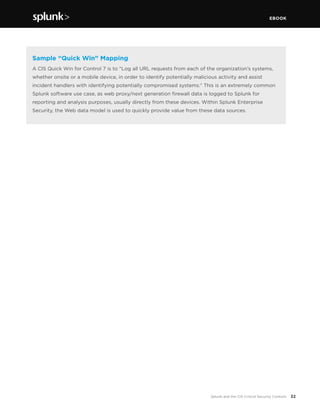
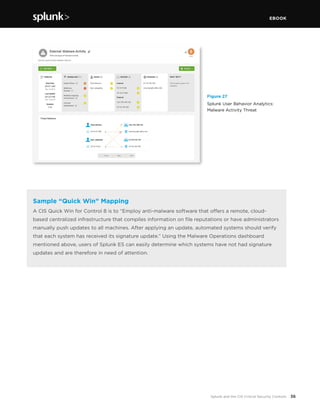
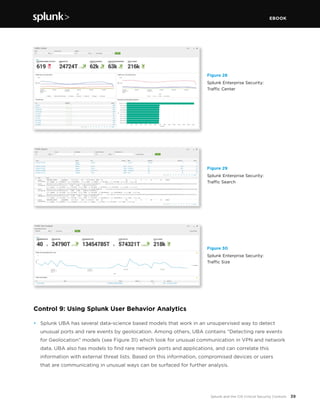
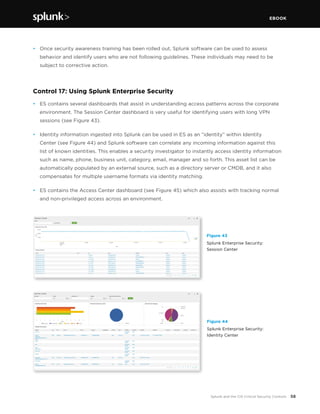
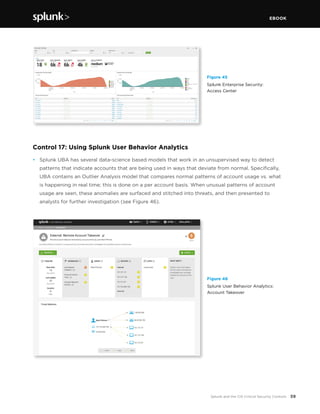
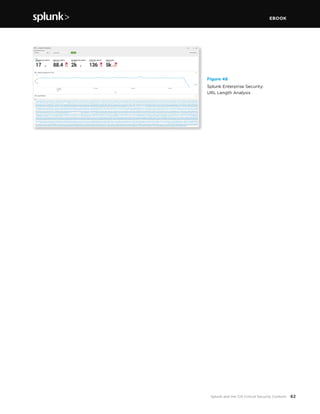
This document discusses how Splunk software maps to the Center for Internet Security's (CIS) Critical Security Controls (CSC). It provides an overview of the CIS CSC, including their importance and history. The CIS CSC are considered the de facto standard for measuring corporate security programs. Splunk software supports the CIS CSC in four main ways: verification of compliance, verification and execution of controls, execution of controls, and support of human activities related to controls. The document then analyzes how Splunk maps to each individual control.