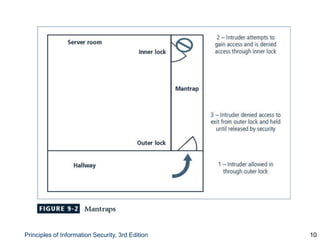
This document discusses physical security controls and considerations. It covers topics like physical security threats, controls like locks, badges, and alarms, as well as special areas like computer rooms, utilities, and mobile devices. Maintaining physical security is as important as logical security, as many logical controls can be circumvented if an attacker gains physical access. A variety of physical and environmental factors must be addressed through risk assessments, implementation of controls, and ongoing maintenance and testing.