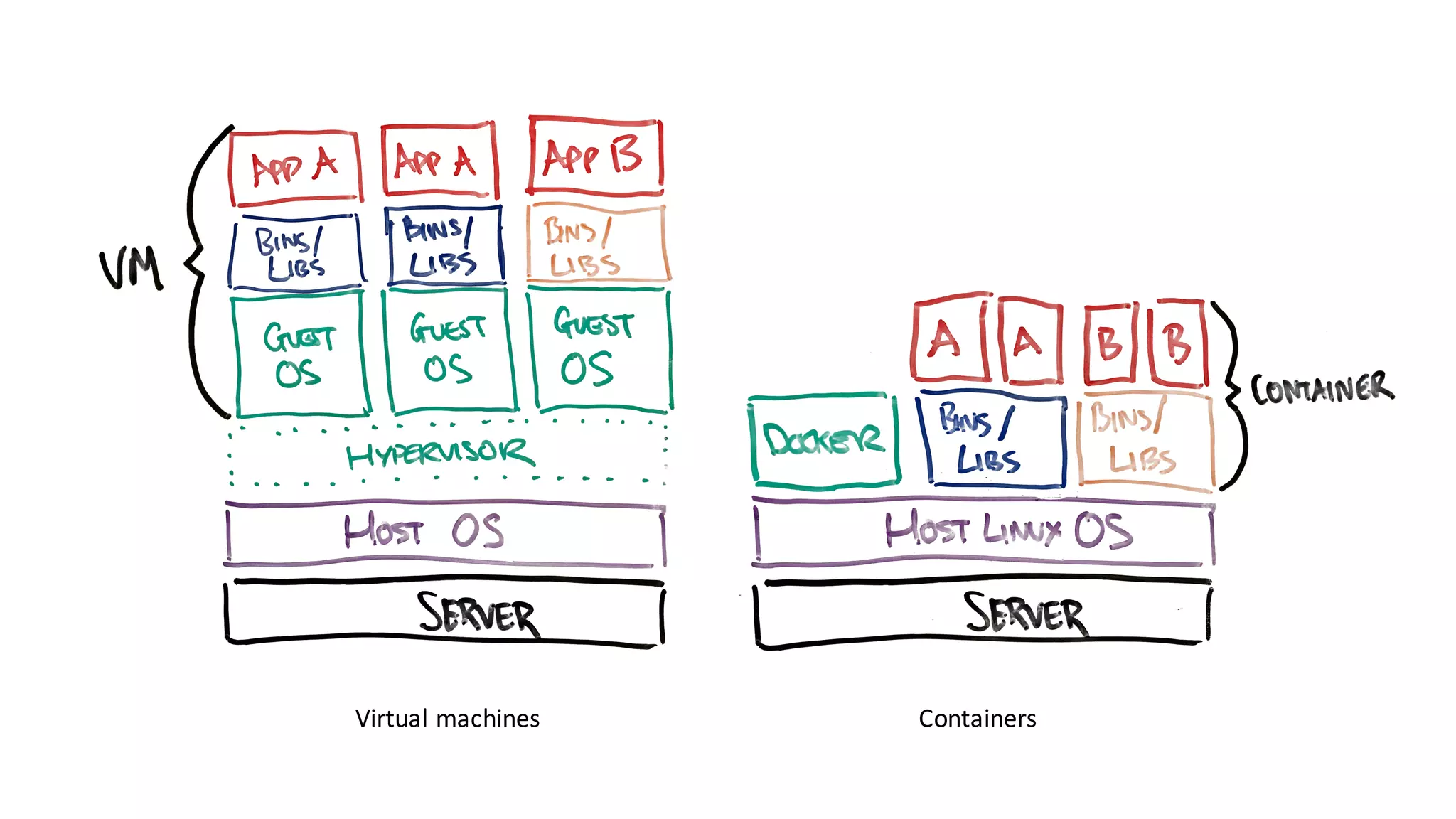
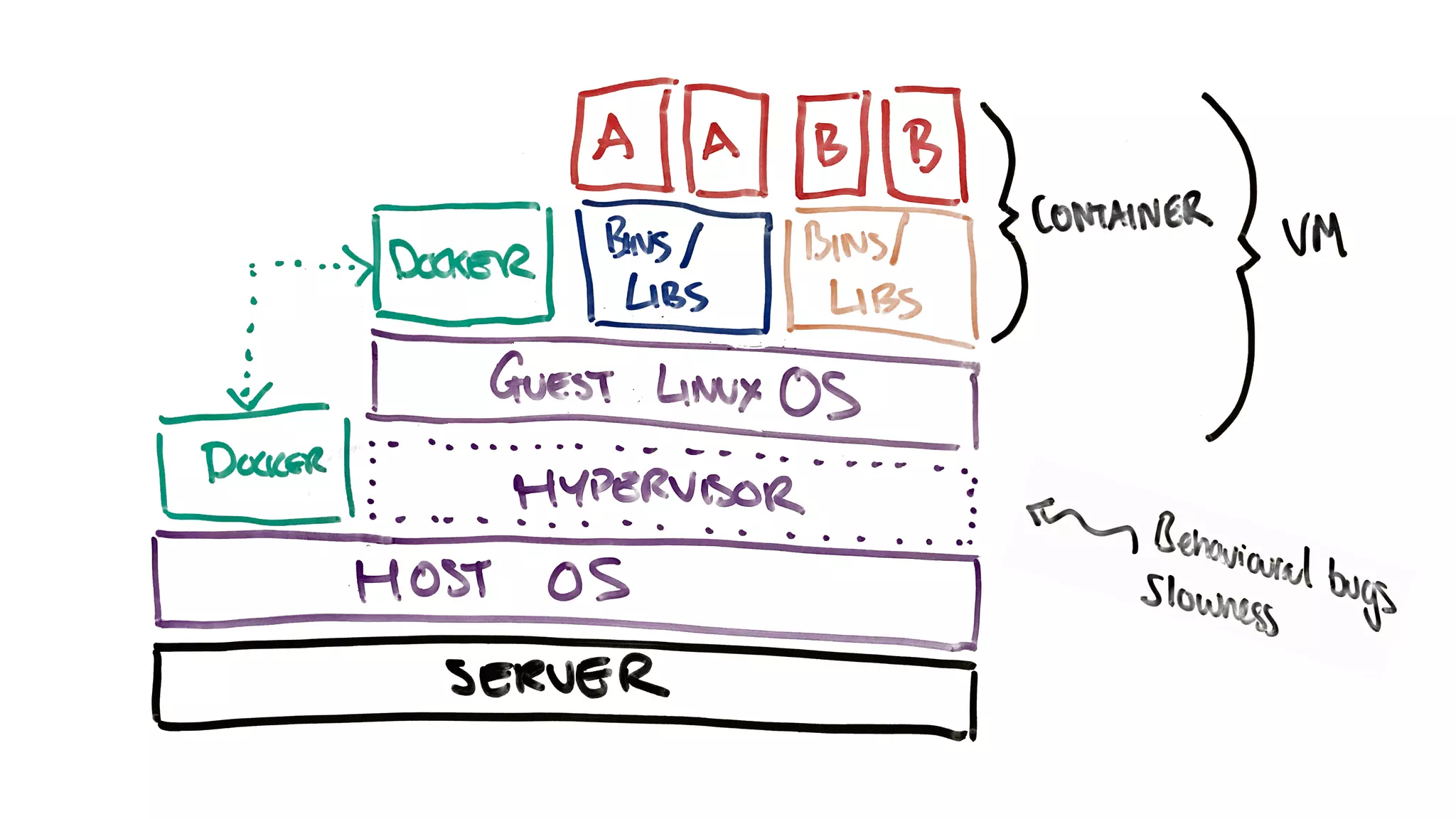
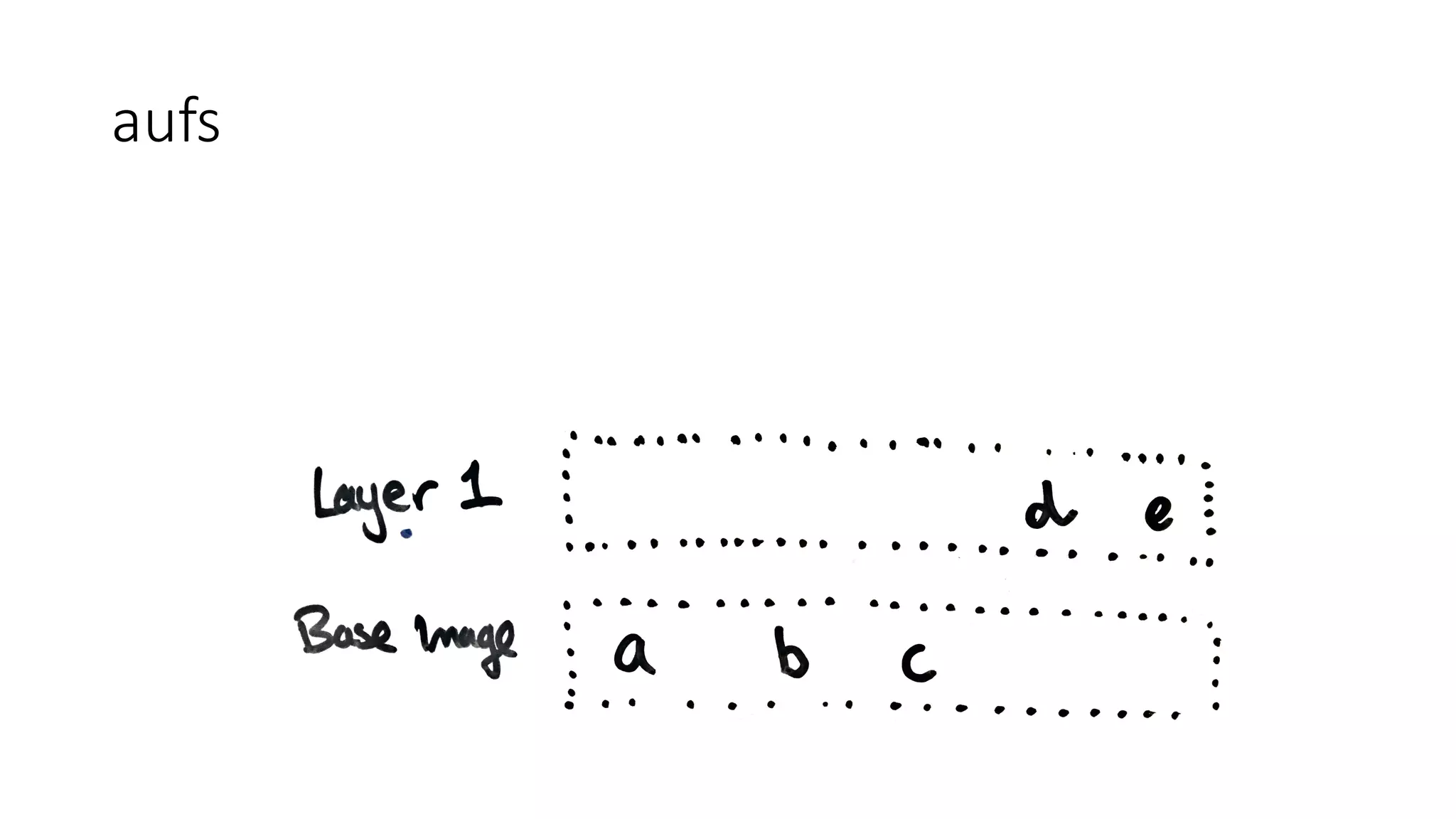
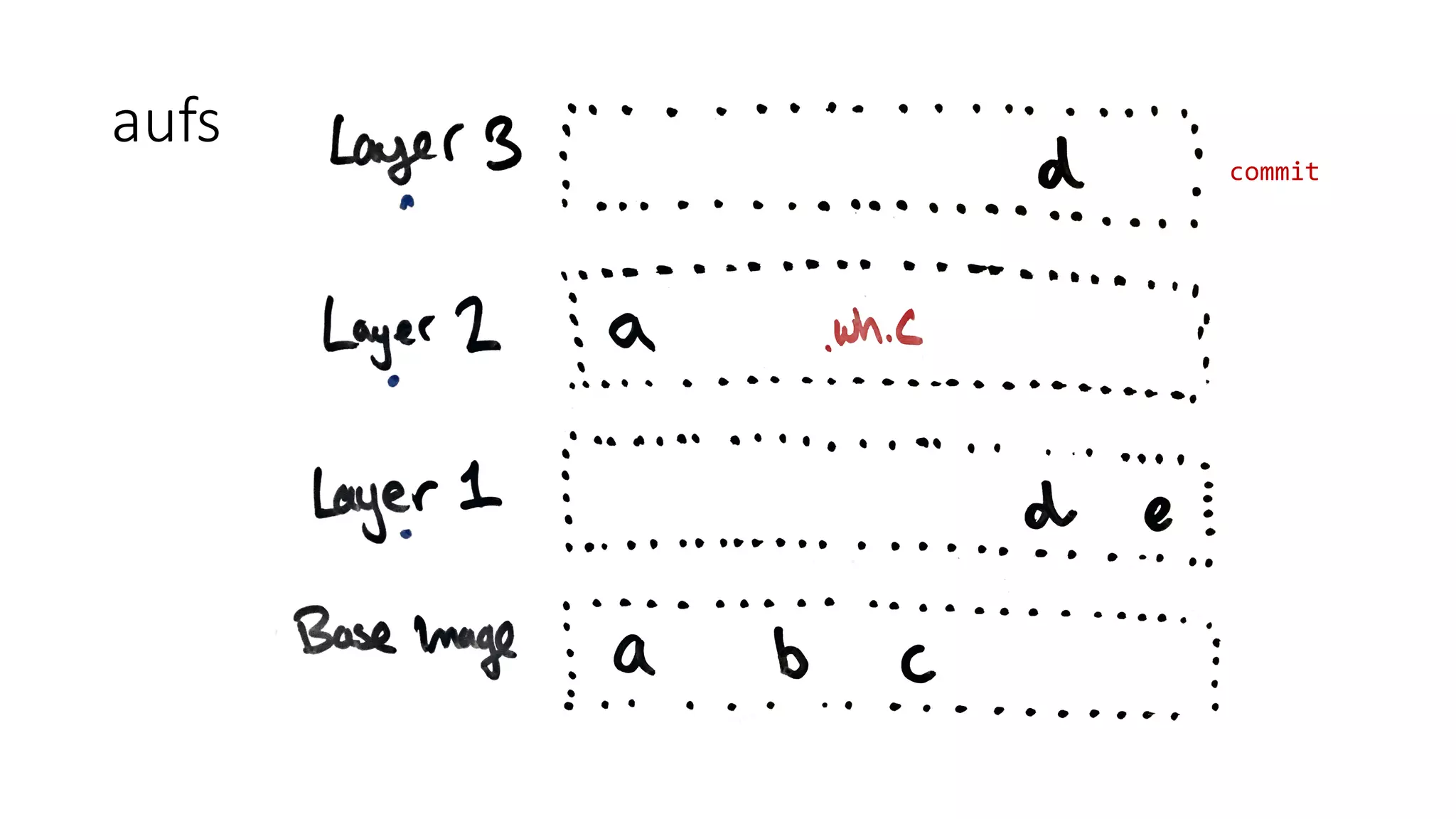
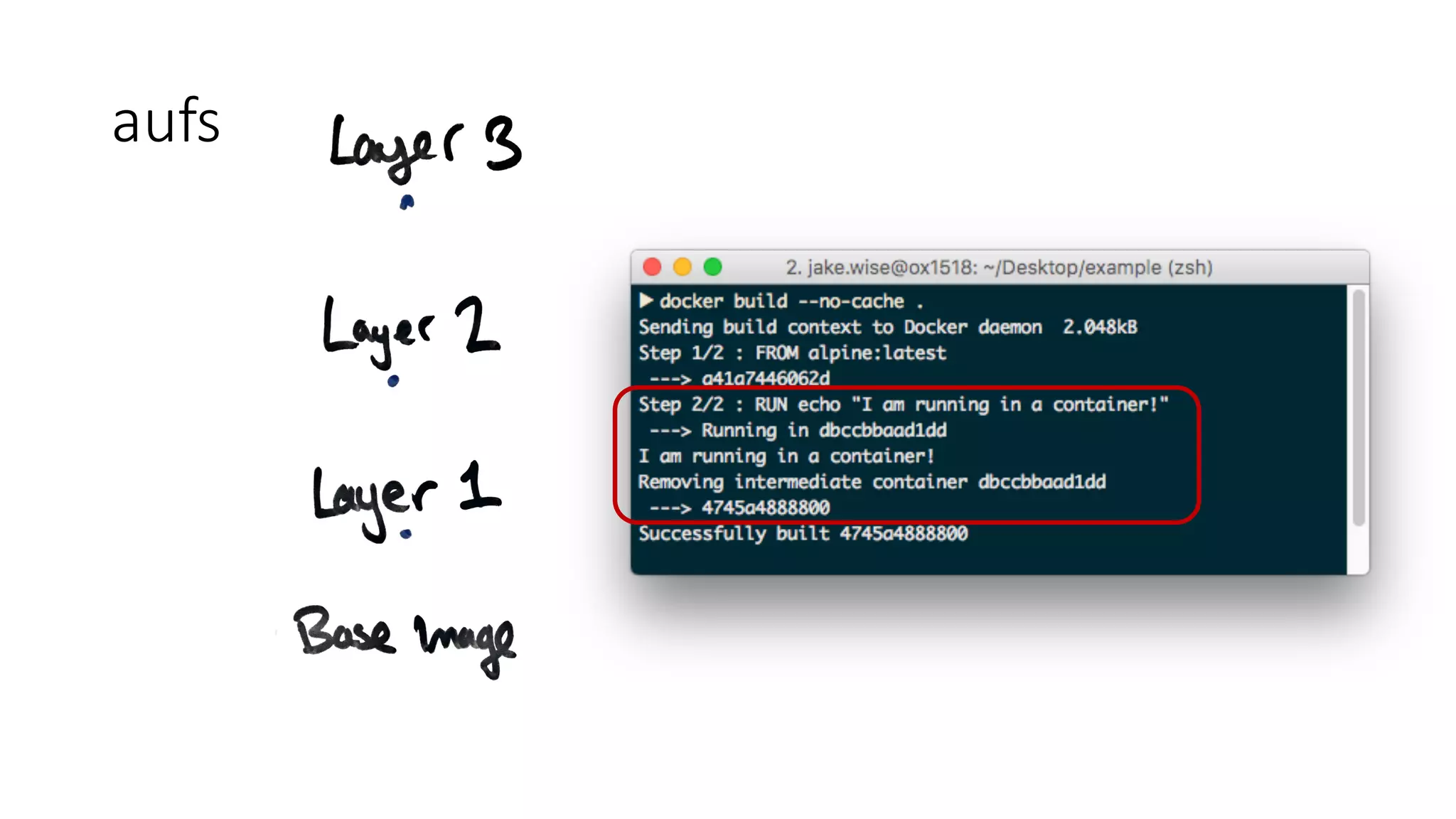
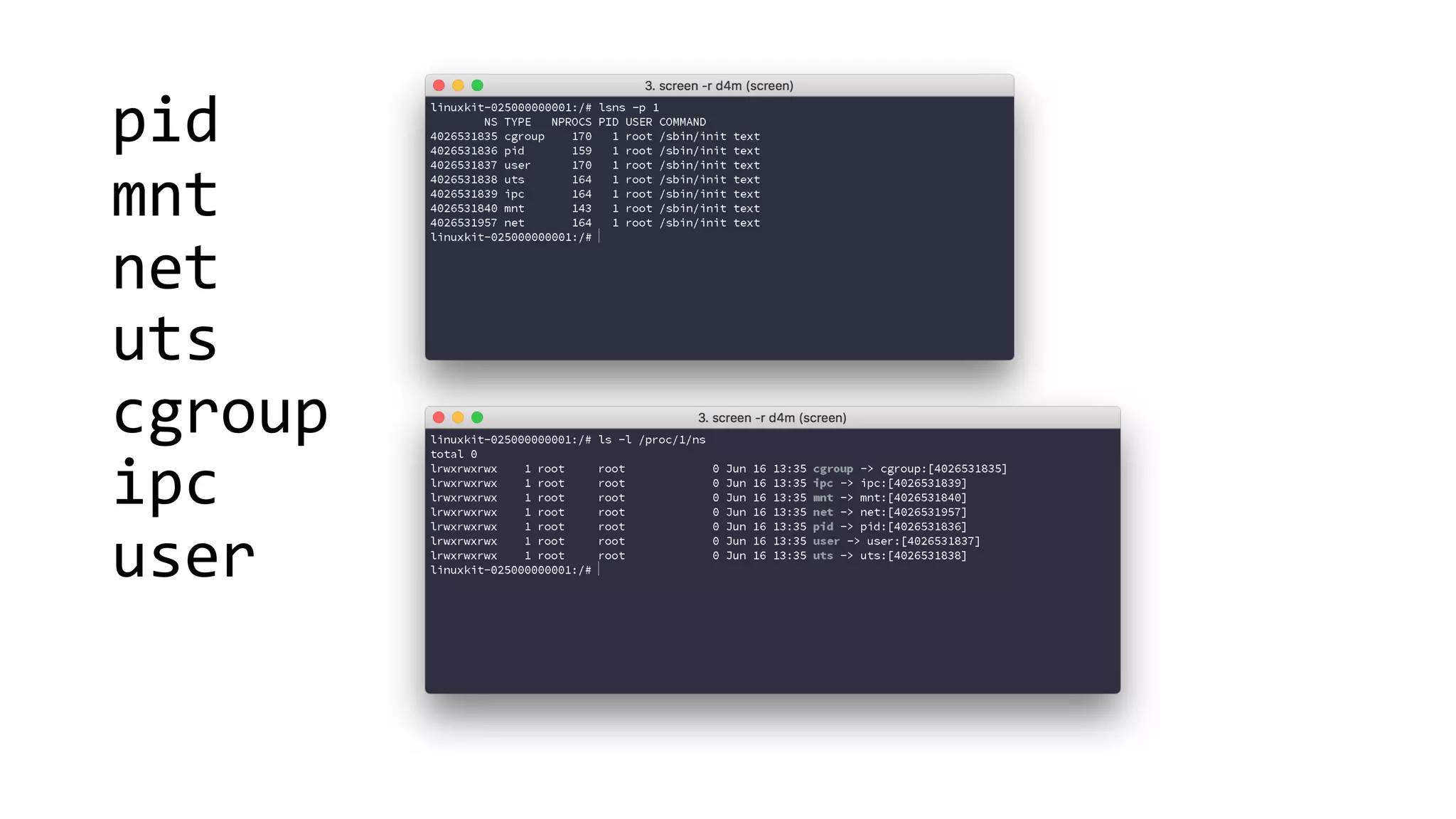
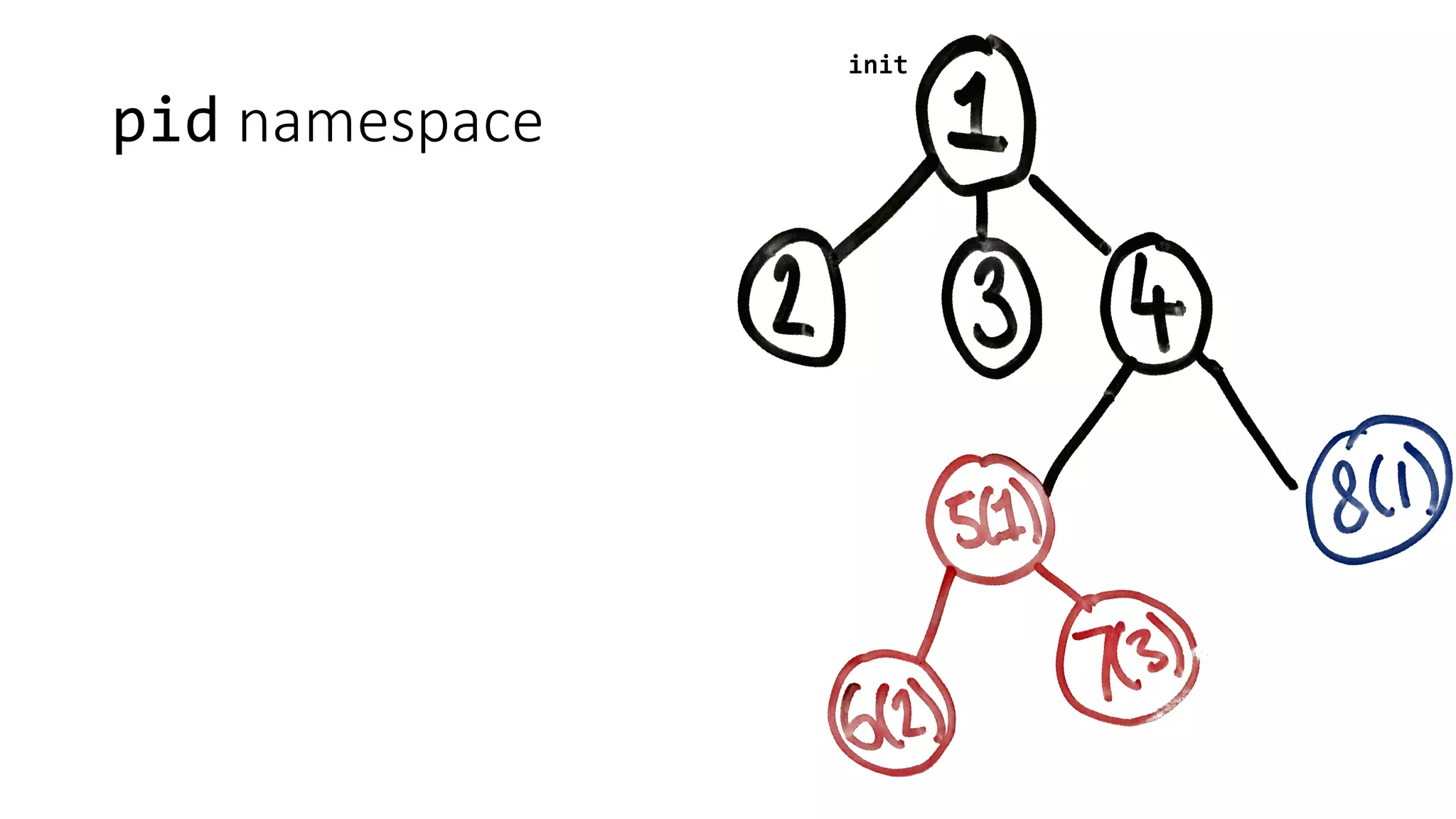
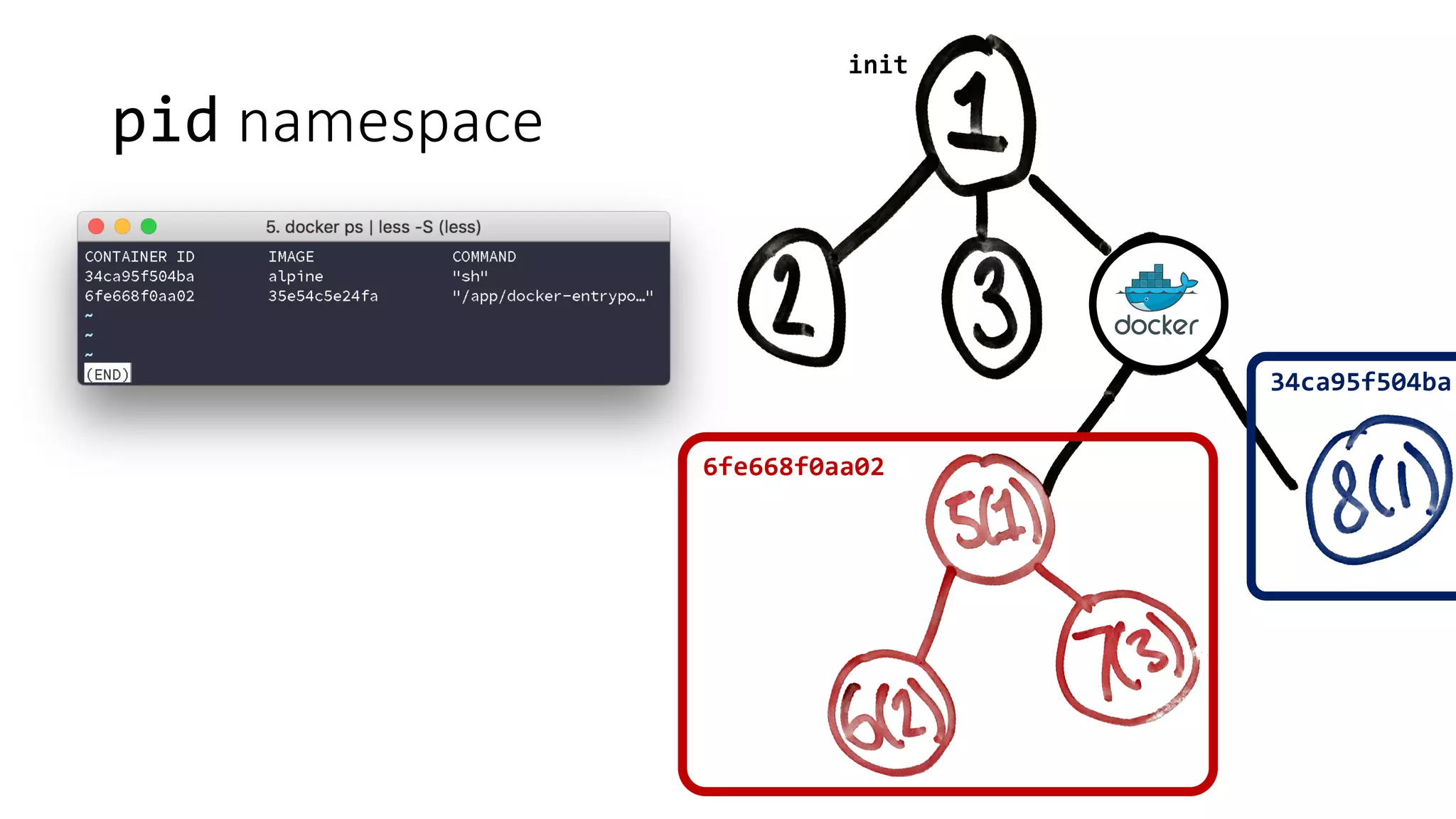
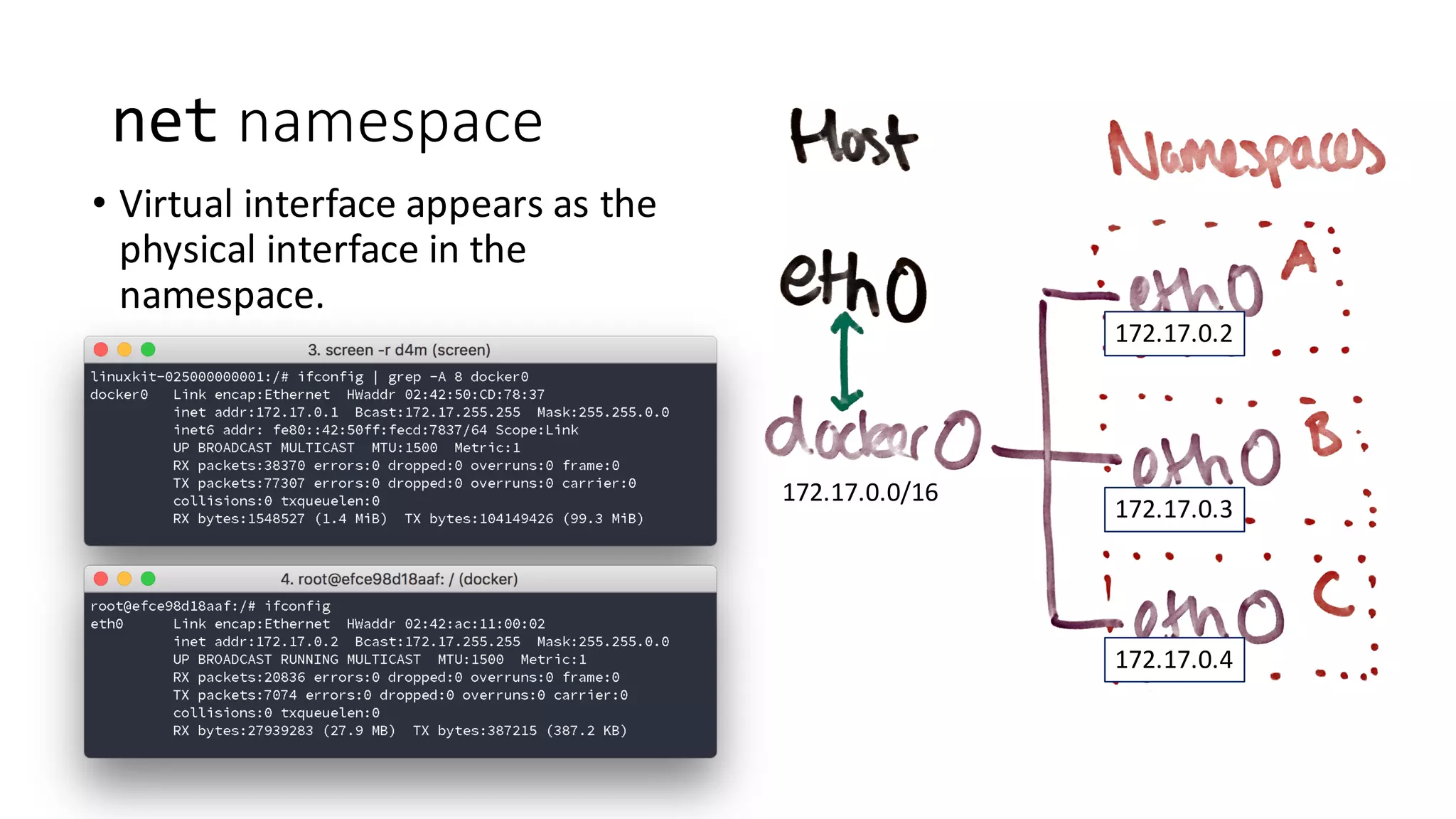
Containers provide isolation using Linux namespaces and control resource allocation via cgroups. A container is a set of namespaces that isolate processes and provide a restricted view of the filesystem. Docker uses the aufs filesystem to build containers from immutable layers, with the container itself as a writable top layer. Logging within containers should use stdout and stderr, and processes are generally kept separate rather than bundled together within a single container.