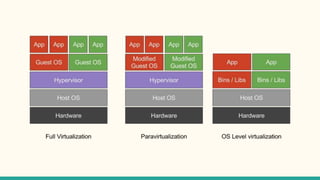
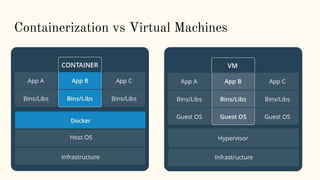
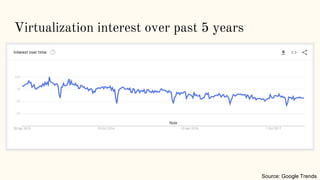
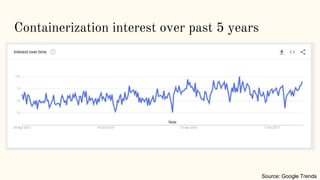
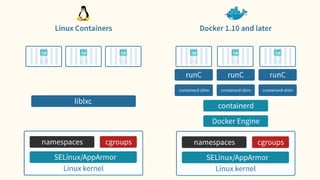
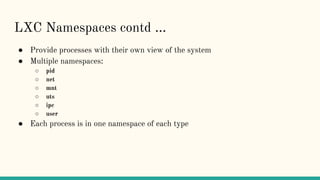
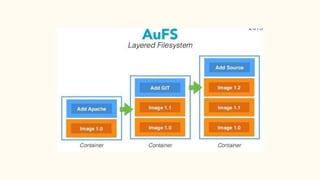
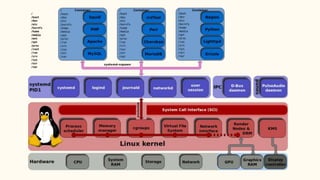
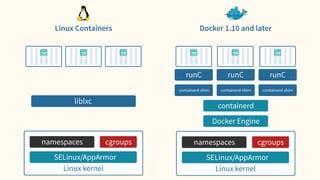
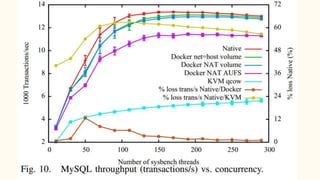
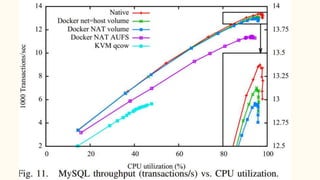
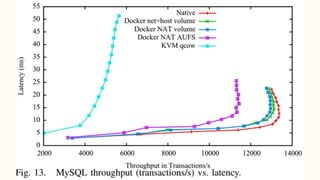
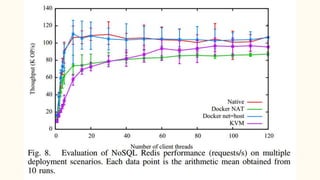
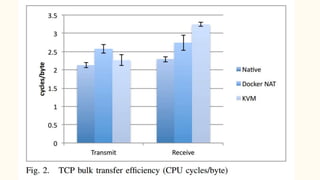
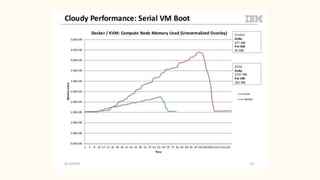
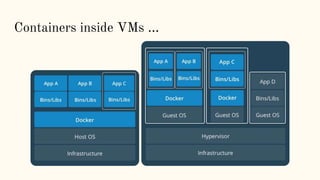
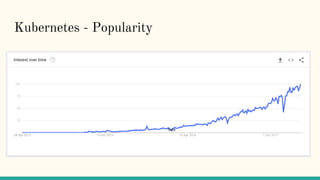
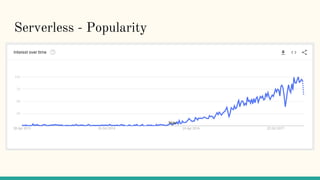
The document discusses virtualization and containerization, focusing on their differences and efficiency benefits. It explains how containers operate at the OS level, allowing for resource optimization and isolation through concepts like namespaces and cgroups, making them faster and cheaper to deploy than virtual machines. Additionally, it highlights the rise of Docker as a tool to manage dependencies and the growing interest in technologies such as Kubernetes and serverless architectures.



























![References
● Docker: lightweight linux containers for consistent development and
deployment [2014]
● An updated performance comparison of virtual machines and Linux containers
[2015]
● https://www.slideshare.net/jpetazzo/anatomy-of-a-container-namespaces-
cgroups-some-filesystem-magic-linuxcon
● https://www.slideshare.net/Docker/golubbenarevmspasse-
140402122017phpapp02-37589021
● https://www.slideshare.net/julienbarbier42/docker-the-future-of-distributed-
applications-docker-tour-de-france-2014](https://image.slidesharecdn.com/containerization-180918115711/85/Containerization-Docker-Under-the-Hood-50-320.jpg)