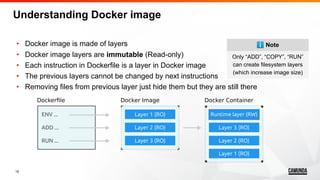
The workshop, led by DevOps engineer Ahmed Abouzaid, covers 18 best practices for effective Docker usage, organized into four categories: essential practices, image practices, security practices, and miscellaneous practices. Aimed at attendees with a basic knowledge of Docker, it includes hands-on experience applying the practices discussed and emphasizes the importance of using proper Dockerfile syntax, optimizing image size, ensuring security, and maintaining best practices in configuration. Key takeaways include using trusted images, avoiding unnecessary files, utilizing Docker build cache, and implementing a non-root user to enhance security.












![19
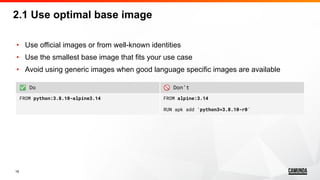
• Multi-stage feature allows you to build
smaller and cleaner images by splitting
the build image from the runtime image
• It’s super useful for languages that
create artifacts like Golang, Java, etc.
• Also it’s helpful to run various tests
during the development
• Additionally, it’s better for security
because it reduces the attack surface
2.4 Use multi-stage whenever possible
✅ Do
# Build stage.
FROM maven:3.6-openjdk-17 AS builder
[...]
RUN mvn clean package
# Runtime stage.
FROM openjdk:17-jdk-alpine3.14
COPY --from=builder /myapp.jar /opt/
ENTRYPOINT ["java", "-jar", "/opt/myapp.jar"]](https://image.slidesharecdn.com/dockerbestpracticesworkshop-ahmedabouzaid-21-210925004057/85/Docker-Best-Practices-Workshop-19-320.jpg)
![20
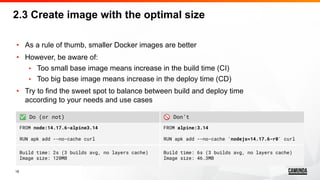
• Every extra file could increase build time, image size, or even both!
• Specify the files and paths that need to be part of the image
• Use “.dockerignore” to filter any unnecessary files
• If necessary, restructure your repo/code to have only needed files
in seperate folders
2.5 Avoid any unnecessary files
✅ Do 🚫 Don’t
FROM python
# Only needed files are added to the image
COPY myapp.py /opt
ENTRYPOINT ["python", "/opt/myapp.py"]
FROM python
# The whole repo/context is added to the image
COPY . /opt
ENTRYPOINT ["python", "/opt/myapp.py"]](https://image.slidesharecdn.com/dockerbestpracticesworkshop-ahmedabouzaid-21-210925004057/85/Docker-Best-Practices-Workshop-20-320.jpg)


![25
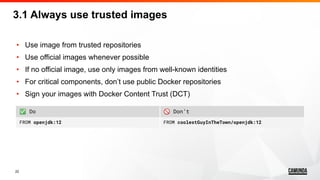
• By default, Docker will use “root” to execute the container commands
• Using root user is a bad practice and considered a security risk
• Always (or whenever possible) set “USER” instruction to a non-root user
• Remember that the user must already exist in the Docker image system
to be used with the “USER” instruction
3.4 Use a non-root user
✅ Do 🚫 Don’t
FROM alpine
USER nobody
CMD ["whoami"]
FROM alpine
# The root user will be used to execute commands
CMD ["whoami"]
Output: nobody Output: root](https://image.slidesharecdn.com/dockerbestpracticesworkshop-ahmedabouzaid-21-210925004057/85/Docker-Best-Practices-Workshop-25-320.jpg)
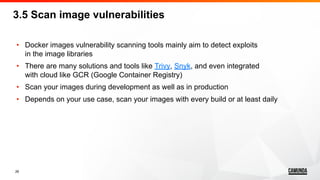

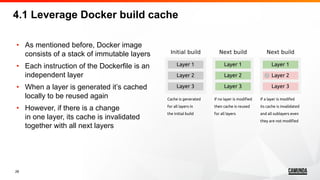
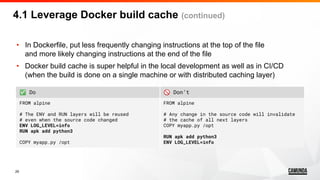

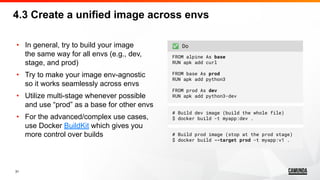
![32
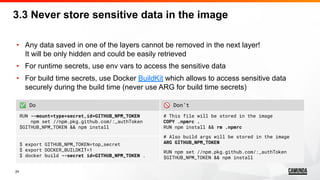
• Both “ENTRYPOINT” and “CMD” are Dockerfile instructions
which used to control the default command within the Docker image
• Either of “ENTRYPOINT” and “CMD” could be used independently
• However, using both of them at the same time makes things easier
to customize containers behaviour, especially in Kubernetes
• As a rule of thumb, if your application customizable via arguments
use “ENTRYPOINT” for the main command and “CMD” for default arguments
4.4 Use ENTRYPOINT with CMD
✅ Do
FROM alpine
ENTRYPOINT ["echo"]
CMD ["-e", "HellonWorld"]](https://image.slidesharecdn.com/dockerbestpracticesworkshop-ahmedabouzaid-21-210925004057/85/Docker-Best-Practices-Workshop-32-320.jpg)




