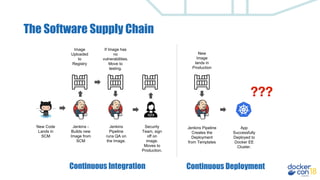
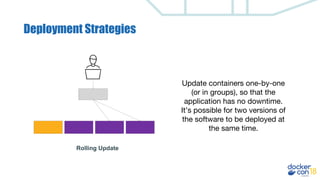
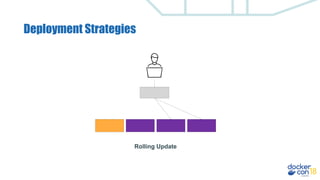
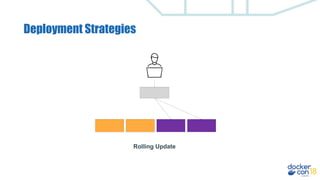
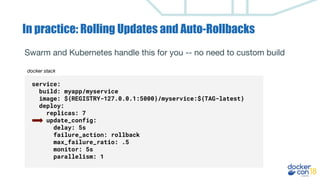
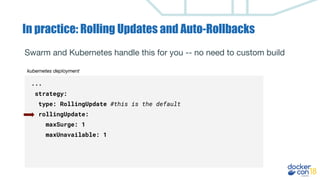
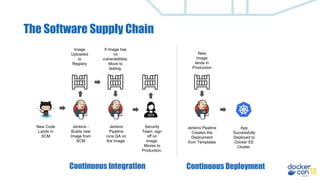
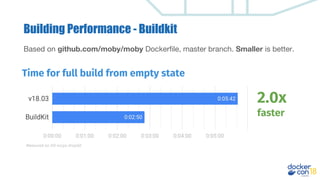
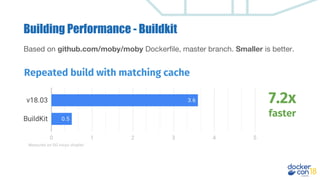
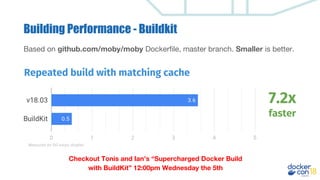
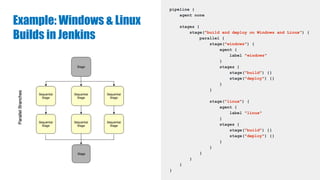
This document discusses building a development pipeline using containers. It outlines using containers for building images, automated testing, security scanning, and deploying to production. Containers make environments consistent and reproducible. The pipeline includes building images, testing, security scanning, and promoting images to production. Methods discussed include using multi-stage builds to optimize images, leveraging Buildkit for faster builds, and parallel testing across containers. Automated tools are available to implement rolling updates and rollbacks during deployments.
















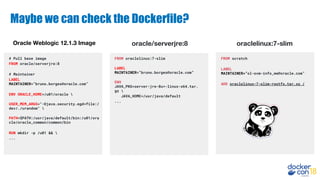
![Building Performance - MultiStage Builds
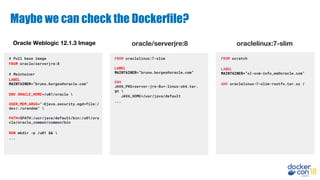
Multi-stage builds in your Dockerfiles. Introduced in Docker CE 17.05.
FROM golang:1.7.3 AS BUILDER
WORKDIR /go/src/github.com/alexellis/href-counter/
RUN go get -d -v golang.org/x/net/html
COPY app.go .
RUN CGO_ENABLED=0 GOOS=linux go build -a -installsuffix cgo -o app
.
FROM alpine:latest
RUN apk --no-cache add ca-certificates
WORKDIR /root/
COPY --from=BUILDER /go/src/github.com/alexellis/href-counter/app .
CMD ["./app"]](https://image.slidesharecdn.com/dceu18buildingyourdevelopmentpipeline-181214184701/85/DCEU-18-Building-Your-Development-Pipeline-19-320.jpg)






![In practice: integration testing patterns
docker-compose.yml docker-compose.test.yml
version: '3'
services:
vote:
build: ../vote/
ports: ["80"]
depends_on:
- redis
- db
networks:
- front-tier
- back-tier
result:
...
worker:
...
redis:
...
db:
...
version: '3'
services:
test:
build: ./tests/
depends_on:
- vote
- result
- worker
vote:
...
result:
...
worker:
...
redis:
...
db:
...
Create new one-off application
environment
Create service to run integration tests](https://image.slidesharecdn.com/dceu18buildingyourdevelopmentpipeline-181214184701/85/DCEU-18-Building-Your-Development-Pipeline-29-320.jpg)






![How do I control what runs in my cluster??
How do I stop my developers running unknown images from the internet on my
production clusters?
$ kubectl apply -f exampleapp.yaml
Error from server (Forbidden): error when creating "exampleapp.yaml": pods
"nginx" is forbidden: one or more container images do not meet the required
signing policy: [nginx: image did not meet required signing policy]
$ docker run nginx:latest
docker: Error response from daemon: image did not meet required signing
policy.](https://image.slidesharecdn.com/dceu18buildingyourdevelopmentpipeline-181214184701/85/DCEU-18-Building-Your-Development-Pipeline-43-320.jpg)