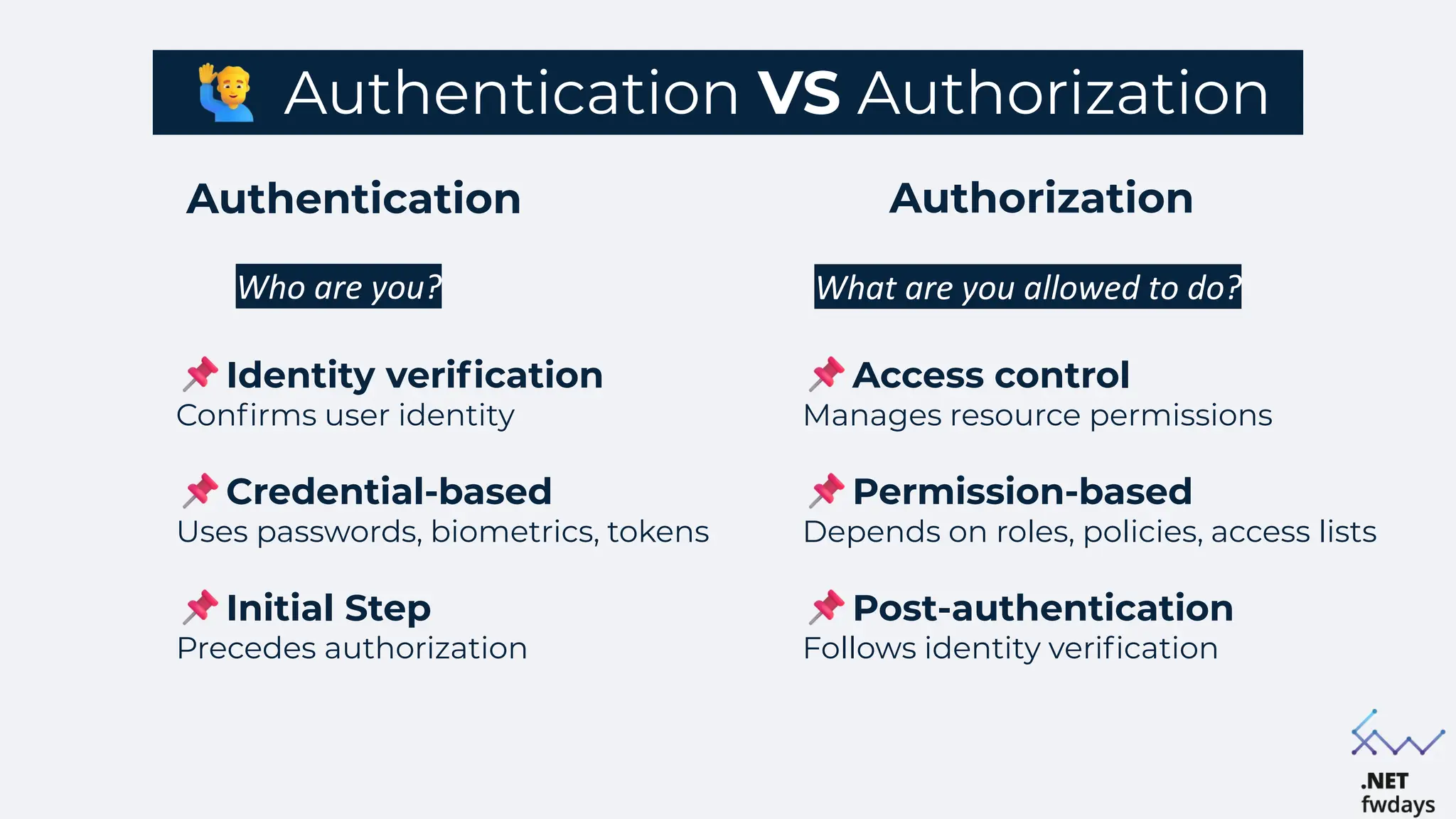
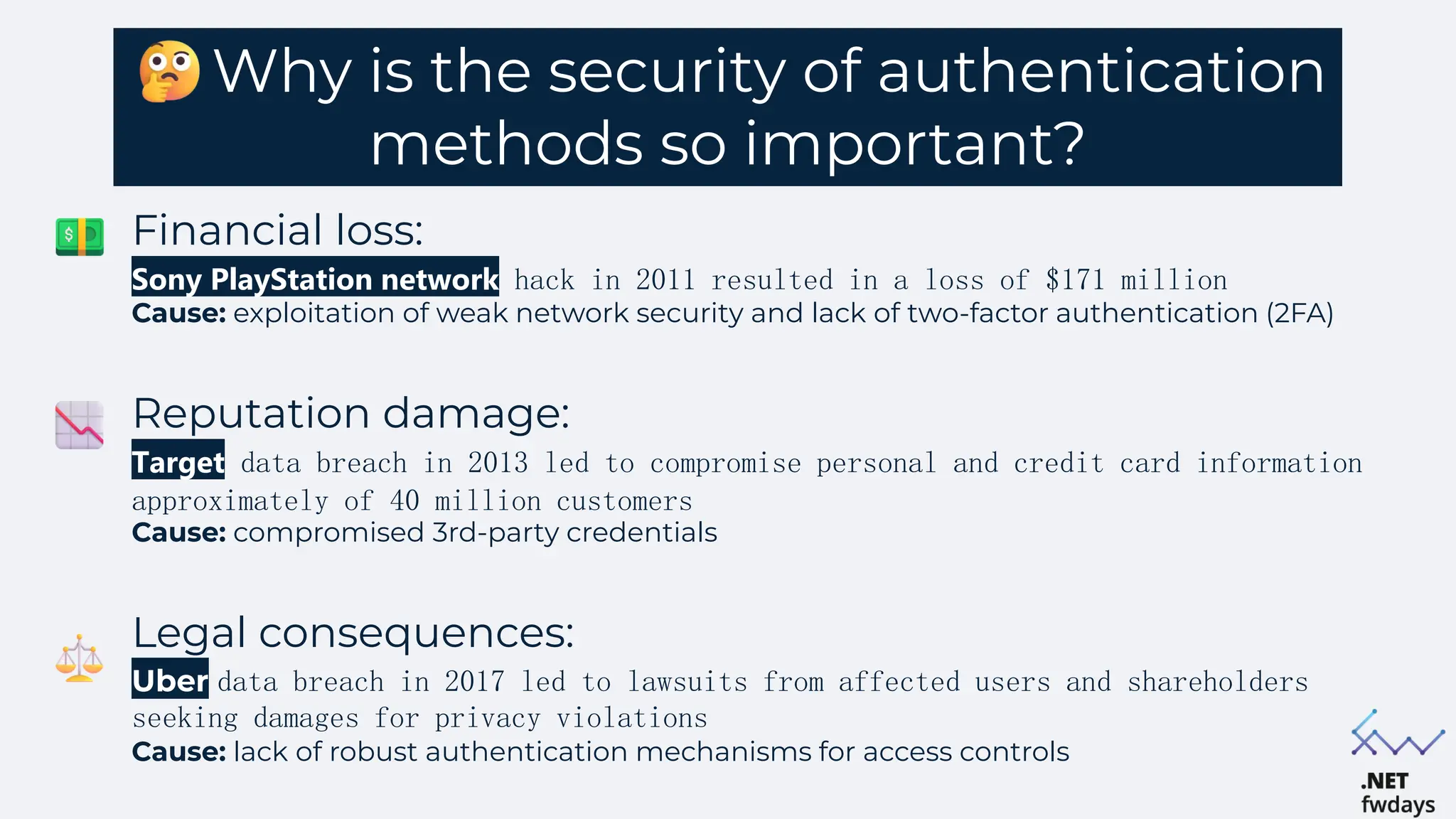
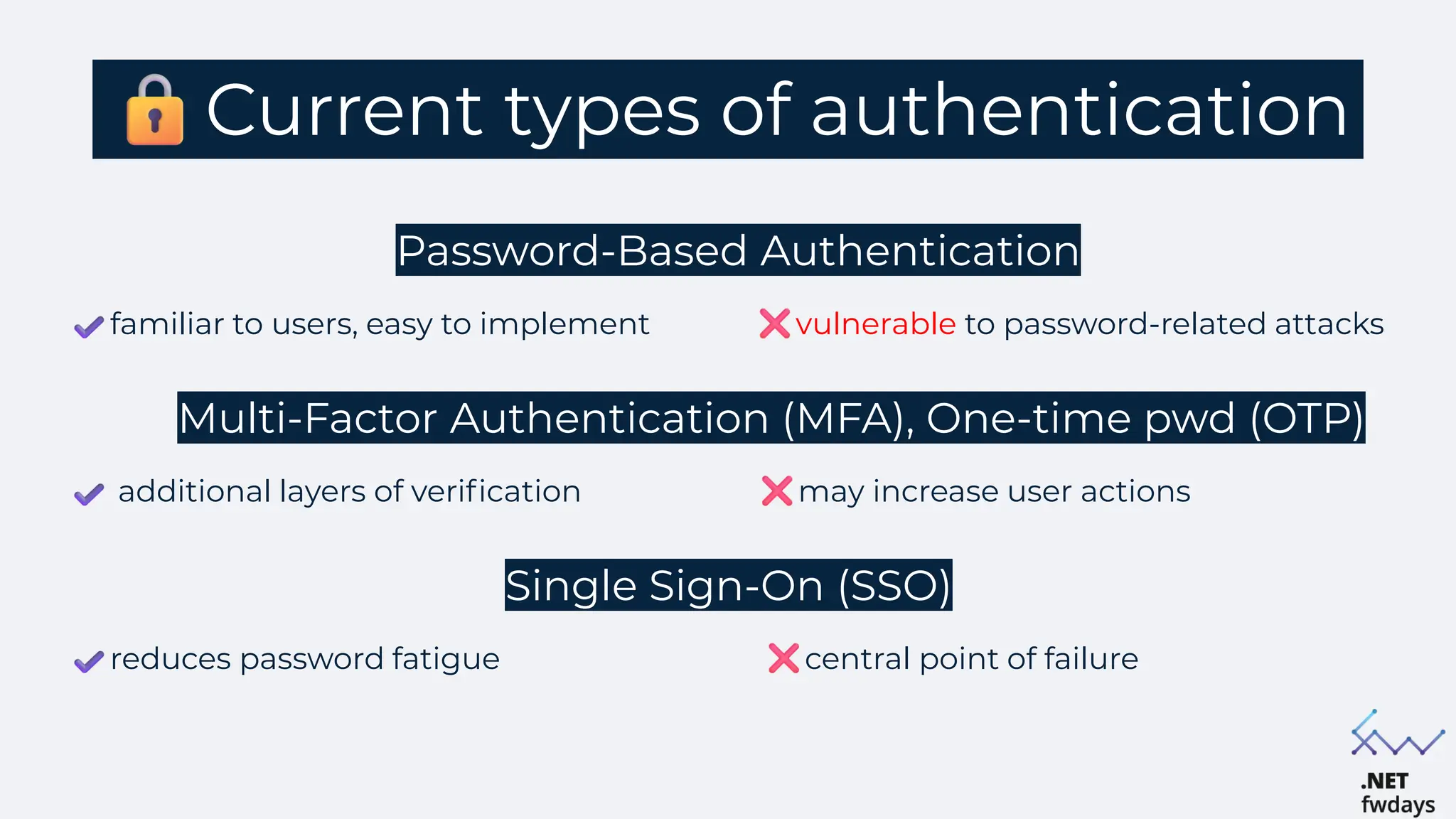
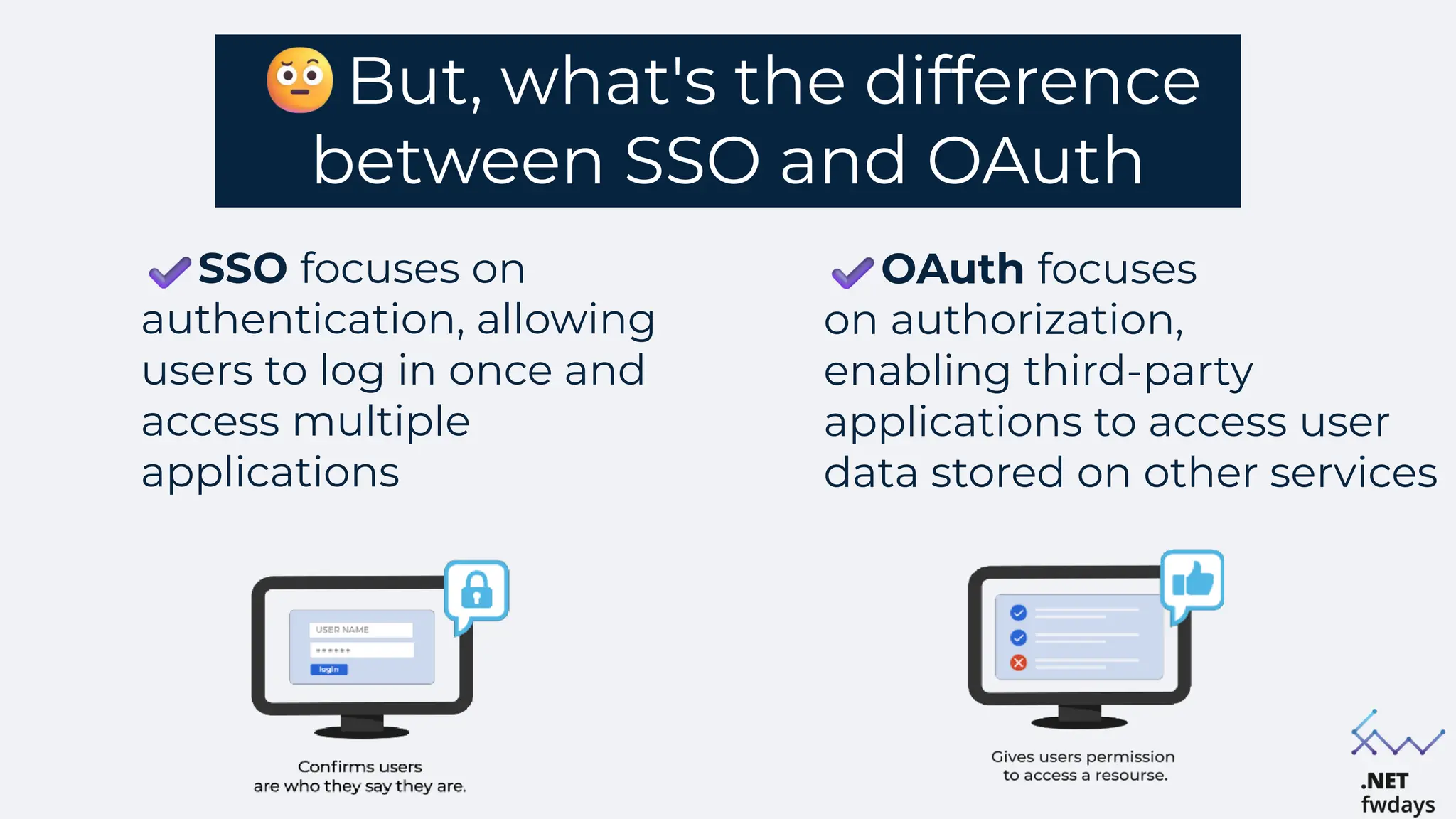
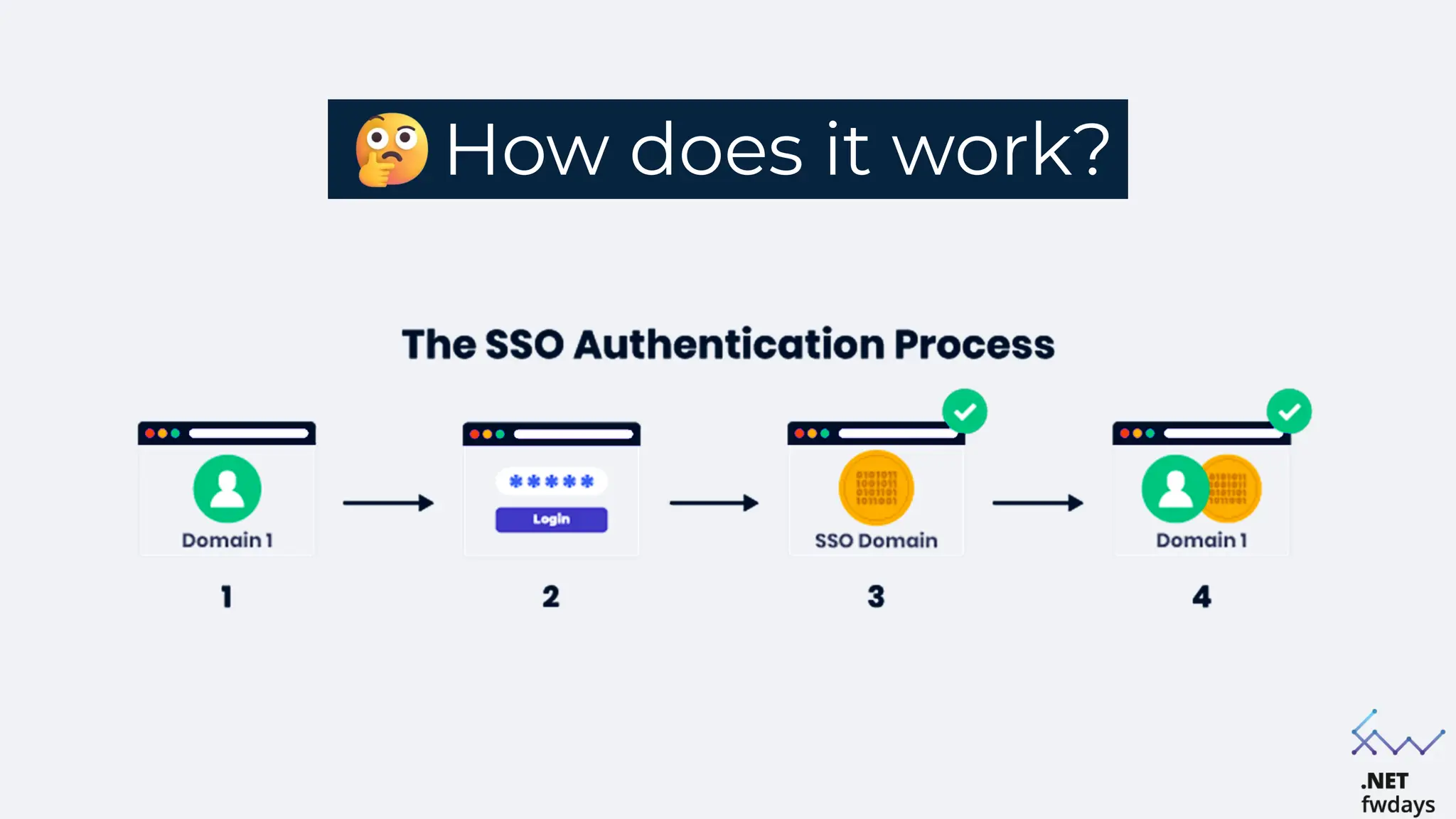
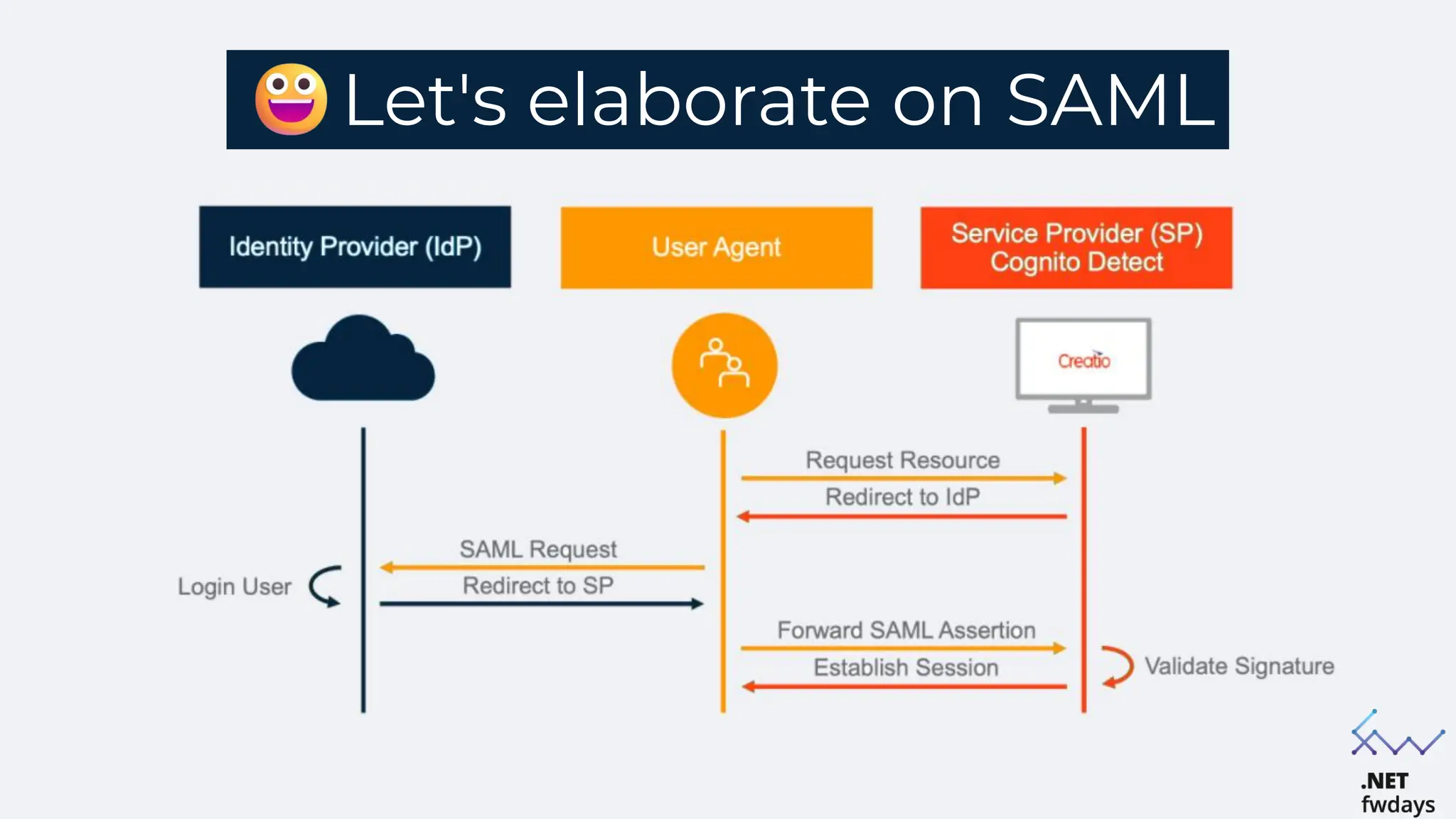
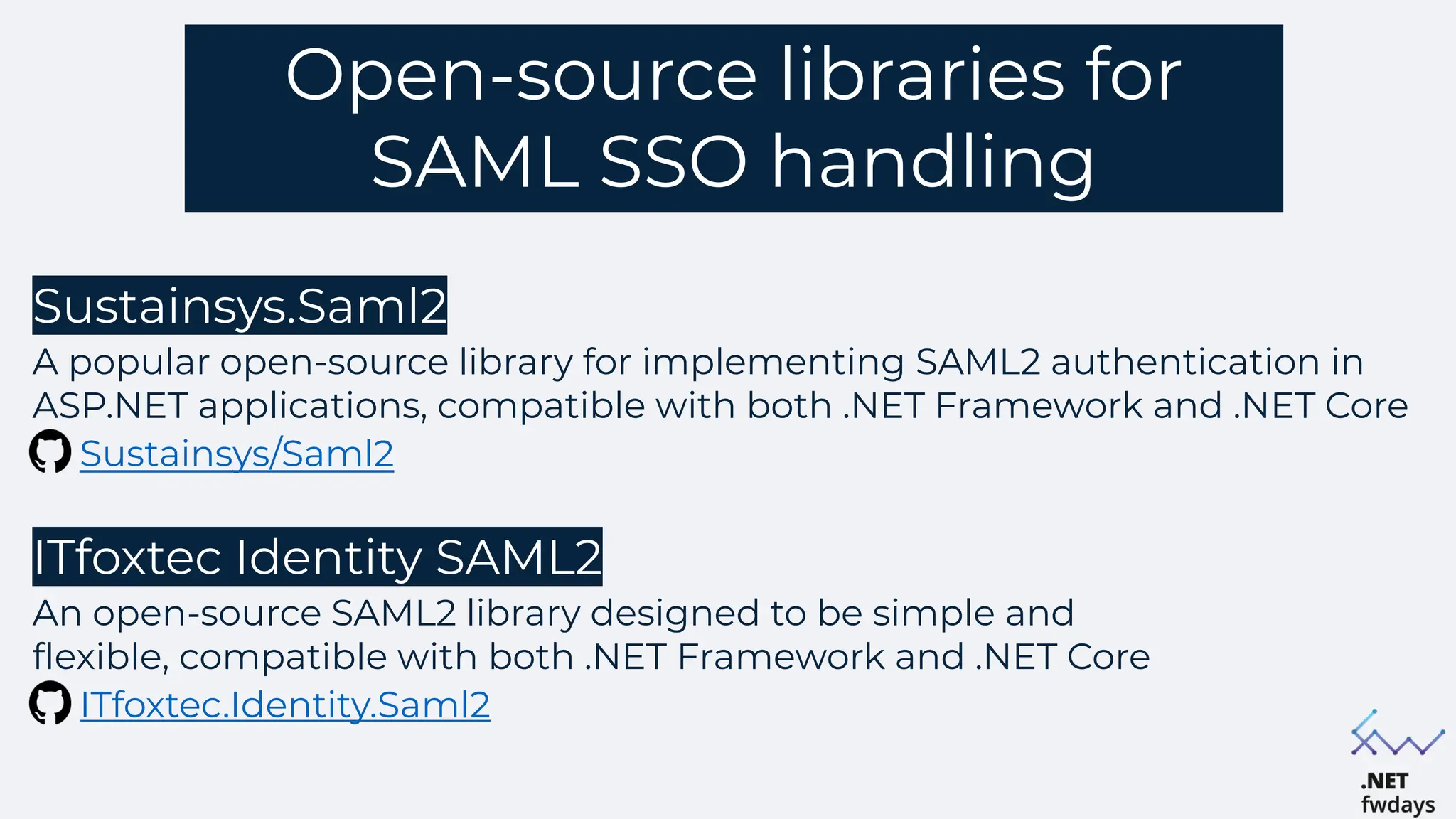
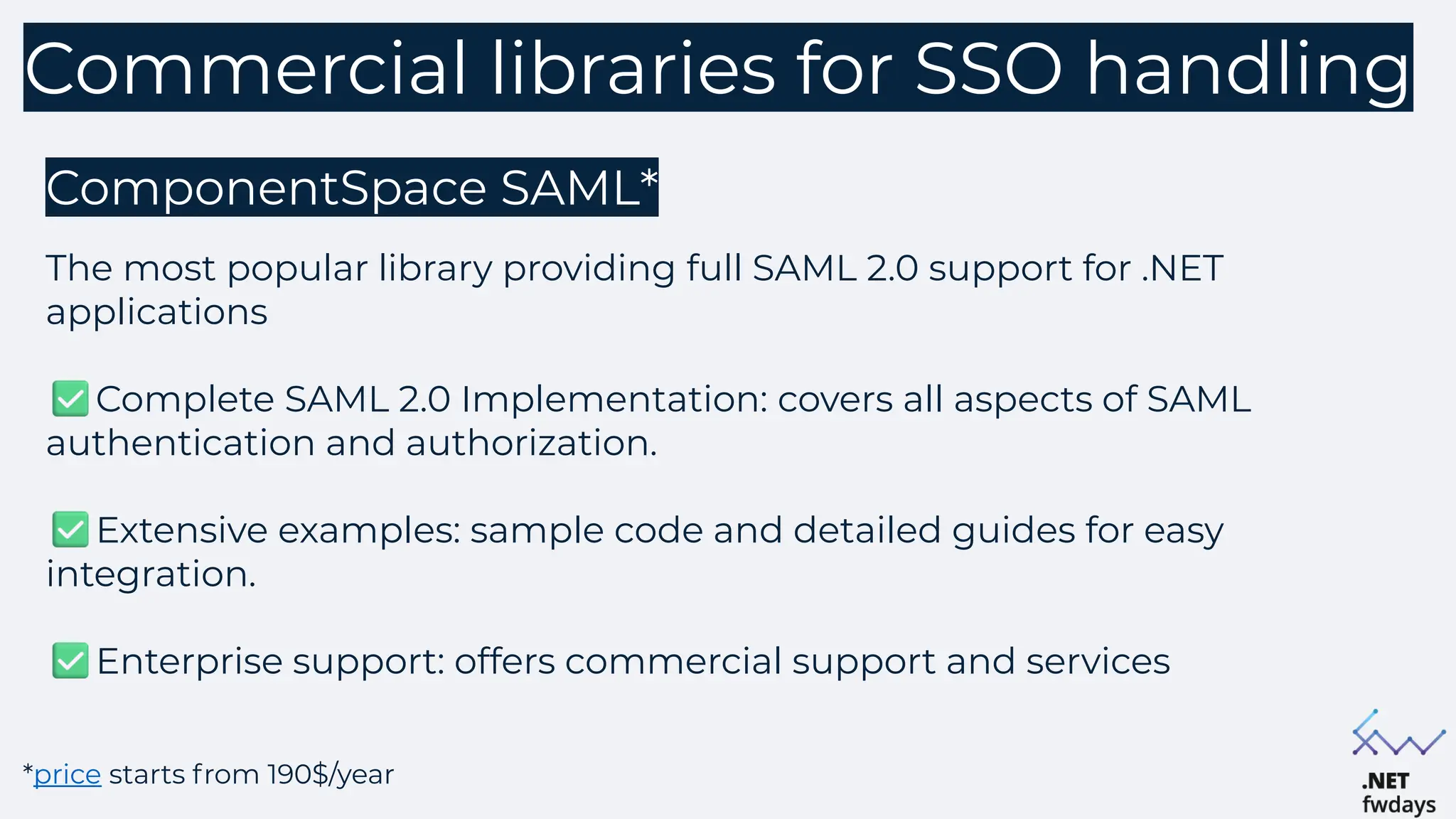
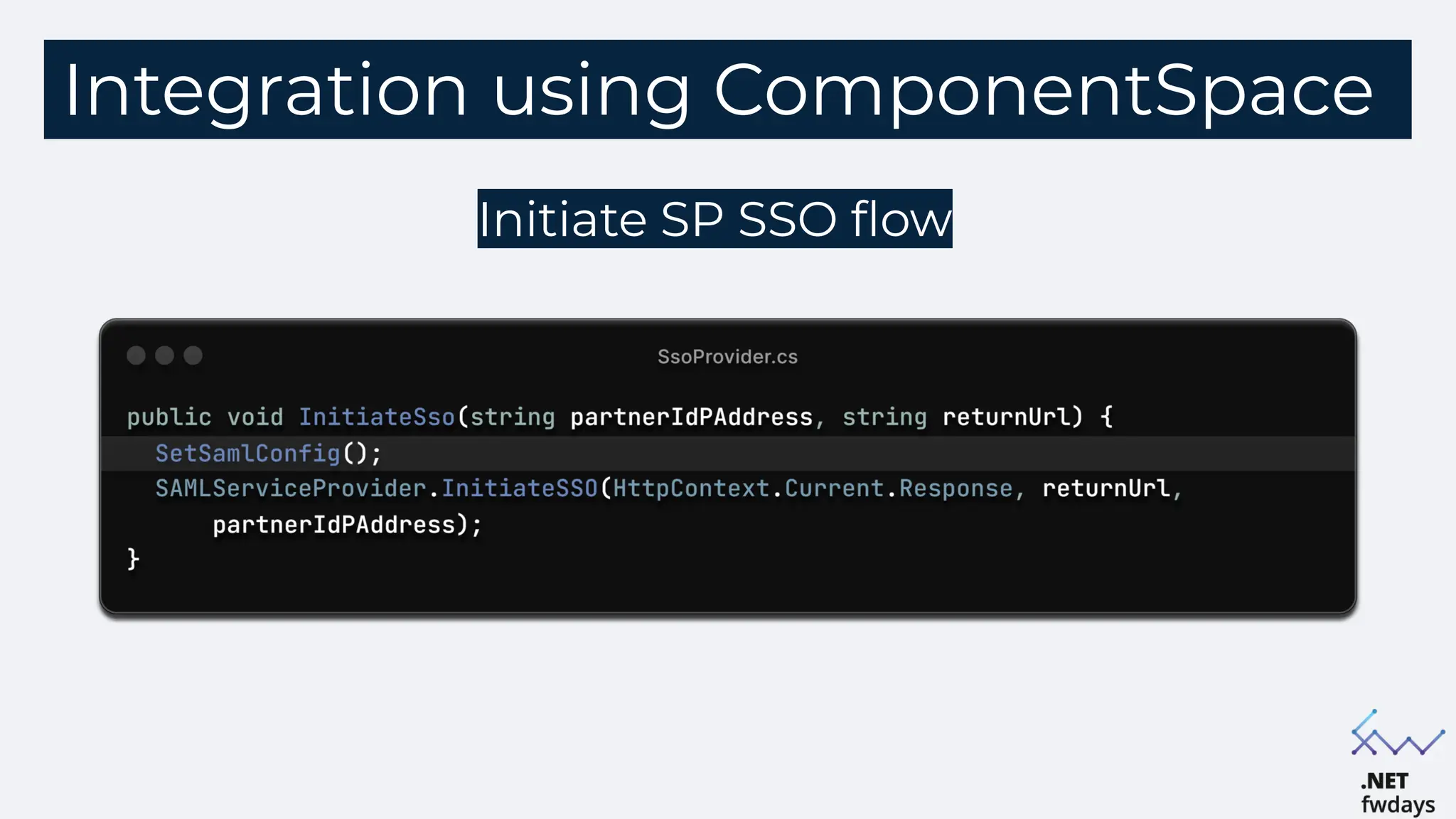
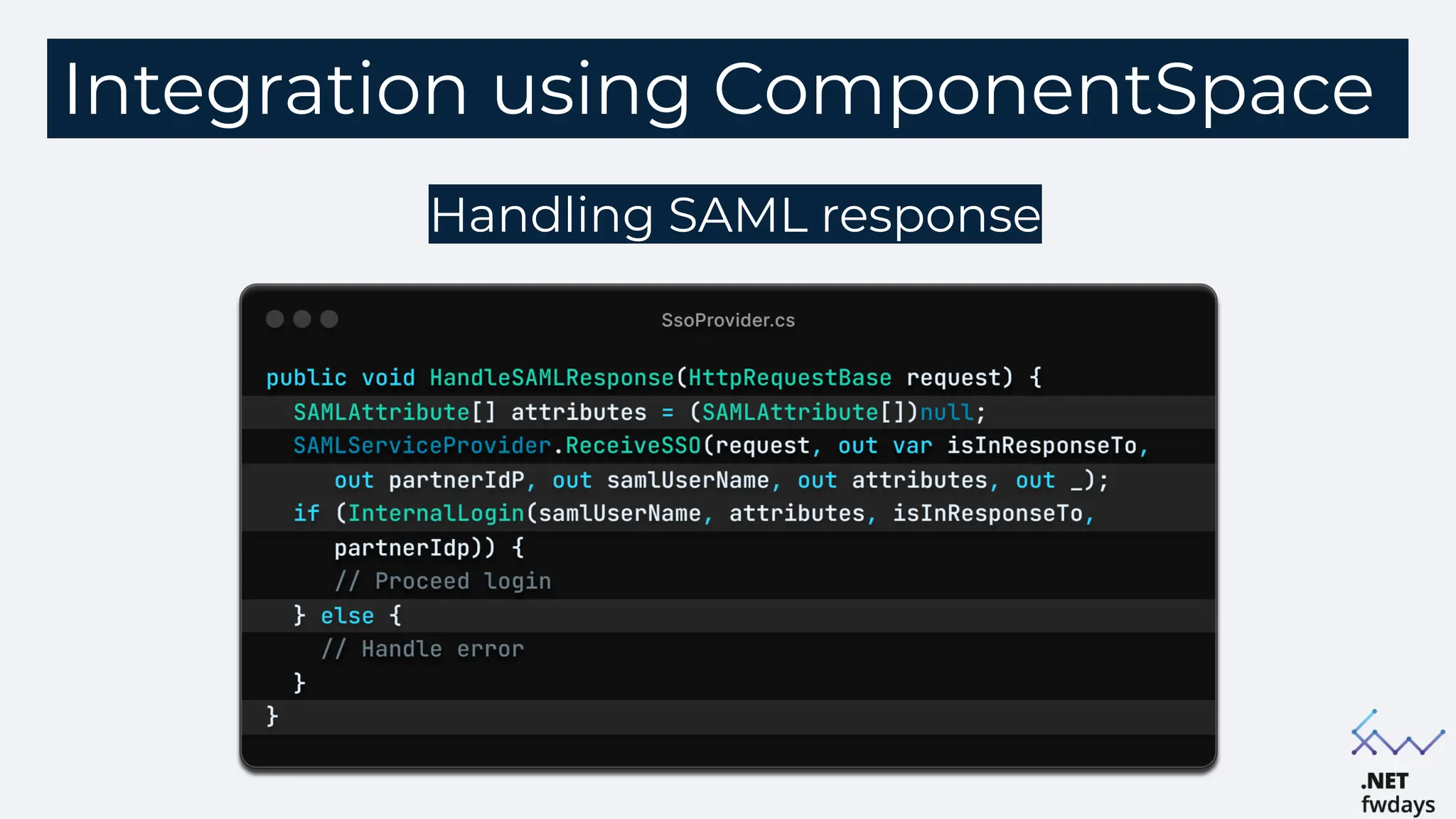
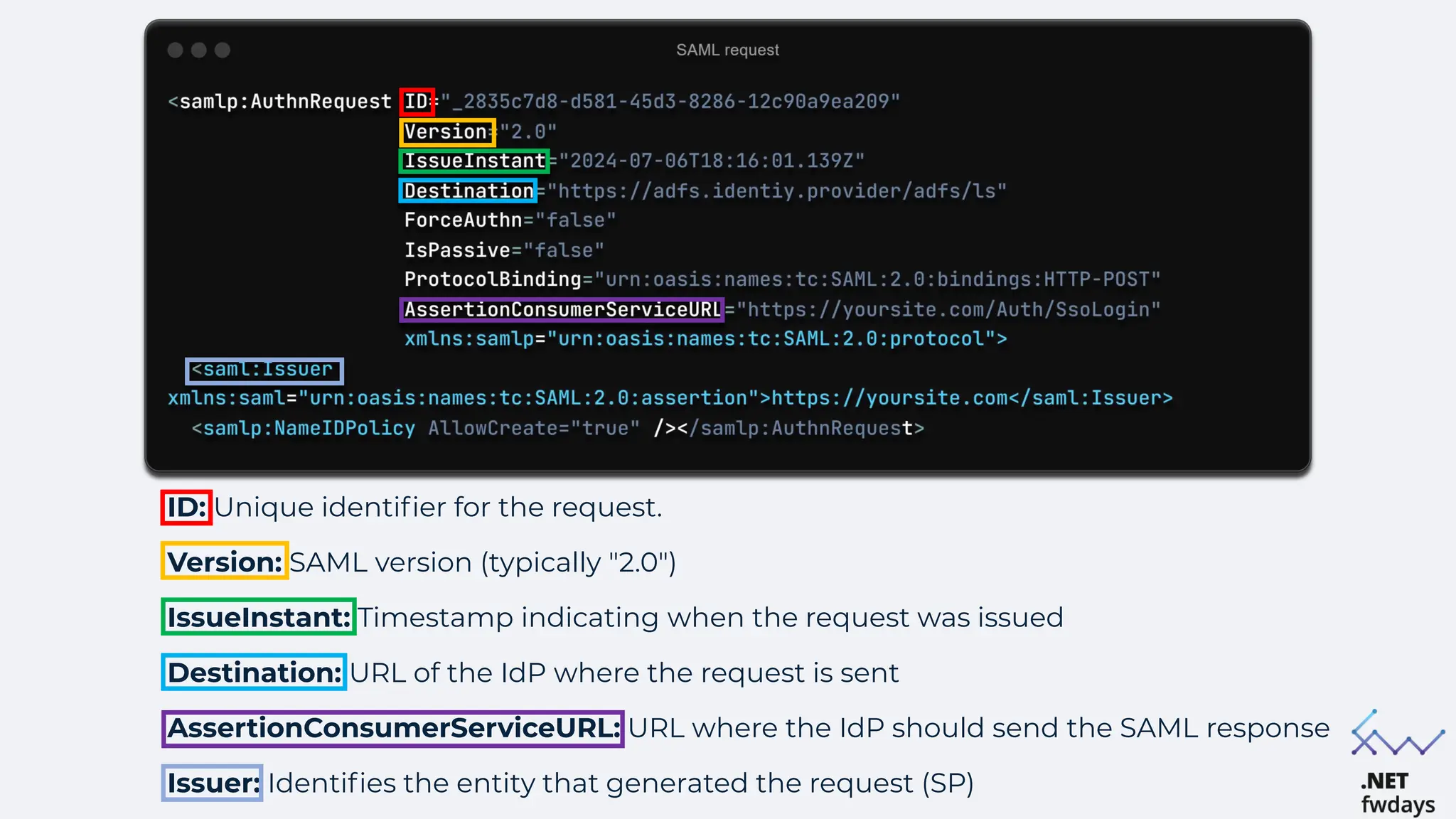
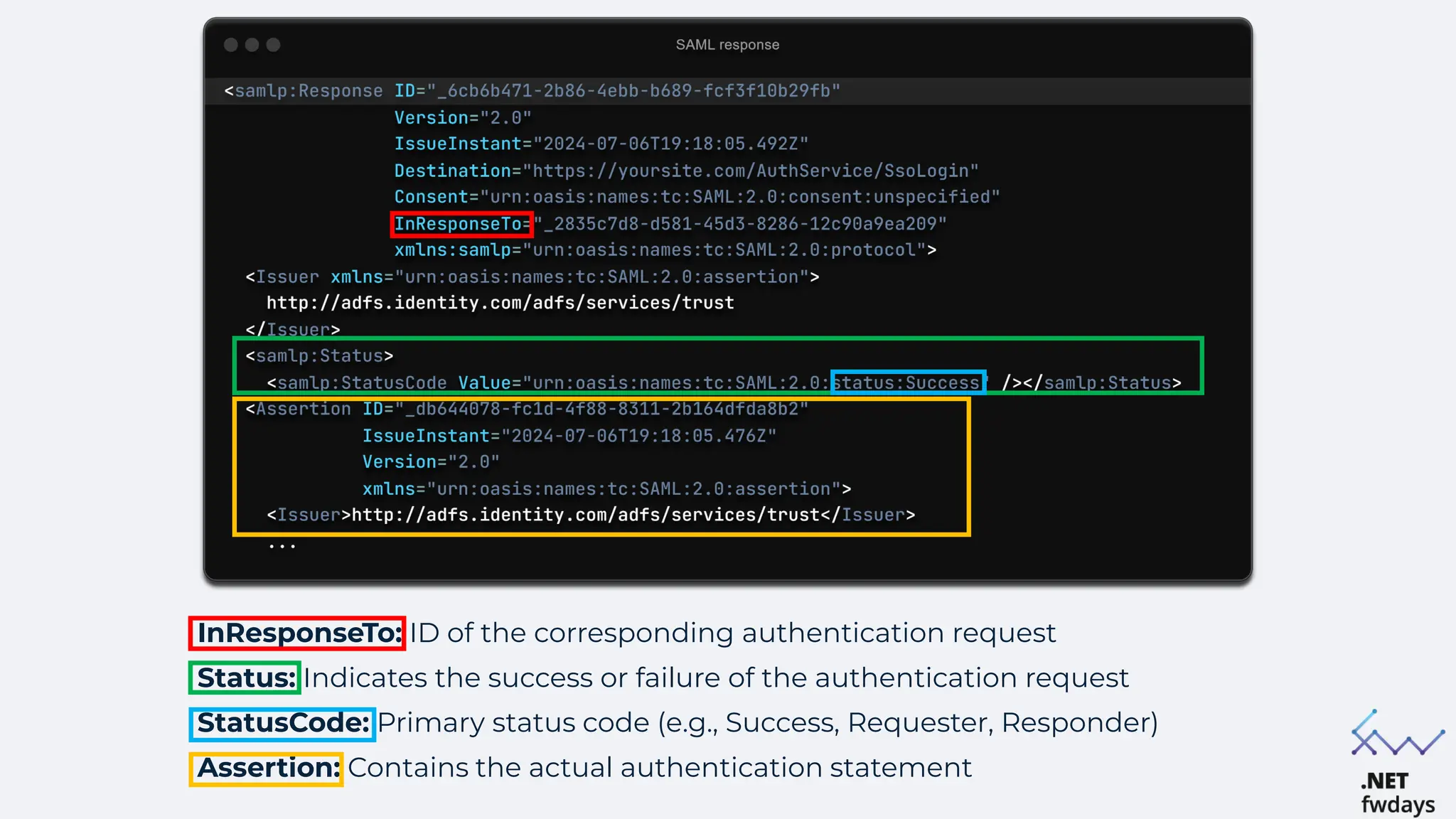
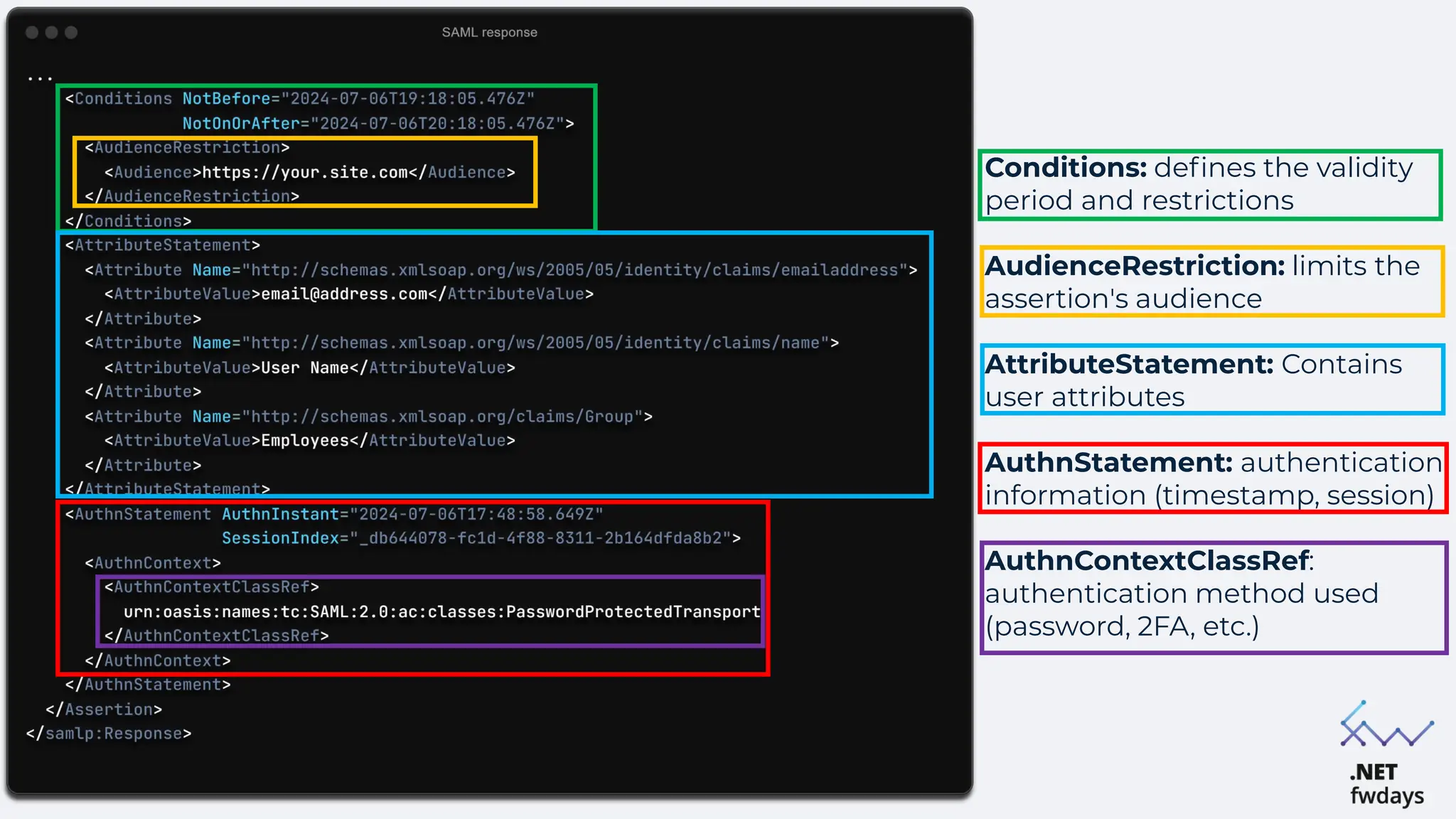
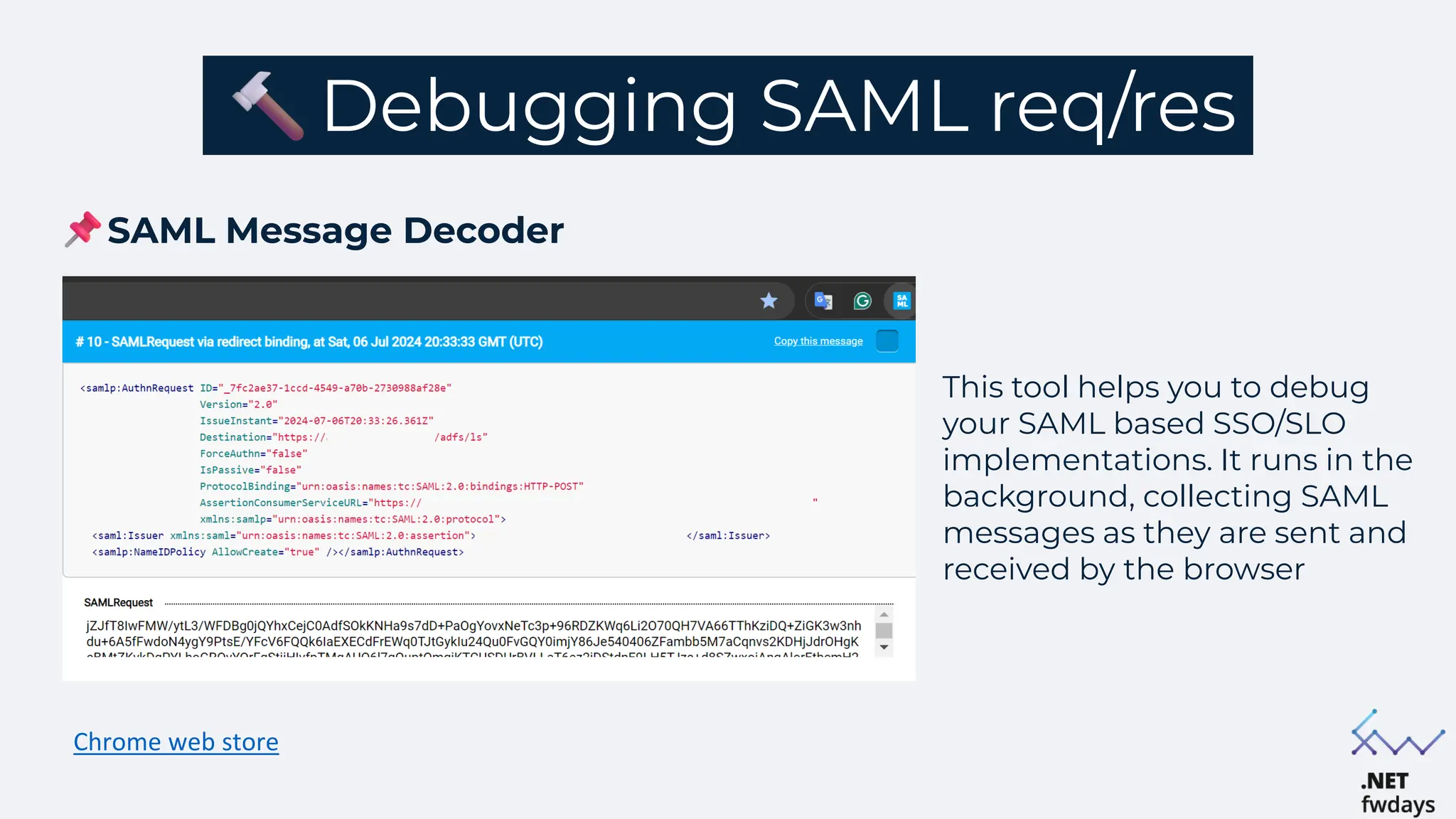
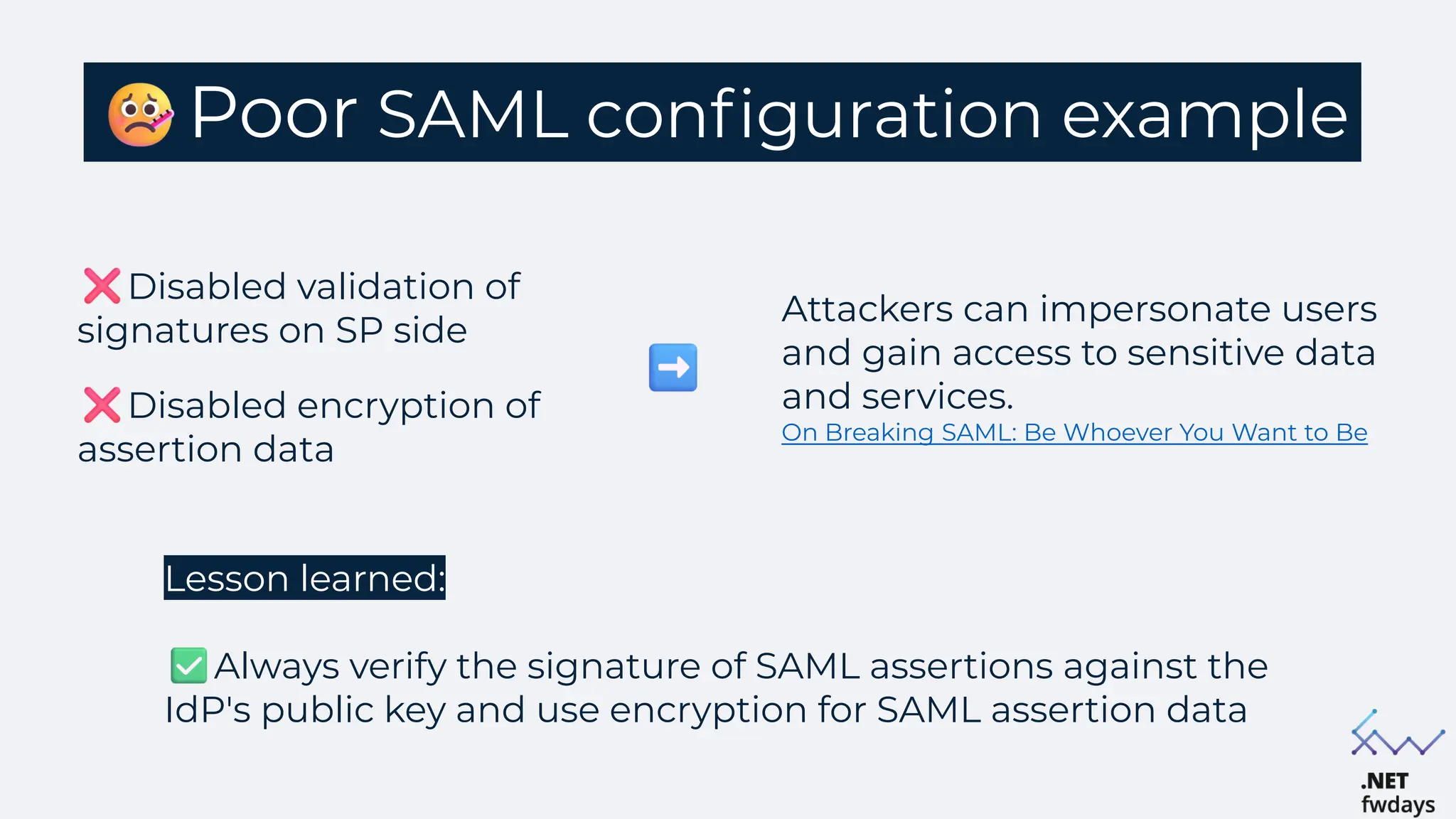
The document discusses the critical importance of secure authentication methods, particularly focusing on Single Sign-On (SSO) and Security Assertion Markup Language (SAML) protocols. It highlights the consequences of poor authentication practices, such as financial losses and reputational damage, while providing best practices for implementing secure SSO and SAML configurations. The document also compares SSO and OAuth, describes common SSO protocols, and emphasizes the need for robust security measures and regular updates to mitigate vulnerabilities.