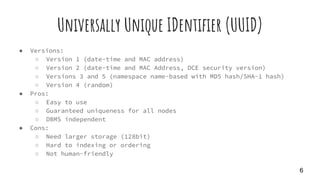
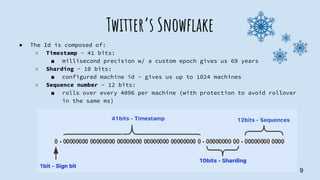
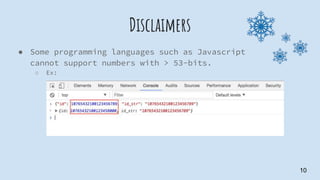
This document discusses solutions for generating unique IDs in distributed systems. It describes existing solutions like auto-incrementing database IDs, ticket servers, and UUIDs, and their pros and cons. It then explains Twitter's Snowflake algorithm in detail, which generates compact, sortable, unique IDs across distributed nodes at high speeds without coordination. Finally, it introduces SepTech's Snowflake4S library, which is inspired by Twitter's Snowflake and makes unique ID generation easily embeddable in applications.