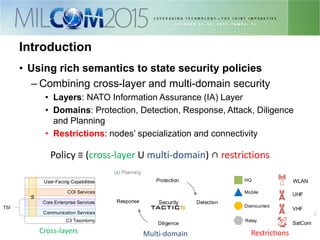
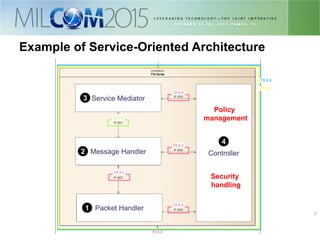
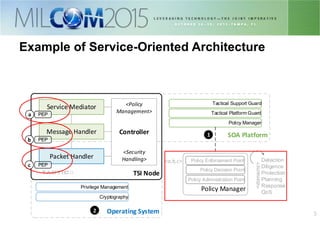
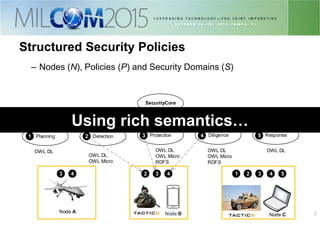
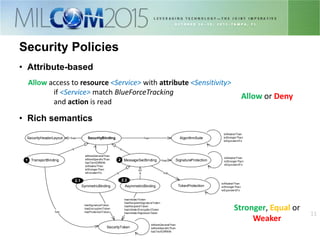
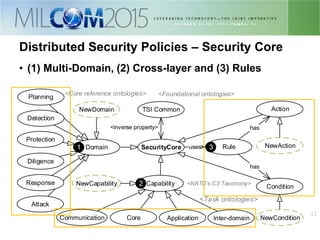
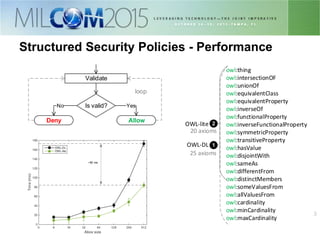
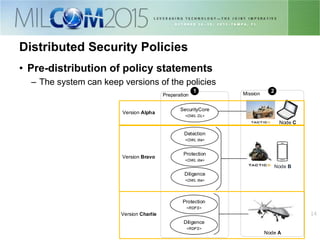
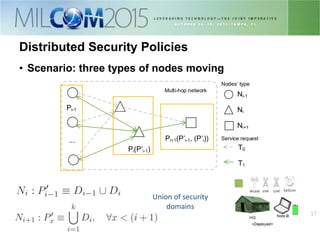
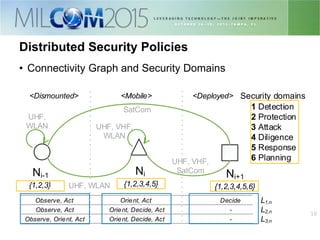
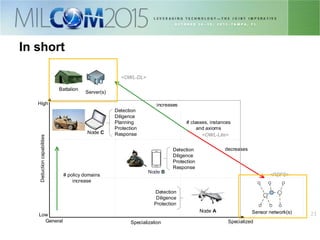
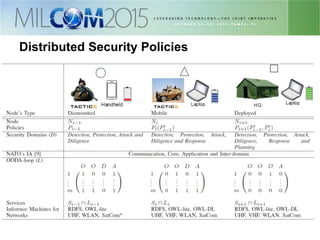
The document discusses the development of distributed security policies for service-oriented architectures in tactical networks, emphasizing the integration of cross-layer and multi-domain security approaches. It presents a comprehensive taxonomy of security domains and structured policies, highlighting the importance of adaptive security measures based on mission profiles and node types. The conclusion suggests that the OWL-DL language is a flexible option for implementing security policies in these complex environments.