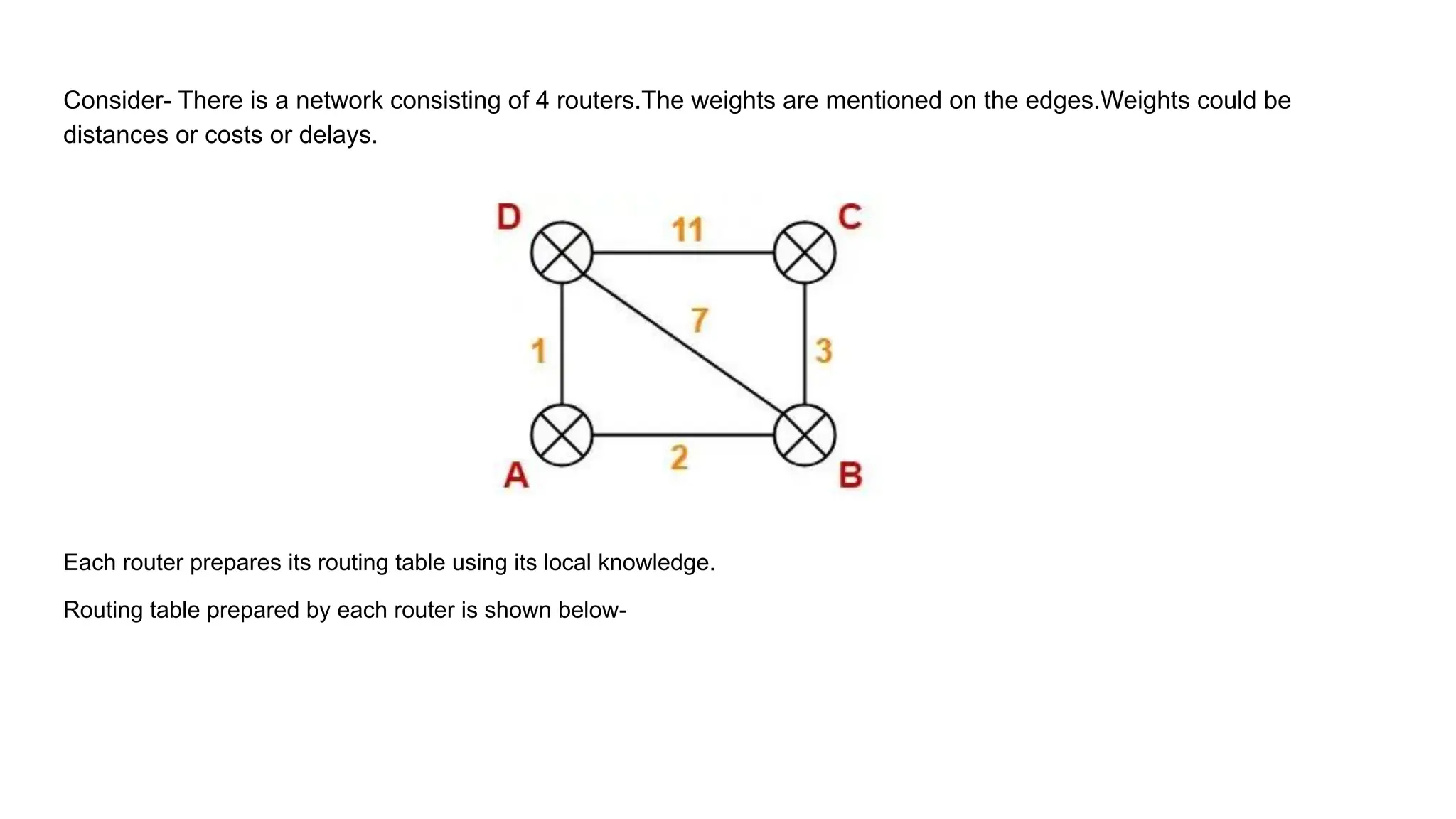
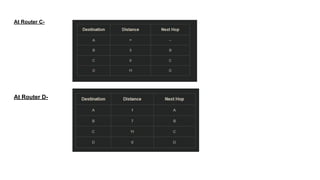
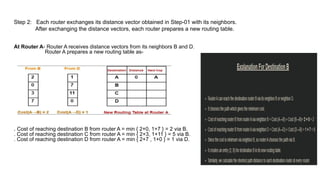
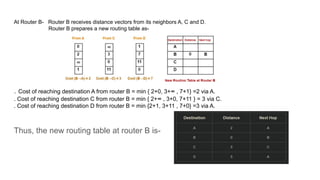
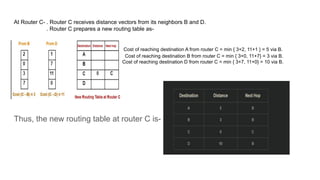
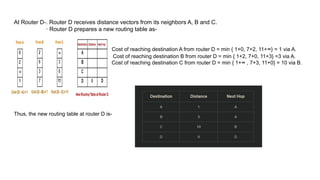
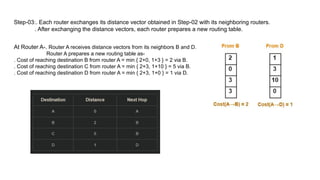
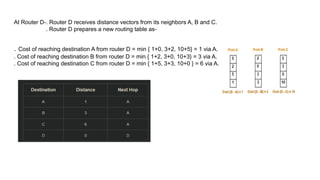
The document describes a scenario involving four routers that exchange distance vectors to prepare their respective routing tables. After iteratively updating these tables based on received information, the routers identify the most efficient paths to each destination, determining which links remain unused once stability is achieved. The final routing tables indicate specific edges utilized and highlight the unused links between certain routers.