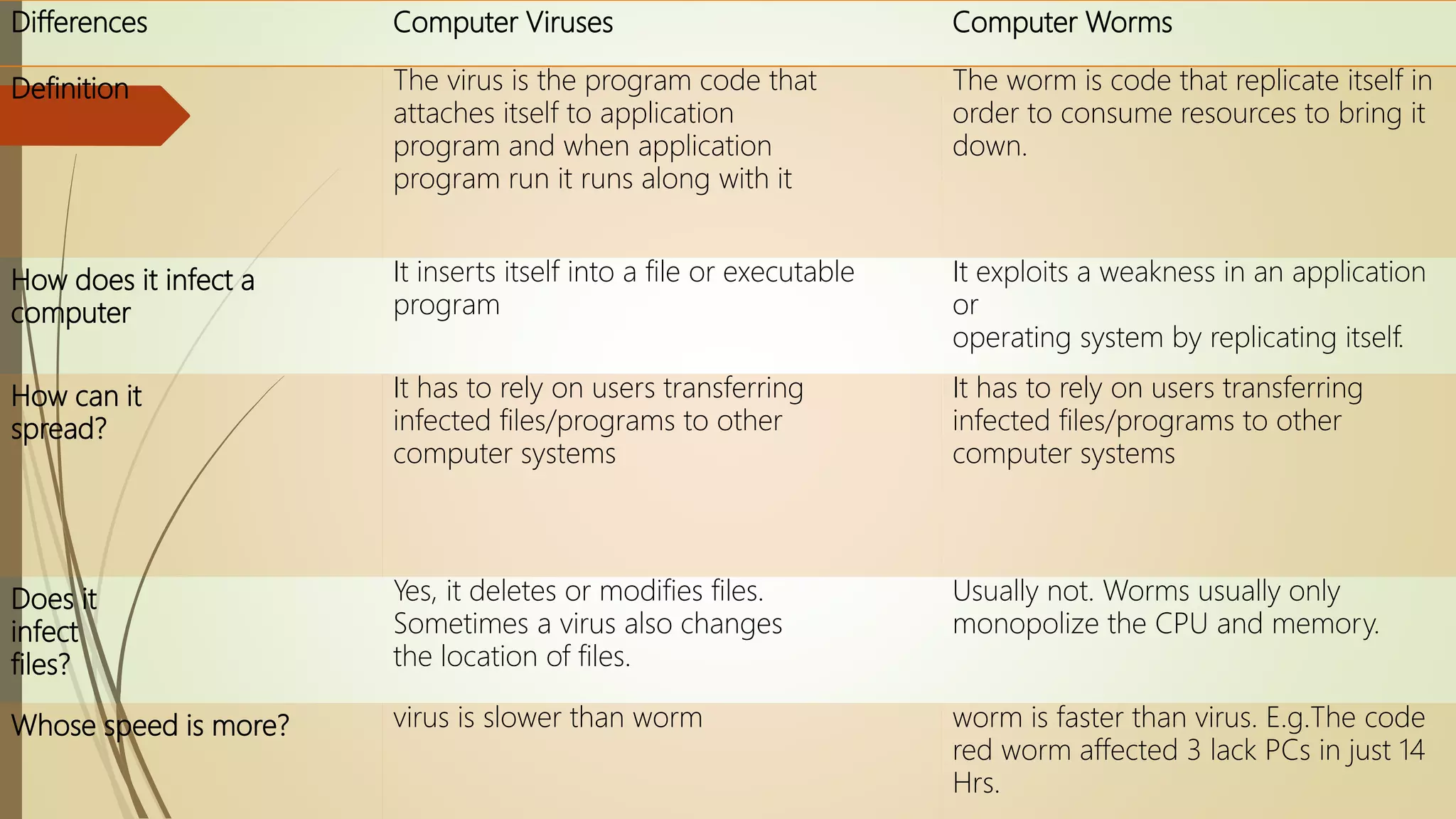
This document discusses different types of cyber attacks including SQL injection, malware, and man-in-the-middle attacks. SQL injection allows inserting SQL statements into a user input field to extract or manipulate database data. Malware includes viruses, worms, trojans, and spyware that can damage systems. A man-in-the-middle attack involves an unauthorized party intercepting communications between two users and modifying the exchange.