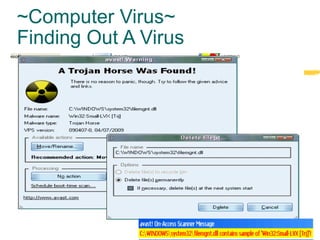
The document provides an overview of computer viruses including their definition, symptoms, how they work and spread, different types of viruses like worms and trojans, examples of specific viruses like Melissa and Bubbleboy, and recommendations for protection like using antivirus software and proper configurations. Computer viruses have become common with over 300 new viruses created each month that can slow down or crash systems and spread through email attachments or downloading infected files. Knowledge of how viruses infect systems can help prevent future attacks.



















![Questions? [email_address] Copies of the latest lovebug virus code are available…in print](https://image.slidesharecdn.com/virus-110502093727-phpapp02/85/Virus-33-320.jpg)