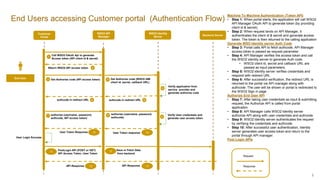
1. End users access a customer portal which calls the WSO2 OAuth API to generate an access token using its client ID and secret.
2. The portal then calls the WSO2 Identity Server to generate an authorization code, passing the access token. It receives a redirect URL to send users to the WSO2 sign-in page.
3. After getting user credentials, the portal calls the authorize API, passing the credentials, authorization code, and access token. If verified, the Identity Server returns a user access token to the portal via the API Manager.